
Oracle Sale Claims Found on Hacker Forums, Crypto Wallet Service, and Empik Data Leak
This week, SOCRadar’s Dark Web Team uncovered a series of high-risk activities surfacing on hacker forums. Key findings include a newly advertised service for processing stolen crypto wallet data across over 100 blockchain networks, and the alleged sale of Empik’s customer database with nearly 25 million records. Additionally, hacktivist group Dark Storm Team claimed responsibility for a DDoS attack on Los Angeles International Airport, and a threat actor is reportedly selling sensitive Oracle data—though Oracle has denied the breach. These developments reflect the ongoing exposure of major platforms and industries to cyber threats.
Receive a Free Dark Web Report for Your Organization:
New Dark Web Service is Detected
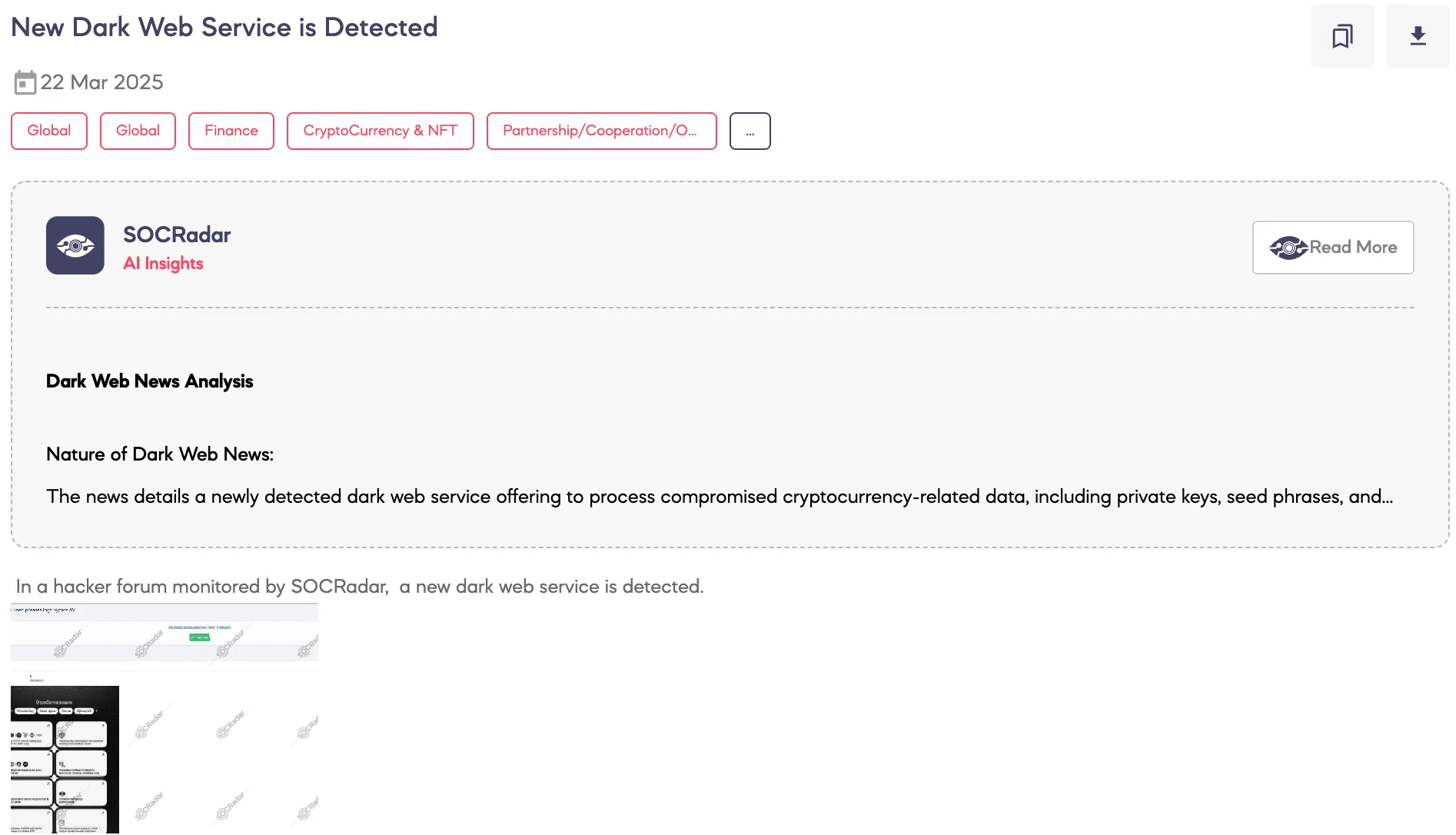
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to offer a service designed to process stolen cryptocurrency-related data, including private keys, seed phrases, and logs. According to the threat actor’s statements, the service supports over 100 blockchain networks, such as Ethereum (ETH), Bitcoin (BTC), Binance Smart Chain (BSC), Polygon, Solana, and others.
The service allegedly includes capabilities to bypass automatic withdrawal protections (anti-bot/anti-burn systems) on EVM-compatible chains, remove liquid NFTs, extract staked tokens, and unlock vested assets. Additionally, it claims to evaluate materials for potential airdrops and withdraw native tokens across supported chains. The threat actor offers to process cryptologs and stolen wallet data under a commission-based model, with varying profit splits depending on the asset value.
The Alleged Customer Database of Empik is on Sale
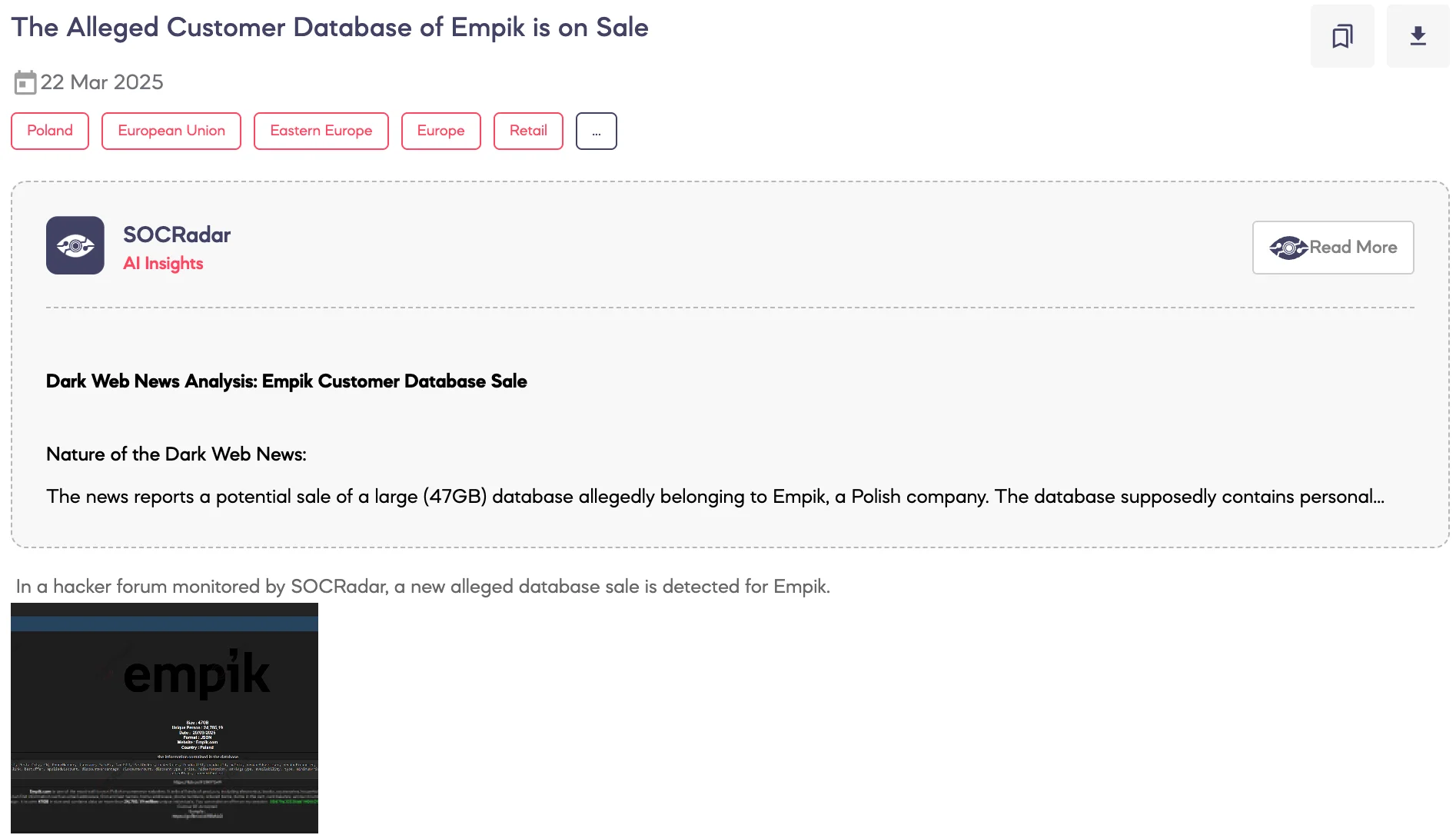
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling a customer database allegedly belonging to Empik.com, a major Polish e-commerce and retail platform. According to the threat actor’s statements, the database is 47GB in size, dated March 20, 2025, and contains information on approximately 24.7 million unique individuals.
The dataset is allegedly in JSON format and includes extensive personal and transactional details such as email addresses, full names, phone numbers, usernames, physical addresses, partial card information, order histories, product details, vendor information, applied discounts, pricing data, and additional metadata related to customer purchases and platform activity.
All claims regarding this dataset are solely based on the threat actor’s statements, and the authenticity of the information has not been independently verified. If accurate, the exposure of such comprehensive customer data could lead to identity theft, financial fraud, and targeted phishing attacks.
Dark Storm Team Conducted DDoS Attack on Los Angeles International Airport
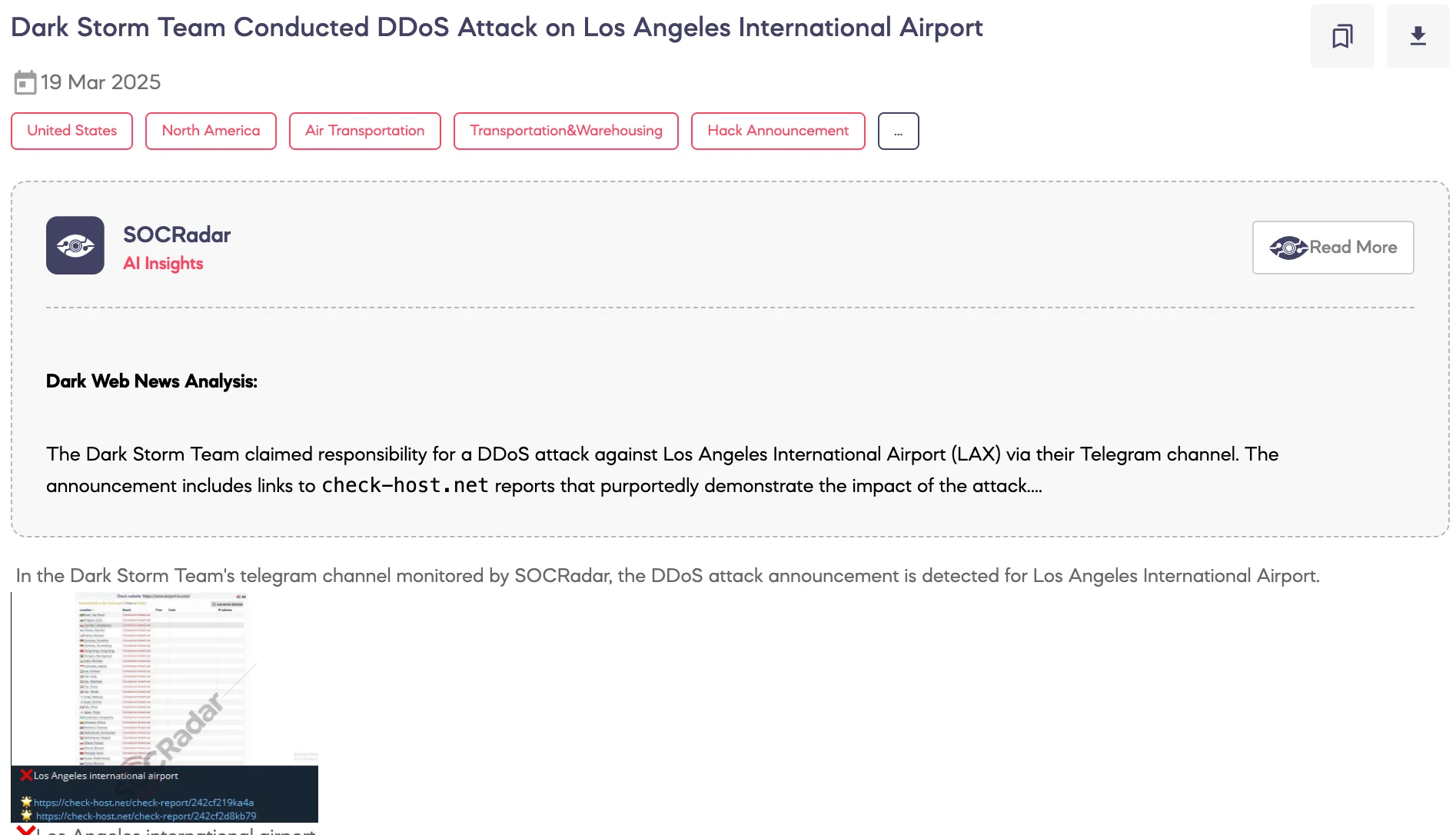
SOCRadar Dark Web Team detected a post on the Telegram channel of the hacktivist group Dark Storm Team, in which the group announced a DDoS (Distributed Denial-of-Service) attack targeting Los Angeles International Airport (LAX). The announcement is based on the statements made by the threat group, and no independent verification has been made regarding the actual impact of the alleged attack. If accurate, targeting critical infrastructure such as an international airport may lead to temporary service interruption, operational disturbances, and reputational damage.
The Alleged Data of Oracle are on Sale
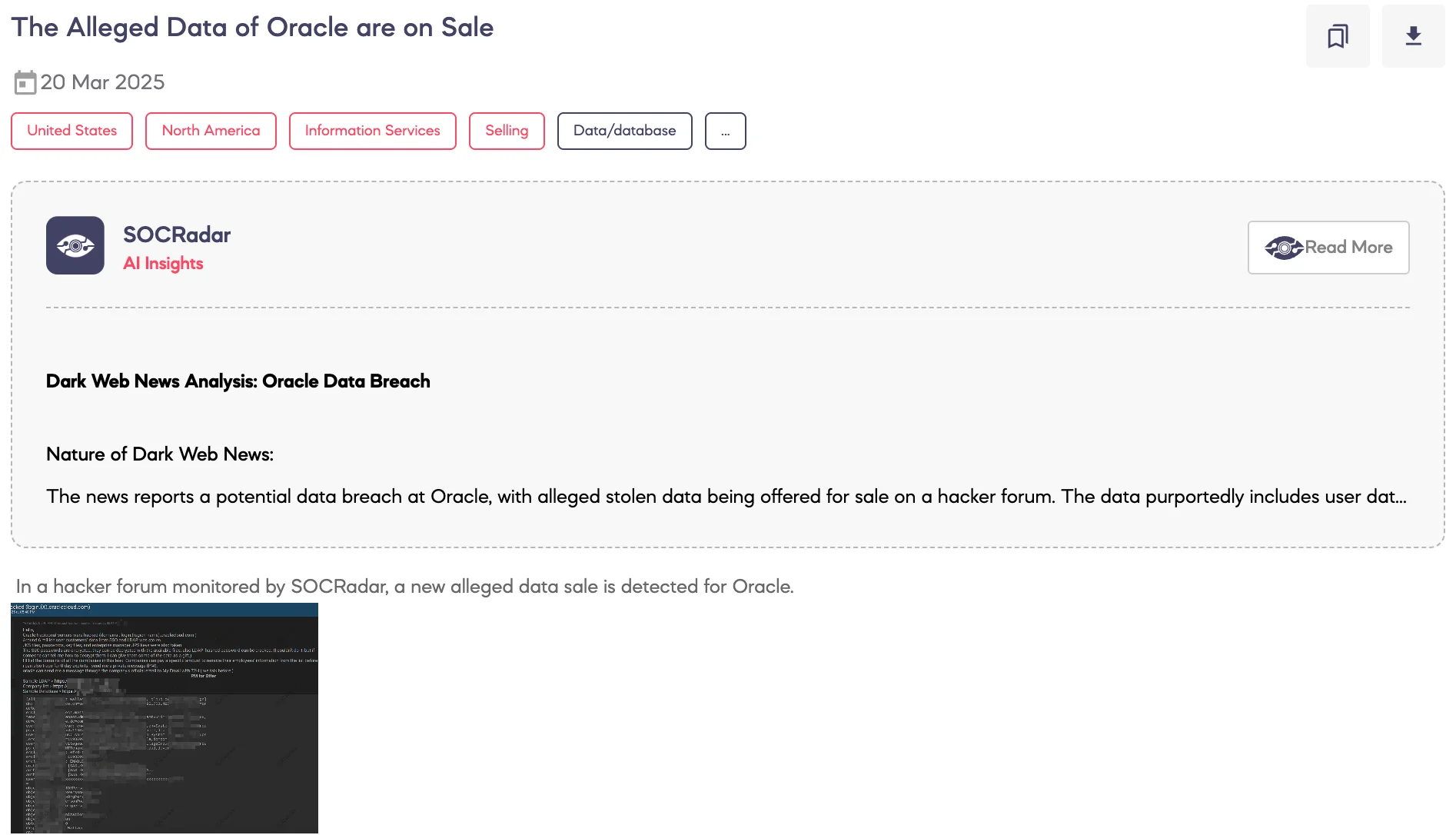
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling allegedly compromised data belonging to Oracle. According to the threat actor’s statements, the breach led to the exposure of approximately six million user records sourced from SSO and LDAP systems, along with JKS files, encrypted passwords, key files, and enterprise manager-related credentials.
The actor also claims that while some of the passwords are encrypted or hashed, they can potentially be decrypted or cracked using the accompanying files. Additionally, the post offers companies the option to pay for the removal of their employee data from the dataset prior to its sale, and invites trades involving 0-day exploits.
However, it is important to emphasize that Oracle has publicly denied the validity of this claim.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































