
Progress Telerik Report Server Receives Security Update for Critical Auth Bypass Vulnerability, CVE-2024-4358
[Update] June 14, 2024: “CISA Adds CVE-2024-4358 to Known Exploited Vulnerabilities Catalog”
[Update] June 4, 2024: “Proof-of-Concept Exploit Available for Critical Telerik Report Server Vulnerability (CVE-2024-4358)”
A critical vulnerability has been discovered in Progress Telerik Report Server, a server-based tool for report management, widely utilized by businesses globally. This platform offers centralized report storage, comprehensive management capabilities, and diverse options for organizing and previewing reports.
The vulnerability in Telerik Report Server, identified as CVE-2024-4358, enables unauthenticated attackers to bypass authentication controls, potentially accessing sensitive report data and server functionalities. Such access could lead to further exploitative actions within the network.
What is CVE-2024-4358? Details of the Auth Bypass Flaw in Progress Telerik Report Server
The vulnerability, cataloged under CWE-290 (Authentication Bypass by Spoofing) carries a critical CVSS score of 9.8. It involves specific versions of Progress Telerik Report Server running on IIS servers.
An attacker can exploit this security vulnerability to access restricted areas of the Telerik Report Server without proper authentication.
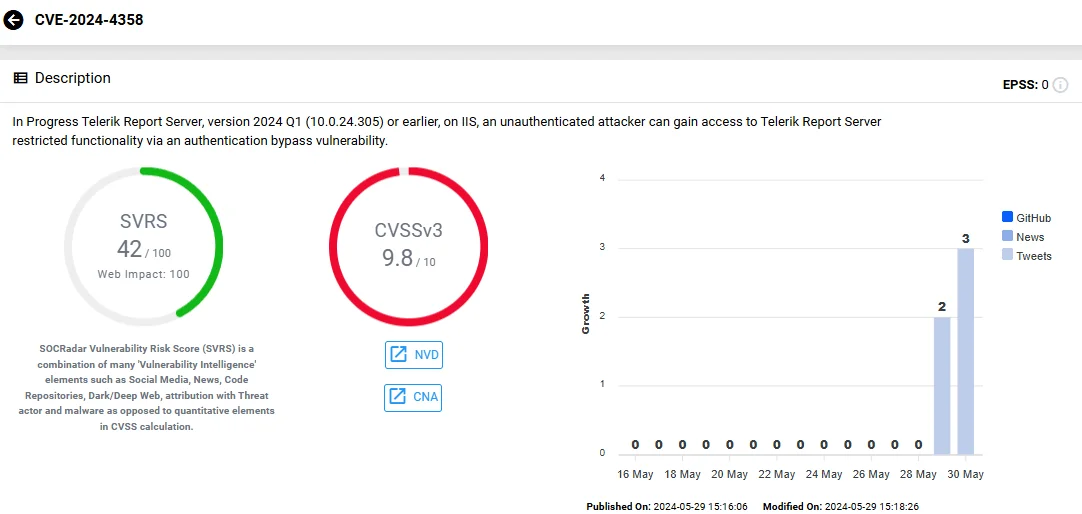
Vulnerability card of CVE-2024-4358 (SOCRadar Vulnerability Intelligence)
Discovered by Sina Kheirkhah of the Summoning Team in partnership with the Trend Micro Zero Day Initiative, this security issue has not yet been reported as exploited in the wild at the time of writing, which provides a window for preventative actions.
Gain insights with SOCRadar’s Vulnerability Intelligence, enhance your organization’s vulnerability management and prioritization, protecting against potential breaches. Using the feature, you can track updates on identified vulnerabilities, including exploits, repositories, and emerging hacker trends.
View the latest CVEs and exploitation trends on SOCRadar’s Vulnerability Intelligence, under the Cyber Threat Intelligence module of SOCRadar XTI
Which versions of Progress Telerik are vulnerable to CVE-2024-4358?
Progress has stated in its advisory that Telerik Report Server versions up to and including 2024 Q1 (10.0.24.305) are affected by the authentication bypass vulnerability.
Furthermore, a ZoomEye search on Telerik Report Server reveals approximately 570 results, most originating from the United States and the United Kingdom. These instances, which have been exposed on the internet, indicate potentially vulnerable systems.
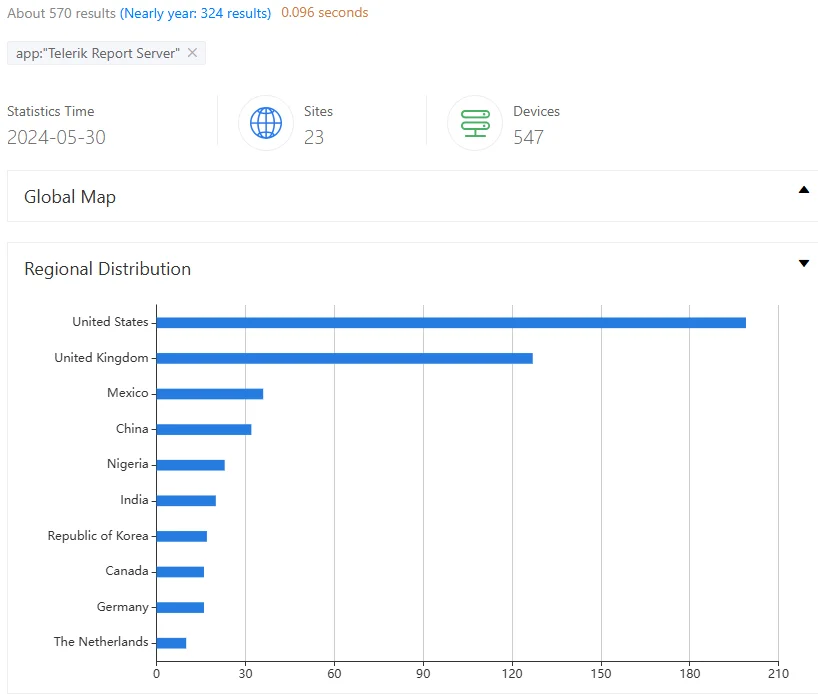
Search results for app:”Telerik Report Server” (ZoomEye)
How to detect the exploitation of CVE-2024-4358? Are there any indicators?
Progress advises administrators to inspect the Report Server’s user list for any unauthorized entries at {host}/Users/Index, which could be an indicator of compromise.
Proof-of-Concept Exploit Available for Critical Telerik Report Server Vulnerability (CVE-2024-4358)
A Proof-of-Concept (PoC) exploit for the critical authentication bypass vulnerability in Telerik Report Server, CVE-2024-4358, is now available. The exploit, written in Python, also chains with a second vulnerability, CVE-2024-1800 (CVSS: 8.8), a deserialization issue in Telerik Report Server, to achieve Remote Code Execution (RCE).
Sina Kheirkhah, the researcher who initially reported the flaw, along with Soroush Dalili, collaborated on developing the exploit. Kheirkhah has also provided a technical write-up detailing the vulnerability’s intricacies and exploitation process.
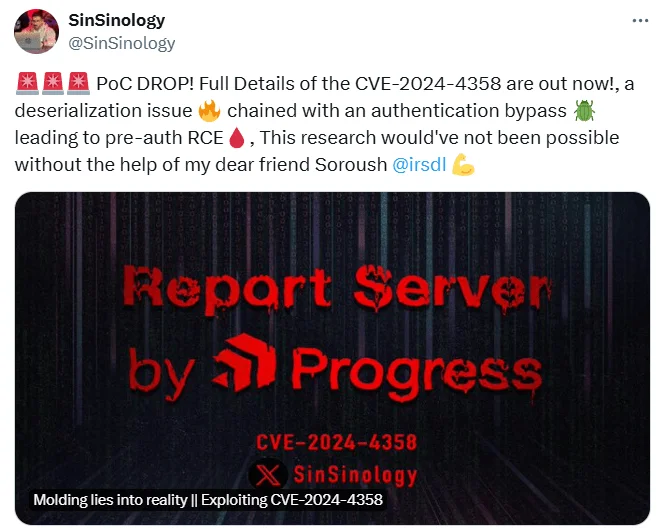
PoC and technical blog announced by researcher @SinSinology on X
The PoC code, available on GitHub, bypasses authentication, creates a backdoor account, and executes arbitrary code on the target server.
Briefly explained, the PoC generates a random username and password to exploit the authentication bypass vulnerability, logs in with the backdoor account, and retrieves an authorization token. It then creates a .trdp file, which is embedded with malicious commands for execution on the target server. This malicious file is uploaded as a new report, triggering the deserialization vulnerability, and allowing RCE.
Although the exploit chain is a bit sophisticated, the public availability of the write-up along with the script increases the risk of real-world attacks, as attackers may soon weaponize it. Administrators are urged to review and apply security patches immediately to prevent exploitation.
CISA Adds CVE-2024-4358 to Known Exploited Vulnerabilities Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2024-4358 to its Known Exploited Vulnerabilities (KEV) Catalog. The agency identifies this critical authentication bypass flaw in Telerik Report Server as a common attack vector posing significant threats to federal enterprises.
CISA mandates that all federal organizations must patch CVE-2024-4358 by the deadline of July 4, 2024, to mitigate potential risks associated with this vulnerability.
How can organizations address CVE-2024-4358?
It is strongly recommended that you upgrade to the latest version, 2024 Q2 (10.1.24.514). The update instructions can be found on the official advisory.
Is there a workaround for CVE-2024-4358?
Progress did not provide any workarounds for Telerik Report Server’s security vulnerability, CVE-2024-4358; the company stated that the only way to address it is to update to Report Server 2024 Q2 (10.1.24.514) or later.
Swiftly respond to emerging vulnerabilities with SOCRadar’s Attack Surface Management (ASM) module. This tool continuously monitors digital assets, providing timely threat alerts and actionable insights, enabling proactive measures to enhance your cybersecurity posture.
The Attack Surface Management module allows you to monitor digital assets and their exposure. On the Company Vulnerabilities page of ASM, you can take quick actions about security vulnerabilities affecting your assets.
In late March 2024, we highlighted another critical Telerik Report Server vulnerability on the SOCRadar blog – a Remote Code Execution (RCE) flaw identified as CVE-2024-1800, which carries a critical CVSS score of 9.9. For more details, you can visit the blog post here.




































