
PoC Exploit for CVE-2024-4956 in Sonatype Nexus Repository 3 Draws Threat Actors’ Attention
Sonatype recently released a security advisory alerting users to a high-severity security vulnerability, identified as CVE-2024-4956, in Nexus Repository. Alarmingly, threat actors have started circulating its exploits, indicating increasing interest.
Sonatype, a prominent figure in software supply chain management, offers Nexus Repository as a repository manager for artifacts related to development; the widespread use of this manager makes CVE-2024-4956 particularly concerning.
Successful exploitation of the Sonatype Nexus Repository vulnerability could allow attackers to gain unauthorized access to critical system files, which may include configuration data and credentials. Such access poses a significant risk, potentially compromising the security of entire software development pipelines and exposing proprietary information.
What is CVE-2024-4956?
The critical vulnerability identified in Nexus Repository 3, designated as CVE-2024-4956, is essentially a path traversal issue. It enables an attacker to craft a URL that returns any file as a download from the repository. The sensitive system files accessed by a threat actor could potentially expose confidential data and compromise the security of software development pipelines.
This vulnerability is particularly severe because it can be exploited without any form of authentication. However, to exploit it, an attacker requires network access to the Sonatype Nexus Repository 3 instance.
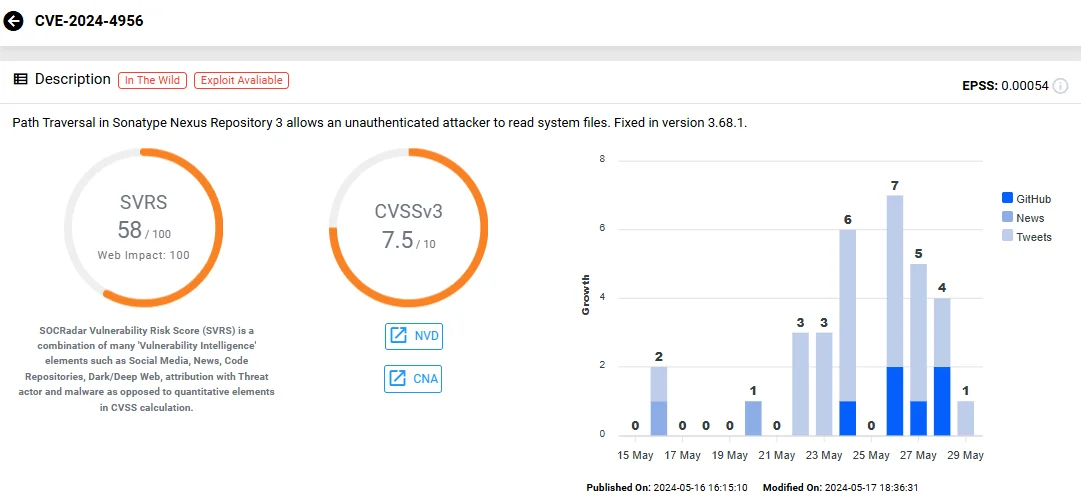
Vulnerability card of CVE-2024-4956 (SOCRadar Vulnerability Intelligence)
Sonatype credited Erick Fernando Xavier de Oliveira with reporting the security vulnerability responsibly via Sonatype’s Bug Bounty Program.
How critical is CVE-2024-4956?
This vulnerability has a high-severity CVSS score of 7.5. An attacker can exploit it to download sensitive system files, including ones outside of the application’s scope.
For companies using Nexus Repository to manage their software artifacts, the ease of accessing and downloading sensitive files through CVE-2024-4956 can have serious ramifications.
Which Nexus Repository versions are affected by CVE-2024-4956?
The vulnerability in question affects a wide range of versions of the Sonatype Nexus Repository. Specifically, all previous versions of Nexus Repository 3.x OSS/Pro up to and including version 3.68.0 are susceptible to CVE-2024-4956.
Has the Nexus Repository 3 vulnerability been exploited?
As of the most recent updates, there have been no reports of exploitation of the CVE-2024-4956 vulnerability.
Nonetheless, Sonatype has acknowledged the existence of publicly available Proof-of-Concept (PoC) examples, indicating a higher risk of exploitation. Recent discussions on platforms such as Telegram show that cybercriminals are getting more interested in exploiting this vulnerability, as SOCRadar observed the recently blogged threat group Hunt3r Kill3rs discussing an exploit that uses Java fuzzing.
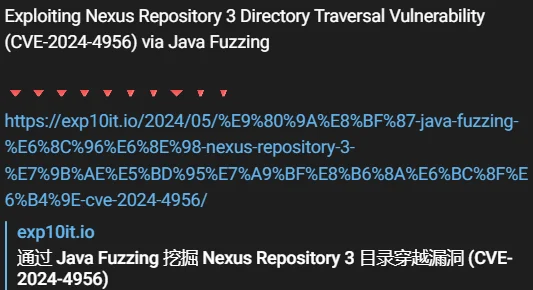
Threat actor(s) shared a Telegram post about the PoC exploit for CVE-2024-4956
Brief of the PoC exploit for CVE-2024-4956
The PoC exploit, demonstrated by the web security researcher X1r0z, involved Java fuzzing techniques using the Jazzer framework to pinpoint and exploit the CVE-2024-4956 vulnerability in Nexus Repository 3.
Knowing that the specific vulnerability allows unauthorized file access on the server, potentially leading to significant data breaches, the researcher demonstrated how manipulated URLs could be used to bypass security measures and access restricted files like /etc/passwd.
This article details the steps taken to analyze and exploit the vulnerability, including setting up a testing environment, identifying the vulnerable components, and demonstrating the successful exploitation.
Additionally, another security researcher successfully reproduced the CVE-2024-4956 vulnerability independently, achieving unauthorized file read capabilities. This independent verification was shared on X.
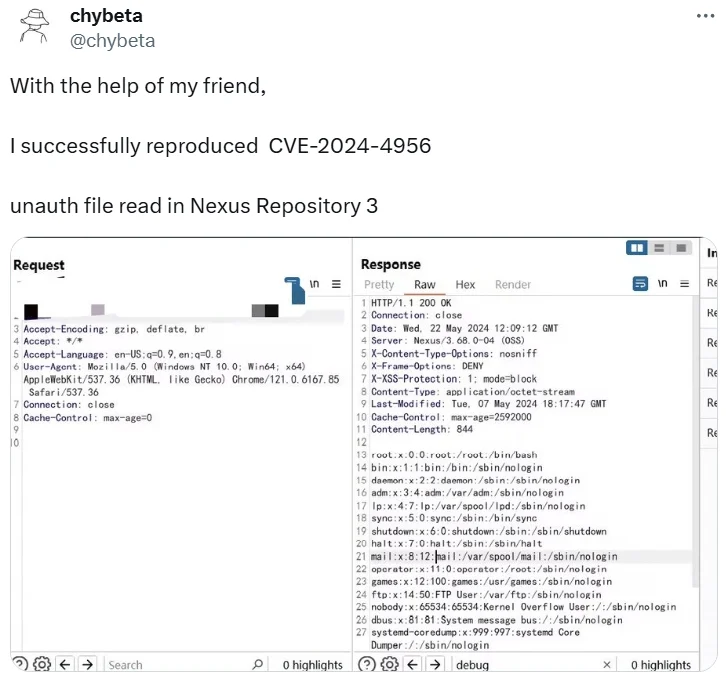
Researcher’s tweet about CVE-2024-4956 (@chybeta on X)
You can obtain extensive details about identified CVEs with SOCRadar’s Vulnerability Intelligence. This includes exploits, mentions on various platforms, relevant repositories, impacted software and systems, all references, as well as observations of the vulnerability in the wild and exploitability scores.
Vulnerability Intelligence, presented under the Cyber Threat Intelligence module of SOCRadar XTI
How to fix the Sonatype Nexus Repository vulnerability, CVE-2024-4956?
In response to the critical path traversal vulnerability identified as CVE-2024-4956, Sonatype has released a security update in Nexus Repository OSS/Pro version 3.68.1.
This updated version effectively patches the vulnerability, closing off the potential for unauthorized file access that previous versions suffered from.
Sonatype strongly recommends that all users of Nexus Repository 3.x OSS/Pro upgrade to version 3.68.1 at the earliest opportunity to ensure protection against this severe security flaw.
As an additional security measure, it is advisable for administrators to rotate credentials for services interconnected with Nexus Repository or hosted on the same server infrastructure.
Further information regarding the vulnerability and its fixes can be found in Sonatype’s official advisory: CVE-2024-4956 Nexus Repository 3 Path Traversal.
For detailed installation instructions and to download the latest version, users can visit the official Sonatype help page: Download Nexus Repository 3.68.1.
Is there a workaround available?
While Sonatype strongly recommends updating to Nexus Repository OSS/Pro version 3.68.1 to address the path traversal vulnerability (CVE-2024-4956), they acknowledge that immediate upgrades may not be feasible for all organizations.
For those unable to upgrade right away, Sonatype has provided temporary mitigations to help protect systems against potential exploits.
Workaround Method 1: Editing the jetty.xml Configuration
For each instance of Sonatype Nexus Repository, administrators should modify the jetty.xml file located at (basedir)/etc/jetty/. The specific modification involves removing the following line:
<Set name=”resourceBase”><Property name=”karaf.base”/>/public</Set>
This action prevents the application from exploiting the vulnerability by disabling the loading of files from the (installdir)/public directory, though it restricts certain functionalities related to file accessibility.
Workaround Method 2: AWS WAF Core Rule Adjustment
If Nexus Repository access is protected by AWS WAF, implementing the GenericLFI_URIPATH rule can provide an effective prevent exploitation. This rule helps block malicious attempts to exploit the path traversal flaw through crafted URLs.
For detailed instructions on implementing these workarounds and to understand their implications, please refer to the official Sonatype support article: Nexus Repository CVE-2024-4956 Workarounds.
Effective Digital Asset Monitoring and Vulnerability Management via SOCRadar
Keep up with cybersecurity trends and respond quickly to new vulnerabilities; with SOCRadar’s Attack Surface Management (ASM) module, you can safeguard digital assets by continuously monitoring them. The module sends timely threat alerts with quick and actionable insights, enabling effective preemptive actions to improve your cybersecurity posture.
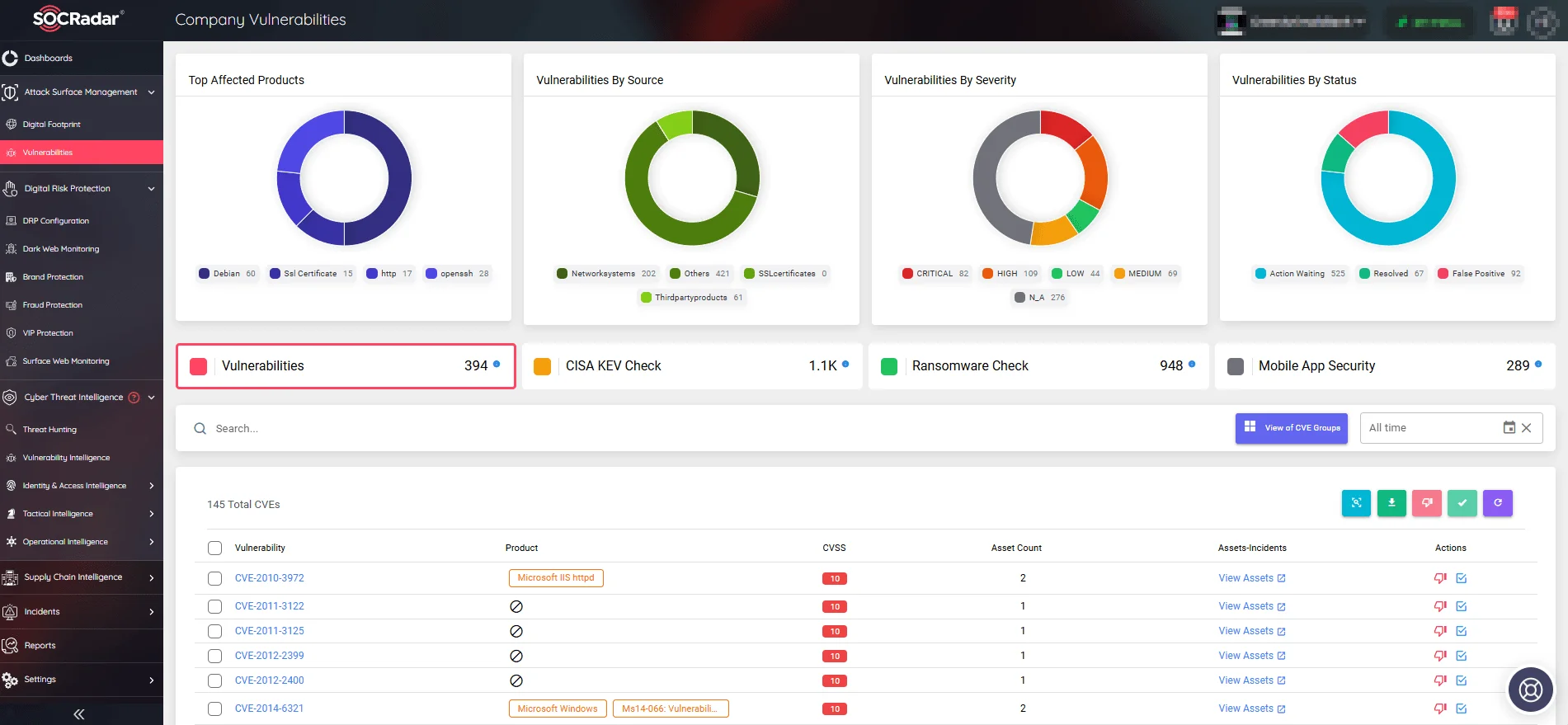
SOCRadar’s Attack Surface Management module, the Company Vulnerabilities page




































