
SOCRadar Denmark Threat Landscape Report: 9 Danish Companies Targeted Every 9 Days
Cybercrime is a threat that closely concerns public authorities, companies, and residents in Denmark, as it is around the world. The fact that threat actors adapt rapidly to the “new normal,” improve their skills and come up with brand new attack techniques makes this issue perhaps more critical than ever before.
In response to the ever-evolving approach of attackers, it is increasingly important for governments, companies, and various organizations to have a dynamic understanding of cybersecurity. SOCRadar’s Threat Landscape Report helps organizations gain a more robust security posture with industry, country, or region-based data by closing gaps in cyber threat intelligence.
Click the button below to download the full Denmark Threat Landscape Report compiled by the SOCRadar CTIA Team from the surface, deep and dark web, cybersecurity researchers, and more.
29 Threat Actors Targeting Denmark
When SOCRadar analysts examined posts targeting Denmark entities on the dark web, they observed that RDP and VPN hacking network access sales were common. It’s nothing new when we consider that the dark web economy, in general, is driven by the sale of hacker tools and databases. However, the fact that the most targeted industry is e-commerce raises concerns about the leakage of sensitive user data.
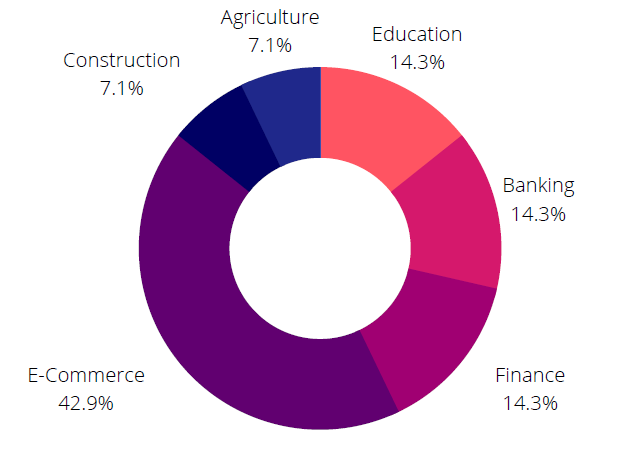
Looking at a few key incidents in 2021, it’s the first time a website has been leaked, and over 8,000 websites have admin access available for sale.
Ransomware Targets Danish Telecommunication Company
Ransomware threats are skyrocketing in Denmark as well as everywhere else. The attackers threatened to extort data by encrypting the victims’ systems, and a lot of data linked to ransomware attacks was put up for sale on the black market. The most used methods for initial access by attackers trying to gain profit with the double extortion technique were:
- Vulnerability exploit
- Unsecure RDP
- Credential Access
The most striking was the attack on a telecommunication company in Denmark. Officials admitted that threat actors had infiltrated the server and accessed the data of some employees.
Top Ransomware Groups Targeting Denmark
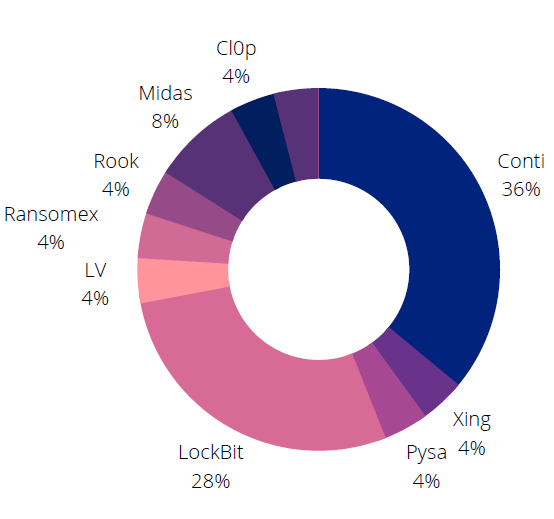
- REvil: REvil is a ransomware-as-a-service (RaaS) operator known to be based in Russia. The gang, which was the name behind major operations such as the Colonial Pipeline attack, was destroyed with an operation in Russia in January 2022.
- Conti: The gang, which targets leading organizations in Denmark, has recently come to the fore after it sided with Russia in the Russia-Ukraine war and the internal correspondence of the group leaked.
- Pysa: The first ransomware version of the relatively new gang appeared in 2018. It was re-released as open-source in 2019. Among its victims are several Denmark companies.
For more details and analysis of the Denmark threat landscape, download the full report.



































