
PoC Released for Authentication Bypass Vulnerability in VMware
Vulnerability-related PoC has been published that allows threat actors to bypass authentication across multiple VMware products. VMware previously shared patches for the vulnerability.
VMware issued a security advisory on May 18, 2022, for vulnerabilities affecting Workspace ONE Access, vRealize Automation, and VMware Identity Manager products.
- CVE-2022-22972 (CVSS 9.8): Authentication Bypass Vulnerability
- CVE-2022-22973 (CVSS 7.8): Local Privilege Escalation Vulnerability
The company, which also published an additional Q&A informing its customers on the subject, shared some mitigating recommendations for users who cannot apply the patches, including disabling all but one admin.
The Impact of the Vulnerability Can Be Massive
Last Tuesday, Horizon3 cybersecurity researchers announced that an exploit is possible for CVE-2022-22972, and they will be sharing PoC soon. They published a detailed analysis of the issue on their website yesterday and PoC on GitHub.
In the review, researchers stated that authentication in vRealize Automation 7.6 could be bypassed thanks to the script to be used by exploiting the vulnerability with the code CVE-2022-22972 and underlined that the exploit could be quite easy for attackers.
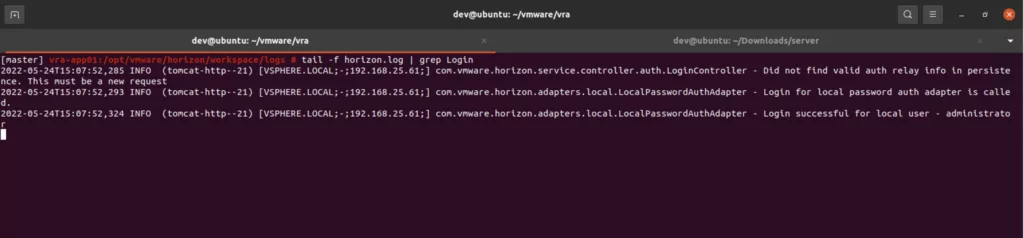
Horizon3’s analysis shows that this vulnerability could have major worldwide consequences. One of the points made explicitly in the review is that although Shodan has shown a limited number of devices vulnerable to this vulnerability, many health, education, and government organizations may be at risk.
The US Cyber Security and Infrastructure Security Agency (CISA) also passed a note warning all organizations.
Other VMware Vulnerabilities Recently Detected
VMware has patched two vulnerabilities, one to RCE (CVE-2022-22954) and the other to “root” privilege escalation (CVE-2022-22960), affecting Workspace ONE Access and Identity Manager. Cybersecurity experts believe that threat actors can combine these unpatched vulnerabilities to launch effective attacks.
No exploit has been identified for CVE-2022-22972 yet, but relevant updates or mitigation measures are urgently needed.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.



































