
Salesforce Credentials Leak, Admin, and Webshell Access Sales, Partnership Announcements
We are experiencing a period in which threat actors are increasingly outsourcing and growing the cybercrime network. SOCRadar researchers have previously addressed these issues in their initial access and vulnerability brokers articles. The larger this network, the easier attackers can gain access or information to form the basis for future attacks.
Last week, the most notable data leak on the dark web was sharing credentials allegedly belonging to Salesforce customers. Another issue was the sharing of a threat actor that could buy any kind of military, political, or technology-related documents from around the world. The threat actor also stated they could pay for an insider linked to the US military.
Read on for this and other dark web threads.
Find out if your data has been exposed.
Customer Credentials of Salesforce are Leaked
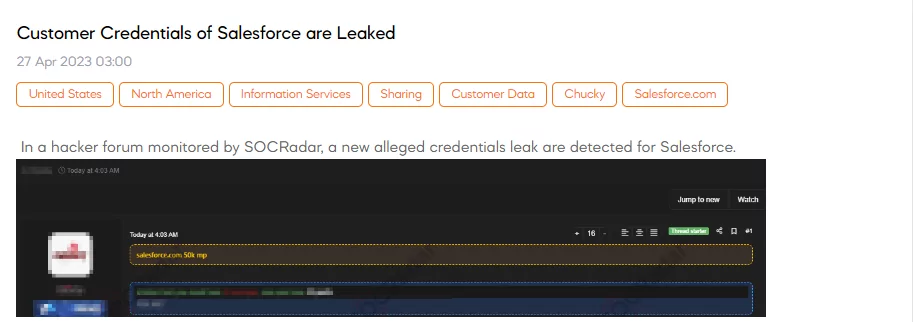
On April 27, a SOCRadar dark web analyst detected a post that a threat actor claimed to have leaked data allegedly belonging to Salesforce customers. The dark web analyst’s first investigation of the leaked data revealed that some credentials matched those shared on the same forum in a previous post. This suggests that the threat actor might have partially reused or combined older data with potentially new compromised customer information.
Document Purchasing Announcement is Detected for Any Politics, Military, and Technology
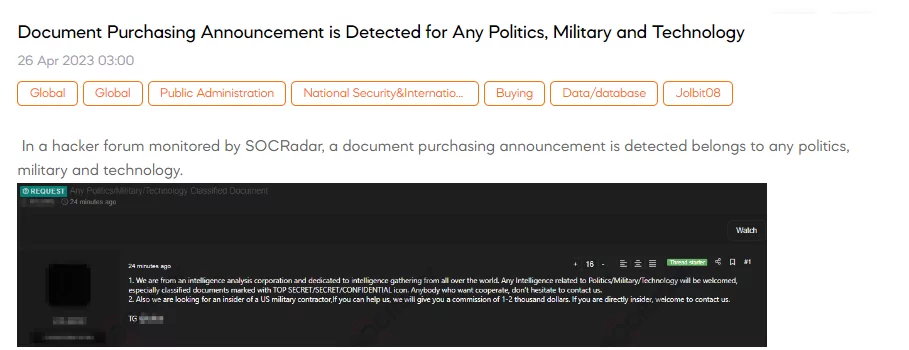
SOCRadar detected a threat actor’s announcement seeking various political, military, and technology-related documents. The threat actor, claiming to be from an intelligence analysis company, expressed a keen interest in obtaining intelligence from across the globe, mainly classified documents marked as top secret, confidential, or restricted. They invited anyone interested in cooperation to contact them. Additionally, the threat actor was searching for an insider within a U.S. military contractor, offering a commission of $1,000 to $2,000 for assistance. They urged direct insiders to reach out to establish contact.
Unauthorized Webshell Accesses Sale is Detected for Many Companies
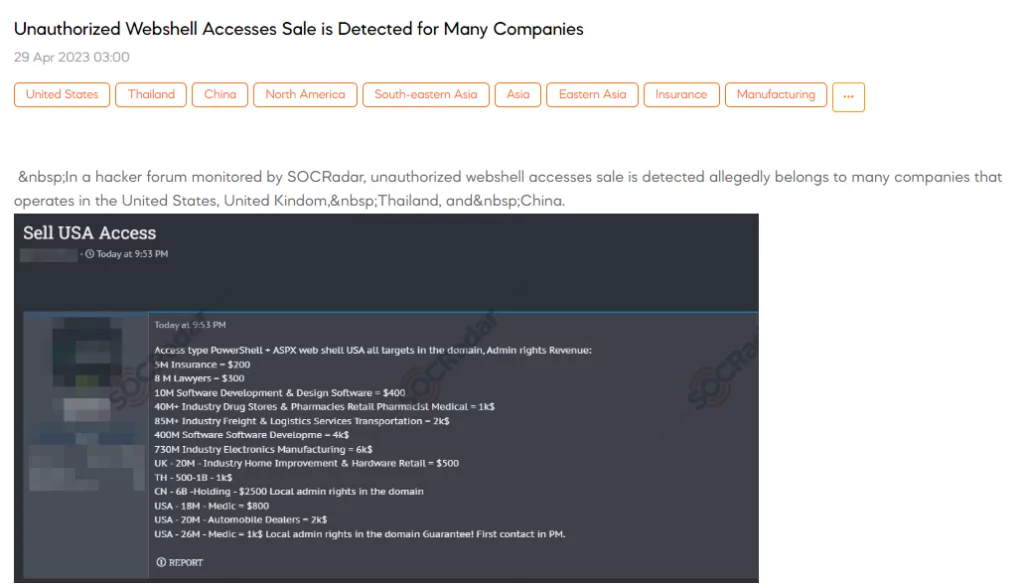
A SOCRadar researcher discovered a forum post advertising unauthorized access to various companies in the United States, United Kingdom, Thailand, and China. The access is achieved through a combination of PowerShell and ASPX web shells, with varying levels of access and associated prices based on the revenue of the target companies. Targets include industries such as insurance, law, software development, drug stores, logistics services, electronics manufacturing, and more. Prices for access range from $200 to $6k, with one target company in China requiring a fee of $2500 for local admin rights in the domain. The group offers a guarantee and instructs interested parties to make first contact in a private message.
Partnership Searching Thread for Hacking Site is Detected
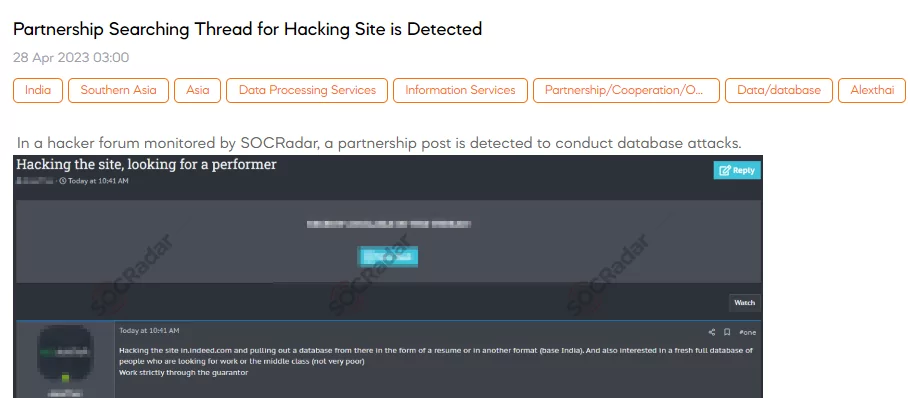
SOCRadar dark web team discovered a post on a hacker forum seeking a partnership to carry out database attacks. The post mentions targeting a site to extract a database through resumes or another format from India. The poster is also interested in obtaining a new, complete database of individuals seeking work or in the middle class.
Unauthorized Admin Access Sale is Detected for an Emirati E-Commerce Company
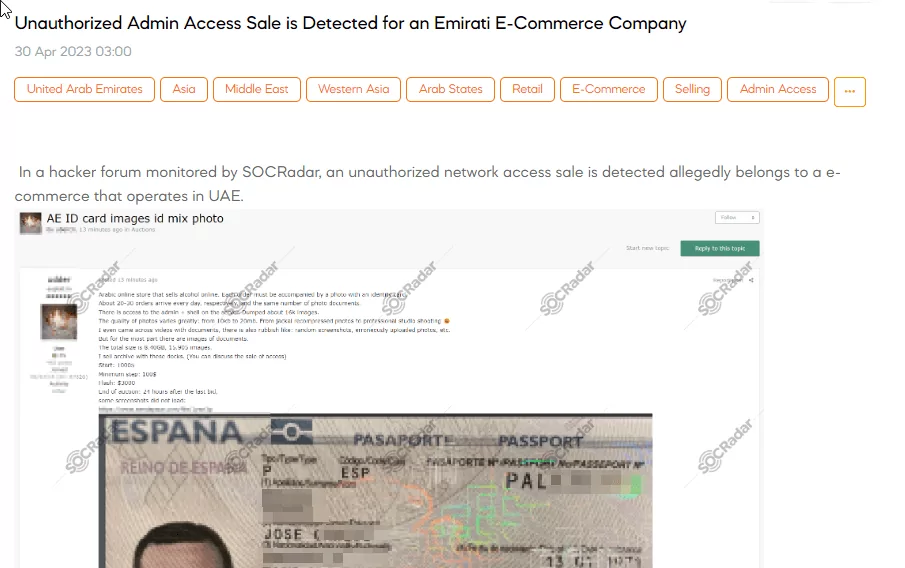
SOCRadar dark web analysts detected a post that a threat actor claimed to have unauthorized administrative access for sale to an e-commerce company in the United Arab Emirates. The company, which specializes in selling alcohol and requires customers to submit I.D. card photos with every order, allegedly had its server accessed with administrative and shell access. According to the post, the attacker obtained around 16,000 images, including professional studio shots, recompressed photos, and even some videos with accompanying documents, with the majority being documented. The post offers an archive of these documents for sale, with a starting price of $1000 and a minimum step of $100.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































