
Sophos Firewall Update Resolves RCE and Privilege Escalation Vulnerabilities (CVE-2024-12727, CVE-2024-12728, CVE-2024-12729)
Recent security patches for Sophos Firewall address several serious vulnerabilities, including two classified as critical. These flaws could lead to Remote Code Execution (RCE) or expose a privileged account, potentially giving attackers the means to escalate their activities if exploited.
Details of the Latest Sophos Firewall Vulnerabilities
Sophos has released updates for two critical vulnerabilities, alongside one high-severity vulnerability, affecting Sophos Firewall v21.0 GA (21.0.0) and older versions. These security vulnerabilities pose significant risks, including Remote Code Execution (RCE) and Privilege Escalation. Below, we outline these vulnerabilities and their potential impacts.
CVE-2024-12727 (CVSS 9.8) – Pre-Auth SQL Injection Leads to RCE
This pre-auth SQL injection vulnerability resides in the email protection feature of Sophos Firewall, granting access to its reporting database and potentially leading to Remote Code Execution (RCE). However, exploitation requires a specific configuration where Secure PDF eXchange (SPX) is enabled, coupled with the firewall operating in High Availability (HA) mode.
Sophos reports that this issue affects approximately 0.05% of devices, making it relatively rare but critical for those impacted.
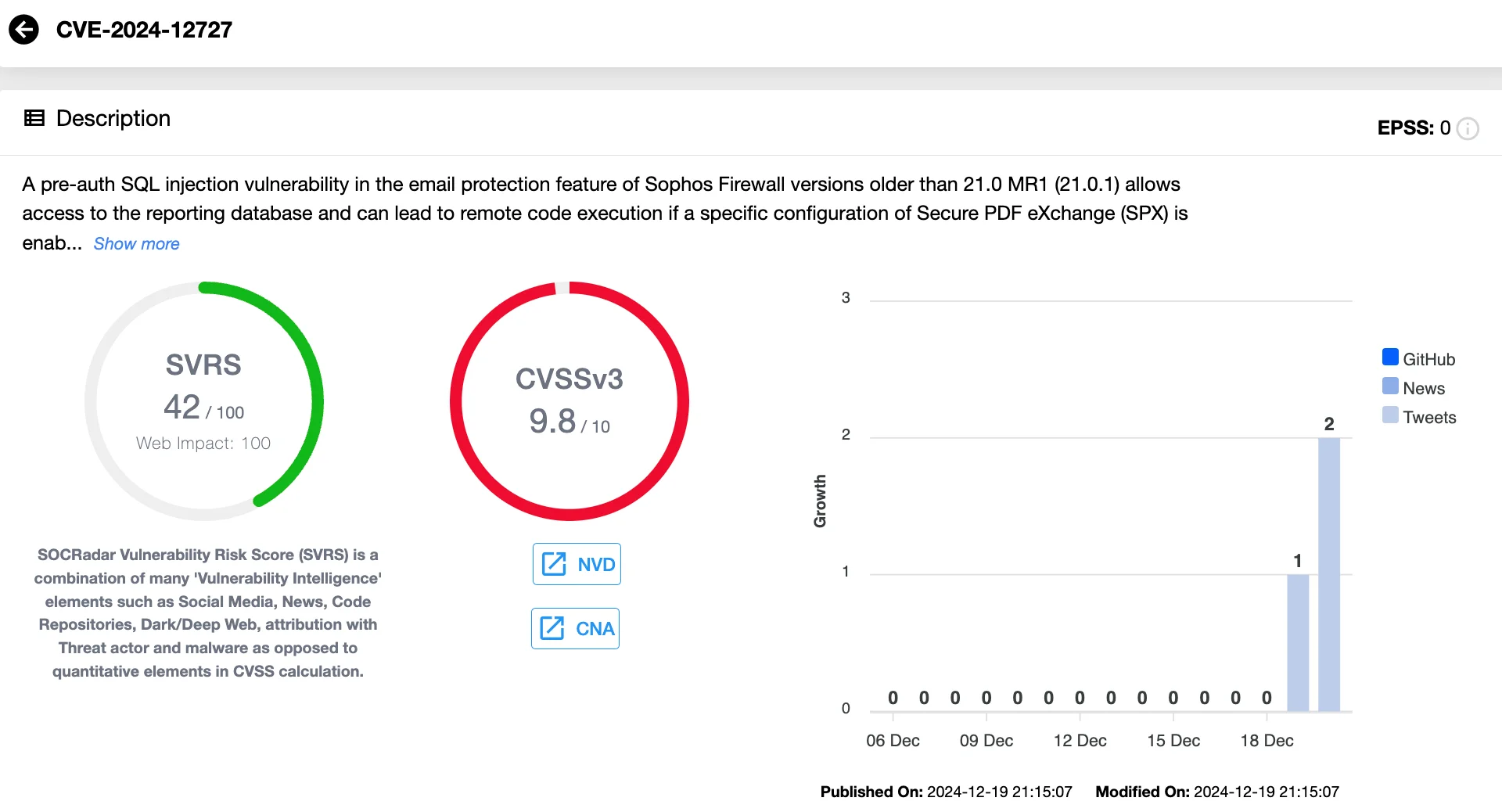
Vulnerability card of CVE-2024-12727 (SOCRadar Vulnerability Intelligence)
CVE-2024-12728 (CVSS 9.8) – Weak SSH Login Passphrase Resulting in Privilege Escalation
This vulnerability stems from the use of a suggested, non-random SSH login passphrase for High Availability (HA) cluster initialization. Sophos found that the passphrase remained active even after the HA setup was complete, potentially exposing a privileged system account where SSH is enabled.
Sophos estimates that approximately 0.5% of devices are affected by this flaw, making the exposure broader compared to CVE-2024-12727.
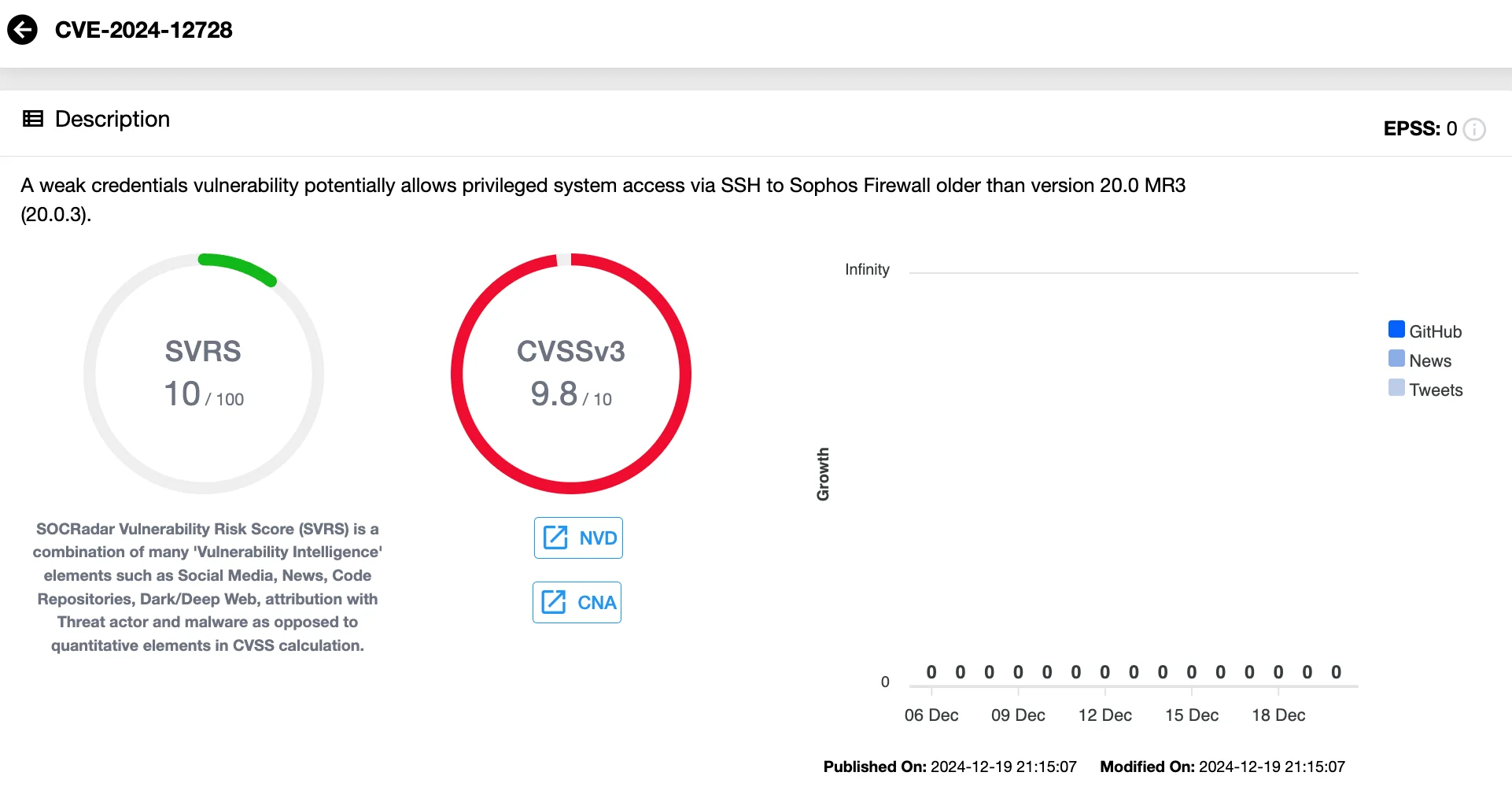
Vulnerability card of CVE-2024-12728 (SOCRadar Vulnerability Intelligence)
CVE-2024-12729 (CVSS 8.8) – Post-Auth Code Injection Paves the Way for RCE
The final vulnerability addressed in this update, CVE-2024-12729, is a post-auth code injection flaw within the User Portal of Sophos Firewalls. Although rated slightly lower than the other two vulnerabilities, it still poses a significant risk, allowing authenticated users to achieve Remote Code Execution (RCE).
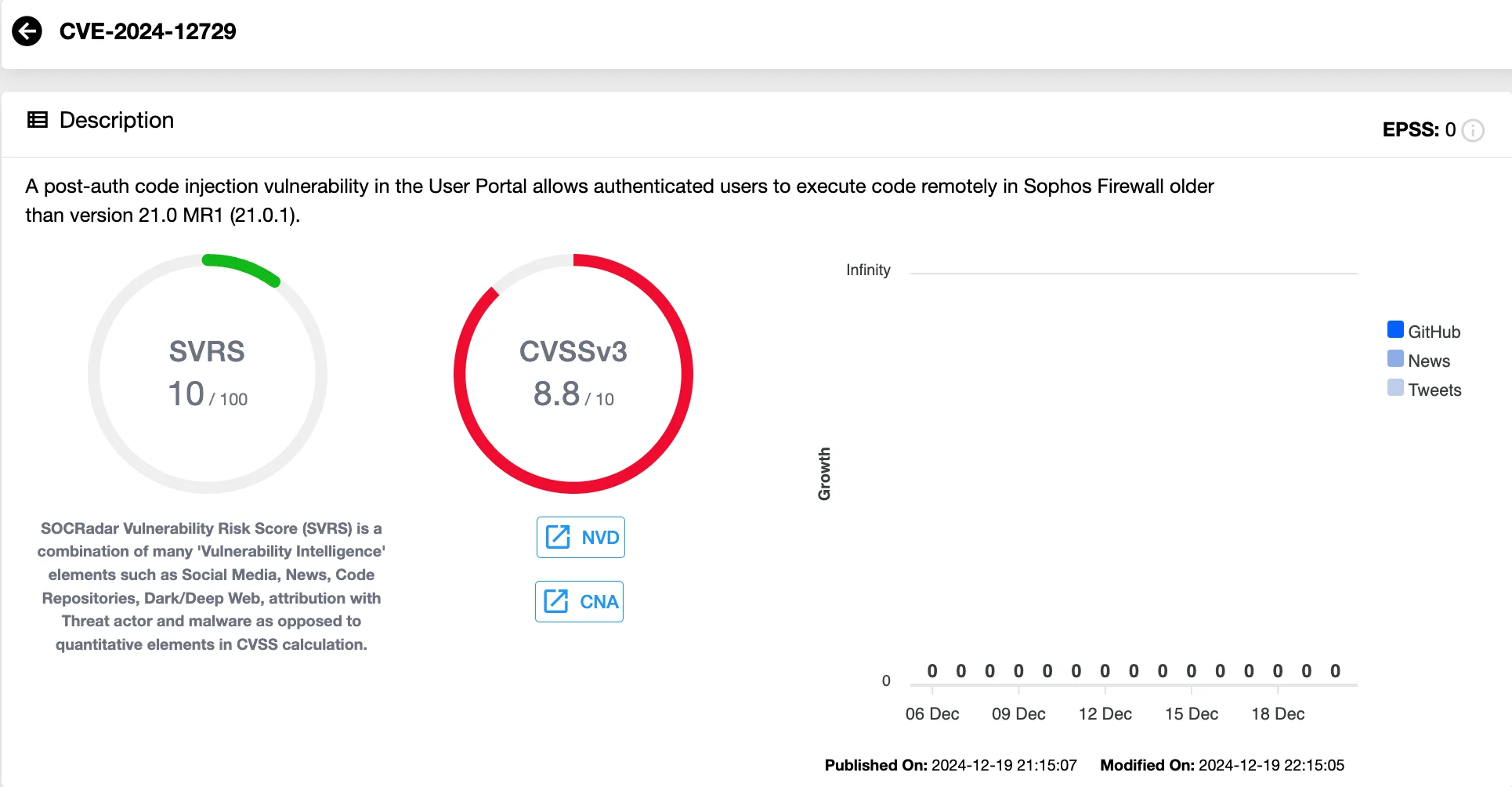
Vulnerability card of CVE-2024-12729 (SOCRadar Vulnerability Intelligence)
The vulnerabilities CVE-2024-12727 and CVE-2024-12729 were discovered and responsibly disclosed to Sophos through its bug bounty program, while the privilege escalation issue, CVE-2024-12728, was identified during Sophos’ internal security testing.
Are the Latest Sophos Firewall Vulnerabilities Being Exploited?
According to Sophos, there have been no reports or observations of these vulnerabilities being exploited in the wild at this time. However, organizations are advised to apply the necessary patches promptly to mitigate any potential risk.
For organizations looking to stay ahead of evolving threats, SOCRadar’s Vulnerability Intelligence module is an essential tool. It provides real-time monitoring and actionable alerts about vulnerabilities, including updates and hacker trends, the availability of exploit code, and the lifecycle of vulnerabilities.
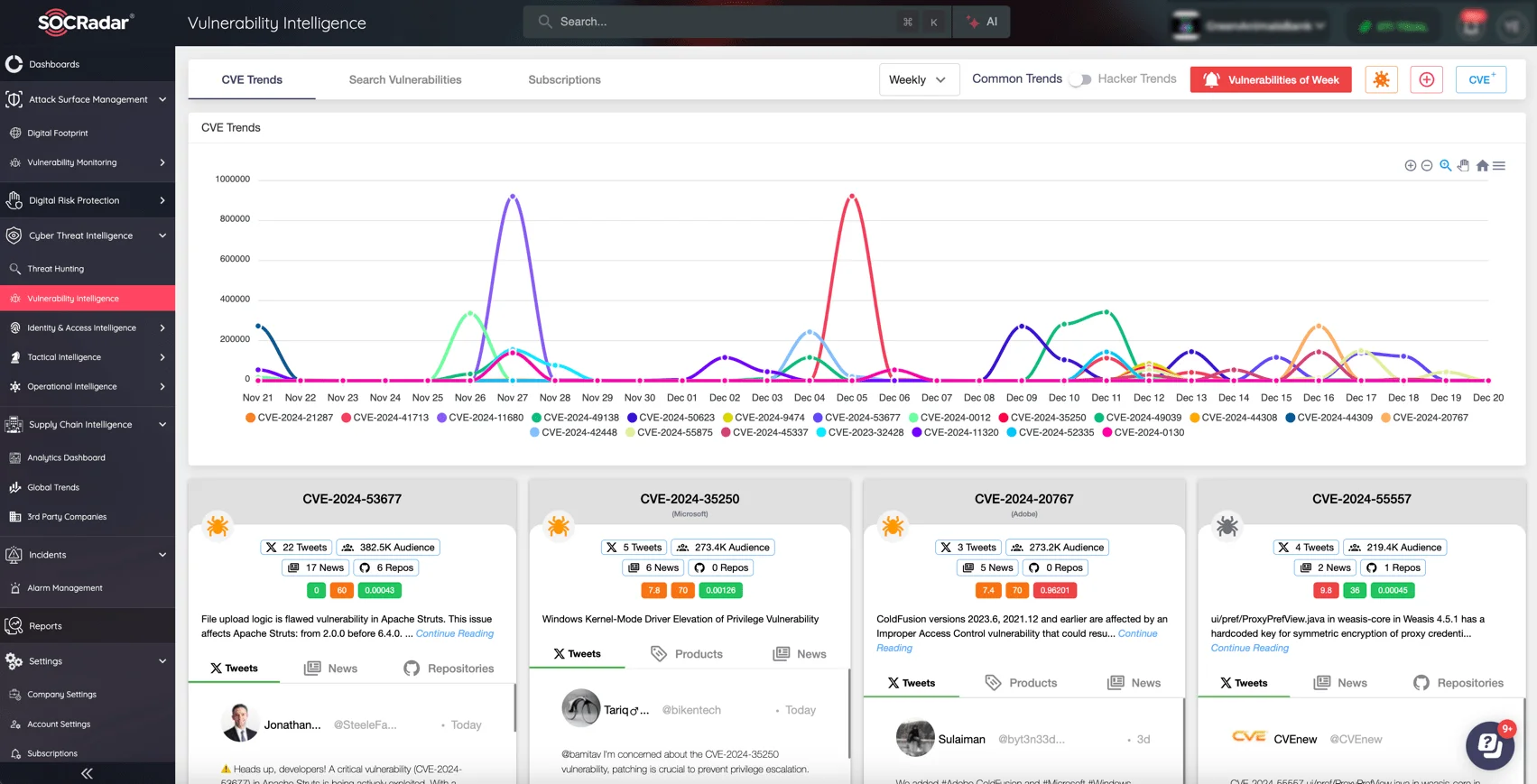
Track new CVEs and exploits with SOCRadar Vulnerability Intelligence
By offering detailed insights into vulnerability details and tracking their progression from discovery to potential exploitation, this module keeps your security team informed at all times.
Applying Patches for Sophos Firewall Vulnerabilities
Sophos has already issued hotfixes to address the recent vulnerabilities in supported versions of Sophos Firewall. To ensure your system is protected, confirm that you are running a supported version and apply these updates promptly. Unsupported versions should be upgraded to receive the latest protections.
Here are the recommended remediation steps for each vulnerability:
- For CVE-2024-12727: Hotfixes were released on December 17, 2024, for several supported versions, with a permanent fix included in v21 MR1 and newer.
- For CVE-2024-12728: Hotfixes became available between November 26 – 27, 2024, depending on the version, with a full fix in v20 MR3 and later versions.
- For CVE-2024-12729: Hotfixes were rolled out between December 4 – 10, 2024, across supported versions. The issue has been resolved in v21 MR1 and newer versions.
Timely application of these updates ensures your system remains secure against these vulnerabilities, minimizing potential risks. To confirm whether the hotfixes have been successfully applied, refer to Sophos’ Knowledge Base Article KBA-000010084.
Sophos Firewall customers with the default “Allow automatic installation of hotfixes” feature enabled on remediated versions are already protected. No further action is needed in such cases.
Are There Any Workarounds?
Sophos’ official advisory provides workaround recommendations for two of the vulnerabilities: CVE-2024-12728 and CVE-2024-12729. These measures can reduce exposure risks until you can apply the permanent fixes.
To address the risk associated with the persistent SSH passphrase (CVE-2024-12728) used during HA deployment:
- Restrict SSH access to a dedicated HA link that is physically separate.
- Reconfigure HA using a sufficiently long and random custom passphrase.
- Disable WAN access via SSH and use VPN or Sophos Central for remote access and management.
Additionally, Sophos recommends preventing external attackers from exploiting CVE-2024-12729 by:
- Ensuring the User Portal and Webadmin are not accessible from the WAN.
- Disabling WAN access to these interfaces and using VPN or Sophos Central for secure management.
The company highlights the importance of following device access best practices to enhance overall security. For more detailed guidance on mitigating these vulnerabilities, refer to the official advisory.
Strengthen Your Security with SOCRadar’s Attack Surface Management (ASM)
Workarounds can provide temporary relief, but understanding and managing your organization’s exposed assets is vital for long-term security.
SOCRadar’s Attack Surface Management (ASM) module delivers continuous visibility into your digital footprint, helping you identify exposed assets and potential vulnerabilities before they can be exploited.
With ASM, you can:
- Discover and map exposed assets.
- Prioritize risks with actionable insights.
- Minimize your attack surface by addressing weak points proactively.
The ASM module page of SOCRadar: Monitor your company’s digital assets and vulnerabilities
By integrating SOCRadar ASM into your security strategy, you can ensure your systems remain resilient against evolving threats.


































