
Step by Step Threat Hunting
Threat hunting is a proactive approach for organizations to identify threats that have not been detected or remedied before. Considering that threat actors are carrying out more and more sophisticated attacks every day, the importance of threat hunting is better understood. In this article, we will discuss cyber threat hunting in detail.
What is Cyber Threat Hunting?
Threat actors are continuously trying new techniques and tools to go unnoticed from cyber defense mechanisms in place. Modern SOCs leverage threat hunting capabilities as part of their Incident Response teams to identify new threats that do not necessarily trigger an alert.
Threat hunting could be defined as a practice of security analysts looking for threats secretly penetrating their internal network. It is a proactive approach to discover hidden cyber attacks by querying various platforms (e.g., SOCRadar ThreatHose) at-scale for artifacts of a certain TTP. The procedure is also called cyber threat hunting or cyber hunting and engages in going beyond the already noticed malicious threats to find unknown vulnerabilities in the system. The threat hunting process differs from penetration tests or similar actions, looking for weaknesses that a threat actor could leverage to sneak into the network.
Why is it So Important?
Once threat actors get inside a computer system, they spend days and weeks inside the network. Before discovering the cybercriminals, they can access sensitive information and even lock the security professionals out of the systems.
Threat hunting is a systematic and human-driven approach that helps security experts quickly react to incidents. It enables a possible threat to be detected much earlier. Thus, it proactively diminishes the overall risk of a cybercriminal damaging an organization and its systems.
Step-By-Step Cyber Threat Hunting
Threat hunting provides organizations a robust framework for security. To conduct effective threat hunting, below are step-by-step instructions.
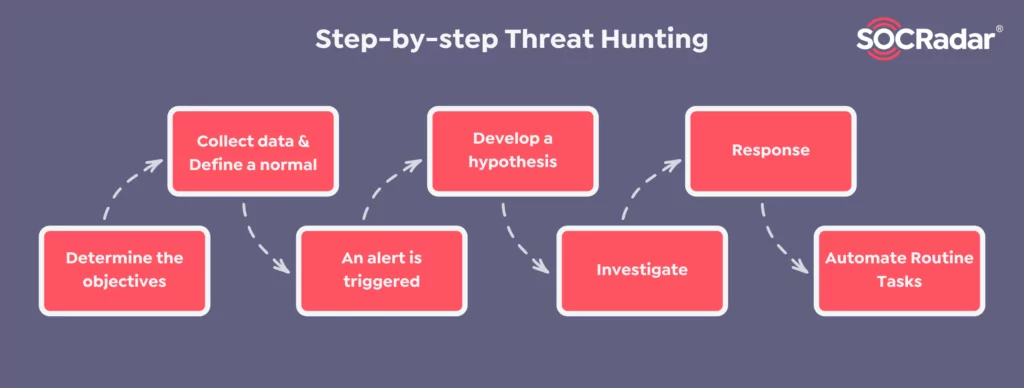
1- Determining the Objectives for the Threat Hunting

Security experts need to start threat hunting by setting a scope for the hunt and defining specific objectives. Identifying the areas you want to perform threat hunting in the system and knowing what you are looking for will make the process more systematic. Some hunt teams waste time over-analyzing threat information rather than concentrating on critical findings. The main reason is that the key objectives in the process have not been determined.
2- Collecting Data and Defining a Normal

An effective threat hunting procedure should have a monitoring and control mechanism that can detect a wide variety of activities on different operating systems and devices. This telemetry mechanism should observe all user activity, system and event logs, and network traffic patterns.
The collected data should be analyzed with the outlier method, and abnormal behaviors should be tracked. In social engineering campaigns, which are most commonly used to penetrate internal networks, attackers often pretend to be an employee to infiltrate the network. Therefore, examining the activities of an ordinary employee and determining a normal will allow the detection of possible abnormal situations.
3- Trigger
Following the normal is determined, the alarm is triggered if abnormal activity is observed in the monitored data. A cyber threat hunter usually identifies the trigger in a particular network area. Thus, threat detection becomes faster and more precise.
4- Developing a Hypothesis

After the trigger is received, it is necessary to make predictions about the details of activity that might be going on in the system. Security professionals generally develop a hypothesis based on social intelligence, past experiences, open-source intelligence (OSINT) tools, and intel frameworks like MITRE ATT&CK.
A Bonus Step: Incident-driven approach in threat hunting
Threat hunting can have an incident-driven approach. The incident and its effects are examined directly during the hypothesis generation step in this situation.
5- Investigation

After formulating the prediction, the following step is investigating different tactics, techniques, and procedures (TTPs) to uncover new adversary activities and patterns in the collected data. To research possible compromises within the infrastructure systems, threat hunters use threat hunting tools like DNSTwist and Yara. The investigation process keeps going until the hypothesis is either confirmed or rejected.
6- Response
When the prediction is proved, the threat hunter should neutralize the incident by creating an immediate response. The primary goal of this step is to cut off the ongoing attack as soon as possible so that the system will not damage by the detected threat. However, it is also crucial to comprehend the vulnerability and its reason to enhance security and control similar cyberattacks in the future.
7- Automating Routine Tasks

Modern threat hunting comprehension involves automating tasks as much as possible. A successful threat hunting process forms a solid basis for future hunts by automating different tasks such as data collection mechanisms and outlier analyses. The data obtained throughout the process strengthens the EDR systems and enables organizations to have a robust cyber security framework.
References:
1- https://www.cybereason.com/blog/blog-the-eight-steps-to-threat-hunting
2- https://www.sentinelone.com/blog/six-steps-to-successful-and-efficient-threat-hunting/
3- https://www.reliaquest.com/blog/build-a-cyber-threat-hunting-plan-with-this-step-by-step-process/
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access



































