Ransomware Incident Response Checklist for CISOs (Top 10 Essential Actions)
Whether it’s a double-extortion scheme or a network-wide lockdown, how your organization responds to ransomware in the first minutes and hours of an incident can mean the difference between containment and catastrophe.
For CISOs and security leaders, having a clear, actionable roadmap is essential. Below is a step-by-step ransomware response framework. This comprehensive checklist is organized by incident response phase and covers Windows, Linux, Cloud, and ICS/SCADA environments.
Use this structured checklist to ensure no critical step is overlooked during a ransomware incident response. If you have any questions regarding this checklist please send an email to: [email protected]
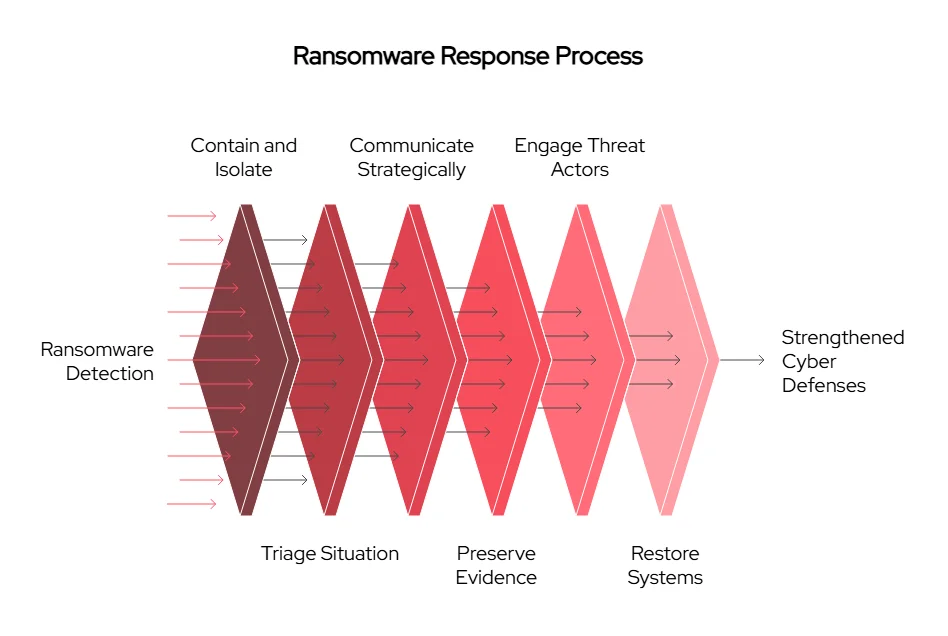
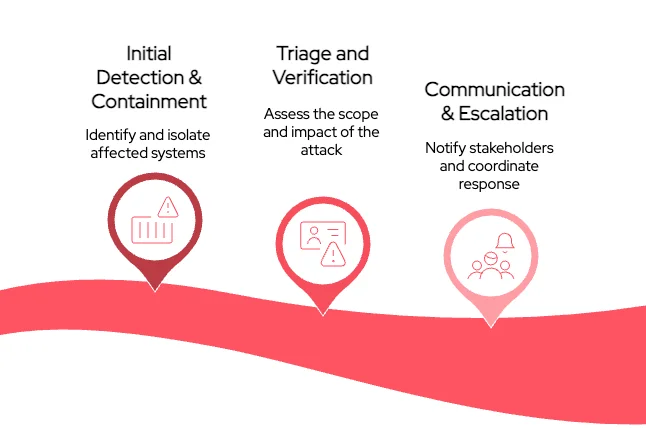
1. Initial Detection and Containment
| Checklist Item | Explanation |
| 1.1 Stay calm and initiate incident response plan | Don’t panic. Keeping a clear head ensures you follow procedures correctly. Begin by activating your incident response plan and assembling the response team. |
| 1.2 Verify the ransomware incident | Confirm the alerts or ransom notes are legitimate and not a false positive. Quick verification prevents unnecessary alarms and triggers the appropriate response if it’s a real attack. |
| 1.3 Isolate affected systems immediately | Disconnect infected computers/servers from the network (unplug Ethernet or disable Wi-Fi) to contain the malware spread. If many systems are impacted, consider temporarily taking whole network segments offline to halt lateral movement. |
| 1.4 Use out-of-band communication for response | Assume the attackers may monitor your network or emails. Coordinate response actions via phone or other out-of-band channels to avoid tipping off the threat actor that they’ve been detected. |
| 1.5 Power down devices only as a last resort | If a device cannot be network-isolated, shut it down to stop further encryption. This preserves remaining data, but do this only if isolation is impossible because power-off wipes volatile evidence. |
| 1.6 Coordinate containment with IT, Cloud, and OT teams | Involve infrastructure teams for each environment. For cloud resources, disable compromised accounts or isolate cloud instances (e.g., remove from load balancers). For ICS/SCADA, work with operations to safely isolate affected OT networks or machines to avoid physical safety issues. This ensures containment across all platforms without causing extra damage. |
| 1.7 Block attacker access routes | Cut off known threat actor paths: e.g., disable VPN accounts or RDP services they used, change compromised passwords, and patch exploited vulnerabilities. This prevents the attacker from reconnecting during the incident. |
The first moment of a ransomware discovery is a stress test. A calm head is as vital as fast reflexes. Activate your organization’s incident response plan immediately and assemble your response team (ideally, these roles are assigned and rehearsed in advance).
Next comes system isolation. Infected devices should be pulled from the network – literally, if needed. Disable Wi-Fi, unplug Ethernet, or cordon off compromised cloud instances. If lateral movement is suspected, you may have to take entire segments offline. It’s a drastic step, but sometimes it is the only way to prevent wider damage.
Since attackers might be monitoring your environment, switch to out-of-band communication:
- Encrypted messaging apps (not on your main network)
- Direct phone calls
- Emergency communication channels (radio or pre-designated apps)
Avoid powering down systems unless you have no other option. Memory-resident forensic data can vanish when you cut the power.
Also, don’t forget infrastructure gaps. Coordinate across IT, cloud, and OT domains. For example, shutting down an ICS machine incorrectly could halt production or trigger a physical safety risk.
2. Triage and Verification
| Checklist Item | Explanation |
| 2.1 Identify the ransomware variant | Determine which ransomware strain is involved (from ransom note or binary). Knowing the variant helps understand the attacker’s tactics and whether decryptors are available, guiding your next steps. |
| 2.2 Determine the initial attack vector | Find out how the ransomware entered (patient zero). Common entry points include phishing emails, exploitation of an exposed service (e.g. RDP), or stolen credentials. This knowledge helps close that entry point (e.g., remove phishing emails enterprise-wide, patch the vulnerability, or reset compromised accounts). |
| 2.3 Assess scope of infection (systems and accounts) | Identify all machines that are encrypted or impacted and any user accounts the attackers compromised. This triage step shows how widespread the incident is and ensures all infected endpoints are contained. Include servers, endpoints, cloud instances, and even OT devices in this assessment. |
| 2.4 Check for active malware or persistence | Determine if any ransomware processes are still running or if backdoors/persistence mechanisms exist on the network. Identifying and killing any leftover malicious processes or scheduled tasks is crucial to prevent reinfection. |
| 2.5 Look for signs of data exfiltration | Many modern ransomware attacks also steal data (“double extortion”). Check network logs for large or unusual outbound transfers, especially to cloud storage or foreign IPs. If data was taken, it elevates the incident to a data breach, requiring additional legal steps. |
| 2.6 Identify critical systems and prioritize | Pinpoint which impacted systems are mission-critical (for business operations, health/safety, etc.). This prioritization guides which systems to focus on first for recovery or further analysis. It also helps in communicating impact (e.g., “ERP server down, finance operations halted”). |
| 2.7 Verify integrity of backups and snapshots | Immediately evaluate if your backups are intact and usable. Attackers often try to delete or encrypt backups; ensure offline or cloud backups weren’t compromised. This verification influences your recovery strategy (restoration vs. negotiation). |
| 2.8 Classify the incident severity | Based on scope and impact, classify the incident (e.g., high severity security incident). A clear classification (per your IR plan or ISO 27001 procedures) ensures proper escalation and resource allocation. For example, a widespread ransomware on servers would be “severe,” invoking full disaster recovery procedures. |
With the infection contained, it’s time to understand what you’re up against. This isn’t just about identifying the malware; it’s about reconstructing the entire event. Start by identifying the ransomware variant. Each variant has unique behaviors and some may even have free decryptors available online. Then ask the hard questions:
- How did the attackers get in? (Phishing, unpatched RDP, compromised credentials)
- How widespread is the infection? (Endpoints, servers, cloud platforms, OT systems)
It’s also essential to assess for ongoing malicious activity. Are there leftover scripts, malicious tasks, or scheduled jobs quietly waiting to re-ignite?
Then, look for signs of data theft, where the ransomware has evolved into double-extortion. Watch for:
- Unusual outbound data flows
- Uploads to unfamiliar cloud destinations
- Data movements to foreign IPs
Backups are another vital checkpoint. Are they intact, unencrypted, and recent enough? If not, recovery just got significantly harder.
Finally, classify the severity of the incident based on:
- Operational impact
- Systems affected
- Data sensitivity
- Potential regulatory exposure
This helps align resources, prioritize recovery, and prepare for external disclosures.
3. Communication and Escalation
| Checklist Item | Explanation |
| 3.1 Notify the internal incident response team and leadership | As soon as ransomware is confirmed, alert your SOC management, CISO, and incident responders. Early communication ensures everyone who needs to know is aware and can mobilize support. Keep senior leaders informed with regular status updates as the situation unfolds. |
| 3.2 Engage legal counsel and executive management | Involve your legal team immediately. They can guide on sensitive communications and regulatory obligations, and their early involvement helps maintain attorney-client privilege over the investigation. Executive leadership should be briefed so they can make high-level decisions (e.g., operational shutdowns, public statements). |
| 3.3 Activate external incident response partners if needed | If you have a retainer with a cyber incident response firm or if your cyber insurance provides experts, call them in promptly. Outside specialists can bring expertise in ransomware forensics and negotiation, helping to contain damage faster. |
| 3.4 Coordinate with IT, security, and OT departments | Ensure IT ops, security teams, and any operational technology teams (for factories, utilities, etc.) are communicating. Actions like shutting down a server or isolating a plant network should be done in coordination to avoid unintended outages or safety issues. A unified communication channel (like a war room call) helps synchronize efforts. |
| 3.5 Craft an internal communication to staff | Inform employees (on a need-to-know basis) about the incident in simple terms, and instruct them on any immediate actions (e.g., “Do not turn off your PC; instead, disconnect from network and leave it for IT,” or “Report any ransom screens to IT”). Controlling the internal message prevents rumors and ensures staff cooperation with response measures. |
| 3.6 Prepare public relations strategy | If a widespread outage or data breach is possible, involve corporate communications/PR to draft holding statements. Decide what will be communicated to customers, partners, or media, balancing transparency with caution. Planning this early ensures accurate information is shared externally if needed and prevents panic. |
A chaotic response invites more chaos. That’s why structured communication is the CISO’s secret weapon.
Start with your internal stakeholders. Alert the SOC team, C-suite, and board-level executives. Establish a single source of truth, such as a virtual war room or secure comms thread, to keep everyone aligned.
Next, engage legal counsel. Their input is vital not just for regulatory compliance, but to protect privileged information during investigations.
If you have cyber insurance, notify your provider promptly. Many insurers offer access to:
- Forensic teams
- Legal support
- Negotiation specialists
- PR consultants
Craft clear, non-technical instructions for employees. Guidance might include:
- Disconnect affected devices from the network
- Do not reboot or power off machines
- Report suspicious behavior or ransom messages to IT immediately
On the external front, loop in your PR team. Prepare holding statements and set expectations around when and how disclosures will be made. Delays and misinformation can damage public trust more than the breach itself.
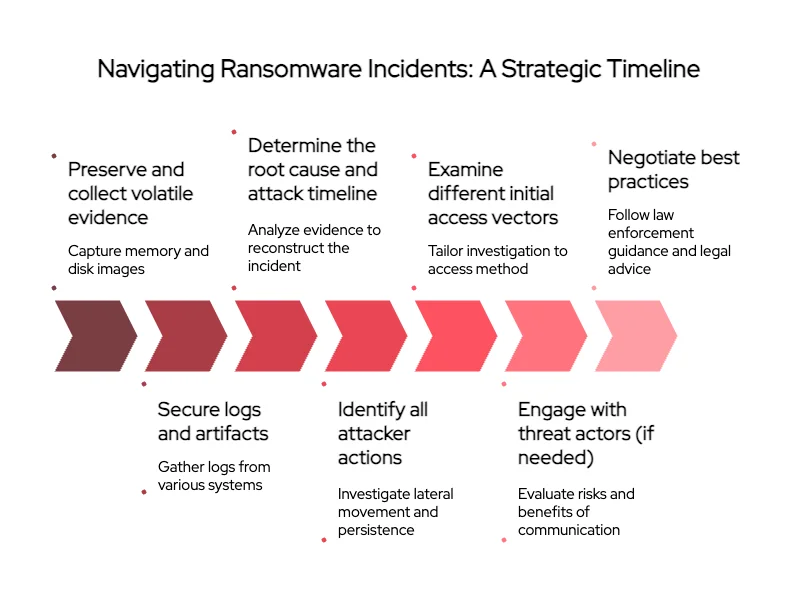
4. Forensics and Root Cause Analysis
| Checklist Item | Explanation |
| 4.1 Preserve and collect volatile evidence | Before systems are reimaged or powered off, capture memory (RAM) and take forensic disk images of representative affected systems. This evidence will help determine how the attack happened and support any legal investigation. Focus on “patient zero” machines and critical servers for deep analysis. |
| 4.2 Secure logs and artifacts | Immediately pull relevant logs from servers, endpoints, network devices, and cloud services (VPN logs, Windows Event Logs, firewall logs, etc.) before they roll over. These logs are vital for timeline analysis and might contain clues like the first malicious login or file encryption events. |
| 4.3 Determine the root cause and attack timeline | Analyze collected evidence to reconstruct the incident: how the attackers entered, what they did before deploying ransomware, and when. Identifying root cause (e.g., a phishing email or unpatched VPN server) is crucial to ensure that exact weakness is remediated and that attackers are fully eradicated. |
| 4.4 Identify all attacker actions (lateral movement, tools) | Investigate how the threat actor moved inside your network: did they use credential theft, RDP, or other exploits? Uncover any backdoors, scripts (like PowerShell or batch files), and persistence mechanisms they installed. This thorough sweep ensures no malware components remain to re-launch the attack. |
| 4.5 Examine different initial access vectors | Tailor the forensic investigation to the suspected access vector. If phishing was involved, analyze the malicious email and any payload or macro. If an RCE (Remote Code Execution) exploit was used, inspect the breached server and identify the vulnerability exploited. If stolen credentials were used (from stealer logs or leaks), review authentication logs for unusual access and determine how those credentials were obtained (and where else they were used). Each vector leaves different evidence that must be examined. |
| 4.6 For ICS/SCADA incidents, involve OT security experts | If industrial control systems are affected, include ICS cybersecurity specialists in the analysis. Check if PLCs or HMIs were compromised or if the ransomware was contained to Windows workstations in the plant. Review ICS network logs or historian data for anomalies. Understanding the impact on physical processes is key in root cause analysis for OT environments. |
Before you wipe, reimage, or restore anything, preserve the evidence. This data is your blueprint for understanding the breach and your lifeline for any legal or insurance claims.
Start with memory captures and disk images from infected systems – especially the initial point of compromise. Then gather logs from:
- Firewalls and network appliances
- Endpoint monitoring tools
- VPN and cloud infrastructure
Once collected, use the data to reconstruct:
- Initial point of entry
- Timeline of attacker movement
- Data accessed or exfiltrated
- Persistence methods used
Be especially alert for lateral movement techniques – did the attacker use RDP, stolen credentials, or tools like PsExec?
In ICS or SCADA environments, bring in OT cybersecurity professionals to analyze potential impacts on physical systems. Was a PLC modified? Did the HMI show unusual behavior? Even if the attack stayed in IT territory, you need to be sure.
5. Threat Actor Engagement (If Needed)
| Checklist Item | Explanation |
| 5.1 Decide whether to establish contact with attackers | Evaluate the benefits and risks of communicating with the ransomware actors. In some cases, engaging can buy time or yield information (such as proof of data theft), but it also carries risk. Only proceed if it aligns with your crisis strategy and legal advice; never feel forced to respond to the criminals. |
| 5.2 Use designated secure channels for communication | If you engage, use the method the attackers provided (often a dark web portal or encrypted chat). Do not use company email or personal accounts, to protect your identity. Maintain anonymity and avoid revealing any sensitive info about your organization during the conversation. |
| 5.3 Request proof or details (if data exfiltration is claimed) | If the attackers claim to have stolen data, consider asking for a small sample of the data as proof. This helps verify their claims (e.g., confirming if personal data is involved) and can guide your legal response. Be cautious not to provide any files to them unless necessary. |
| 5.4 Keep communications professional and limited | Interact in a calm, business-like manner. Do not antagonize the threat actors with emotional or accusatory language. Every message should be carefully crafted, as anything you say could provoke them or be used later. The goal is to gather information and assess their demands, not to negotiate immediately. |
| 5.5 Engage a negotiation specialist if considering dialogue | If your organization decides to enter extended communication or negotiation, involve experienced ransomware negotiators or incident responders who have handled threat actor communications. They understand criminal tactics and can avoid pitfalls, increasing the chance of a favorable outcome (or at least preventing the situation from worsening). |
Engaging with ransomware operators is a risky business – and should only be done under legal counsel and with a clear strategic goal. Typically, that goal is to buy time or validate the attackers’ claims, not to negotiate immediately.
If engagement is required, always:
- Use the secure channel the attacker provided (often a TOR-based portal)
- Maintain complete anonymity
- Avoid confirming your identity, and capabilities, or even that you’re considering payment
Ask for a sample decryption or proof of exfiltrated data. If the threat actor refuses, they may be bluffing.
Keep interactions professional, calm, and brief. Do not make threats, and do not offer information they can exploit. For extended conversations, bring in a negotiation specialist who’s familiar with cyber extortion tactics.
6. Negotiation Best Practices
| Checklist Item | Explanation |
| 6.1 Follow law enforcement guidance (do not pay if possible) | Know that the FBI, CISA, and Europol strongly discourage paying ransoms. Paying is no guarantee of data return and may encourage further attacks. Make the decision carefully with executive and legal counsel input – and explore all other recovery options first. |
| 6.2 If negotiating, use a trained negotiator or third-party | Ransomware negotiation is delicate. Assign a professional (often provided via cyber insurance or IR firms) to handle discussions. They know how to communicate without making costly mistakes, and can try to reduce the ransom or get more time. |
| 6.3 Do not reveal financial or insurance details | Never let the attackers know if you have cyber insurance or large cash reserves. If they sense you have the means to pay a big sum (especially via insurance), they may refuse to lower the demand. Pretend resources are very limited to aim for a smaller settlement. |
| 6.4 Ask for extended time and a small test decryption | It’s wise to stall for time under some pretext (e.g., needing management approval) – this gives you breathing room to work on recovery. If you are considering payment, first ask the attackers to decrypt one or two files as a show of good faith. This tests whether their decryption key actually works before you send any money. |
| 6.5 Never pay full ransom upfront without validation | If ultimately agreeing to pay, avoid paying the entire amount in one go. Negotiate to pay a portion only after you receive a working decryptor. This way you ensure they deliver a functional key before sending the remainder. Always use a secure escrow or payment method as advised by your negotiator. |
| 6.6 Check sanctions and legal restrictions before paying | Before any payment, verify that the threat group isn’t on a sanctions list. Paying a sanctioned entity could be illegal (e.g., violating OFAC rules in the US). Consult with legal counsel on this matter; you may need to get government clearance or refrain from paying to avoid severe penalties. |
There’s no easy answer to the question, “Should we pay?” The default advice from law enforcement is clear: Don’t. Payment encourages future attacks and carries legal risks – especially if the threat actor is under sanctions.
But some organizations, faced with operational paralysis or irreplaceable data loss, may choose to explore payment. If you go down this path:
- Avoid revealing your cyber insurance coverage or financial resources
- Ask for a test decryption
- Negotiate a staged payment (never pay the full amount upfront)
Always consult legal counsel and check if the attacker’s group is listed under international sanctions. Violating OFAC regulations or similar laws can lead to severe penalties – even jail time for executives.
Payment should be a last resort, not a shortcut to recovery.
7. Legal and Compliance Checks
| Checklist Item | Explanation |
| 7.1 Consult legal counsel on regulatory obligations | Engage your legal team early to identify which laws and regulations apply. They will determine if personal data is involved (triggering privacy breach notifications), or if industry-specific rules (like HIPAA for health data or PCI DSS for card data) come into play. This ensures you fulfill all legal duties. |
| 7.2 Assess GDPR implications (EU) | If any personal data of EU residents is affected (encrypted, stolen, or inaccessible), treat it as a potential personal data breach. Under GDPR, even losing access to personal data (availability loss) counts as a breach. You likely must notify the relevant Data Protection Authority within 72 hours of becoming aware of the breach, unless you can demonstrate a low risk to individuals. |
| 7.3 Check NIS2 / critical infrastructure reporting | If you are in the EU and your organization is an essential or important entity (e.g., critical infrastructure, per NIS2 Directive), a ransomware incident might require rapid reporting. NIS2 mandates an initial notice within 24 hours and a detailed incident report within 72 hours to the national CSIRT or authority. Ensure compliance with these timelines to avoid penalties. |
| 7.4 Verify OFAC and sanctions status (US) | Determine if the ransomware group is a known sanctioned entity (the ransom note or variant might hint at the group’s identity). The U.S. OFAC sanction list prohibits paying certain groups; violating this can lead to serious legal consequences. If the threat actor is on a sanctions list, work closely with legal counsel and authorities on how to proceed (usually, not paying and informing law enforcement). |
| 7.5 Document all decisions and rationales | Keep a detailed log of all actions taken, decisions made, and the reasoning behind them. This documentation is important for demonstrating compliance with frameworks like ISO 27001 and could be needed for legal evidence. For example, if you decide not to notify a regulator, record why it was not legally required; if you did notify, record when and how. |
| 7.6 Ensure contract and insurance compliance | Review your contractual obligations and insurance policy. Some contracts with clients may require you to inform them of security incidents. Your cyber insurance policy might also require timely notice (and the use of specific vendors). Following these terms is not only legally required but also ensures you don’t inadvertently void insurance coverage. |
In the aftermath of an attack, your legal exposure extends far beyond your own systems. Every regulation, from GDPR to NIS2 to HIPAA, comes with its own notification requirements and timelines.
Begin with internal legal counsel to determine:
- Was personal data affected?
- Was data exfiltrated?
- Do you fall under critical infrastructure rules?
For EU entities, GDPR requires breach notifications within 72 hours. NIS2 mandates a report to the national CSIRT within 24 hours for essential services.
In the U.S., if healthcare data is involved, HIPAA requires a report to HHS/OCR within 60 days. Public companies may also need to file incident disclosures with the SEC.
Maintain detailed logs of:
- Every decision made
- Why it was made
- Who was involved
Also, review your client contracts and service-level agreements. Some may require partner disclosures even if no regulation demands it.
8. Insurance Notification and Cooperation
| Checklist Item | Explanation |
| 8.1 Notify your cyber insurance provider immediately | If you have cyber insurance, report the incident as soon as possible via the insurer’s 24/7 breach hotline. Prompt notification is usually required by the policy and kicks off support services. Delaying could jeopardize coverage. |
| 8.2 Follow the insurer’s guidelines and panel vendors | Insurance companies often have a panel of preferred incident responders, forensic firms, and negotiators. Use the experts they recommend or provide (as the policy stipulates). This ensures costs are covered and you benefit from experienced professionals (e.g., legal counsel, forensics, PR specialists) arranged by the insurer. |
| 8.3 Provide necessary information to the insurer | Work with the insurance adjusters and calmly give them the facts of the incident (when detected, what’s impacted, initial actions taken). They may require details to approve certain expenses or to engage their experts. Be truthful and thorough; incomplete information could lead to disputes later. |
| 8.4 Understand coverage for ransom payments and response costs | Review your policy to know what is covered: e.g., restoration costs, business interruption, ransom payments, public relations, regulatory fines, etc. This helps in decision-making. For instance, if ransom payments are covered but require insurer approval, do not pay until you have that clearance. Knowing the financial coverage lets you plan the recovery budget and negotiation strategy accordingly. |
| 8.5 Cooperate with insurance investigations | The insurer may conduct its own investigation or require a formal incident report. Cooperate fully, providing forensic reports or system images if requested. This can speed up claims processing. Remember that insurance-funded teams are there to help, but also document everything for the claim record. |
If you’ve invested in cyber insurance, now is the time to use it – not just for financial recovery, but for professional support. Call your provider as soon as the incident is verified. Most policies require near-immediate notification.
Insurers often provide:
- Incident response vendors
- Negotiation teams
- Legal counsel
- PR crisis management
Use only approved vendors to ensure coverage isn’t voided. Keep your provider updated as events unfold and ask for clarification on:
- What is covered (e.g., ransom, business interruption, regulatory fines)
- Claim filing requirements
- Documentation needed
Be proactive, clear, and thorough. The more organized your side is, the faster claims will process.
9. Decryption, Recovery and Reconstitution
| Checklist Item | Explanation |
| 9.1 Check for available decryptors or keys | Before considering paying a ransom, research if a free decryptor exists. Law enforcement and security researchers have cracked certain ransomware strains. Consult resources like the No More Ransom project or FBI – you might recover data without payment if the variant is known and decryptable. |
| 9.2 Obtain and test the decryption tool (if paying or provided) | If you receive a decryption program (either from paying the ransom or from law enforcement), first test it on a small subset of encrypted files in an isolated environment. This ensures the tool works and doesn’t contain additional malware. Verifying samples protects from a faulty decryptor that could corrupt data further. |
| 9.3 Restore from clean backups where possible | For systems where you have safe backups, prefer restoring from backup over decryption. Wipe the affected machines and rebuild them, then recover data from backups. This guarantees a clean start. Ensure the backups are malware-free by scanning them before restoration, since attackers might have planted malware in the backup if they had long-term access. |
| 9.4 Decryption process for unrecoverable systems | For systems without backups, you may proceed with decryption using the provided key/tool after testing. Decrypt systematically, starting with the most critical systems. Monitor the process closely in case of issues. Keep copies of the encrypted data separately, just in case the decryptor damages some files and you need to try again. |
| 9.5 Gradual network reintegration | As each system is decrypted or restored, do not immediately connect it back to the production network before ensuring it’s clean. Patch the system, change all passwords on it, and verify no attacker footholds (like new user accounts or scheduled tasks) remain. In ICS environments, bring machines back up in a controlled manner to avoid surges or unsafe conditions in industrial processes. |
| 9.6 Conduct thorough malware scans on recovered systems | Use up-to-date antivirus/EDR tools to scan every restored or decrypted system. The goal is to catch any leftover malware such as rootkits or trojans that the attackers may have left (e.g., they sometimes leave backdoor accounts or tools for future access). Only when a system is verified clean should it be considered fully restored. |
| 9.7 Validate data integrity and completeness | After recovery, verify that critical applications and data are functioning correctly. Check databases for corruption, ensure files open properly, and that all essential services are running. If any data was irretrievably lost, plan how to rebuild it or communicate the loss. This step ensures you actually have a working environment and not just decrypted files. |
| 9.8 Preserve evidence before wiping systems | Before wiping or reimaging any compromised system for reconstitution, ensure you have saved forensic images and logs (from Step 4). This preserves evidence for any future investigation or legal action. Once preserved, you can safely rebuild systems knowing you can refer to the evidence later if needed. |
Once you’ve analyzed, contained, and preserved evidence, recovery can begin – but tread carefully.
Start by checking for available decryptors from law enforcement or threat intel platforms. If you use one, test it in a sandbox before rolling it out network-wide.
Where possible, rebuild from clean backups:
- Wipe infected systems
- Reimage using gold-standard images
- Scan backups for dormant malware before restoring
If decryptors are your only option, decrypt in stages – starting with high-priority systems. Validate the output, check for corruption, and monitor for anomalies.
Before reconnecting any machine to the network:
- Patch vulnerabilities
- Change all system and domain passwords
- Scan thoroughly for persistence
And always, always preserve evidence from each restored system before wiping – just in case future legal action or internal review requires it.
10. Internal and External Reporting
| Checklist Item | Explanation |
| 10.1 Report the incident to law enforcement | Inform appropriate law enforcement agencies early (for instance, in the US contact your local FBI field office or CISA; in the EU, law enforcement via your national CSIRT). Reporting can help authorities track ransomware gangs and might provide you with assistance or intelligence. It’s often seen as a positive compliance step too, and in some jurisdictions, it’s strongly encouraged or even required. |
| 10.2 Notify regulators and authorities as required | If personal data was compromised, file a breach notification to your data protection authority (e.g., GDPR 72-hour notification rule). If you’re in a regulated industry (finance, healthcare, energy), you may need to notify sector regulators or oversight bodies. For example, healthcare organizations in the US must notify HHS/OCR within 60 days if the PHI of more than 500 individuals was breached. Timely notification avoids legal penalties. |
| 10.3 Consider obligations to inform customers/partners | Based on the incident’s impact, decide if you need to directly notify affected customers or third-party partners. If attackers stole data, you may have a legal duty to inform those individuals (e.g., data breach notification letters). Even if not legally required, transparency with key business partners can maintain trust – better they hear it from you than in the news. |
| 10.4 Prepare an executive summary report for management | Internally, document the incident in a formal report for senior management and the board. Include what happened, how it was contained, impact on operations, data loss, financial costs, and next steps. This report not only keeps leadership informed but is also useful for insurance claims and for refining future security strategies. |
| 10.5 File insurance claims and required documentation | Work with your insurance to formally report the full details of the incident (often they require a written report or questionnaire). Include the who-what-when-how of the attack and all expenses incurred. Prompt and accurate reporting to insurance ensures you can recover costs under the policy. |
| 10.6 Share Indicators of Compromise (IOCs) with the community | Once the immediate crisis is managed, consider sharing anonymized technical details of the attack with information-sharing groups (like MS-ISAC, ISACs for your sector, or through CISA). By sharing IOCs (malicious IPs, hashes of malware, etc.), you help others in the community bolster their defenses, and it contributes to the collective effort against the ransomware group. |
| 10.7 Meet any other jurisdictional reporting duties | If your company is multinational, ensure compliance in each relevant country (e.g., some countries require notifying a CERT or law enforcement separate from GDPR). Public companies may also have to disclose the incident in financial filings (the SEC in the US now requires 8-K disclosure of material cyber incidents). Work with legal to cover all bases, so no required report is missed. |
The crisis may be over, but the responsibility isn’t. Your final step is thorough and transparent reporting – internally and externally.
Report the attack to law enforcement and, if applicable, your national CERT or sectoral regulator. These reports not only fulfill legal duties – they help authorities track ransomware gangs and may provide threat intelligence in return.
Disclose incidents to customers or partners when necessary. Even if not legally required, proactive communication builds long-term trust.
Internally, prepare an executive-level incident summary covering:
- What happened
- Business impact
- Response timeline
- Recovery outcomes
- Next steps
File insurance claims promptly and submit all required documentation. And don’t forget to share anonymized IOCs with peers or industry groups. Collective security is a shared responsibility.
Bonus: Post-Incident Review and Hardening
| Checklist Item | Explanation |
| 11.1 Conduct a “lessons learned” debrief | Hold a post-incident review meeting with all involved teams (technical, management, legal, etc.) as soon as possible after recovery. Discuss what went well and what didn’t. This honest assessment identifies gaps in your plan and opportunities to improve response next time. |
| 11.2 Identify security control failures or gaps | Determine how the ransomware bypassed defenses. For example, was a critical server missing patches? Did the SOC miss detection signs? Was MFA not enabled on VPN? List these shortcomings. They highlight where your security needs strengthening (be it technology, processes, or training). |
| 11.3 Improve and update the incident response plan | Update your IR plan and playbooks based on the lessons learned. If communication channels were unclear or a step was missed, adjust the plan. Incorporate new checklists or tools that proved useful. Ensure the plan addresses all environments (cloud, on-prem, OT) effectively, and align it with standards like ISO 27001’s continuous improvement requirement. |
| 11.4 Implement security enhancements (hardening) | Take corrective actions to prevent a repeat. This may include: patching all systems that were vulnerable, increasing network segmentation (especially isolating OT networks from IT), deploying better endpoint protection, improving monitoring (EDR, IDS) to catch lateral movement, and requiring multi-factor authentication everywhere. The goal is to close the gaps identified in step 11.2. |
| 11.5 Strengthen backups and recovery capabilities | Ransomware underscores the importance of robust backups. If backups failed or were insufficient, invest in a more resilient backup strategy (e.g., offline backups, immutable storage). Also, regularly test restoring from backups during drills. Ensuring you can recover quickly in the future reduces the temptation to ever pay a ransom. |
| 11.6 Train and awareness to address human factors | If the incident started via phishing, use it as a teachable moment to improve security awareness training. Educate staff on recognizing suspicious emails or other social engineering. Likewise, train admins on better privilege management if credential abuse was a factor. Human errors can be reduced with ongoing education and simulation exercises. |
| 11.7 Document the incident in the risk register | Finally, record the incident and its outcomes in your organization’s risk management or incident tracking system. Update risk assessments to reflect the new insights (e.g., “ransomware risk” likelihood or impact might be adjusted). This ensures executives and the board understand the incident’s impact and that it’s accounted for in future risk mitigation planning. |
Every incident is a learning opportunity – if you take it seriously.
Host a cross-functional post-mortem. Invite IT, security, legal, comms, operations. Document what worked, what failed, and what must improve.
Focus on:
- Missed detection opportunities
- Control failures (e.g., lack of MFA, poor segmentation)
- Communication breakdowns
- Policy or playbook gaps
Then invest in your future defenses:
- Patch and segment aggressively
- Upgrade endpoint and cloud monitoring
- Strengthen backups with offline and immutable solutions
- Educate employees through phishing simulations and real-world exercises
Finally, log the incident in your enterprise risk register. Use it to shape security budgets, strategy sessions, and board conversations going forward.
Closing Thought: Discover and Defend with SOCRadar Ransomware Intelligence
Ransomware attacks are inevitable, but damage isn’t. A CISO-led, cross-functional response that is fast, smart, and thorough can protect your organization’s operations, reputation, and legal standing.
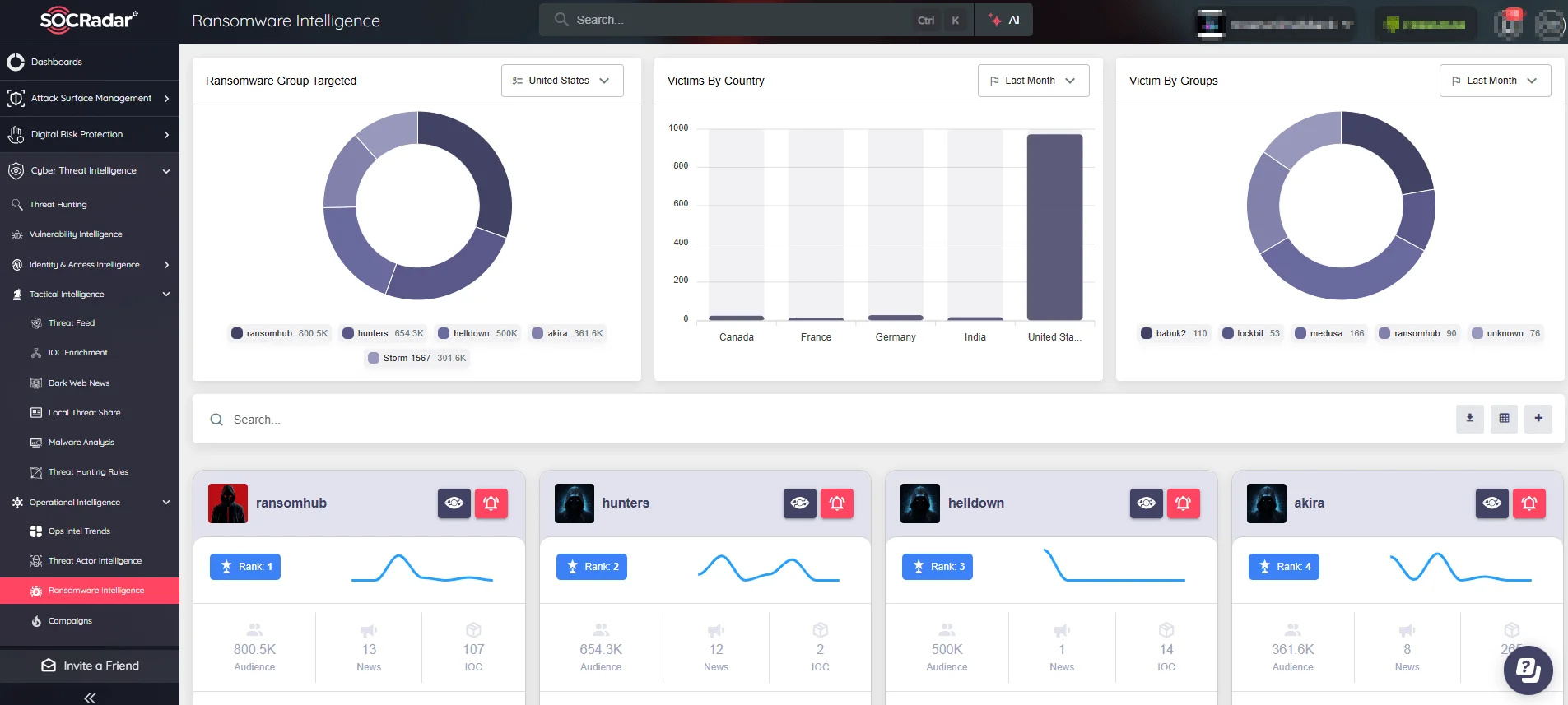
SOCRadar’s Ransomware Intelligence module offers real-time visibility into ransomware groups, their victims, and attack trends across the globe. With intuitive dashboards and threat insights, security teams can monitor adversary movements, identify targeted industries, and prioritize defenses with precision.
From understanding the top groups like RansomHub and Hunters, to tracking victim distribution across geographies, SOCRadar gives you the intelligence edge.
Stay ahead of evolving ransomware threats – visualize, prioritize, and respond effectively with SOCRadar.