
Securing Your Browser Against Cross-Site Scripting (XSS) Attacks
Cross-site scripting (XSS) is one of the most common web security vulnerabilities. Despite the fact that it is not frequently exploited, it can cause significant impact.
XSS attacks target vulnerabilities in web applications, allowing hackers to inject malicious scripts into a user’s browser. This can lead to stolen sensitive data, compromised accounts, and even full system breaches. To maintain browser security and ensure secure web browsing, it’s important to understand XSS attacks and implement protective measures.
XSS attacks can have an effect that extends beyond a single user; organizations can also suffer significant data breaches, loss of customer trust, and legal consequences if their websites are exploited through XSS vulnerabilities.
Understanding XSS Attacks: What is Cross-Site Scripting (XSS)?
Cross-site scripting works by manipulating a vulnerable web application so that it returns malicious scripts to users. Any web application that accepts unsanitized user input, or does not encode an output it generates is vulnerable to XSS attacks.
When the malicious code executes inside a victim’s browser, the attacker can fully compromise user’s interactions within the compromised application, and can steal data, redirect users to phishing sites, or manipulate website content.
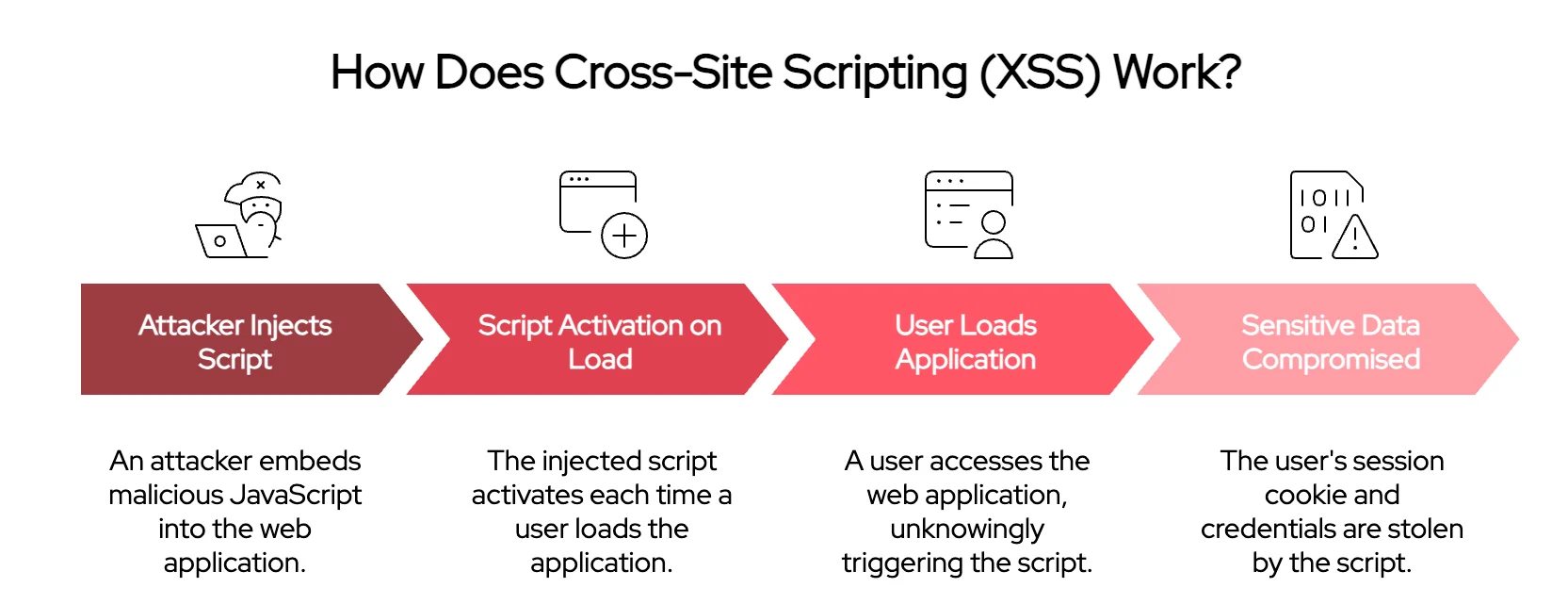
An example on how XSS attacks work
What Malicious Activities Can It Lead to?
The severity of an XSS attack is determined by the sensitivity of the data that can be found in the affected web application and by the privileges of the victim user. After exploiting a cross-site scripting vulnerability, an attacker could be capable of:
- Access session cookies and tokens
- Impersonate as a victim and perform user actions
- Capture keystrokes
- Redirect a user to another website
- Access all the data a victim user had access to
- Obtain victim user’s credentials and take over their account
- Rewrite content of the HTML page
- Inject trojan or other malware into the web application
Types of XSS Attacks
XSS attacks come in different forms, each with its own method of execution and impact:
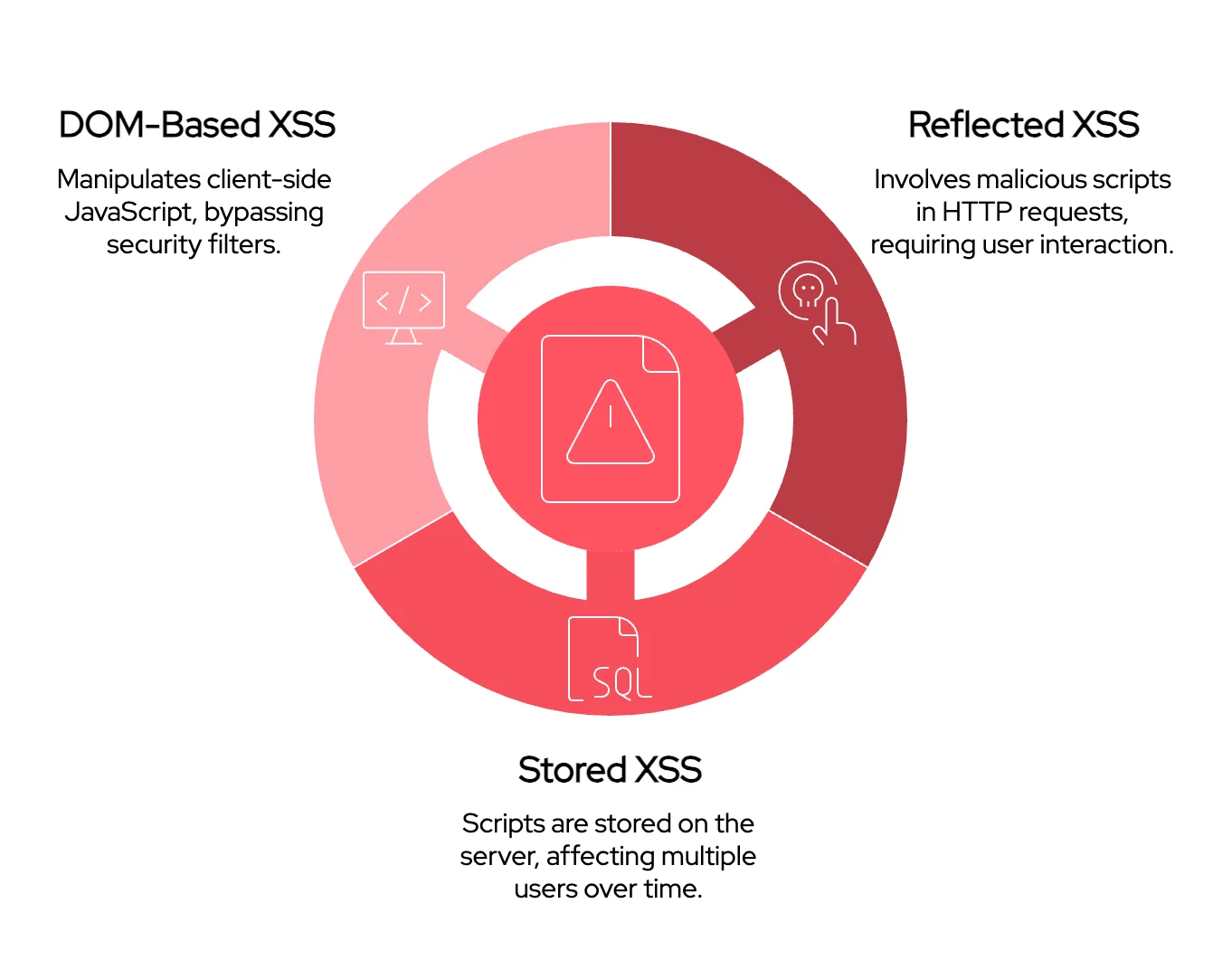
The three types of XSS attacks: Reflected XSS, Stored XSS, and DOM-Based XSS
Reflected XSS
In reflected XSS, malicious scripts are embedded into HTTP requests and the web application reflects received scripts to a victim’s browser without sanitizing them. Reflected XSS is also known as “non-persistent” XSS, because the scripts are not stored on server-side.
This type of attack is typically launched by phishing emails or third-party websites, where the victim is persuaded to click on a malicious link that will make an XSS request to a vulnerable web application.
A user has to click on distributed malicious links for exploitation to be carried out. Attackers may hide the original malicious URL by using URL shortening services, these services make it easier for attackers to trick more users.
Reflected XSS is the most common type of XSS attacks, but it can be avoided easily by not falling for threat actor’s tricks and not visiting suspicious websites.
Stored XSS
Also called a “persistent” XSS attack, stored XSS attacks are where malicious scripts are stored on server-side databases. The script could be entered from different places on a vulnerable web application where user input is available, such as a comment field or post section. This can compromise large numbers of users over an extended period.
When a victim user loads the malicious JavaScript embedded page, the script will be executed in their browser too, resulting in the attacker having access to the user’s capabilities.
For both reflected and stored cross-site scripting attacks, the attack payloads are placed in HTTP response pages.
DOM-Based XSS
The vulnerability exists in the website’s client-side JavaScript, allowing attackers to manipulate the Document Object Model (DOM). Unlike other types, this occurs within the browser and can bypass traditional security filters.
DOM-based cross-site scripting attacks are primarily used by attackers to target applications that have an executable path for data to travel from a JavaScript property called “source” to a location called “sink”. Sinks, such as eval(), setTimeout, and innerHTML can execute the functions while rendering HTML. Sources such as document.URL, window.location, document.referrer, location.search, and location.has can act as a location of malicious input. The most common source in DOM-based XSS attacks is URL, which can be accessed by “window.location”.
DOM-based XSS attack is carried out as follows:
- A URL with a malicious string is created and sent to the victim.
- Victim user clicks on the URL, which requests a URL from the web application.
- The website responds with a clean URL, without malicious code.
- The legitimate script in the response is executed by the victim’s browser, which inserts the malicious script into the page.
- Malicious script is executed on the user’s browser, the cookies are sent to the attacker.
Protecting Against Vulnerabilities
The best practice against XSS is to create an overall safe web application from the start, by implementing proper restrictions and using the correct headers. Check out the practices listed below to get started securing against XSS attacks.
Best Practices for Web Users
To safeguard against XSS attacks, web users must adopt proactive security measures:
- Keep Your Browser Updated – Regular updates patch vulnerabilities that hackers may exploit. Outdated browsers often lack security enhancements necessary to defend against XSS threats.
- Use a Trusted Antivirus Program – Security software can detect and block malicious scripts before they execute.
- Disable JavaScript on Untrusted Sites – Extensions like NoScript allow users to control where JavaScript runs.
- Be Cautious with Links and Forms – Avoid clicking suspicious links or submitting forms on unverified websites. Even seemingly legitimate links may hide malicious payloads.
- Enable Content Security Policy (CSP) – This browser feature restricts the execution of unauthorized scripts, significantly reducing exposure to XSS threats.
- Regularly Clear Cookies and Cache – This can remove potential malicious scripts that have been stored in the browser.
- Use Multi-Factor Authentication (MFA) – If credentials are compromised through an XSS attack, MFA can prevent unauthorized account access.
Best Practices for Website Owners
Website administrators also play a crucial role in preventing XSS vulnerabilities:
- Sanitize User Inputs – Filter and validate all user input to prevent malicious script injection.
- Use HTTP-Only and Secure Cookies – Prevent cookies from being accessed by JavaScript.
- Implement Escaping Techniques – Encode dynamic data before rendering it on web pages to prevent unauthorized script execution.
- Conduct Regular Security Audits – Periodic code reviews and penetration testing help identify vulnerabilities.
- Implement Web Application Firewalls (WAFs) – WAFs can detect and block XSS attack attempts before they reach the server.
- Apply the Principle of Least Privilege (PoLP) – Limit user permissions to reduce the impact of a successful XSS attack.
- Monitor Website Traffic and Logs – Unusual behavior patterns may indicate an ongoing attack, allowing for faster incident response.
- Check OWASP’s Cross-Site Scripting Prevention Cheat Sheet for further guidance.
In addition to these practices, SOCRadar’s Attack Surface Management (ASM) continuously scans your network applications and other external-facing assets for the most recent security vulnerabilities, whether they are Cross-site Scripting (XSS) or other types.
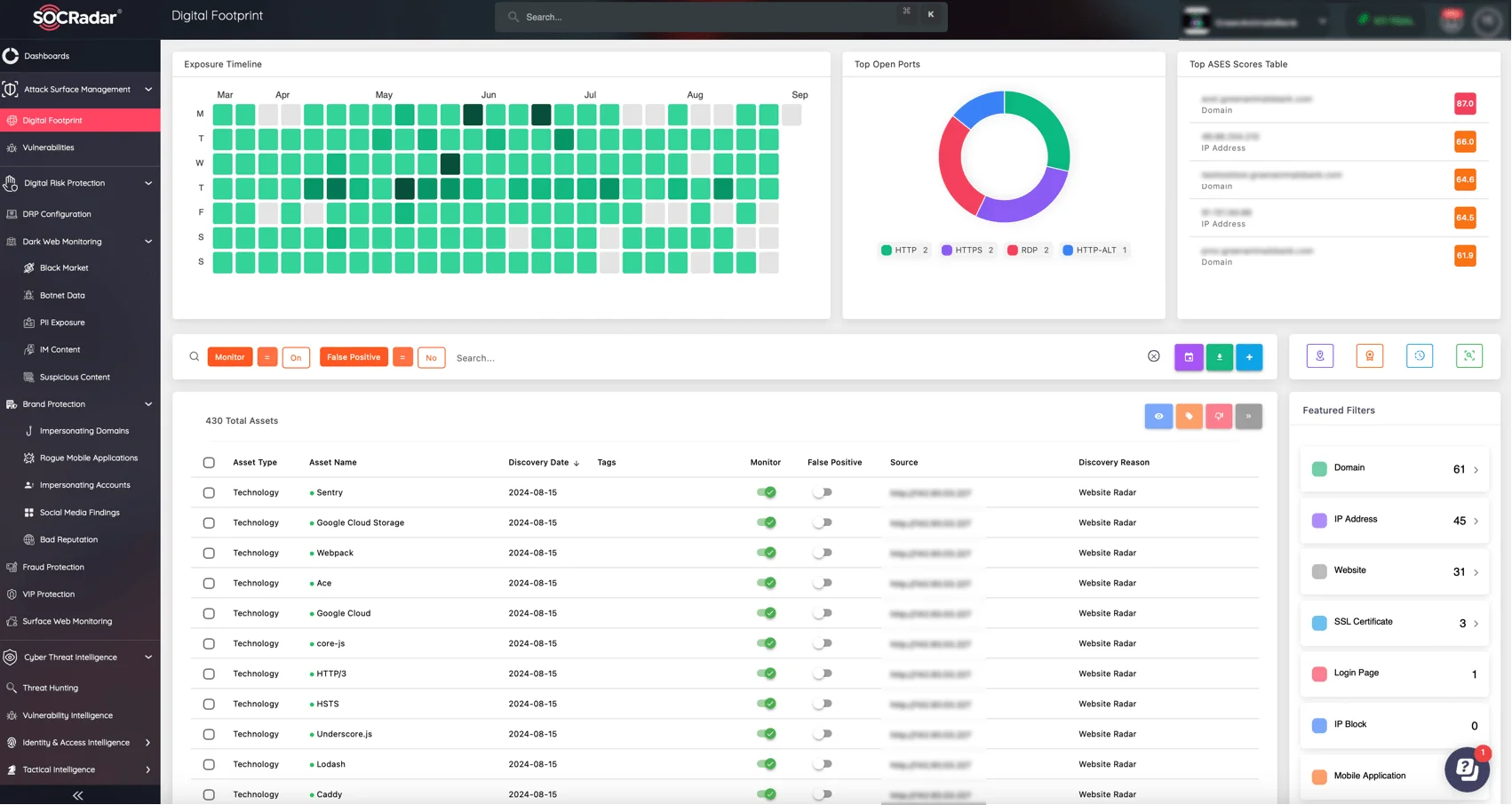
Easily track your digital footprint with SOCRadar ASM
SOCRadar’s platform also delivers updates on newly discovered threats and trending vulnerabilities through Vulnerability Intelligence, provided under the Cyber Threat Intelligence module, allowing you to learn more about vulnerabilities and remain secure.
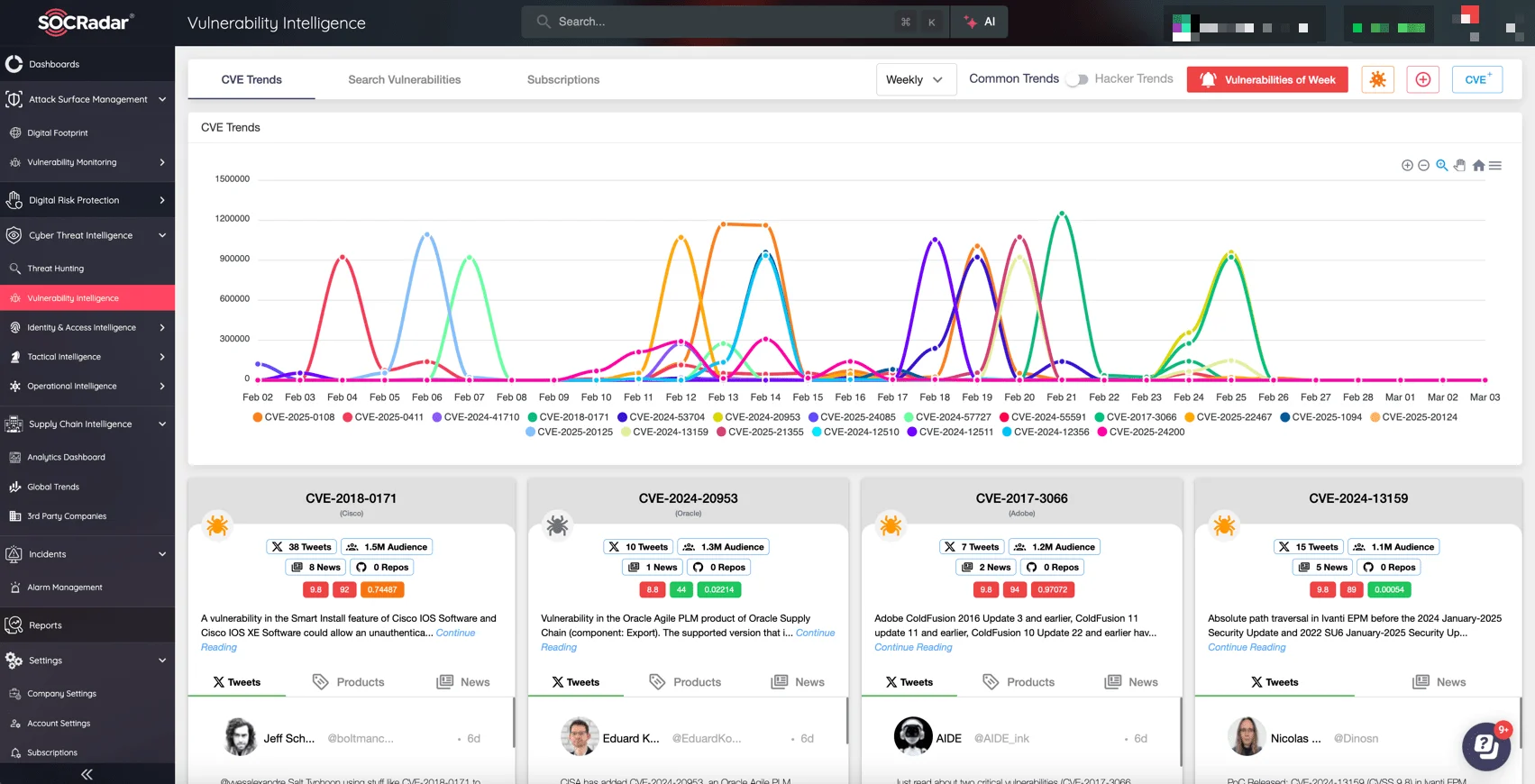
Follow the newest CVEs and hacker trends via Vulnerability Intelligence on SOCRadar XTI
Tools for Secure Web Browsing
By leveraging the right tools, users and administrators can significantly reduce the risk of XSS attacks. Below are some key tools and techniques that enhance browser security and protect against XSS vulnerabilities.
What tools can you use to enhance security against Cross-site Scripting?
Web Application Firewalls (WAFs)
Web Application Firewalls analyze and filter malicious traffic, preventing XSS and other cyber threats before they reach users. Advanced WAF solutions use artificial intelligence to detect and mitigate new attack patterns in real time.
Security Headers
Browsers support security headers that help mitigate XSS risks:
- Content Security Policy (CSP) – Restricts sources from which scripts can be loaded, reducing the likelihood of unauthorized script execution.
- X-XSS-Protection – Enables built-in browser protections against XSS.
- Referrer-Policy – Limits the information sent with requests to prevent data leakage.
- Strict-Transport-Security (HSTS) – Enforces HTTPS connections to protect against data interception.
XSS Testing Tools
Website owners and security professionals can leverage specialized tools such as these to detect XSS vulnerabilities:
- Burp Suite – A powerful tool for web vulnerability scanning, including XSS detection.
BurpSuite (Source: Portswigger)
- OWASP ZAP (Zed Attack Proxy) – An open-source tool designed to find security weaknesses in web applications.
Browser Security Extensions
There are numerous browser extensions that enhance secure web browsing by providing additional layers of protection against XSS attacks. Some of the known ones include:
- NoScript – Blocks JavaScript execution on untrusted websites, preventing malicious script injection.
- uBlock Origin – Prevents malicious ads and scripts from loading, reducing the risk of drive-by attacks.
- Privacy Badger – Blocks tracking scripts that could be exploited for XSS-based attacks.
Conclusion
XSS attacks are a serious threat to browser security and online safety, allowing malicious scripts to compromise sensitive data. However, by taking proactive measures and leveraging the right security tools, both web users and website administrators can reduce the risk of exploitation.
Your security practices play a vital role in defending against cyber threats. Whether you’re an individual user or a business owner, staying informed about XSS vulnerabilities and actively mitigating risks is essential for safe web navigation.
To simplify security management, SOCRadar XTI continuously scans network applications and external-facing assets for vulnerabilities, including XSS risks.
By prioritizing security today, you contribute to a safer and more resilient digital environment for everyone.





































