
Sumo Logic Security Breach: Unauthorized Access to AWS with Stolen Credentials
Sumo Logic, a cybersecurity company renowned for its expertise in cloud-based log management, analytics, and insights, recently disclosed a security breach. The breach came to light when the company detected unauthorized access to its Amazon Web Services (AWS) account.
Sumo Logic serves more than 2,100 enterprise customers worldwide. This incident, had it not been detected promptly, could have led to data exposure, causing harm to the company’s reputation as a cybersecurity provider, and serves as a stark reminder of the ongoing challenges in safeguarding digital assets within the cloud environment.
What Happened? How Did the Attacker Access AWS Credentials of Sumo Logic?
The breach was discovered by the company on November 3, 2023. An attacker had gained access to a Sumo Logic AWS account by utilizing stolen credentials.
In a security notice posted on the Sumo Logic website, the company clarified that, upon uncovering evidence of the breach, they had not detected any impacts on networks or systems, and customer data remained encrypted. Swiftly, the company contained the security breach within the compromised infrastructure and initiated the rotation of exposed credentials.
The notice further stated, “We have identified the potentially exposed credentials and have added extra security measures to further protect our systems. This includes improved monitoring and fixing any possible gaps to prevent any similar events and we are continuing to monitor our logs to look for further signs of malicious activity.”
While specific details are currently unavailable, potential avenues through which the attacker might have obtained the credentials include scenarios such as phishing attacks, compromised employee accounts, or vulnerabilities in third-party services.
Receive Security Alerts with SOCRadar and Mitigate Credentials’ Exposure
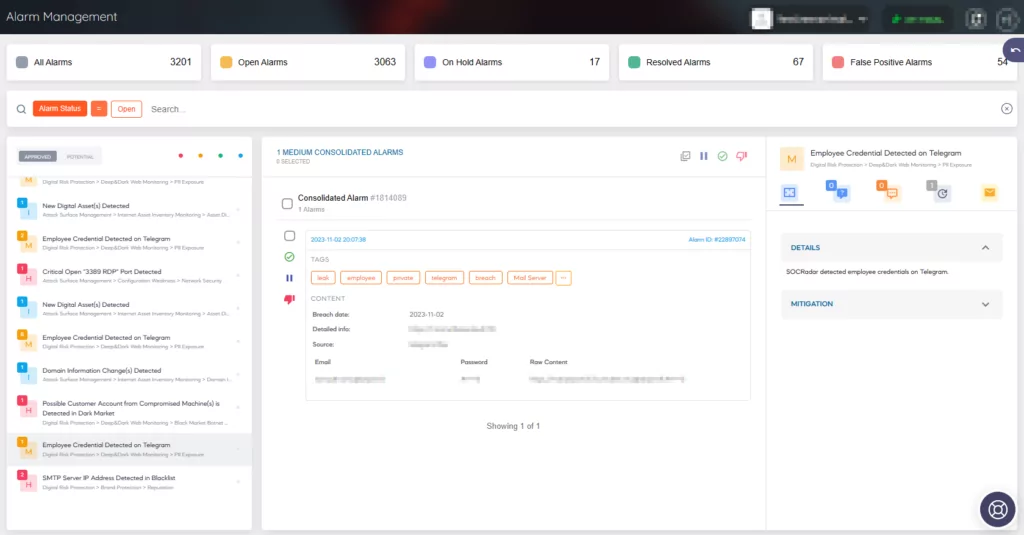
SOCRadar goes above and beyond in safeguarding your organization’s data by actively monitoring both the clear web and dark web to detect exposed data and credentials. With its advanced capabilities, SOCRadar can:
- Identify credentials stolen by malware or other threats, ensuring that you are promptly informed of any unauthorized access to your systems.
Monitor hundreds of dark web black markets to detect authentic credentials, providing you with early alerts to potential security threats.
Recommendations
The company recommends that customers take the following steps:
- Promptly update Sumo Logic API access keys.
- Rotate any credentials used to access Sumo Logic or shared with the company for accessing other systems.
The company had previously recommended rotating the following information as additional precautionary measures:
- Credentials for the Sumo Logic installed collectors.
- Third-party credentials that have been stored with the company for the purpose of data collection by their hosted collector (such as credentials for S3 access).
- Third-party credentials that have been stored with the company as part of webhook connection configuration.
- User passwords for Sumo Logic accounts.
As of November 8, Sumo Logic has updated these recommendations, stating they are reducing the scope as a result of their ongoing investigation. An additional precautionary measure that can now be considered for rotation is third-party credentials that have been stored with Sumo Logic as part of the webhook connection configuration.




































