
ShadowRoot Ransomware Campaign
The ShadowRoot ransomware campaign represents a significant cybersecurity threat targeting Turkish businesses.
This campaign, identified by the X-Labs research team, utilizes phishing emails to distribute malicious PDF attachments, which, when interacted with, download and execute a ransomware payload.
This article provides an in-depth campaign analysis, including its attack vectors, execution methods, and mitigation strategies.
How Does ShadowRoot Achieve Initial Access? The Campaign’s Attack Vector
The ShadowRoot campaign initiates with phishing emails from “internet[.]ru,” featuring PDFs disguised as legitimate invoices. These PDFs contain hidden malicious URLs that, when clicked, prompt the download of a ransomware-launching executable from a compromised GitHub repository.
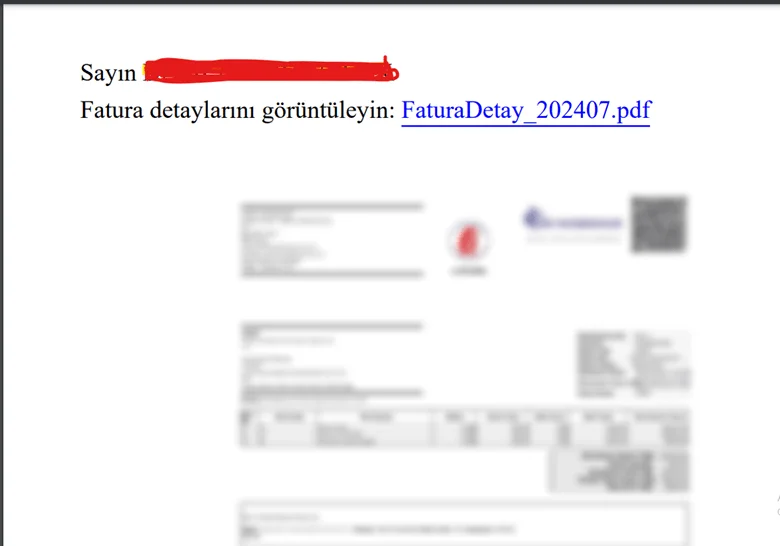
PDF attachment
The executable, a 32-bit Delphi binary, further deploys several files, including a key executable named RootDesign.exe, which is obscured using .NET Confuser Core version 1.6 to bypass standard security measures, and Uninstall.exe and Uninstall.ini.
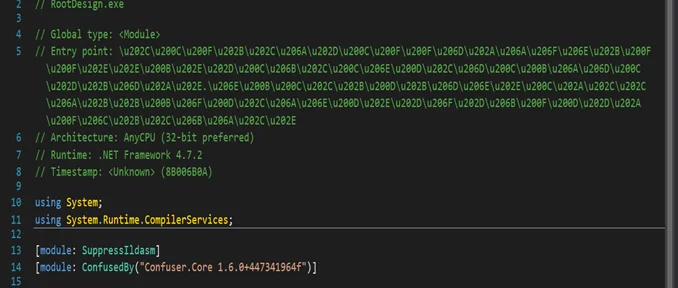
Packer info
ShadowRoot’s Obfuscation Techniques
The ShadowRoot ransomware employs advanced obfuscation techniques, utilizing classes and functions named with special characters to bypass security applications. This obfuscation complicates detection and analysis, allowing the malware to remain undetected for extended periods.
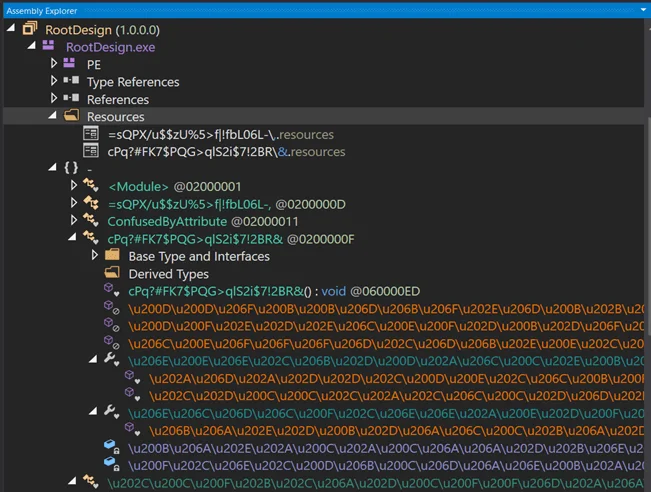
Obfuscated function and class name
Further Execution and Encryption
Following the payload drop, the initial executable triggers a PowerShell command to run RootDesign.exe in hidden mode:
The ransomware then creates several mutexes to ensure its smooth operation:
- LocalZonesCacheCounterMutex
- LocalZonesLockedCacheCounterMutex
- _SHuassist.mtx
It proceeds to spawn recursive threads, increasing memory consumption, and logs all activities in C:TheDreamlog.txt. Subsequently, the malware encrypts various system-critical files, appending the “.ShadowRoot” extension, and drops a ransom note (readme.txt) on the desktop.
Ransom Note and Communication
ShadowRoot’s ransom note, written in Turkish, instructs victims to contact the attackers via email for payment and decryption instructions.
Additionally, the ransomware establishes an SMTP command and control (C2) connection to smtp[.]mail[.]ru on port 587, transmitting details to email accounts associated with the domain “internet[.]ru”.
Find out more about the ShadowRoot ransomware campaign on the SOCRadar XTI platform
Mitigation Strategies Against Ransomware Attacks
The ShadowRoot ransomware campaign highlights the ongoing threat posed by cybercriminals targeting businesses through sophisticated phishing attacks. Despite its rudimentary characteristics, the campaign effectively employs obfuscation and encryption techniques to evade detection and cause significant disruption. By implementing strong security measures and staying vigilant, businesses can mitigate the risks associated with such attacks and protect their critical assets.
To defend against such ransomware attacks, the following strategies are recommended:
- Implement Multi-Factor Authentication (MFA): Enhances security by requiring multiple verification forms.
- Regularly Update and Patch Systems: Closes vulnerabilities that attackers could exploit.
- Employee Training on Phishing: Educates staff on recognizing and reporting phishing attempts.
- Use Endpoint Protection Solutions: Deploys advanced solutions capable of detecting and preventing sophisticated malware.
- Network Segmentation: Limits the spread of malware within the network, reducing potential damage.
In the event of a ransomware attack, it is also crucial to:
- Establish an Incident Response Plan: Develop a comprehensive plan to manage and contain the breach.
- System Restoration: Use clean backups to restore systems and ensure the removal of all malicious code.
- Conduct Network Forensics: Perform detailed analyses to understand the breach’s scope.
- Reset Credentials: Change all affected credentials and enforce MFA to prevent further unauthorized access.
- Communicate with Stakeholders: Inform all relevant parties about the breach and the measures to address it.
For information on other similar cyber threat campaigns, visit the SOCRadar LABS Campaigns page.
Campaigns page on SOCRadar LABS
The Campaigns page provides detailed analyses and updates on various cyber threat campaigns, including ShadowRoot and many others, helping organizations stay informed and prepared.


































