
Reports of ProxyNotShell Vulnerabilities Being Actively Exploited (CVE-2022-41040 and CVE-2022-41082)
According to reports, the zero-day vulnerabilities CVE-2022-41040 and CVE-2022-41082, dubbed ProxyNotShell, are still being actively exploited.
Researchers published proof-of-concept (PoC) details after Microsoft patched the vulnerabilities in October Patch Tuesday. Since the patch, the attackers still target vulnerable MS Exchange Server builds such as MS Exchange Server 2013, MS Exchange Server 2016, and MS Exchange Server 2019 with the exploit. Microsoft strongly recommends updating MS Exchange Server instances to prevent ProxyNotShell exploits.
The vulnerabilities, collectively known as ProxyNotShell, can be used in a chain exploit; an attacker could use CVE-2022-41040, a server-side request forgery (SSRF) vulnerability, to become able to exploit the next vulnerability, CVE-2022-41082.
In August, threat actors exploited the vulnerabilities in an attack on critical infrastructure.
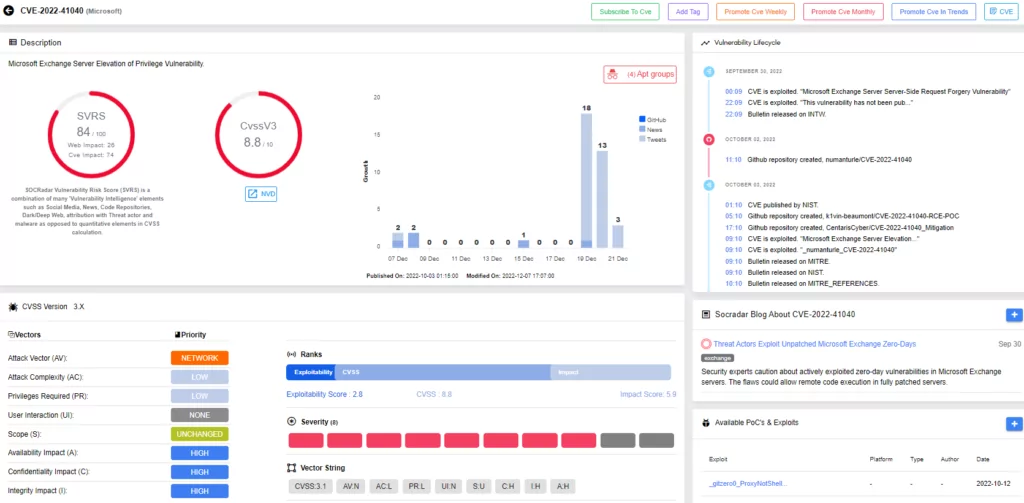
How Is It Exploited?
Attackers initially used CVE-2022-41040 to gain access to the PowerShell API endpoint (https://%exchange server domain%/powershell). An attacker with a known credential combination for a registered account can use this access to execute PowerShell commands in the Exchange environment.
The attacker must then use the WSMAN Protocol to gain access to the Web-Based Enterprise Management (WBEM) and launch shell for further script execution via Windows Remote Management (PsRemoting).
Additionally, the attacker immediately sends a special request through WSMAN to enable the keep-alive option, which extends the shell’s lifetime.
Eventually, CVE-2022-41082 can be exploited using PowerShell Remoting to send a request that passes encoded and serialized data with a special payload as a parameter. This spawns an object of the System.Windows.Markup.XamlReader class to create a new object of the System.Diagnostics class, and contains a method call to start new processes.
Post-Exploitation Activities
After ProxyNotShell was successfully exploited in the wild, post-exploitation activities included hijack attempts, reconnaissance of users, groups, and domains, remote process injection, reverse shell deployment, and obtaining persistence.
The attacker was able to exploit the company’s Exchange Server and generate processes on the system to pass payloads because they had the necessary credentials to carry out the attack.
All processes launched through exploitation have the main parent process with specific parameters: w3wp[.]exe -ap “msexchangepowershellapppool.”
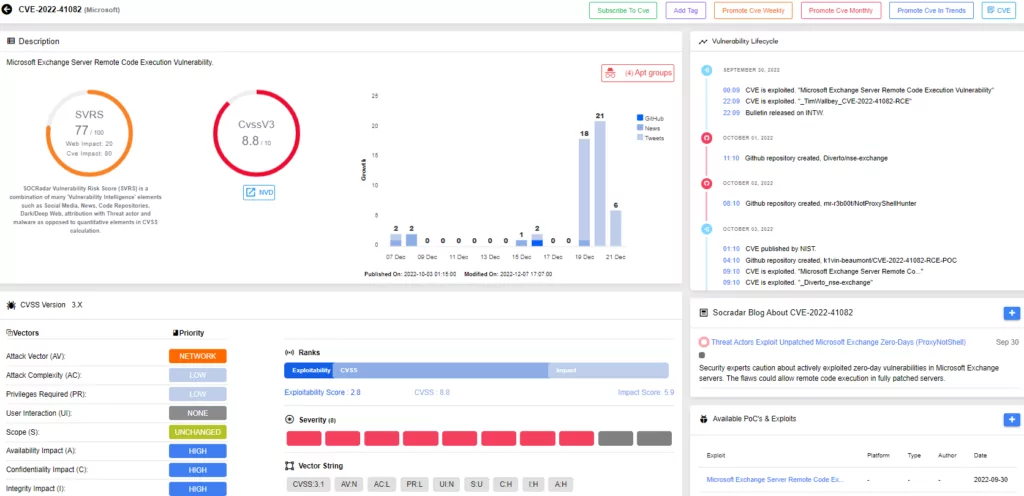
Play Ransomware Gang Breaches Servers Using a New Microsoft Exchange Exploit
Researchers discovered a new exploit technique (called OWASSRF) that uses CVE-2022-41080 and CVE-2022-41082 to allow remote code execution (RCE) through Outlook Web Access (OWA).
The ransomware operators used Remote PowerShell to execute arbitrary commands on infected servers to take advantage of the CVE-2022-41082 vulnerability, which ProxyNotShell also exploited.
In response to ProxyNotShell, Microsoft provided URL rewrite mitigations for the Autodiscover endpoint, but the new exploit technique bypasses it.
According to researchers who reviewed relevant logs, there was no proof that threat actors used CVE-2022-41040 to gain initial access.
Instead, related requests seemed to be sent straight through the Outlook Web Application (OWA) endpoint, which suggests a previously unreported Exchange exploit technique.
While ProxyNotShell exploits target CVE-2022-41040, it is discovered that the vulnerability used by the recently discovered exploit is probably CVE-2022-41080, a security vulnerability Microsoft classified as critical but which has not yet been used in the wild that allows remote privilege escalation on Exchange servers.
OWASSRF PoC Exploit Leaked
Threat researcher Dray Agha discovered and leaked online tooling for a threat actor. A proof-of-concept (PoC) for Play’s Exchange exploit was included in the leaked tooling, enabling CrowdStrike to replicate the malicious activity logged in Play ransomware‘s attacks.
CrowdStrike thinks the proof-of-concept exploit was used to install remote access programs like Plink and AnyDesk on infected servers.
Additionally, BleepingComputer discovered that the ConnectWise remote administration program was present in the Agha-leaked toolkit and probably used in attacks.
Applying the most recent Exchange security updates or disabling OWA until you can apply the CVE-2022-41080 patch are recommended for businesses with on-premises Microsoft Exchange servers on their network.
IoCs
|
F77E55FD56FDAD21766CAA9C896734E9 |
LockDown.dll |
Malware hijack library |
Trojan.Win64.Dllhijacker |
|
F9322EAD69300501356B13D751165DAA |
mfeann.exe |
Dropped vulnerable binary for DLL hijack |
PDM:Exploit.Win32.Generic |
|
A2FAE32F116870E5A94B5FAB50A1CB71 |
Svchosts.exe |
Malware reverse proxy |
Trojan.Win64.Agent.qwibok |
|
47A0814408210E6FCA502B3799B3952B |
Glib-2.0.dll |
Malware hijack library |
Trojan.Win64.Dllhijacker |
|
379F87DAA6A23400ADF19C1CDD6B0DC9 |
vmwarexferlogs.exe |
Dropped vulnerable binary for DLL hijack |
PDM:Exploit.Win32.Generic |
|
193.149.185.52:443 |
С2 server |
||
|
sync.service.auzreservices.com |
С2 server |
||




































