
Critical Path Traversal in FortiWLM (CVE-2023-34990) Permits Code Execution; Next.js Auth Bypass (CVE-2024-51479)
Fortinet and the popular React framework Next.js have recently addressed serious security flaws, shining light on the recurrent risks in digital ecosystems. Among these, CVE-2023-34990 in FortiWLM stands out as the most critical vulnerability, exposing sensitive files without authentication. Additionally, Fortinet has patched flaws in other products, including FortiManager and FortiClient VPN. Meanwhile, users of Next.js face an authorization bypass vulnerability that could compromise sensitive data.
What is CVE-2023-34990?
The most alarming vulnerability identified is CVE-2023-34990 (CVSS 9.8), a critical flaw in FortiWLM, Fortinet’s wireless LAN management solution. This flaw allows unauthenticated attackers to access sensitive files, exploiting a relative path traversal (CWE-23) issue in the application.
How the Vulnerability Works
CVE-2023-34990 enables attackers to abuse the /ems/cgi-bin/ezrf_lighttpd.cgi endpoint in FortiWLM. In detail, by injecting path traversal sequences (../) into the imagename parameter, attackers can gain unauthorized access to log files stored on the system.
According to the NVD, the vulnerability can be exploited to execute unauthorized code or commands through specially crafted web requests, whereas Fortinet’s advisory only describes that it is capable of enabling a remote unauthenticated attacker to read sensitive files.
It is also worth noting that Fortinet has rated the vulnerability with a CVSS score of 9.6 in its advisory, differing from the NVD’s score of 9.8.
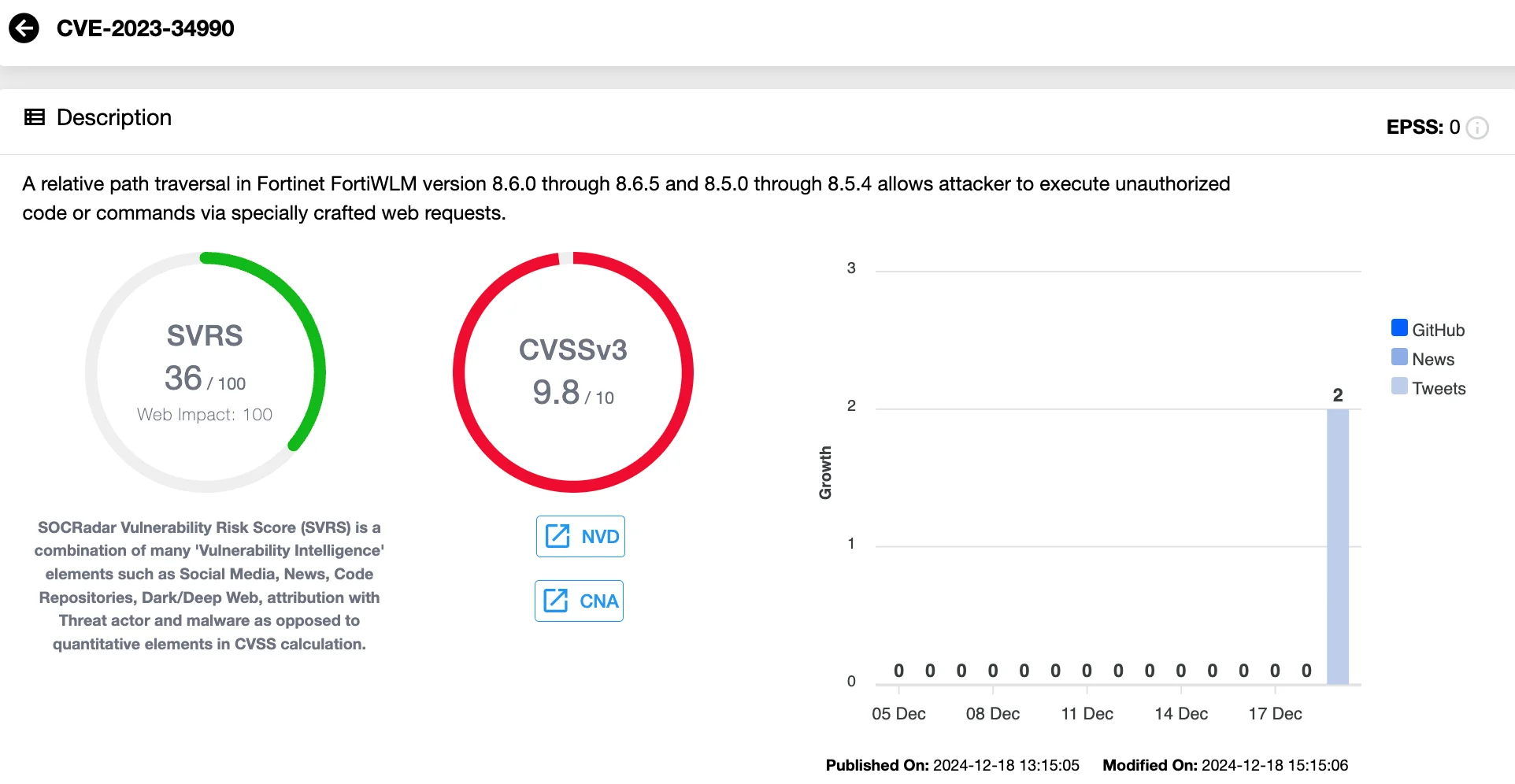
Vulnerability card of CVE-2023-34990 (SOCRadar Vulnerability Intelligence)
The vulnerability poses significant risks because these verbose log files contain administrator session ID tokens. Using these tokens, attackers could hijack sessions, granting them access to authenticated endpoints. The flaw results from improper input validation, which permits directory traversal and unrestricted access to sensitive files without requiring authentication.
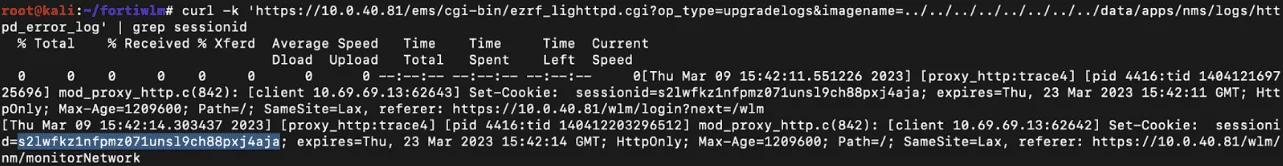
Session ID leaked via the vulnerability (Source: Horizon3)
Concerns About the Vulnerability’s Timeline
Fortinet credits Zach Hanley of Horizon3 for the discovery and responsible disclosure of this vulnerability. In his research blog, Hanley provides an in-depth analysis of the flaw, illustrating how insufficient input validation allows attackers to exploit the vulnerability.
Interestingly, the Horizon3 blog describes the vulnerability as a 2024 zero-day (CVE-2024-????) leading to Remote Code Execution (RCE). Researchers have drawn connections between this said zero-day and CVE-2023-34990, citing the similarity in exploit details and methodology.
In parallel, Fortinet’s advisory and the timeline of the vulnerability have drawn criticism. Hanley reportedly disclosed the flaw in May 2023, but Fortinet only issued a patch on December 18, 2024, leaving a 19 month gap between disclosure and remediation. The possibly missed details in the advisory and the delay in patching has sparked concern within the security community, highlighting the importance of timely patching for vulnerabilities of this severity.

Timeline shown under Hanley’s research blog
Which FortiWLM Versions Are Affected?
The following versions of FortiWLM are impacted by CVE-2023-34990:
- FortiWLM 8.5: Versions 8.5.0 through 8.5.4
- FortiWLM 8.6: Versions 8.6.0 through 8.6.5
Fortinet has addressed this vulnerability by releasing updates for affected versions. Users should immediately upgrade to the latest available versions (8.5.5 and 8.6.6 or later) to protect their systems from potential exploitation.
Emerging threats are increasingly complex, and relying solely on traditional methods can leave your organization exposed. With vulnerabilities being discovered and exploited rapidly, timely detection and response are critical to preventing breaches and minimizing damage. This is where SOCRadar can help.
SOCRadar’s Vulnerability Intelligence Module provides real-time monitoring and alerts for newly discovered vulnerabilities and active exploit activity. This ensures your team stays informed about threats as they emerge, enabling swift action to mitigate risks before they escalate.
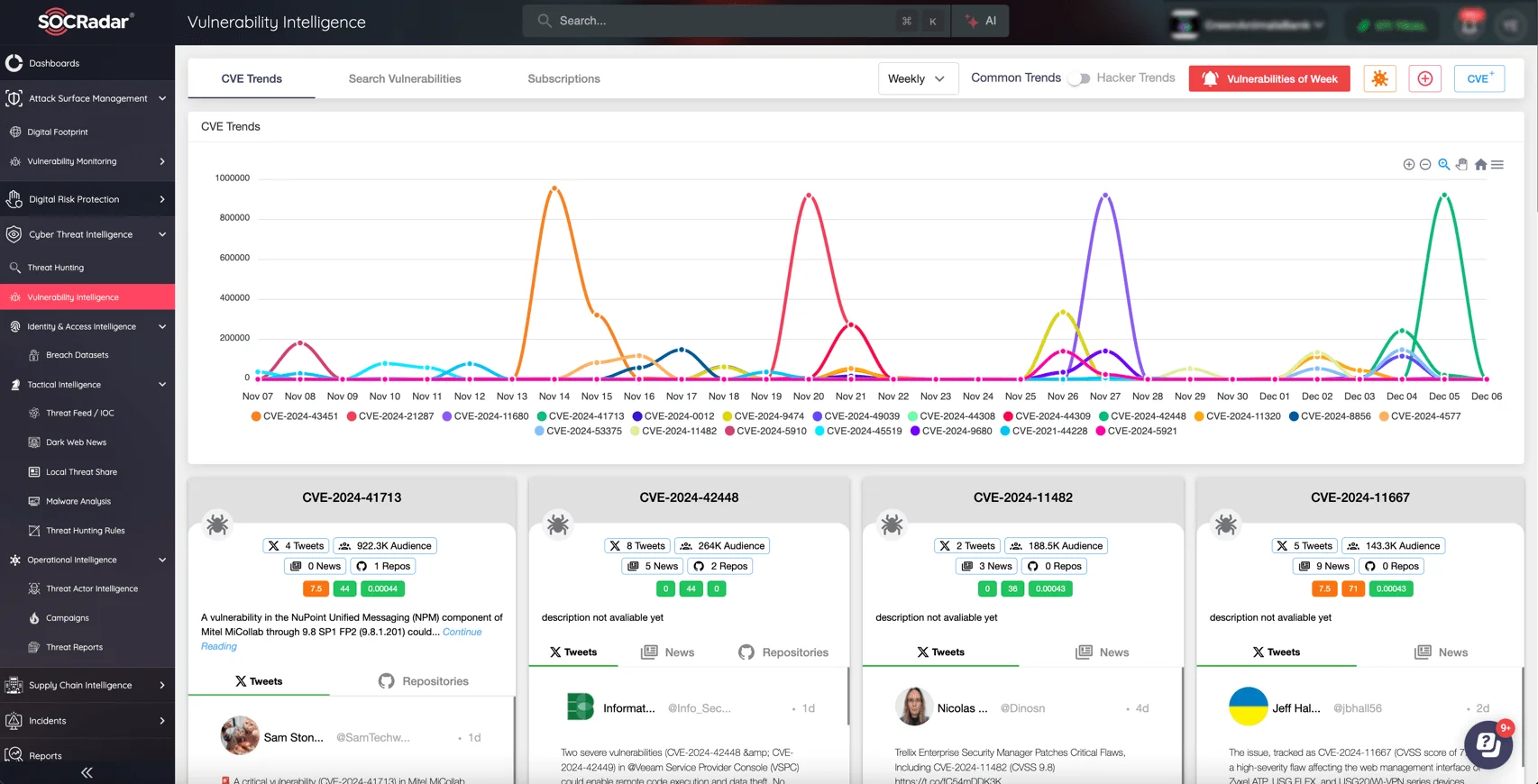
SOCRadar’s Vulnerability Intelligence
The Vulnerability Intelligence module continuously scans for recent vulnerabilities, ensuring you stay up-to-date on emerging threats. It delivers actionable alerts with detailed, prioritized information about critical risks, helping your team address the most pressing issues first.
Integrated with SOCRadar’s Attack Surface Management (ASM), the module provides a detailed view of your exposed assets, identifying potential weak points and enabling you to prioritize patching effectively.
Other Vulnerabilities in Fortinet Products: FortiManager, FortiClient VPN
Beyond CVE-2023-34990, Fortinet has recently addressed additional vulnerabilities that could severely impact organizational security.
CVE-2024-48889 (CVSS 7.2) impacts FortiManager, allowing authenticated attackers to execute arbitrary code remotely, due to improper neutralization of special elements in OS commands. Exploiting this vulnerability could grant attackers significant control over affected systems, potentially leading to data breaches and operational disruptions.
Meanwhile, CVE-2024-50570 (CVSS 5.0) affects FortiClient VPN for Windows and Linux, enabling attackers to extract VPN passwords from memory. This vulnerability stems from improper handling of sensitive data by JavaScript’s garbage collector, potentially allowing unauthorized access.
Fortinet recommends upgrading to the latest versions of FortiManager and FortiClient to mitigate these risks. For CVE-2024-50570, implementing Two-Factor Authentication (2FA) and ensuring the FortiClient console closes automatically after establishing VPN connections can further reduce exposure.
Patch Your Fortinet Products Now
Applying the latest updates to your Fortinet products is critical to protecting your systems and data from potential attacks. Fortinet has issued advisories outlining the affected and fixed versions, as well as any available workarounds. Review the advisories below:
- FortiWLM Advisory: CVE-2023-34990
- FortiManager Advisory: CVE-2024-48889
- FortiClient Advisory: CVE-2024-50570
Gain Full Visibility and Control with SOCRadar
Threat actors exploit overlooked vulnerabilities in exposed assets. And without a clear view of your organization’s digital footprint, securing your systems becomes a daunting challenge.
SOCRadar’s Attack Surface Management (ASM) module provides complete visibility into your attack surface by identifying all exposed assets and potential weak points. It enables your team to pinpoint vulnerabilities before they escalate, minimizing your exposure to threats.
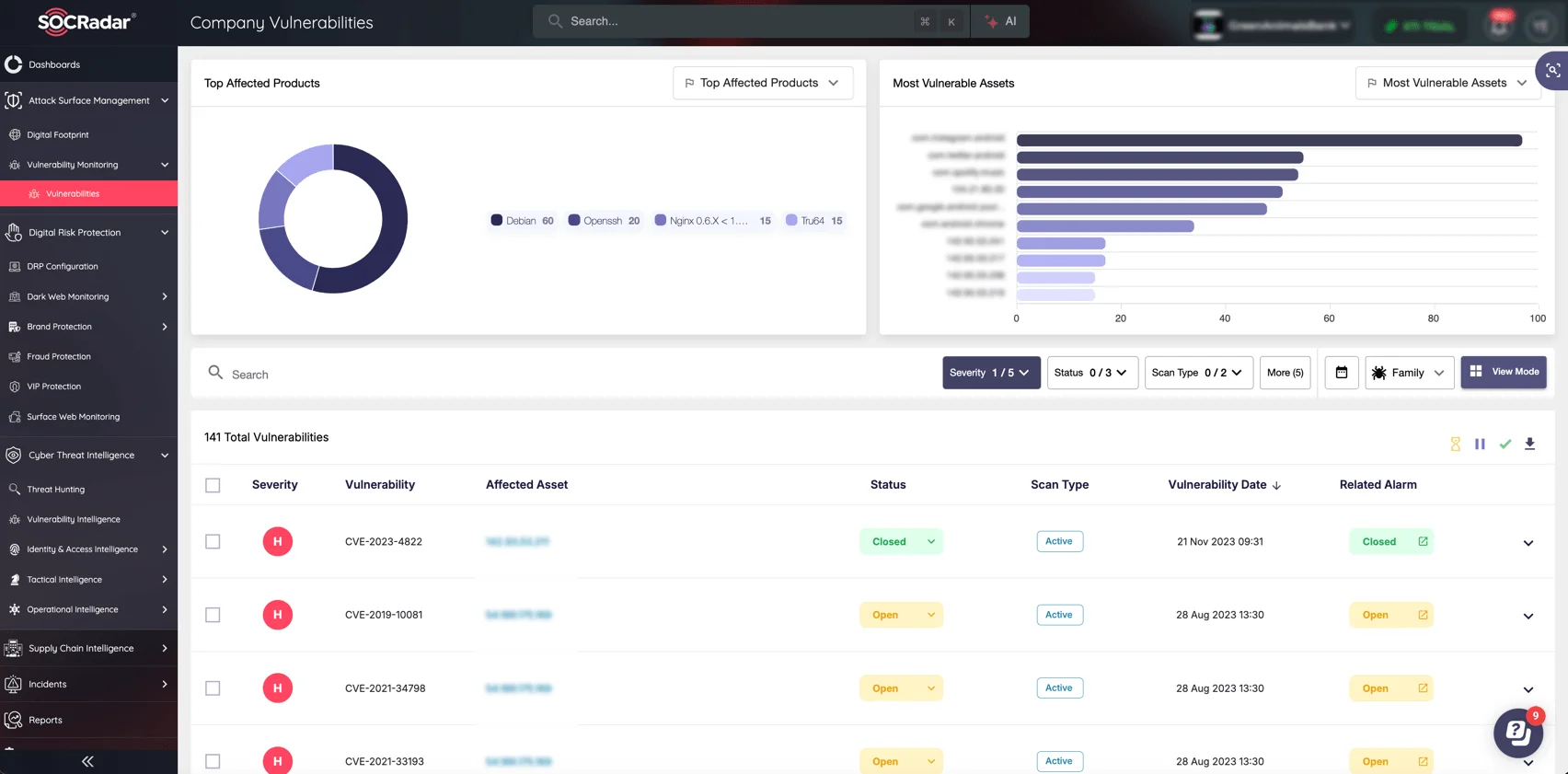
SOCRadar’s Attack Surface Management module, Company Vulnerabilities
With SOCRadar’s ASM module, you gain the tools and insights needed to reduce your attack surface, fortify your defenses, and maintain a strong cybersecurity posture:
- Asset Discovery: ASM maps your organization’s digital footprint, uncovering exposed assets and shadow IT.
- Prioritized Risk Insights: Receive detailed analysis of vulnerabilities with actionable insights, enabling your team to focus on the most critical risks.
- Streamlined Mitigation: ASM integrates seamlessly with your security workflows, helping you remediate vulnerabilities efficiently.
Authentication Bypass Vulnerability (CVE-2024-51479) in Next.js Receives a Fix
Shifting from Fortinet’s recent vulnerabilities, another pressing issue has surfaced in the web development ecosystem. An important security flaw in Next.js, a widely used React framework for building full-stack web applications, has been addressed. With over 7.9 million weekly downloads on npm, the framework’s widespread adoption makes this issue particularly noteworthy.

Official page of Next.js on npm platform
Tracked as CVE-2024-51479 (CVSS 7.5), the vulnerability is a high-severity authorization bypass issue, allowing unauthorized access to sensitive data if authorization is performed in middleware based on pathname.
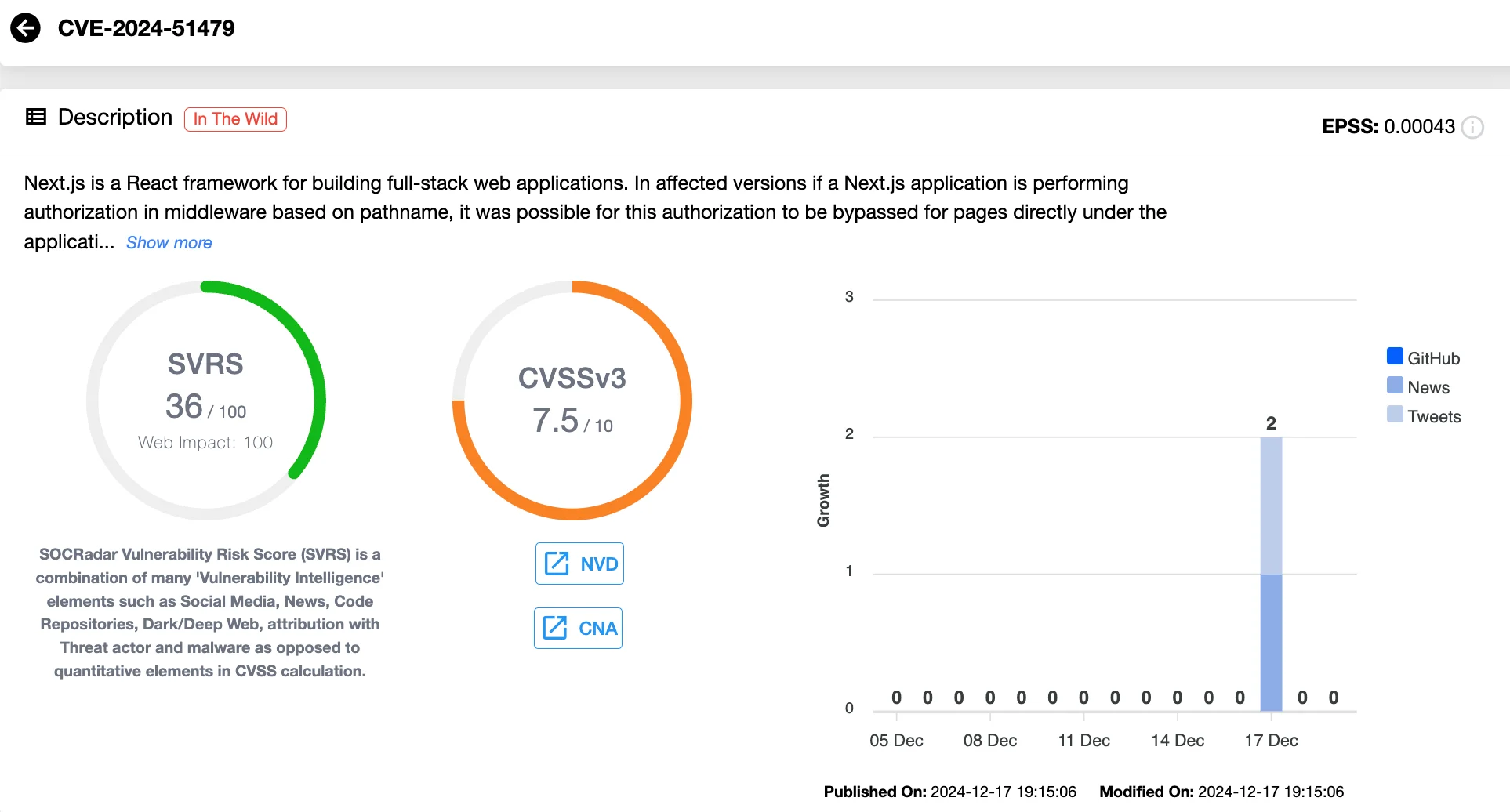
Vulnerability card of CVE-2024-51479 (SOCRadar Vulnerability Intelligence)
Specifically, pages located directly under the application’s root directory could bypass authorization checks. The advisory provides the following example:
- Not affected: example[.]com/
- Affected: example[.]com/foo
- Not affected: example[.]com/foo/bar
Notably, it affects Next.js versions 9.5.5 through 14.2.14.
To mitigate the risk, the Next.js team has released a fix in version 14.2.15 and later, urging developers to update their applications immediately. No official workarounds exist for this vulnerability, but applications hosted on Vercel benefit from automatic mitigation regardless of their Next.js version.
For more details, refer to the official Next.js security advisory on GitHub.




































