
Tesla Charging Stations, Banque de France, and NOQ Group Targeted on Dark Web
SOCRadar’s Dark Web Team has highlighted a range of concerning cyber threats since last week. Among these are the launch of new tools and the sale of sensitive databases. A new exploit service, Impact Solutions, offers advanced payload delivery methods with antivirus bypass capabilities, while the Kraken phishing tool targets banks, cryptocurrency exchanges, and social media platforms. Additional findings include the alleged leak of Tesla EV charging station user data, unauthorized access to Banque de France systems, and a large-scale data breach affecting NOQ Group, a platform for event management.
Receive a Free Dark Web Report for Your Organization:
A New Exploit Service is Detected
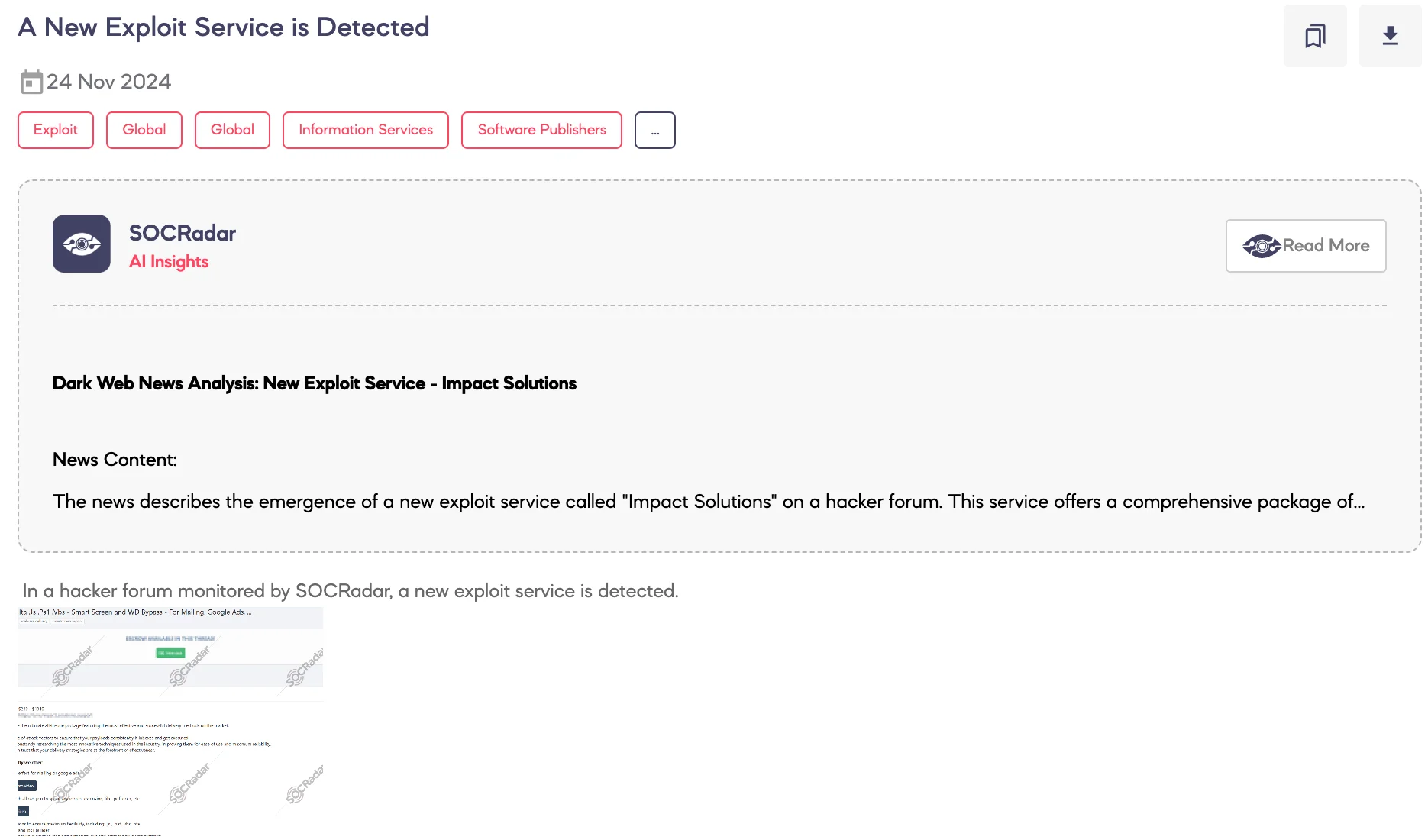
SOCRadar Dark Web Team identified a post on a hacker forum announcing a new exploit service called Impact Solutions. The threat actor described it as an all-in-one package providing advanced delivery methods and attack vectors for payload distribution. According to the threat actor, the service includes tools such as an HTML exploit builder, a .LNK/.URL builder for spoofing file extensions, and support for various formats like .JS, .BAT, and .PS1. Features allegedly include antivirus and Windows Defender bypass capabilities, Smart Screen bypass, payload persistence, and decoy file execution. The service is offered through three pricing tiers—Basic, Standard, and Pro—with increasing functionality and update frequency, designed to ensure maximum effectiveness against detection systems.
A New Phishing Service Kraken is Detected
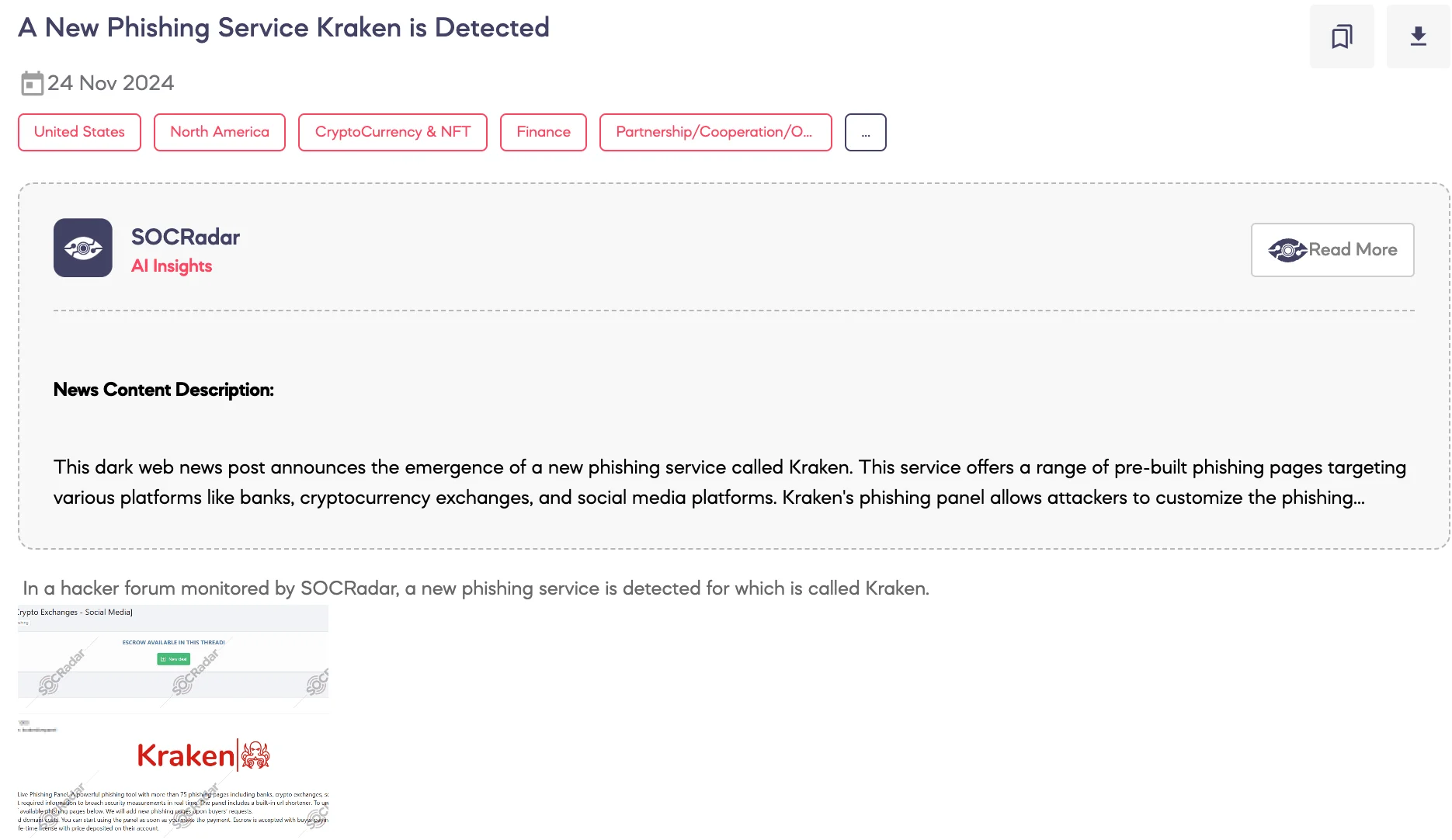
SOCRadar Dark Web Team detected a post on a hacker forum announcing a new phishing service called Kraken. According to the threat actor, Kraken is a sophisticated phishing tool that includes more than 75 phishing pages targeting various platforms such as banks, cryptocurrency exchanges, and social media. The phishing panel allows real-time manipulation of what victims see, enabling the collection of sensitive information.
The tool also features a built-in URL shortener and offers customization options for phishing pages upon request. Hosting and domain costs are included in the purchase price, and the service is available immediately after payment. Testing is restricted to moderators and buyers committing to a lifetime license with an escrow option available, subject to the buyer covering the fee.
Alleged Database of Tesla EV Charge is Leaked
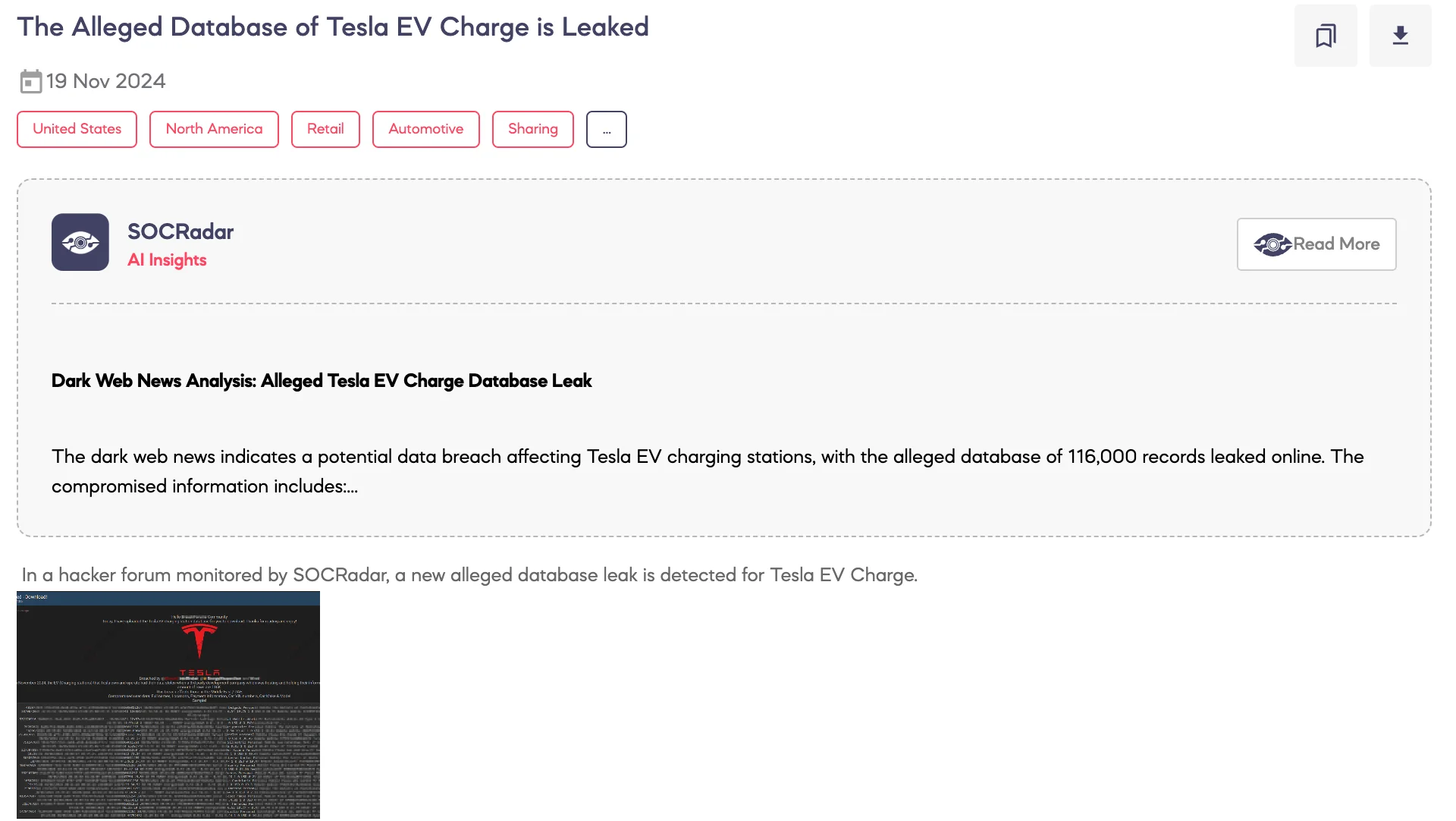
On November 19, SOCRadar detected a post on a hacker forum in which a threat actor claimed to have uploaded a database allegedly belonging to Tesla EV charging stations. The actor stated that the breach occurred in November 2024 and involved a third-party development company hosting Tesla’s data. The leaked database reportedly contained approximately 116,000 rows of user information, including full names, locations, payment details, and vehicle information.
Alleged Unauthorized Access Sale is Detected for Banque de France
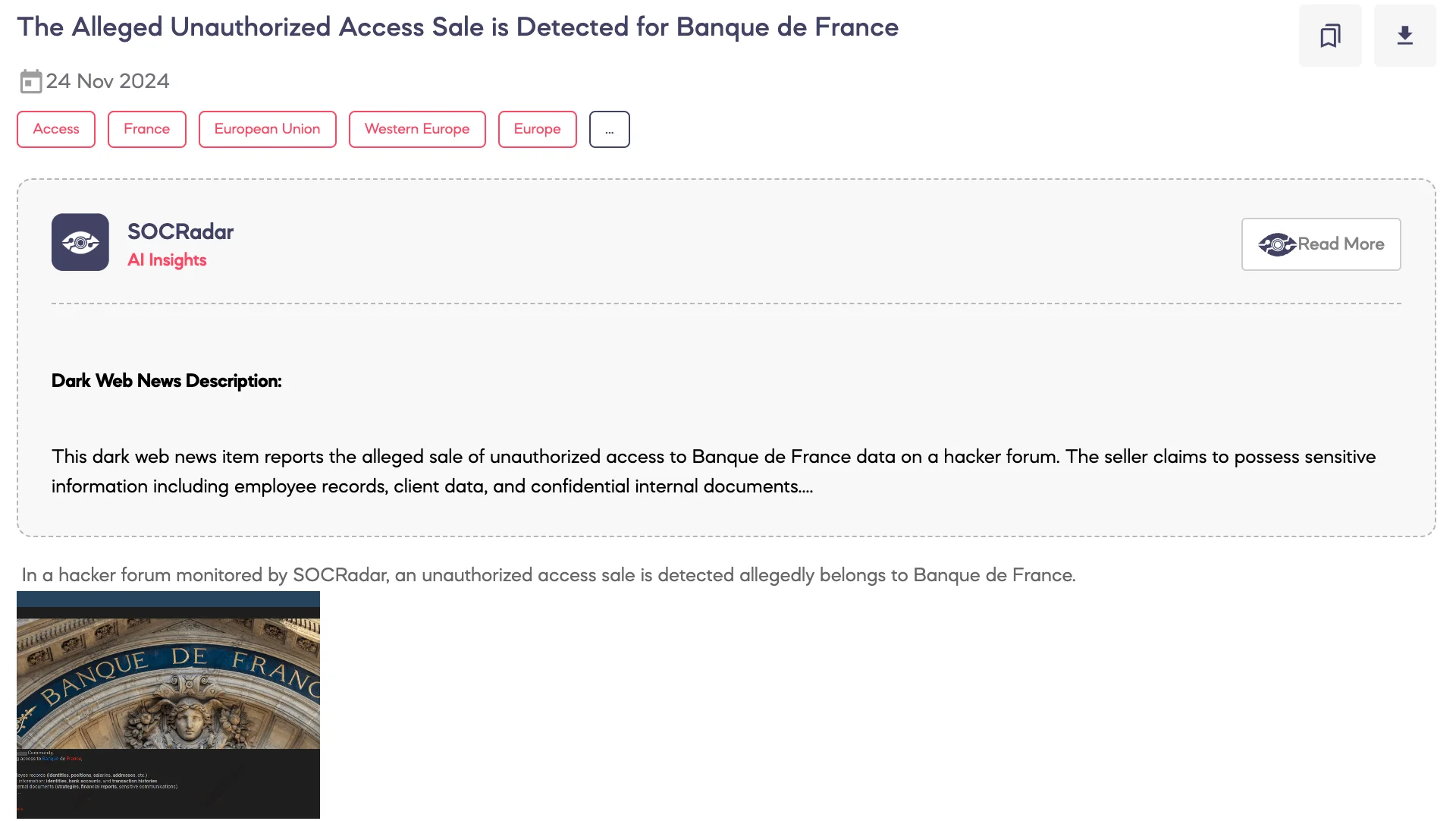
SOCRadar Dark Web Team identified a post on a hacker forum advertising the sale of unauthorized access allegedly linked to Banque de France.
According to the threat actor, the access provides exposure to highly sensitive data, including complete employee records such as identities, positions, salaries, and addresses. Additionally, the threat actor claims that the data includes sensitive client information, such as identities, bank account details, and transaction histories. Confidential internal documents, including strategies, financial reports, and sensitive communications, are also purportedly available.
Alleged Database of NOQ Group is on Sale
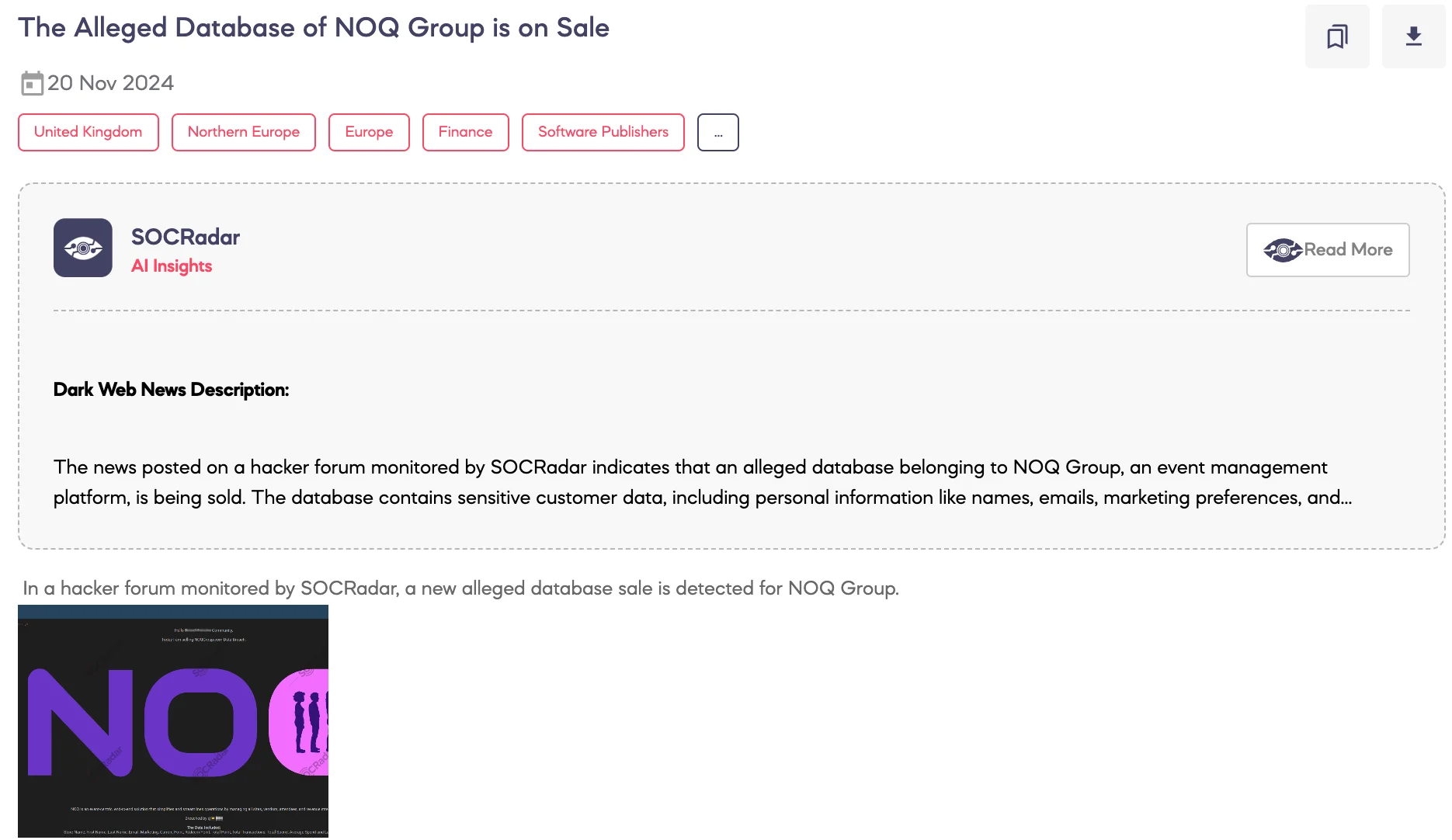
SOCRadar Dark Web team identified a post on a hacker forum advertising the sale of an alleged database from NOQ Group. According to the threat actor, the breach involves NOQ Group, a platform designed to streamline event management by handling sites, vendors, attendees, and revenue streams. The compromised database is claimed to include detailed user information such as store names, personal details, transaction records, and spending habits. The total dataset allegedly contains 2,985,416 rows.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































