Sensitive Information Belonging to BMW Exposed Due to Misconfigured Cloud Bucket
A recent event involving a misconfigured cloud storage bucket owned by BMW has highlighted the crucial role of cloud security. The issue was detected by one of SOCRadar’s researchers, Can Yoleri. According to Yoleri, this bucket, which was accidentally configured for public access, led to the exposure of sensitive company data, including private keys.
The Discovery of BMW’s Exposed Data
The discovery was made by Can Yoleri, a security researcher at SOCRadar. On December 18th, during his routine scan for publicly accessible cloud resources on the internet, Yoleri stumbled upon the misconfigured server. Within the exposed files (azconfig.io), he identified critical data such as database connection information for both development and production environments, Azure Docker (azurecr) authentication details, and secret keys for additional private buckets, affecting the company’s cloud services across North America, Europe, and China.
Yoleri traced the problem back to a Microsoft Azure-hosted storage “bucket” in BMW’s development environment, which was incorrectly set to public access as a result of a configuration mistake. The bucket in question housed script files containing Azure container access information, secret keys for accessing other private bucket addresses, and specifics on various cloud services.
Yoleri emphasized the difficulty in ascertaining the duration for which such buckets are left open, a detail only known to the bucket’s owner.
BMW’s Response to the Incident: Emphasizing the Importance of Continuous Cloud Resource Monitoring
BMW acknowledged that the incident involved a Microsoft Azure bucket within its storage development environment and confirmed that no customer or personal data was affected. The issue was rectified at the beginning of 2024, with ongoing monitoring in collaboration with their partners.
TechCrunch’s reporter, Carly Page, shared that they reached out to the company’s spokesperson, Chris Overall. Overall confirmed to TechCrunch that the data exposure affected a Microsoft Azure bucket based in a storage development environment and said no customer or personal data was impacted as a result.
The Incident as a Common Issue: The Prevalence of Cloud Resource Misconfiguration
This incident serves as a testament to a wider issue in cloud security – the misconfiguration of cloud resources. A 2019 Gartner survey revealed that misconfigurations cause 80% of data breaches, a figure anticipated to exceed 90% by 2025. Such misconfigurations are often due to human error, underscoring the necessity for stricter identity access management, avoidance of default credentials, and continuous monitoring of bucket statuses.
SOCRadar’s Cloud Security Module (CSM) presents an effective strategy to address these challenges. Offering immediate alerts regarding the status of cloud buckets and tracking any status changes, the CSM empowers organizations to swiftly identify and mitigate potential security threats. This proactive stance on cloud security is vital for preventing data leaks and safeguarding sensitive data.
How SOCRadar Cloud Security Module Protects Organizations
SOCRadar enhances its External Attack Surface Management (EASM) services with the introduction of the Cloud Security Module (CSM), designed to secure customer cloud storages. This module not only identifies new cloud buckets via EASM but also allows these buckets to be classified as assets by determining if they are “public,” “private,” or “protected.” A “Cloud Bucket Detected” alert is issued upon discovering new cloud storage belonging to users, incorporating it into digital assets.
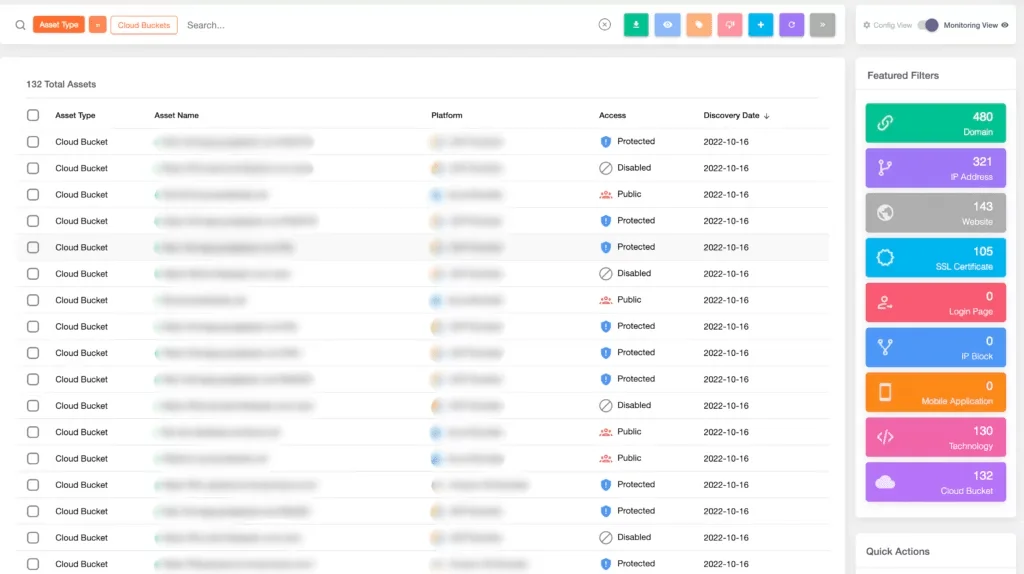
A cloud storage bucket can be defined as an asset in SOCRadar XTI.
With the CSM, the status of your buckets is under constant surveillance, alerting you to any changes, such as a bucket’s transition from “private” to “public.”
This incident with BMW underscores the critical need for diligent cloud security practices. As organizations increasingly adopt cloud storage solutions, implementing advanced security measures like SOCRadar’s Cloud Security Module becomes essential to protect against misconfigurations and potential data breaches.


































