
Security Misconfigurations Caused 35% of All Time Cyber Incidents
By SOCRadar Research
Security misconfiguration is the vulnerability that arises when systems or applications are not configured properly, resulting in potential security risks. According to OWASP, in 90% of the applications they examined, they found some form of misconfiguration. It’s crucial to address security misconfigurations promptly as they can lead to serious security breaches, such as unauthorized access to sensitive data or unauthorized control of systems or networks. Identifying misconfigurations and exposures can be among the first observations a threat actor makes when performing initial reconnaissance on an organization. Good security hygiene that addresses misconfigurations and vulnerabilities is critical for a mature security posture.
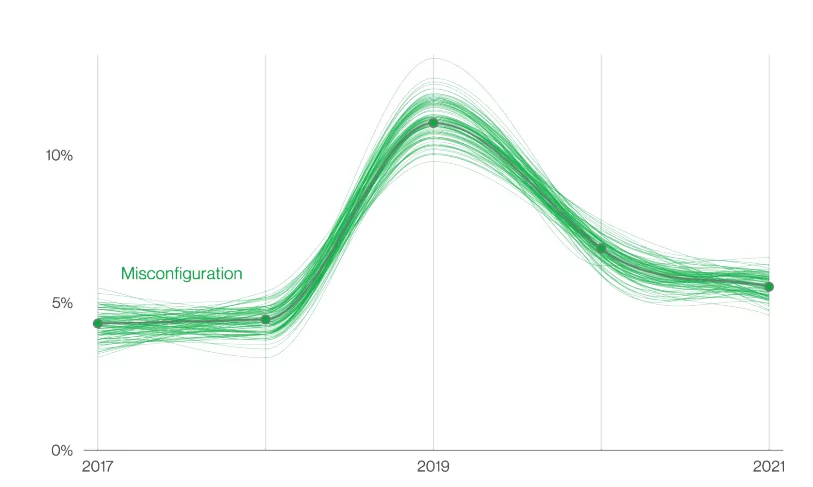
While most patterns have changed over the years, a never-changing pattern has been people making mistakes. The misconfiguration errors started rising in 2018, as seen in the graphic below and declined in recent years. However, this does not mean it is not an essential security aspect. It is still a considerable threat because of the human element. The costs of mistakenly exposing data or a system to the internet due to a simple misstep or misconfiguration can be financially and reputationally devastating.
According to the graphic below, the rise and decline were primarily driven by cloud data store implementations that were stood up without appropriate access controls. The overlooked configurations later got more robust with the efforts of the major cloud providers to make the default settings more secure. According to Fugue’s report: In 2021, 36% of cloud professionals said their firm experienced a severe cloud security breach or leak.
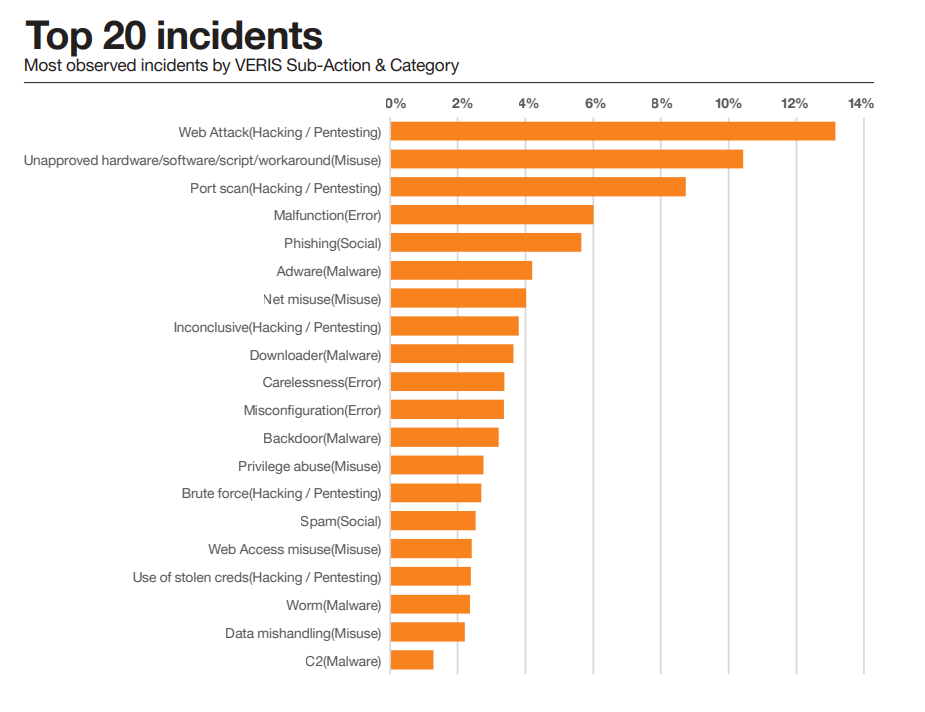
According to Statista, 15 million data breaches were registered globally in the third quarter of 2022, a 37% increase compared to the previous quarter. According to the VERIS, an open-source project for event recording and incident sharing, around 35% of the observed incidents of all time were caused by either error or misuse, which backs up the importance of misconfiguration.
The Reason Behind Misconfigurations
Security misconfigurations can happen due to human error, lack of knowledge or understanding, or lack of proper guidelines or procedures for configuration management. They can also occur when new systems or applications are added to a network without adequately assessing and addressing potential security risks.
Default Settings
Many configuration errors happen when system administrators do not change the default settings of a device or program. These default settings are often targeted by automated attacks, so changing them can decrease the risk of a breach.
Lack of Understanding
Some organizations may not fully understand the security implications of certain configurations or may be unaware of best practices to secure their environment against potential threats.
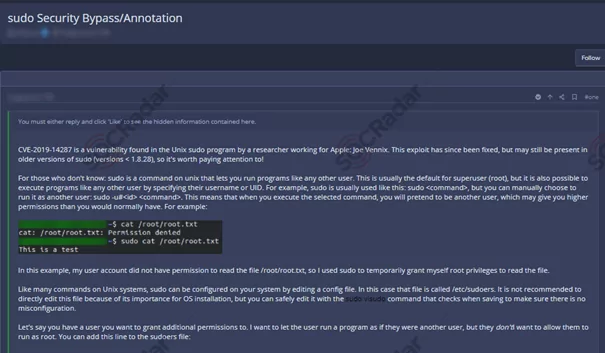
Unfixed Flaws in the Software
Utilizing unpatched or obsolete software, threat actors gain unauthorized access to the functionalities or data of a business system. Occasionally, the exposed vulnerability can lead to a complete system breach.
Inactive Pages and Unneeded Services/Features
In addition to unused pages, features, or services, attackers can acquire unauthorized access to a business application or device. If left unchecked, these flaws may lead to severe problems like command injections, brute force assaults, and credential stuffing attacks.
Inadequate Access Controls
Default passwords, unused user accounts, and unused access rights that have not been updated or removed by administrators allow threat actors to obtain entry to the network infrastructure. Overly permissive access policies also permit adversaries to inflict a variety of disruptions, such as malware attacks and data breaches.
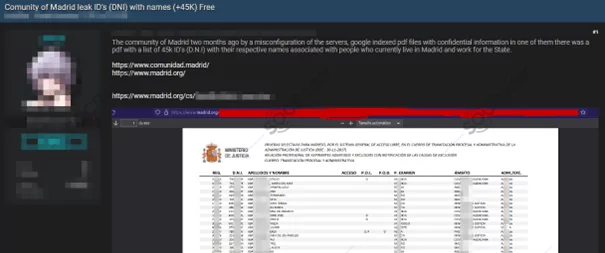
Unprotected Folders and Files
Without adequate security safeguards, files and directories are susceptible to cyberattacks. Attackers can identify platforms and programs that easily-guess names and locations to get important system information and execute targeted attacks.
Predictable file names and locations can expose administrative interfaces, allowing an adversary to obtain privileged access, configuration details, business logic, and even manipulate application functionality.

Human Error
One of the most important reasons for misconfigurations is human error. Mistakes or oversight during the configuration process can lead to misconfigurations. Most of the reasons listed before might stem from human error. People manage the systems, so it is natural for human error to be this destructive in security misconfigurations.
Prominent Recent Misconfiguration Exploits
BlueBleed
On September 24, 2022, SOCRadar’s security researchers discovered a misconfigured endpoint on Microsoft’s systems. This misconfiguration allowed for unauthorized access to specific business transaction data, including information such as names, email addresses, email content, company name, phone numbers, and possibly attachments related to interactions between Microsoft and its prospective customers, including planning and potential implementation of Microsoft services. Unauthorized parties could have accessed this data.
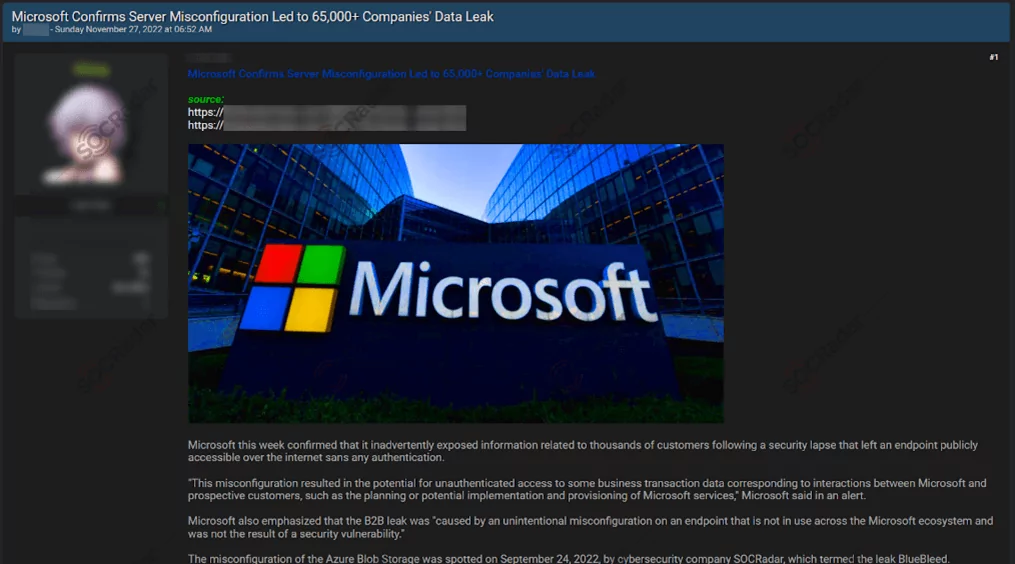
Pentagon Email Leak
On February 20, 2023, the Pentagon isolated and secured a compromised server that had been leaking internal US military email to the open internet for the past two weeks. The server was hosted on Microsoft’s Azure government cloud, specifically designed for Department of Defense customers. Authorities used it to store about three terabytes of military emails related to USSOCOM, the unit responsible for special military operations. However, due to a misconfiguration, the server did not require a password, making the sensitive mailbox data accessible to anyone on the internet who knew the IP address.
T-Mobile Leak
T-Mobile reported that an attacker accessed a limited set of customer account data through a misconfiguration on API starting on November 25, 2022, and was detected on January 5, 2023. The attacker obtained data from 37 million current postpaid and prepaid customer accounts.
Nissan Public Git Server
In 2021, threat actors released some Nissan source code online. Nissan is a Japanese multinational vehicle manufacturer. A Swiss security researcher determined that the misconfiguration of a company’s Git server was to blame. The Git server was left accessible through the internet with the default username and password of admin/admin.
Solution: SOCRadar analyzes the contents of a vast number of GitHub repositories that it monitors. It quickly detects references to your organization. SOCRadar also notifies businesses of any information that may have become public and monitors for credential leaks.
Constantly watched are the account credentials of your customers or workers, credit cards, PII, and other sensitive company-related information.
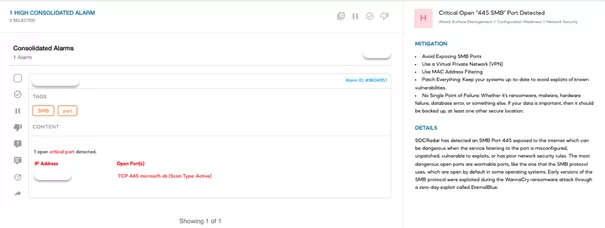
Citrix Targeted Using Unsafe Legacy Protocols
According to analysts, 60% of Microsoft Office 365 and G-Suite tenants have been attacked with IMAP-based password-scanning attacks.
The attackers target the misconfigurations on the obsolete and insecure IMAP protocol to circumvent MFA settings and compromise cloud-based accounts that provide access to SaaS applications. Citrix was reportedly one of these targets, which is odd given that they specialize in federated systems. According to the FBI, the attackers acquired a footing using password spraying and defeated additional protection layers.
It is difficult for system administrators to set up and activate MFA when legacy protocols such as POP or IMAP are in use. Attacks against Office 365 and G-Suite cloud accounts utilizing IMAP are challenging to defend against with multi-factor authentication, with service accounts and shared mailboxes especially vulnerable.
Recommendations Against Security Misconfigurations
Harden the process: A repeatable hardening procedure expedites and simplifies the deployment of another adequately secured environment. The configuration of the development, QA, and production environments should be identical, with separate credentials used for each domain. You should automate this procedure to reduce the work required to establish a new secure environment.
Pay attention to your digital footprint: Continuously assess your digital footprint to prevent any exposed attack surface on the wild.
Configure properly: As part of the patch management process, a duty to examine and update the configurations applicable to all security notes, updates, and patches. Review storage permissions in the cloud. With segmentation, containerization, or cloud security groups, a segmented application architecture effectively and securely separates components or tenants (ACLs).
Implement IAM (Identity and Access Management): Ensure that only authorized users can access sensitive data or systems by properly configuring access restrictions.
Employ automated security tools: Utilize automated security tools like security scanners, integrity verifiers, and configuration checkers to identify and address misconfigurations and other vulnerabilities promptly.
Conclusion
It is important to remember that security is an ongoing process and requires constant monitoring, testing, and maintenance to ensure systems are correctly configured and secured. The reason to emphasize automated tools and process management is to decrease the involvement of the human element. Even the most experienced security personnel can sometimes miss a small detail that would lead to immense consequences. According to Verizon’s 2022 Data Breaches Investigations Report, 82% of data breaches involved a human element. Whether directly exposing information by misconfiguring databases or making a mistake enabling cybercriminals to access the organization’s systems.
With timely, relevant, and actionable threat intelligence by SOCRadar’s Attack Surface Management (ASM), organizations can overcome misconfiguration challenges through a comprehensive view of assets by ingesting, deduplicating, and correlating data from IT and security solutions. Additionally, Digital Risk Protection (DRP) can protect digital assets and leverage Cyber Threat Intelligence (CTI) monitoring to highlight specific security risks.
CTI is a strategy that can prevent data breaches and save money on incident cleanup by providing businesses with an understanding of the most significant risks to their infrastructure and instructions on how to protect against them. SOCRadar’s unified CTI product can safeguard externally reachable digital assets. It is important to remember that security is an ongoing process and requires constant monitoring, testing, and maintenance to ensure systems are correctly configured and secured.



































