
Severe Vulnerabilities in Cisco IOS, IOS XE and Other Products Addressed – Patch Now
Cisco, a leading provider of network technologies, has issued new security advisories addressing 16 vulnerabilities affecting key products, including Cisco IOS, IOS XE, and Catalyst SD-WAN Routers.
Released on September 25, 2024, the advisories detail nine high severity vulnerabilities, including those that could lead to Denial-of-Service (DoS) attacks or privilege escalation, among other risks that may enable further malicious activities across compromised networks.
Cisco IOS, IOS XE, and More Impacted by DoS, Privilege Escalation, CSRF Flaws (CVE-2024-20381, CVE-2024-20467, …)
Cisco has recently addressed a number of high-severity vulnerabilities impacting several of its core products, including Cisco IOS XE, Catalyst SD-WAN Routers, and other key network technologies. Below, we detail the cause and impact of these vulnerabilities, as well as the individual products that were affected:
CVE-2024-20381 (CVSS 8.8) – Privilege Escalation Vulnerability in Multiple Cisco Products
A critical flaw in the JSON-RPC API of Cisco Crosswork Network Services Orchestrator (NSO), Optical Site Manager, and RV340 Dual WAN Gigabit VPN Routers could allow a remote attacker with access privileges to modify application configurations. Exploiting this vulnerability could result in unauthorized user account creation or privilege escalation, potentially compromising system integrity.
This issue also affects ConfD if the JSON-RPC API is enabled.
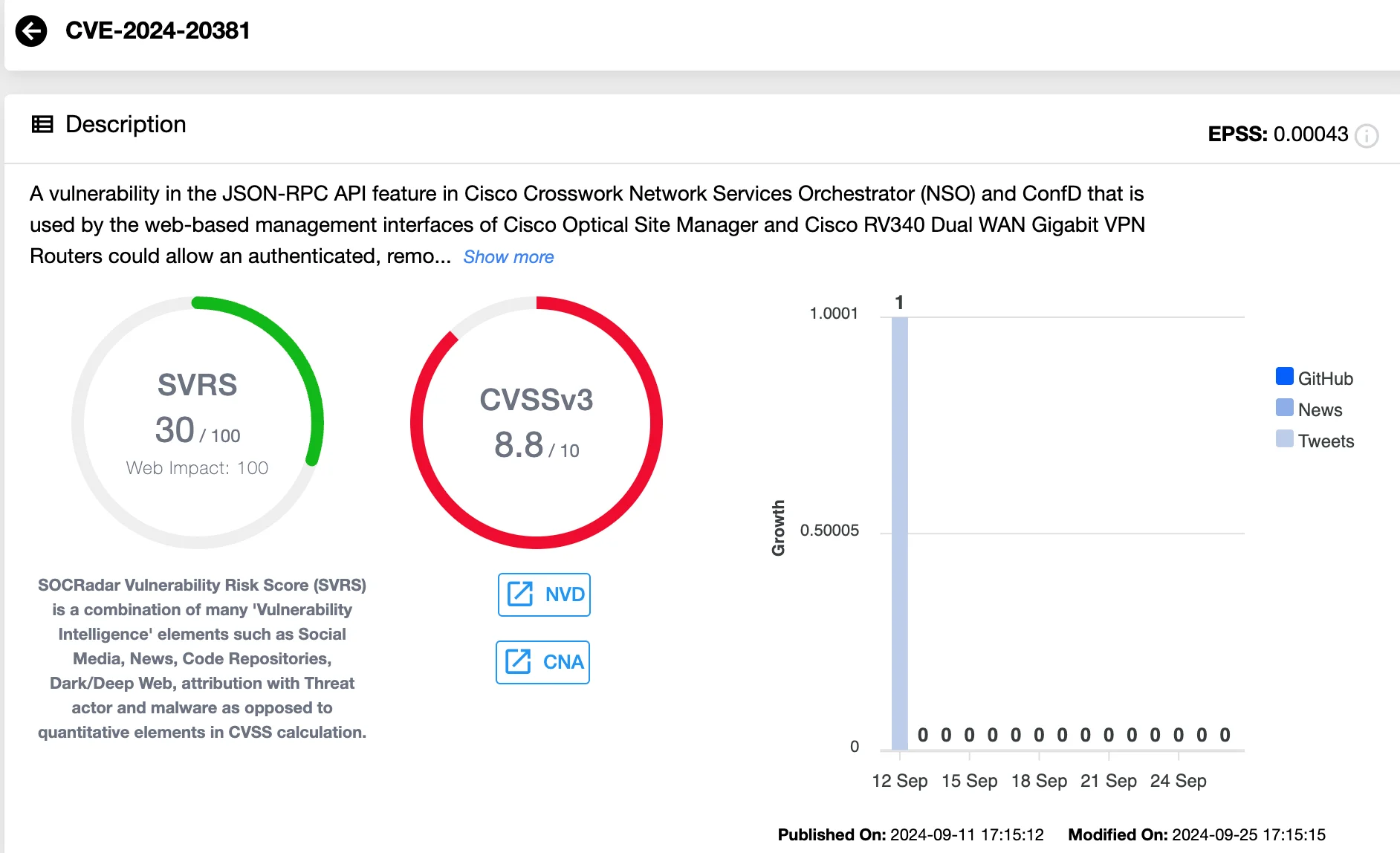
Details of CVE-2024-20381 (SOCRadar Vulnerability Intelligence)
CVE-2024-20467 (CVSS 8.6) – DoS Vulnerability in Cisco IOS XE IPv4 Fragmentation
In Cisco IOS XE, improper resource management in the IPv4 fragmentation reassembly code could lead to a Denial-of-Service (DoS) attack. An attacker could send fragmented packets to trigger a system reload, disrupting services. Affected devices include the Cisco ASR 1000 Series and Cisco cBR-8 Routers running specific versions of IOS XE (17.12.1 or 17.12.1a).
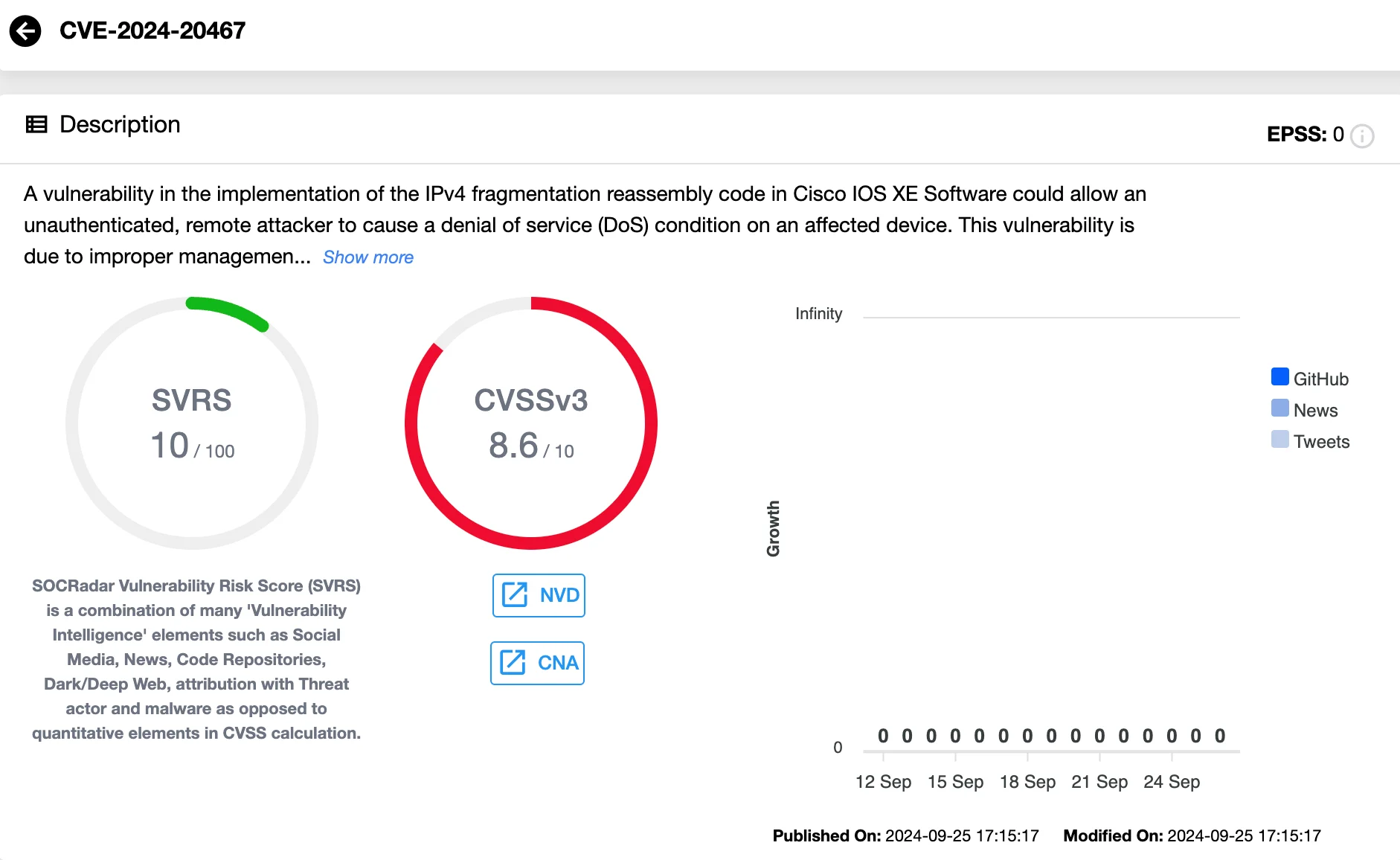
Details of CVE-2024-20467 (SOCRadar Vulnerability Intelligence)
CVE-2024-20436 (CVSS 8.6) – DoS Vulnerability in Cisco IOS XE HTTP Server Telephony Services
A vulnerability in the HTTP Server feature in Cisco IOS XE, when paired with the Telephony Service feature, could allow an attacker to cause a device to reload, leading to a DoS condition. This issue arises from a null pointer dereference triggered by malicious HTTP requests.
CVE-2024-20480 (CVSS 8.6) – DoS Vulnerability in Cisco IOS XE SD-Access Fabric Edge Node
Cisco IOS XE’s DHCP Snooping feature on Software-Defined Access (SD-Access) fabric edge nodes can be exploited by sending specific DHCP packets, resulting in high CPU utilization and causing a DoS condition. A manual reload is required for recovery, which disrupts network traffic.
CVE-2024-20464 (CVSS 8.6) – DoS Vulnerability in Cisco IOS XE PIM
In the Protocol Independent Multicast (PIM) feature of Cisco IOS XE, insufficient validation of IPv4 PIMv2 packets could allow attackers to cause affected devices to reload, triggering a DoS condition. Devices running vulnerable releases with PIM enabled are at risk, though IPv6 PIM is not affected by this vulnerability.
CVE-2024-20433 (CVSS 8.6) – DoS Vulnerability in Cisco IOS & IOS XE Resource Reservation Protocol
Cisco IOS and IOS XE Software are vulnerable due to a buffer overflow in the Resource Reservation Protocol (RSVP) feature. Malicious RSVP traffic could cause a system reload, resulting in a DoS attack. Only devices with RSVP enabled are affected.
CVE-2024-20455 (CVSS 8.6) – DoS Vulnerability in Cisco Catalyst SD-WAN Routers
A vulnerability in Cisco IOS XE Software’s Unified Threat Defense (UTD) traffic classification for SD-WAN IPsec tunnels could allow attackers to trigger a DoS condition by sending crafted packets. Only devices with UTD installed and enabled are vulnerable, but those using Generic Routing Encapsulation (GRE) tunnels are unaffected.
Additionally, the lowest scored vulnerabilities in the high-severity category are as follows:
- CVE-2024-20437 (CVSS 8.1): A Cross-Site Request Forgery (CSRF) vulnerability in the web-based management interface of Cisco IOS XE.
- CVE-2024-20350 (CVSS 7.5): A vulnerability in the SSH server of Cisco Catalyst Center, which could enable impersonation via a Machine-in-the-Middle attack.
SOCRadar’s Vulnerability Intelligence module provides detailed updates on the newest CVEs, including exploit availability and mentions. With comprehensive insights, your security team can prioritize patching and proactively defend against potential exploits before they impact your systems.
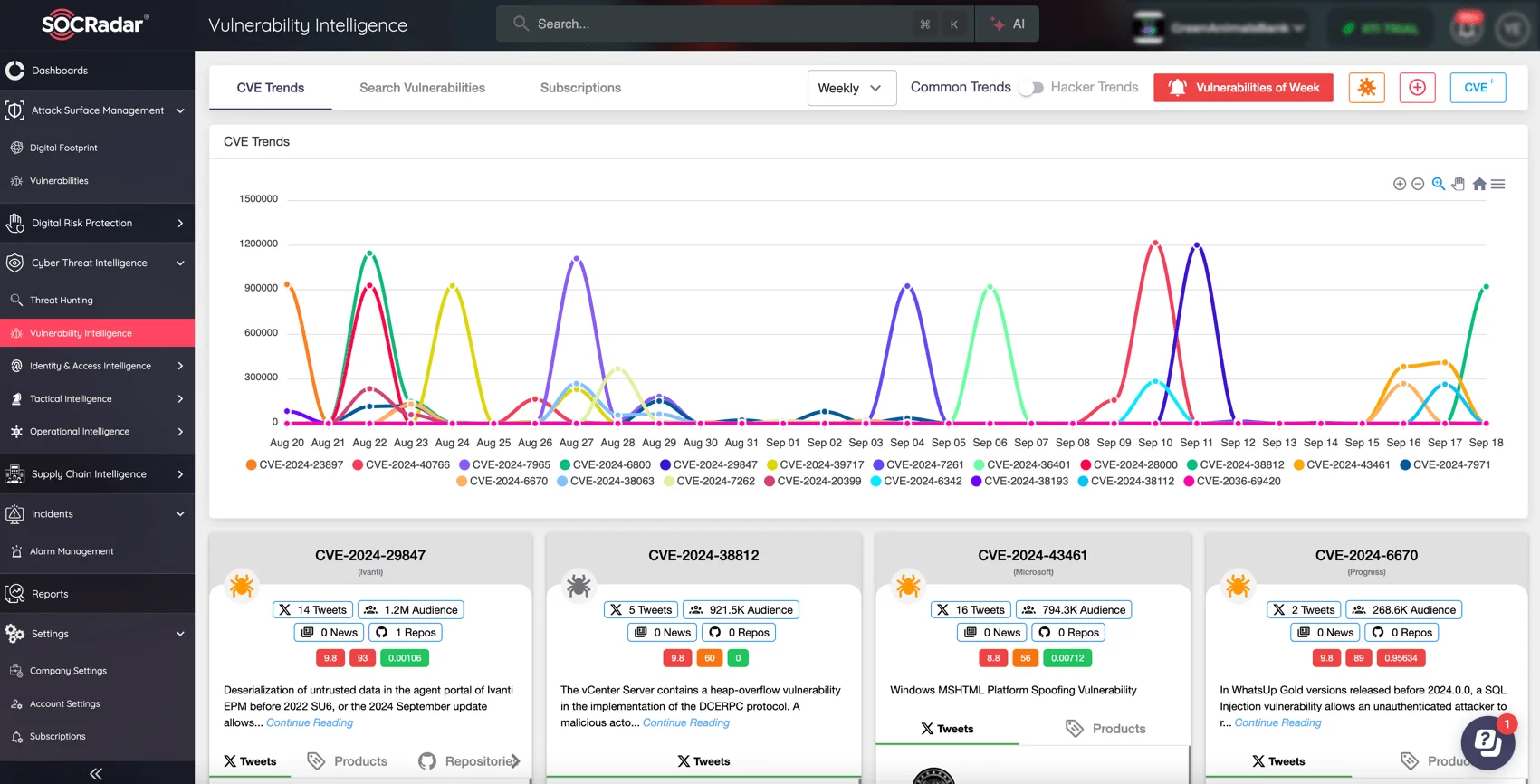
Gain more insights into vulnerabilities with SOCRadar’s Vulnerability Intelligence
Additional Vulnerabilities in Cisco Products
While the previous vulnerabilities are high severity, the remaining vulnerabilities in the update with medium severity ratings still pose significant risks across various Cisco products.:
- CVE-2024-20434: Denial of Service vulnerability in Cisco Catalyst 9000 Series Switches, potentially causing device crashes.
- CVE-2024-20508: Security policy bypass and DoS vulnerability in Cisco Unified Threat Defense Snort Intrusion Prevention System Engine for Cisco IOS XE Software.
- CVE-2024-20475: Cross-Site Scripting vulnerability in Cisco Catalyst SD-WAN Manager, which could allow malicious code injection.
- CVE-2024-20496: UDP Packet Validation flaw in Cisco SD-WAN vEdge Software, which could lead to DoS attacks.
- CVE-2024-20465: Access Control List (ACL) bypass vulnerability in Cisco IOS Software on Cisco Industrial Ethernet Series Switches.
- CVE-2024-20414: Cross-Site Request Forgery (CSRF) vulnerability in Cisco IOS and IOS XE Software Web UI.
- CVE-2024-20510: ACL bypass vulnerability in Cisco IOS XE Software for Wireless Controllers during CWA Pre-Authentication.
Apply the Patches for the Latest Cisco Vulnerabilities
The vulnerabilities discussed in this article, ranging from Denial of Service (DoS) to Privilege Escalation, pose significant risks to organizations using affected Cisco products.
As history has shown, delayed patching can lead to serious consequences. For instance, in 2023, APT28 exploited an old vulnerability, CVE-2017-6742 (CVSS: 8.8), in Cisco IOS and IOS XE software to deploy the Jaguar Tooth malware on routers.
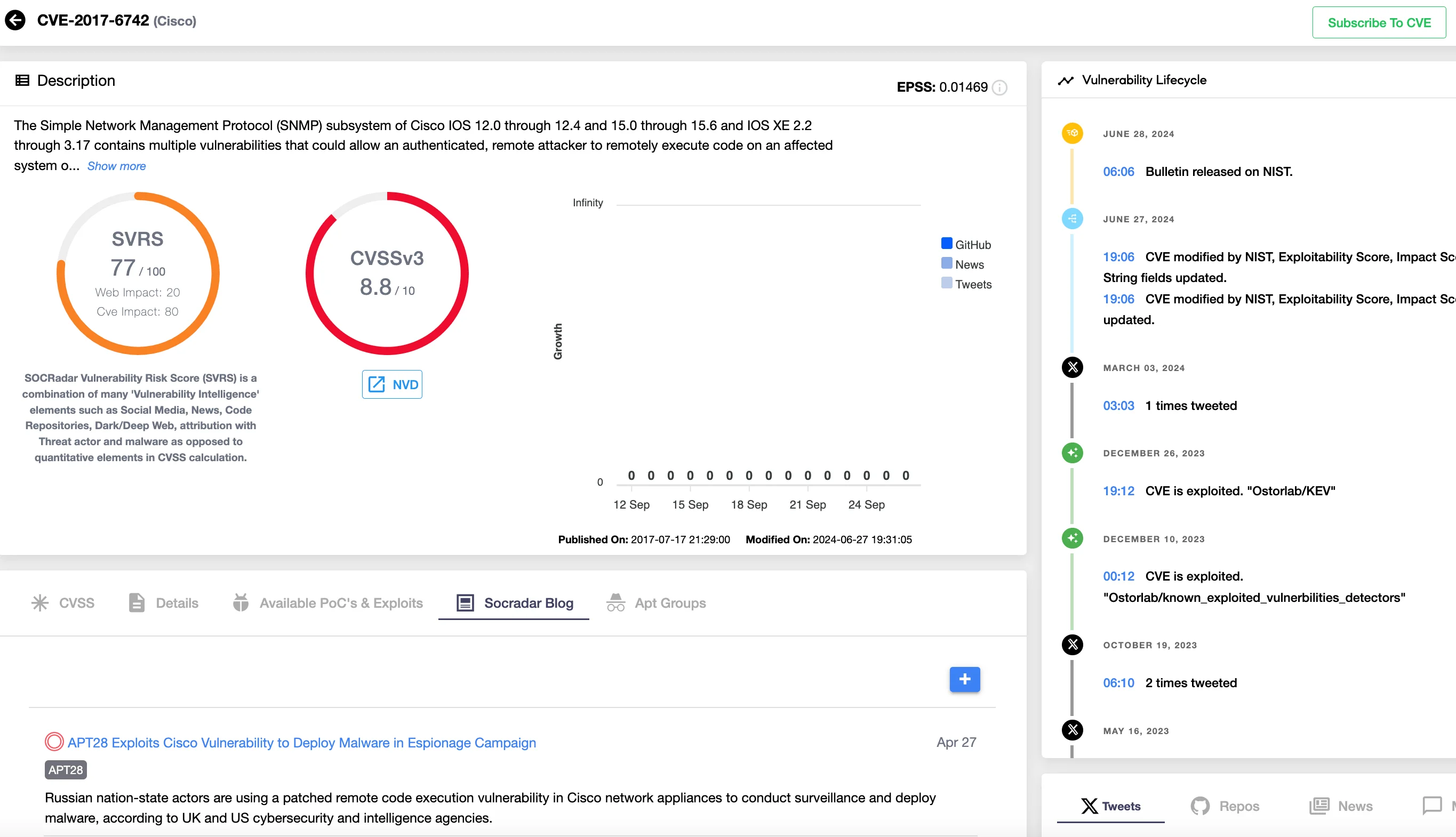
Details and the latest activity on CVE-2017-6742, shown on SOCRadar’s Vulnerability Intelligence module
Given the critical nature of the current vulnerabilities, timely patching is important to safeguard against potential exploitation.
For more information on the vulnerabilities and Cisco’s recommended mitigations, refer to the official security advisories. It is also important to note that most of these vulnerabilities are part of Cisco’s September 2024 IOS and IOS XE Security Advisory Bundled Publication, which you can refer to for a more targeted approach to addressing vulnerabilities in these products.
Protect Your Digital Assets with SOCRadar’s Attack Surface Management Module
SOCRadar’s Attack Surface Management (ASM) offers real-time monitoring of your organization’s digital assets. By identifying vulnerabilities in software, exposed sensitive data, and shadow IT, ASM provides the insights needed to address risks before they are exploited.
Stay ahead of evolving cyber risks with dynamic, automated detection and protection from SOCRadar’s industry-leading ASM solution.
With continuous visibility into your attack surface, SOCRadar’s advanced monitoring equips your security team to take proactive steps in mitigating threats.




































