
Secure the Credentials: How to Work With Breach Datasets
Data breaches have become an increasingly common and devastating threat to businesses of all sizes. The need for proactive measures to secure your credentials and identify and mitigate these threats has never been more crucial. That’s where our “Breach Dataset” module comes into play, providing comprehensive insights and actionable intelligence to help organizations stay ahead of the curve in the fight against cybercrime.
What is the Breach Dataset Module?
The Breach Dataset is a tool designed to help cybersecurity professionals navigate the complex world of data breaches. This module contains a vast collection of breached datasets, “combolists”, sensitive documents, credit card details, and Personally Identifiable Information (PII) sourced directly from dark web platforms and threat actors. By leveraging advanced data mining techniques, our team of experts analyzes this data to uncover critical insights that can help organizations protect their assets.
One of the key features of the Breach Dataset module is its robust search engine, which allows users to quickly and easily navigate through the vast trove of data. If you’re seeking specific breached datasets or “combolists” relevant to your industry, our advanced search engine is at your service.
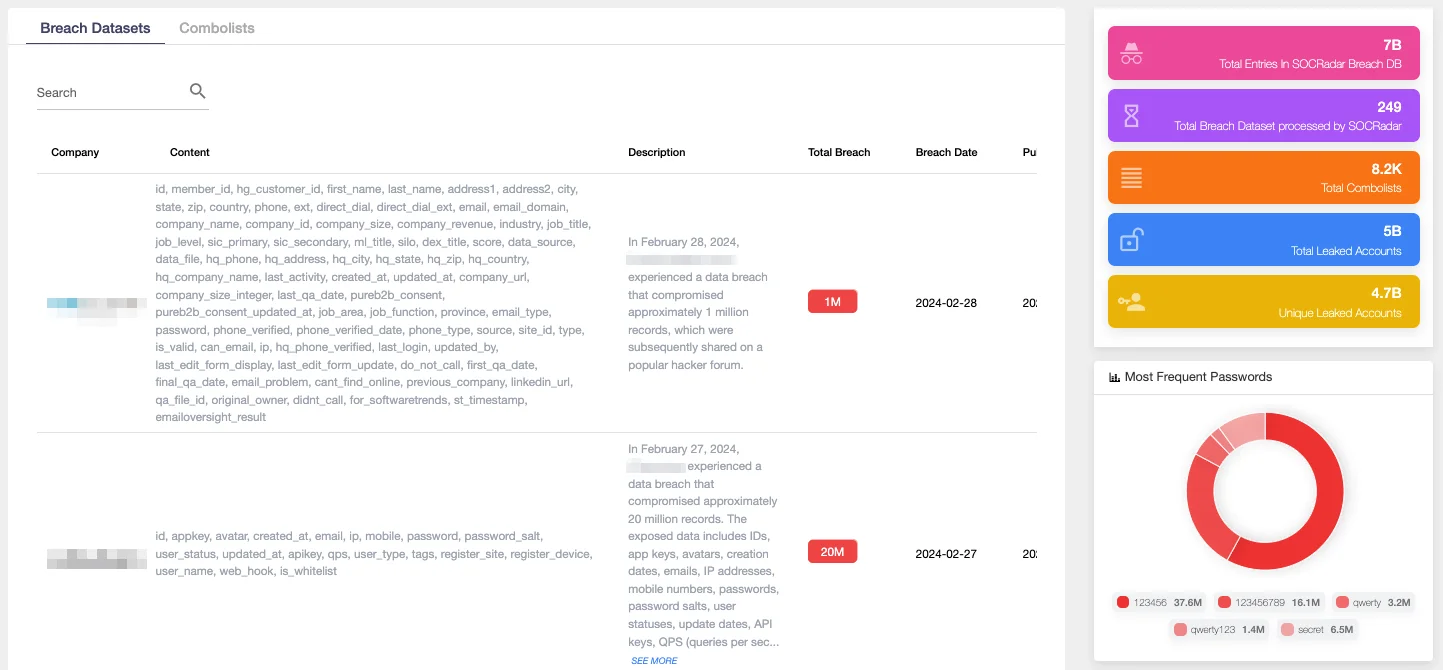
SOCRadar Breach Datasets
The Importance of Timely Breach Detection and Analysis
Early detection is the key to minimizing the impact of data breaches. By staying informed about the latest threats and having access to comprehensive datasets, businesses can proactively identify potential vulnerabilities and take steps to mitigate them before they can be exploited by cybercriminals.
How to Use Breach Datasets
Protect Your Clients
In a bustling tech hub a software development firm Create was providing various services to other businesses. They also had an in-house security team to protect the applications created for their clients. Despite their advanced security measures, they found themselves struggling to keep pace with emerging threats and vulnerabilities. Their existing threat intelligence capabilities were limited, and they knew they needed to enhance their approach to stay ahead of cybercriminals.

Create Office – Generated by ImageFX
One day, they learned about a powerful tool from SOCRadar, the Breach Datasets tool. They decided to integrate it into their operations. The module promised to provide access to a wealth of breach datasets, “combolists”, and sensitive information sourced directly from dark web platforms and threat actors.
You can protect your business from the dangers lurking in the hidden corners of the internet. SOCRadar also provides a dark web monitoring service to its clients where it is possible to track criminal activitiy without visiting the dangerous forums. Our analysts monitor various forums and Telegram channels run by criminals to extract intelligence from those sources. You can gain insights about your industry or region with the help of the SOCRadar Advanced Dark Web Monitoring module.
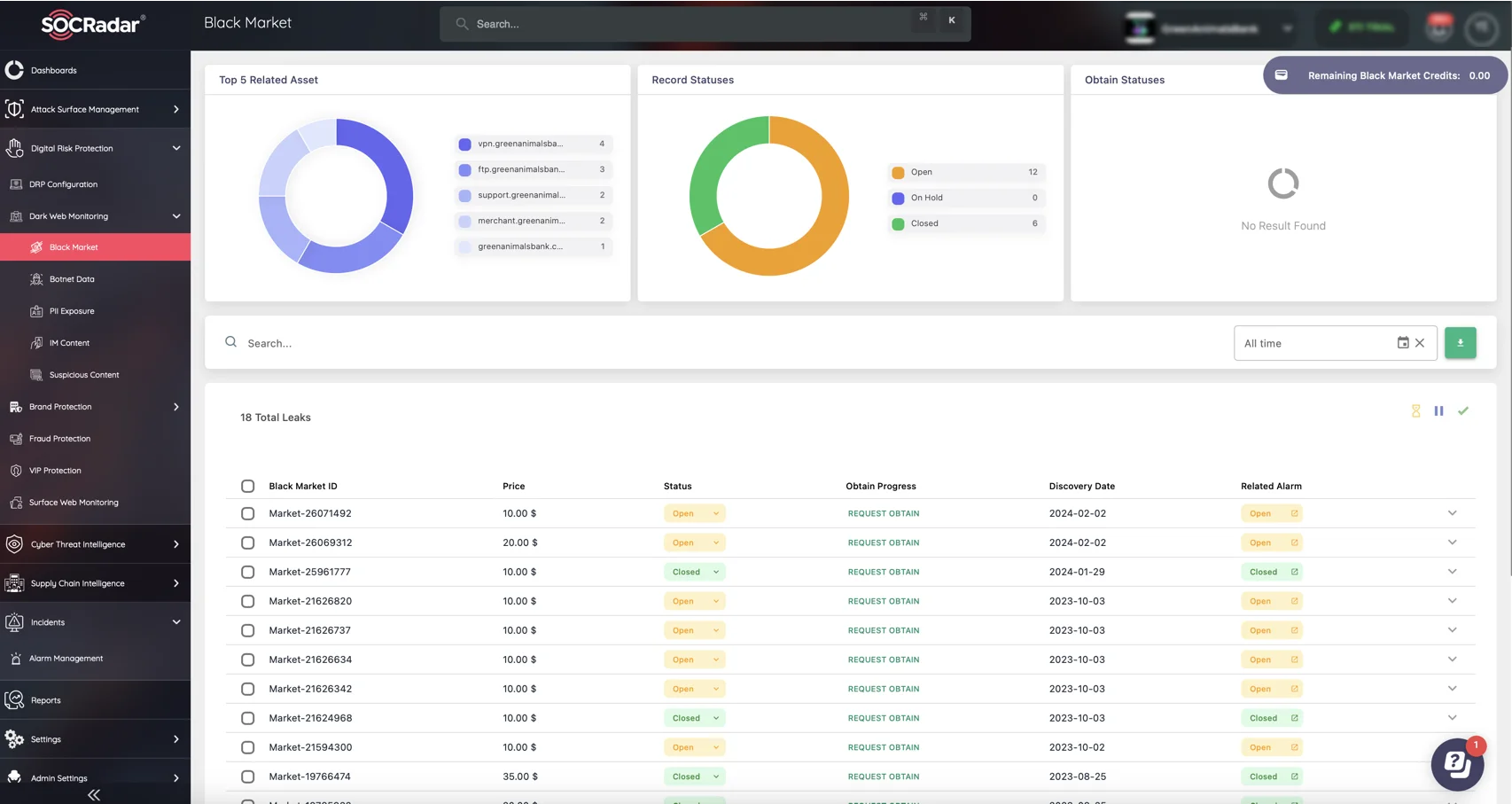
SOCRadar’s Dark Web Monitoring real-time monitoring of Balck Markets
As soon as the module was integrated, they began monitoring the breach datasets for any signs of breaches that impacted their customers. They alerted the exposed clients so they could take the necessary steps. The team also set up alerts for specific keywords and patterns that could indicate new vulnerabilities relevant to their clients’ industries. Within days, they identified a surge in “combolists” targeting financial institutions, revealing a new attack vector that had not yet been widely recognized.
With these insights, they quickly met with their incident response team. They discussed adapting their threat detection and response strategies based on the new intelligence. By utilizing the existing intelligence, they refined their detection mechanisms, ensuring that their systems could recognize and respond to emerging threats more effectively.
Protect Financial Data
The Tree Bank fraud team was tasked with protecting their institution from the growing threat of data breaches and financial fraud. However, they were having problems with a comprehensive data source. By integrating the Breach Dataset tool from SOCRadar into their security stack, they gained access to a wealth of data on compromised financial accounts and credit card information sourced directly from the dark web and Telegram channels.

Tree Bank – Generated by ImageFX
With this intelligence, the fraud team could identify specific accounts and cards that had been exposed in recent breaches and “combolists”. They quickly implemented measures to prevent unauthorized transactions and mitigate potential financial losses.
One of the bank’s top priorities was to alert affected customers about the breach and take immediate steps to secure their accounts. They developed a streamlined process to notify customers whose data had been compromised, monitor their accounts, and report any suspicious activity. This allowed customers to take action quickly and minimize their exposure to fraud.
In addition to flagging suspicious accounts, the ability to rapidly identify compromised accounts and credit cards enabled them to prevent fraudulent transactions as well. Now, they can see the web of connections between criminals and how they transfer their money from one account to another.
The finance industry is one of the few industries where the stakes are high. Any loss in terms of data or time is hazardous. It is vital for corporations to make sure that they know their threats and prepare for them. You can visit SOCRadar’s Financial Data Breaches report to understand the threat landscape.

Financial Data Breaches Report – SOCRadar
Protect Your Company
In the dynamic e-commerce landscape, MarketPlatz recognized the paramount importance of safeguarding customer data and payment information following a series of legal challenges. After that, they decided to increase their intelligence capabilities because they didn’t know about the risks until they saw the memo from the legal department. By leveraging the Breach Dataset module from SOCRadar, they could monitor breached datasets and “combolists” for any signs of compromised credentials of their employees. Numerous threat actors are sharing datasets across the dark web, making it challenging for MarketPlatz to track and verify the authenticity of each one. That’s why a comprehensive tool like this is really useful for them.

HQ of MarketPlatz – Generated by ImageFX
MarketPlatz’s proactive approach allowed them to quickly identify accounts exposed to data breaches and flag them for security measures. This prevented unauthorized access and account takeovers, ensuring the system could operate securely.
By analyzing the breach datasets, MarketPlatz’s team of cybersecurity experts identified patterns and trends that could indicate larger-scale breaches targeting their company. This intelligence enabled them to swiftly identify vulnerabilities within their systems and begin the patching process.
How to Get Started with Breach Datasets
You can start using the Breach Dataset tool with ease. Our user-friendly interface and advanced search capabilities are extremely easy to use, and they will empower you to navigate our data and extract critical insights to protect your organization. Whether you focus on identifying compromised credentials, monitoring for data leaks, or staying ahead of emerging threats, the Breach Dataset tool is designed to meet your needs. You can access the tool from here.
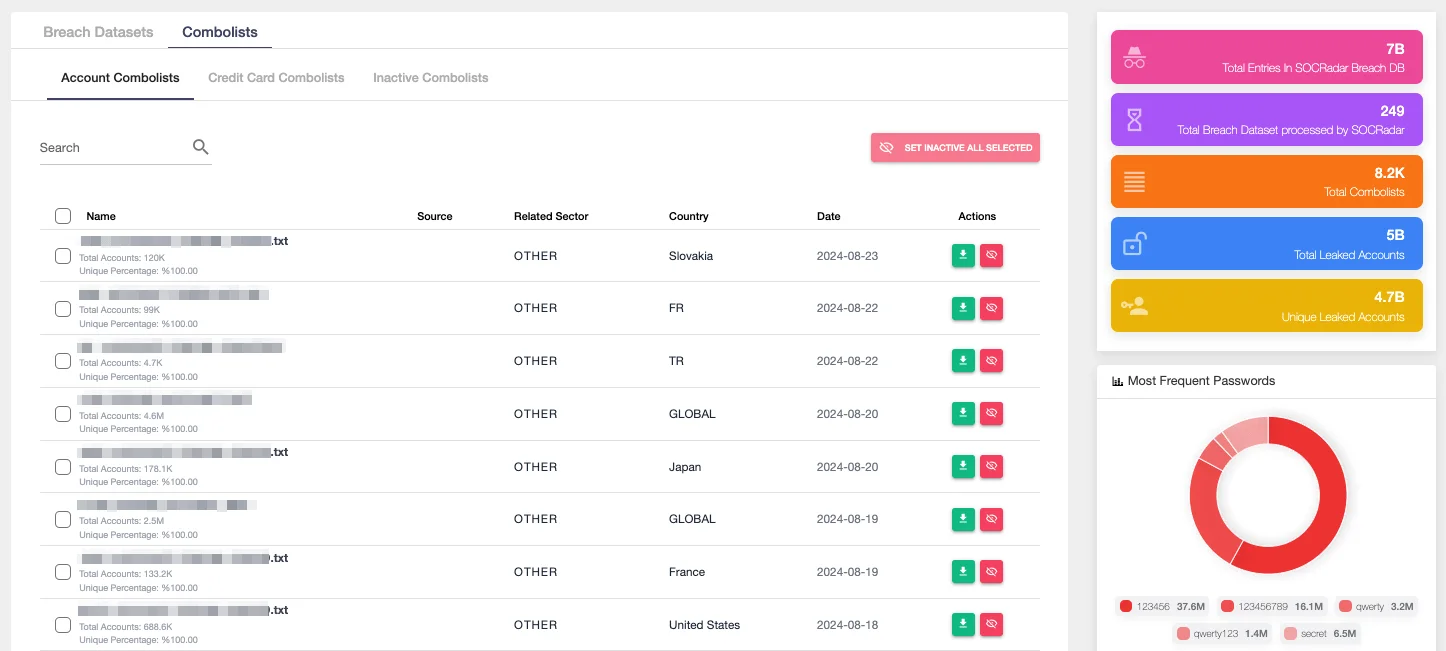
SOCRadar Combolists
In addition to the Breach Datasets tool, you can also utilize SOCRadar’s Threat Hunting module, which again utilizes the same datasets but with advanced search capabilities. This module allows you to see each leak individually and equips you with more information related to the threat actors and the breach itself. You can track the criminals targeting your organization and understand their actions in depth.
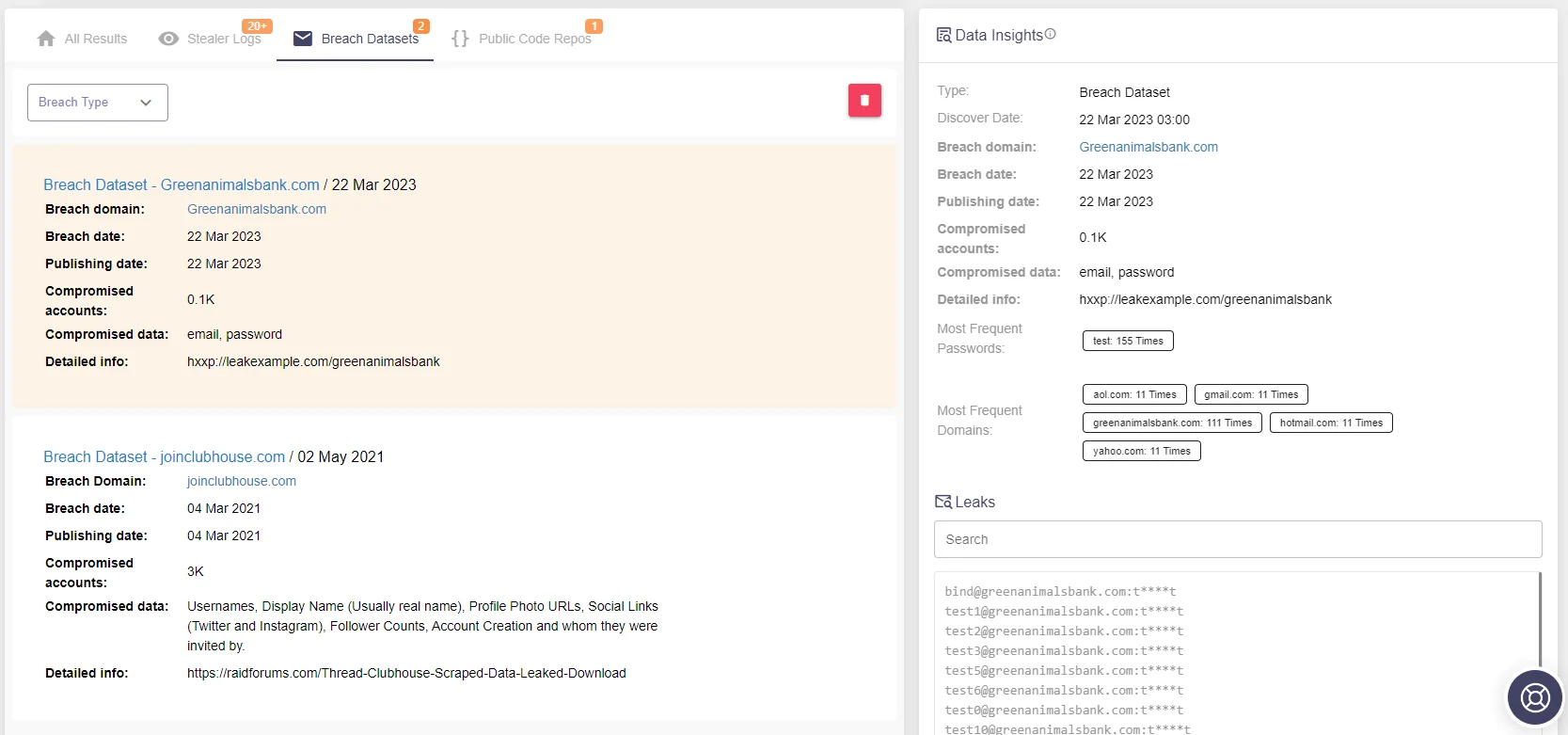
SOCRadar Threat Hunting
Conclusion
In today’s digital age, data breaches are a reality that no organization can afford to ignore. Understanding threat actors’ TTPs (Tactics, Techniques, and Procedures), which serve as the cornerstone of proactive intelligence, is important for any CTI program.
As threat actors increasingly exploit leaked credentials for unauthorized access and impersonation attacks, this shift in the threat landscape underscores the growing importance of securing credentials and enhancing protective measures. By utilizing the advanced capabilities of our Breach Dataset tool, businesses can find out what happened behind their back.
Whether employee credentials are exposed by threat actors, customer credit card information is at risk, or clients are unaware of a breach, our Breach Dataset tool delivers up-to-date intelligence from the dark web, enabling you to mitigate these risks effectively.




































