What Happens on the Shadowy Lands of Vulnerability Brokers
In the ever-growing world ofcybersecurity, vulnerability brokers have gained enough voice to be recognized as essential actors in the space. These actors can be anonymous individuals or well-known organizations specializing in identifying and purchasing vulnerabilities or exploits from potential sellers. These vulnerabilities, most of the time, are zero-day vulnerabilities.
After the purchase, they can sell or share these vulnerabilities or exploits with vendors or third parties with other intentions, such as government agencies, security firms, or even criminal organizations. Because of this situation, the ecosystem is sometimes considered a gray market landscape.
Trading valuable vulnerabilities has been ongoing for decades, but their place in cyberspace has progressed. The activity surrounding exposure brokering was not as active as today back in the time. It mostly started with a threat intelligence company called iDefense offering mere pennies for vulnerabilities compared to the amounts being paid now.
Most of the time, when a vulnerability was found, disclosure would have been made to the vendors. However, with the increasing value of vulnerabilities and exploits for particular actors, vulnerability brokers provided a way for researchers to profit from their findings.
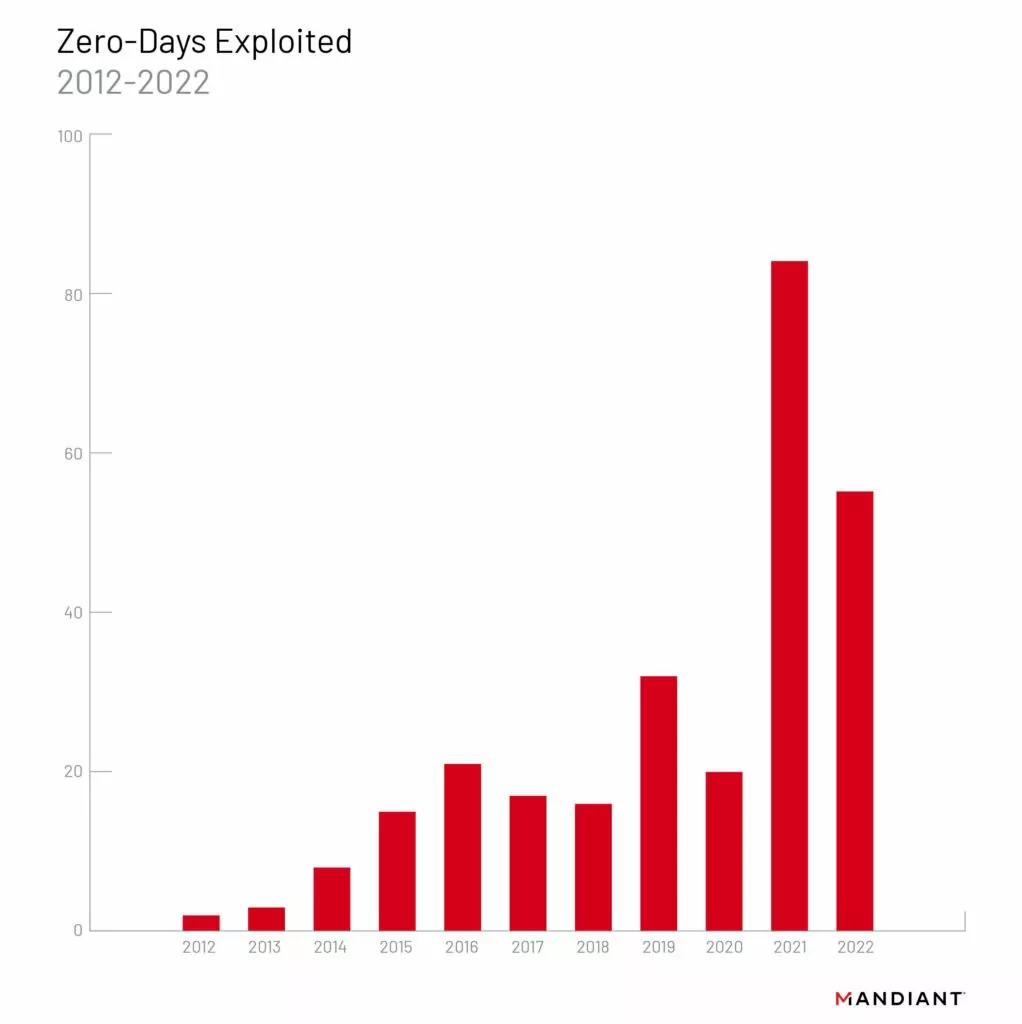
As shown in the graphic below, the number of zero-days exploited has been increasing through the years, which supports the idea that zero-days are essential to get a hold of before anyone else exploits them.
Who Buys and Where Do They Buy?
Vulnerability brokers play a notable role in cyberspace with their ability to move around undisclosed vulnerabilities or exploits. They provide a storefront for the potentially devastating exploits. The intentions behind this buying vary, and there are different types of brokers to be considered. Also, it is hard to pinpoint the intentions because this kind of transaction is primarily done in secrecy. According to our research, we put actively buying parties into three categories: Government Agencies, Private Organizations, and Cybercriminals.
Government Agencies
It is known in the cybersecurity scene that government involvement in buying vulnerabilities is the highest. They are the ones who have fastened the rise of the market for vulnerabilities. Governments, through their intelligence agencies or other means, purchase vulnerabilities and exploits to use in their overseas activities, or as it was disclosed in the leaks by Edward Snowden, over their people.
The primary source of zero-day vulnerabilities or exploits for government agencies is individual researchers with connections or firms such as Zerodium, Exodus Intelligence, or Operation Zero, who buy exploits or zero-days from security researchers.
Private Organizations
Organizations that buy vulnerabilities can be broken into two parties. One is the organizations such as The Zero Day Initiative (ZDI), Zerodium, and Exodus Intelligence, which buy vulnerabilities for their objective. For example, Zerodium’s customers are government institutions (mainly from Europe and North America) needing advanced zero-day exploits and cybersecurity capabilities. Another example would be ZDI which was created to encourage the reporting of zero-day vulnerabilities privately to the affected vendors by financially rewarding researchers.
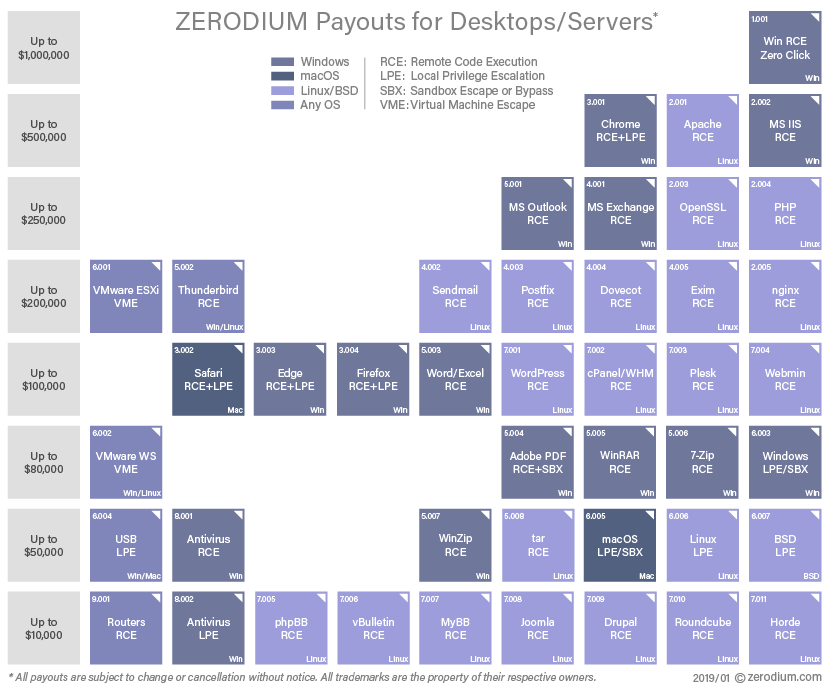
The other party is the organizations that have bug bounty programs. Bug bounty programs offer rewards to researchers who find and report vulnerabilities. This can also be considered a form of vulnerability brokerage because a transaction is being made for a vulnerability.
Cybercriminals
Cybercriminals, as in their nature, are also interested in purchasing vulnerabilities or exploits to conduct malicious activities. They may buy exploits to gain unauthorized access to systems or networks, steal sensitive data, or spread malware. These actors may range from ransomware operators to nation-state actors.
These kinds of actors mainly operate secretly, and it is hard to find any trails left behind them. However, there are open markets that provide anonymity for the interested parties to conduct transactions.
Who Provides These Vulnerabilities?
Vulnerability brokers rely on various sources to obtain information about vulnerabilities and exploits. Sellers of vulnerability information may have a variety of motivations for providing this information to brokers. Our research divided these sources into two categories: security researchers and cybercriminals.
Security researchers are one of the main driving forces uncovering vulnerabilities to the light of day. Most of the time, they are cybersecurity professionals or enthusiasts who discover vulnerabilities as part of their work or research. They may do this research to gain recognition for their findings, or if they are not already paid to do this line of business, they might go beyond bug bounty programs to monetize their conclusions for a higher price.
Another motivation for security researchers to find new vulnerabilities might be to improve security. They can freely share their findings with the vendor or sell to programs like ZDI and HackerOne to gain extra money while contributing to the scene.
Cybercriminals are the other source for the vulnerability brokers to obtain vulnerability or exploit. The significant aspect to consider for cybercriminals’ motivation is money. It is the top motivator for these actors, particularly cybercriminals selling information on the dark web, to conduct any business on the subject.
Vulnerabilities or exploits for widely used software can generate quite a money for these actors. These individuals operate in the dark web and sell information about vulnerabilities to other cybercriminals or vulnerability brokers or carry out attacks themselves. These actors range from individuals who want quick cash to nation-states who wish to finance their malicious activities.
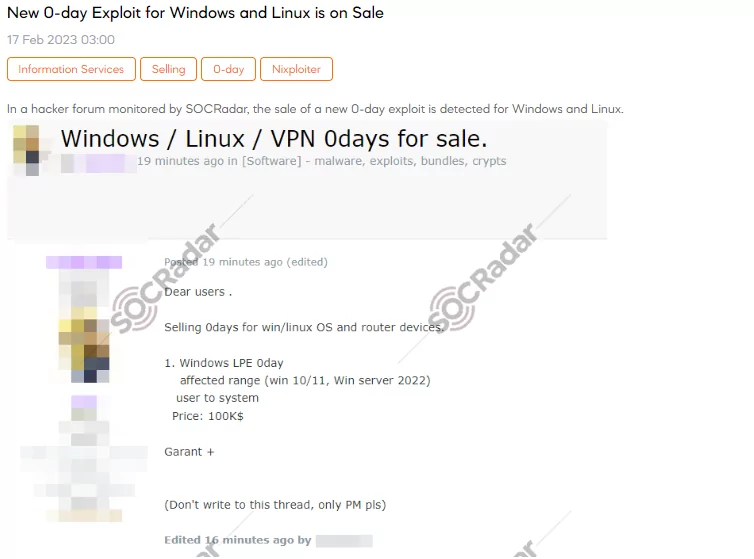
What are the Notable Activities Related to Vulnerability Brokering?
In 2015, a significant data breach occurred on the Italian surveillance software company Hacking Team, which was acquired to create Memento Labs in 2019. The leak contained 400 GB of data involving contracts, invoices, emails, and source code. The breach showed that the company had been selling its surveillance tools to various governments and law enforcement agencies worldwide, including regimes with poor human rights records. Among their clients were 23 Intelligence Agencies and 30 Law Enforcement Agencies.

In mid-2016, the Shadow Brokers began releasing tools and exploits they allegedly stole from Equation Group, which is allegedly part of the US National Security Agency (NSA). The leaks came in waves and lasted until 2017. They tried to auction off some of the tools to the highest bidder but eventually released them for free online. The event stressed the risks associated with the stockpiling of vulnerabilities by government agencies and the potential for such information to be leaked or stolen.
NSO Group is an Israeli company that sells surveillance software to governments and law enforcement agencies. The company has been linked to the sale of exploits that target popular messaging apps like WhatsApp, and its products have been used to spy on human rights activists and journalists. Their primary tool is the Pegasus Spyware, allegedly leveraged in numerous spying activities since its inception. It is capable of remote zero-click surveillance of smartphones. Lately, they have been sued by Apple and Meta for their spying activities on iPhones and Meta’s WhatsApp.
What Does This All Mean for Cyberspace?
Zero-day brokers operate in secrecy, often using pseudonyms and encryption to protect their identities and communications. The brokers typically have a network of researchers and hackers who actively search for zero-day vulnerabilities in popular software products and then sell those vulnerabilities to the highest bidder. Some argue that the brokers simply provide a market-based solution for software vendors who are slow to fix vulnerabilities. In contrast, others argue that brokers make the internet less secure by enabling malicious actors to launch cyber attacks.
As in the case of ZDI, vendors are pressured to patch and focus on critical vulnerabilities immediately. In their policy, after they acquire a critical vulnerability, they provide the vendor with 30 days to patch or mitigate. If the vendor is uncooperative, ZDI will publish the information regarding their talks with the vendor. In addition, they have a strict policy that suggests in no cases will an acquired vulnerability be “kept quiet” because a product vendor does not wish to address it.
In conclusion, the impact of buying and selling vulnerabilities has many layers. Yes, there are potential risks involved regarding the ecosystem. However, there are also examples, such as ZDI, that work toward improving the scene by identifying and disclosing vulnerabilities. It is essential to balance these competing concerns to ensure that the benefits of vulnerability brokerage are realized while minimizing the risks.
SOCRadar has a predictive, preventive, and proactive approach toward security. SOCRadar monitors and analyzes the dark web to provide intelligence regarding underground activities. With the Dark Web News module, you can track the ecosystem and receive a heads-up if an actor on our radar tries to sell a vulnerability.