
Over 22,000 CyberPanel Servers at Risk from Critical Vulnerabilities Exploitation by PSAUX Ransomware
Threat actor’s have been actively exploiting three Remote Code Execution (RCE) vulnerabilities in CyberPanel, a popular web hosting control panel. The vulnerabilities, identified as CVE-2024-51567, CVE-2024-51568, and CVE-2024-51378, allow attackers to gain unauthorized root access and deploy PSAUX ransomware. The affected CyberPanel versions include 2.3.6 and 2.3.7, enabling attackers to completely take over vulnerable systems.
What Are the Vulnerabilities in CyberPanel?
Cybersecurity researchers DreyAnd and Luka Petrovic uncovered multiple zero-day vulnerabilities in CyberPanel versions 2.3.6 and potentially 2.3.7. Each of these vulnerabilities carries a maximum CVSS score of 10, indicating severe risk:
- CVE-2024-51567: This flaw exists in the upgrademysqlstatus function within databases/views.py. Attackers bypass the security middleware using shell metacharacters in the statusfile property, leading to remote command execution.
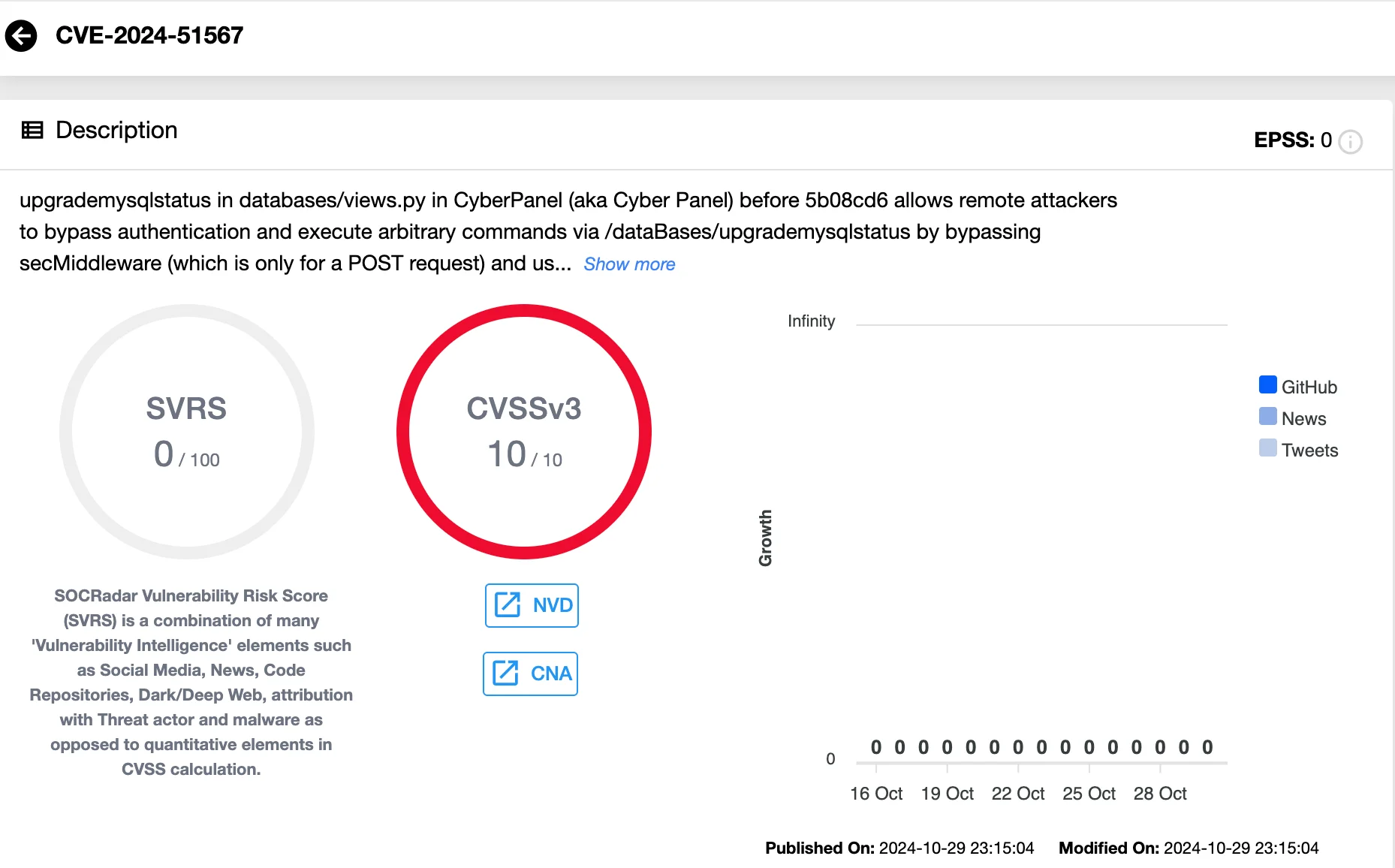
Details of CVE-2024-51567 (SOCRadar Vulnerability Intelligence)
- CVE-2024-51568: This vulnerability involves command injection in the ProcessUtilities.outputExecutioner() function, specifically through the completePath parameter. It allows for file uploads and remote code execution without authentication.
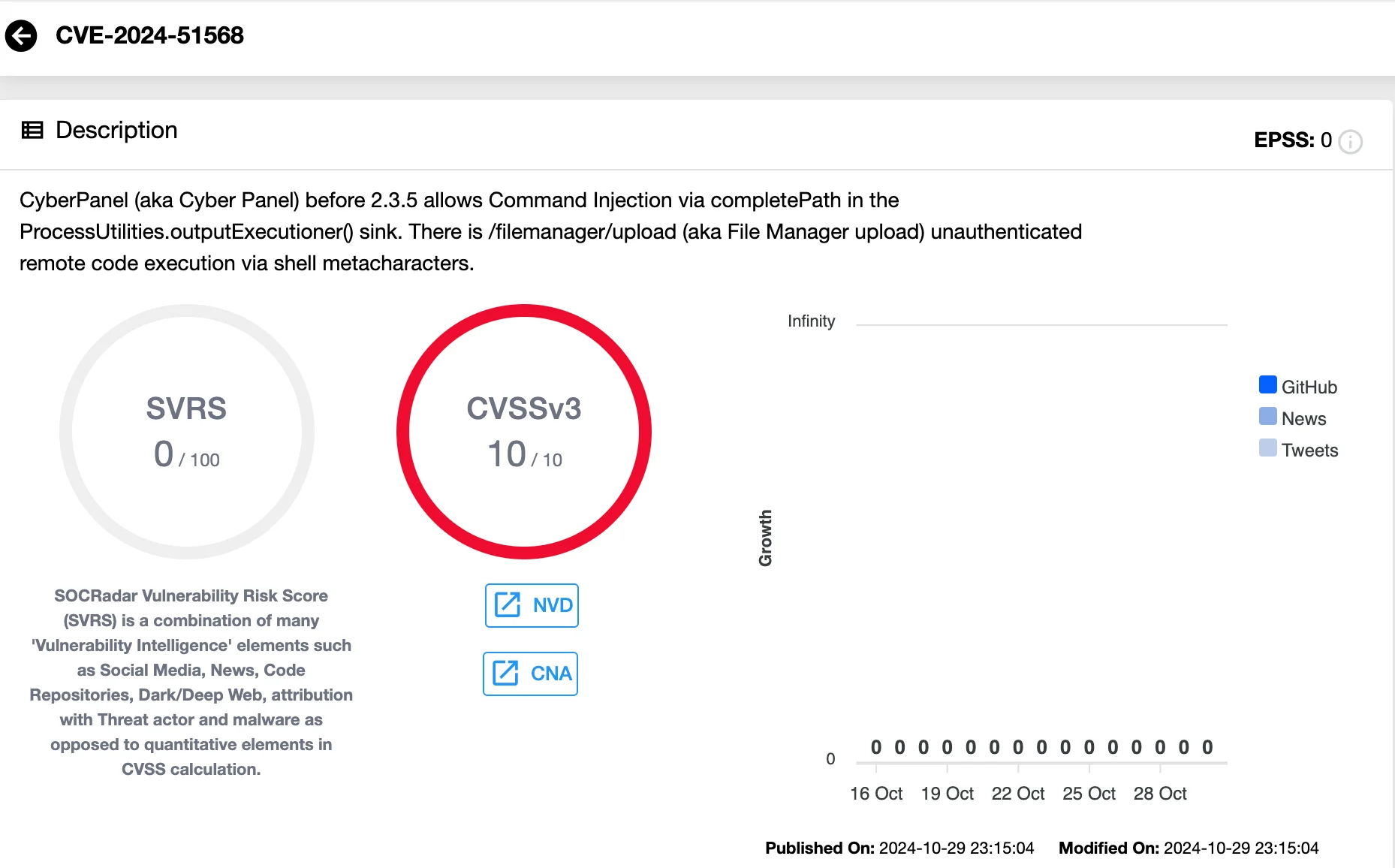
Details of CVE-2024-51568 (SOCRadar Vulnerability Intelligence)
- CVE-2024-51378: This vulnerability affects the getresetstatus function within dns/views.py and ftp/views.py. It enables attackers to execute commands remotely by bypassing middleware.
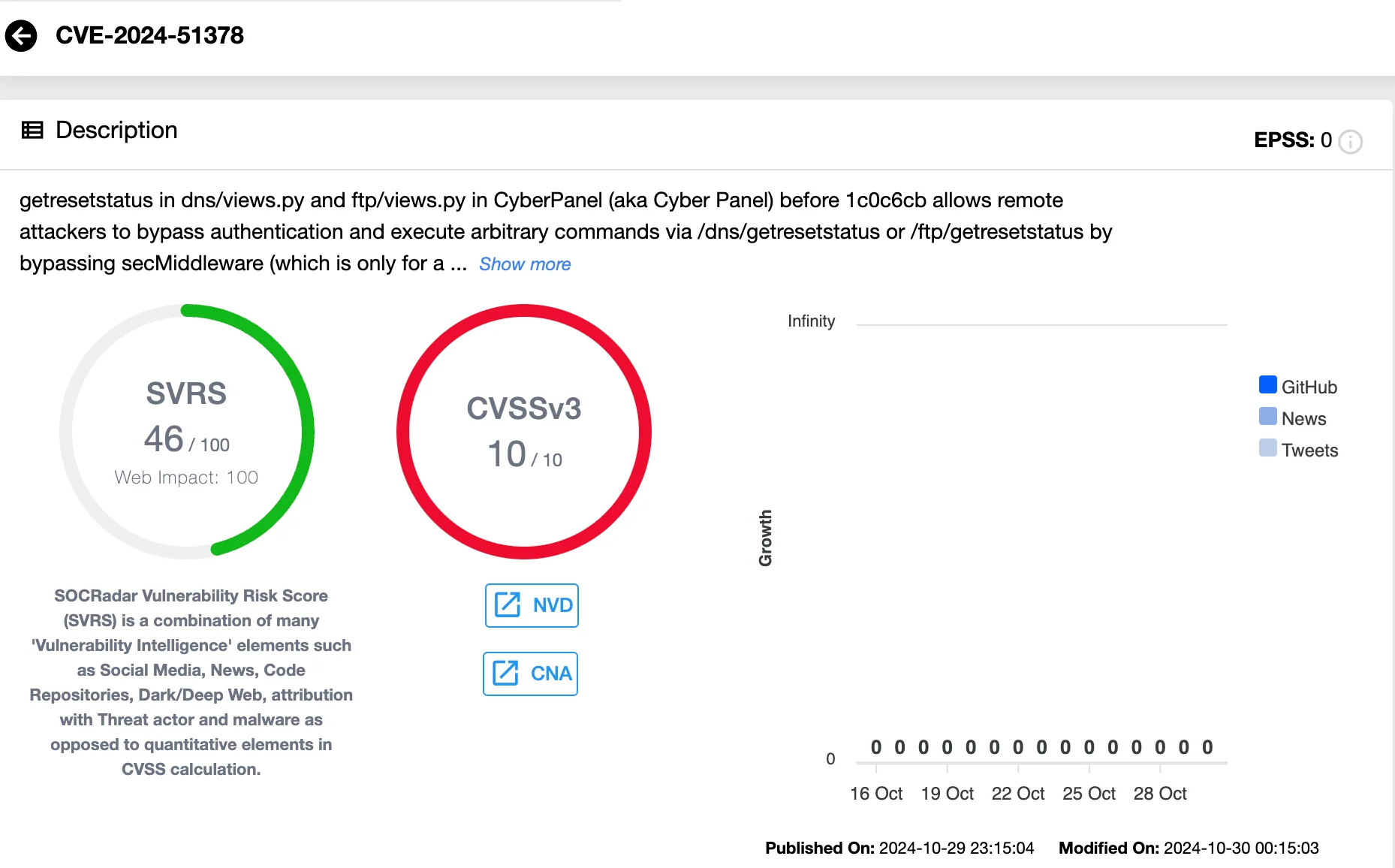
Details of CVE-2024-51378 (SOCRadar Vulnerability Intelligence)
Are you fully aware of your attack surface? SOCRadar’s Attack Surface Management (ASM) provides the visibility needed to maintain security. By continuously tracking your digital footprint—identifying shadow IT, exposed assets, and vulnerabilities—you can swiftly detect and address weaknesses before attackers exploit them.
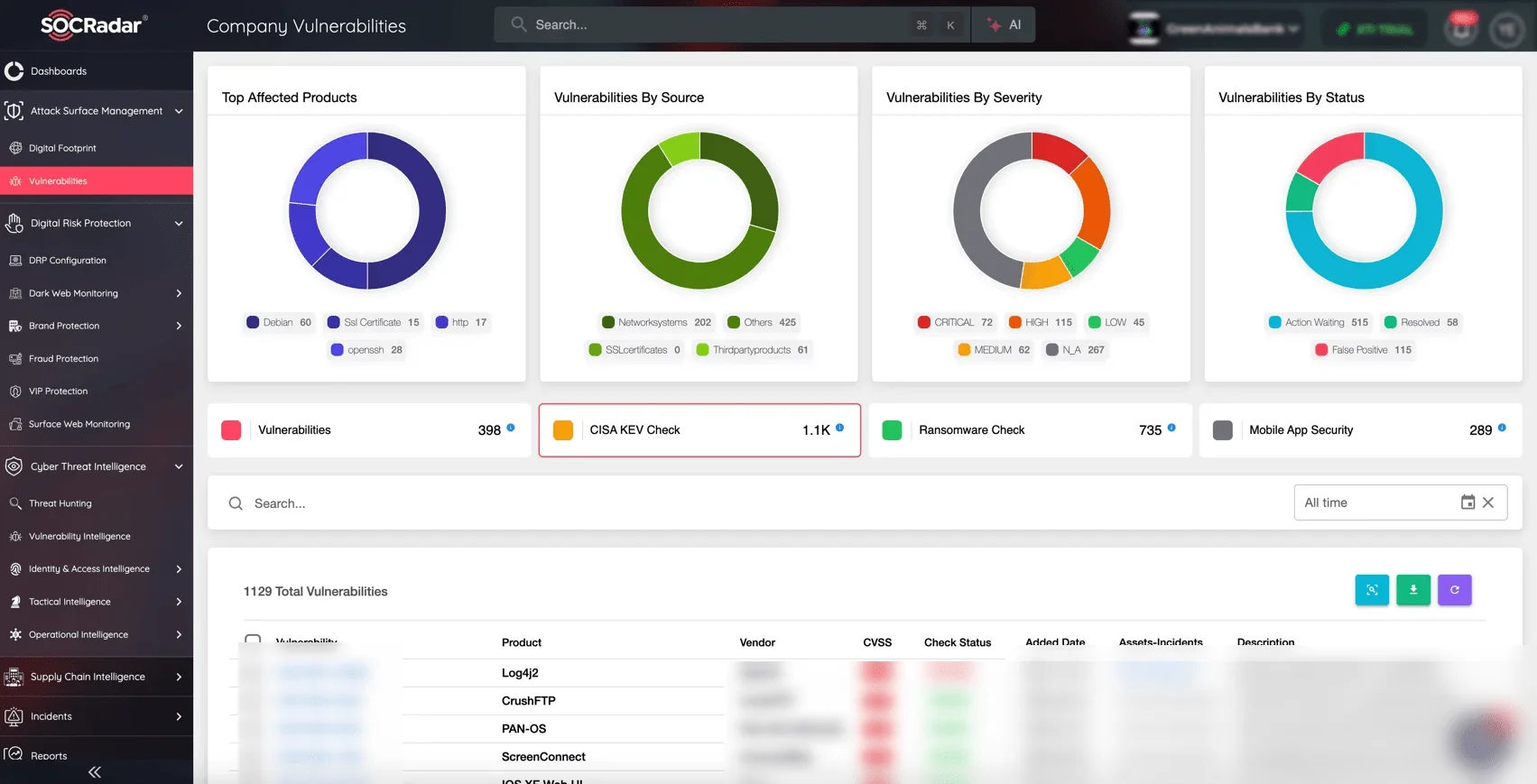
With SOCRadar’s ASM module, identifying and assessing company vulnerabilities becomes simpler.
SOCRadar’s ASM empowers you to close security gaps, enhance defenses, and stay ahead of emerging threats. Additionally, it features a CISA KEV Check, which automatically monitors the CISA Known Exploited Vulnerabilities (KEV) list. This keeps you informed about actively exploited vulnerabilities affecting your systems, enabling you to prioritize patches and maintain compliance with regulatory requirements.
How Extensive is the Threat?
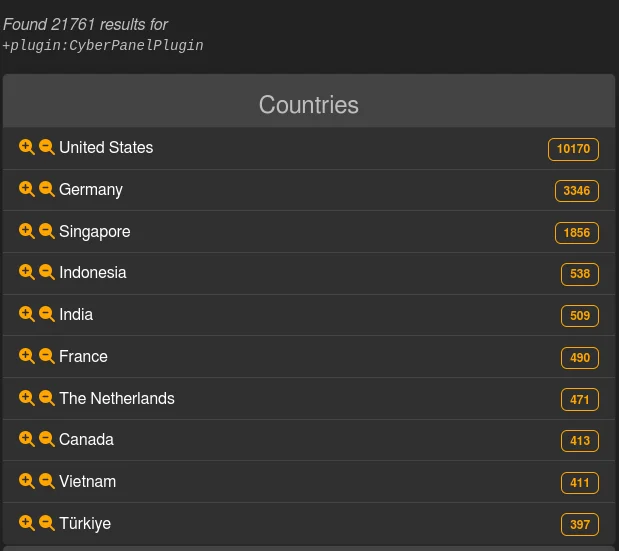
Geographical Distribution of Exposed and Vulnerable Instances (LeakIX)
The LeakIX findings reveal that 21,761 CyberPanel servers are exposed worldwide, with their geographical distribution highlighted. The highest number of exposed CyberPanel servers is found in the United States (10,170), followed by Germany (3,346) and Singapore (1,856).
This distribution suggests that attackers might focus more on servers located in these countries, increasing the risk of attacks in these regions. With the majority of the exposed CyberPanel instances located in the U.S., they could be more susceptible to attacks, serving as a potential vulnerability hotspot.
How Did PSAUX Exploit CyberPanel?
The PSAUX ransomware campaign, active since June 2024, has targeted exposed web servers through known vulnerabilities and configuration weaknesses. When PSAUX ransomware infects a server, it performs the following actions:
- File Encryption: Generates a unique AES key and Initialization Vector (IV) to encrypt server files.
- Ransom Note Deployment: Drops ransom notes named index.html in every directory and copies them to /etc/motd, displaying the ransom note upon login.
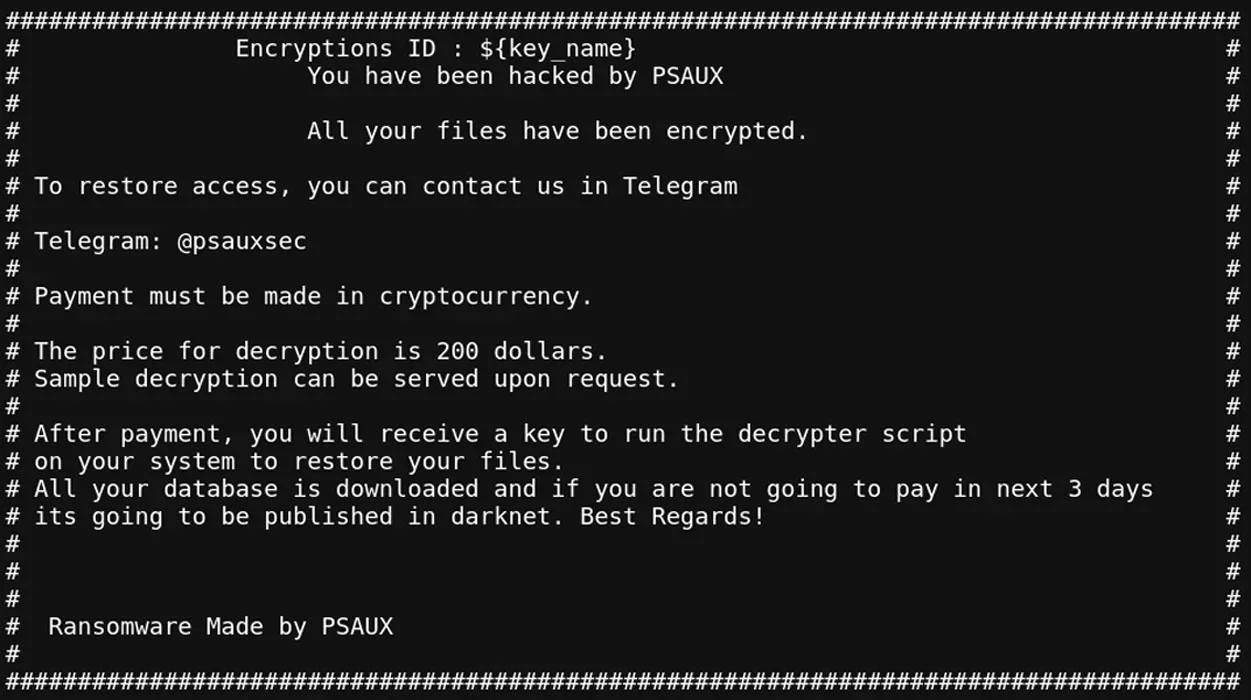
PSAUX ransom note (LeakIX)
- RSA Key Protection: The AES key and IV are further encrypted with an embedded RSA key, saved as /var/key.enc and /var/iv.enc.
Attackers used scripts like ak47.py to exploit the CyberPanel vulnerabilities and actually.sh to handle file encryption.
How Are Researchers Responding with PSAUX Decryption Tools?
In response to the widespread PSAUX ransomware attacks, LeakIX and researcher Chocapikk have developed and released a decryption tool. This tool takes advantage of a weakness in the ransomware’s encryption routine, potentially allowing victims to recover their files without paying the ransom.
However, there is a risk involved: the decryption process relies on the specific encryption keys used by the attackers. Using the wrong key could corrupt the data, so users should back up their files before attempting to use the tool.
How Did CyberPanel Respond?
Upon receiving the vulnerability report, CyberPanel’s development team acted quickly, reviewing the issue and deploying a security patch within 30 minutes. While the researchers suggested a public disclosure, CyberPanel initially withheld the announcement to allow users time to update their systems. Despite these precautions, details about the flaw were prematurely leaked by a third-party source, leading to heightened user concerns.
The patch has since been rolled out as part of a routine update on GitHub, but CyberPanel has not yet provided full details about the flaw to prevent further risk to unpatched servers.
CyberPanel issued specific recommendations to ensure users can secure their systems:
- For Users with SSH Access: Users are advised to apply the patch using CyberPanel’s update guide. This manual update is essential to mitigate the vulnerability effectively.
- For Users without SSH Access: If SSH access is restricted, likely due to server overload from attack attempts, CyberPanel suggests contacting hosting providers. Users should request a temporary lifting of IP blocks or enable port 22 to proceed with the update.
CyberPanel urges users to update their installations as soon as possible to safeguard against potential attacks. The development team has confirmed that additional information about the vulnerability will be shared once the majority of users have applied the patch.
Get Ahead with SOCRadar’s Vulnerability Intelligence
As new vulnerabilities emerge daily, taking proactive steps is crucial to secure your organization’s digital landscape. SOCRadar’s Vulnerability Intelligence equips you with the tools needed to anticipate potential threats. It helps you identify and prioritize critical vulnerabilities, providing real-time alerts and actionable insights to address risks before attackers can exploit them.
SOCRadar Vulnerability Intelligence Module
The module ensures that your efforts are directed toward the most pressing vulnerabilities, enabling quicker patching and maintaining strong security. With SOCRadar, you’ll consistently stay ahead, shielding your organization from the latest cyber threats.




































