
The Meeten Campaign: Realst Stealer’s Return Under Guise of Meeting Apps
The cybersecurity landscape faces constant evolution, and recent threats highlight the urgency of vigilance. One such sophisticated campaign, known as Meeten, brings the infamous Realst Stealer malware back into the spotlight. This iteration, disguised as legitimate meeting apps, has been wreaking havoc on MacOS users by targeting their passwords and browser-stored data.

An AI illustration of the Meeten Campaign (DALL-E)
Here, we delve into the core aspects of the campaign, its Indicators of Compromise (IoCs), mitigation strategies, and SOCRadar’s role in countering such threats.
Meeten Campaign Overview
The Meeten malware leverages social engineering techniques to deceive users into downloading malicious meeting applications. These counterfeit apps are distributed through phishing emails, fraudulent advertisements, and malicious links, tricking individuals into believing they are using legitimate collaboration tools.
Once installed, the malware initiates its core functions – extracting sensitive information such as passwords, browser credentials, and financial data from victims’ devices.
Targeting primarily MacOS users, the Meeten campaign exploits inherent vulnerabilities while leveraging user trust in meeting programs. Its advanced obfuscation and encryption techniques allow it to bypass traditional antivirus software, extending its period of undetected activity.
The campaign’s impact spans across various sectors, including finance, healthcare, education, and software publishing, with countries such as the United States, Germany, and Japan being heavily affected.
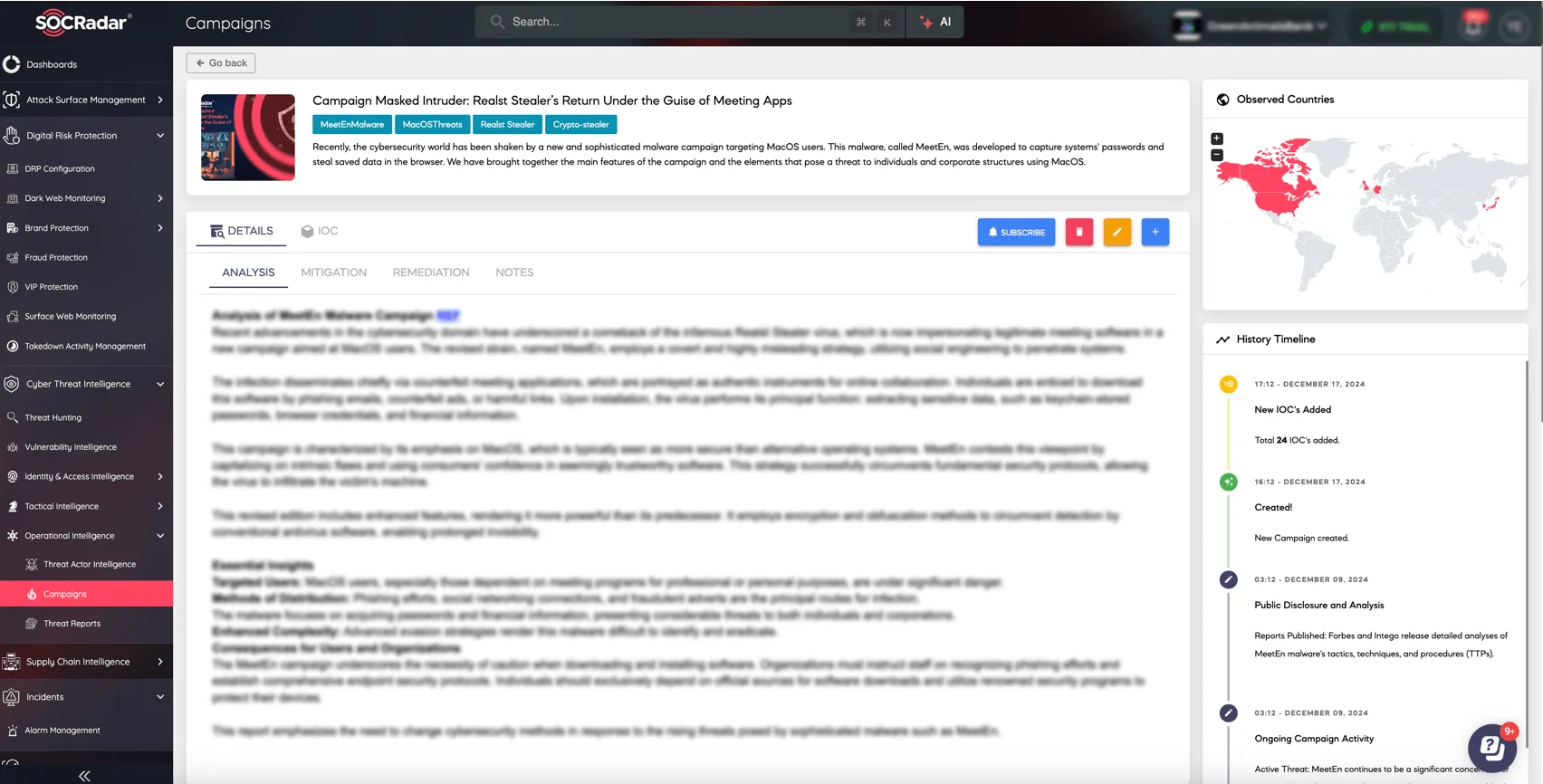
Realst Stealer’s Return – Meeten Campaign page on the SOCRadar XTI platform
For more in-depth information on the Meeten campaign and its tactics, visit the Campaigns page on SOCRadar XTI. There, you’ll find detailed insights, up-to-date intelligence, and actionable data to help you understand the threat actor’s methods and strengthen your defense strategies.
Indicators of Compromise (IoCs)
Meeten malware’s IoCs help organizations detect and prevent infections. Key IoCs include:
Hashes:
- 09b7650d8b4a6d8c8fbb855d6626e25d
- 209af36bb119a5e070bad479d73498f7
- 6a925b71afa41d72e4a7d01034e8501b
IP Addresses:
- 139.162.179.170
- 172.104.133.212
Domains:
- www.Meeten.us
- deliverynetwork.observer
URLs:
- http://139.162.179.170:8080/new_analytics
- http://deliverynetwork.observer/qfast/AdditionalFilesForMeet.zip
Mitigation Strategies
Effective mitigation strategies can limit the impact of Meeten and similar threats:
- Restrict Registry Permissions: Ensure proper permissions for registry hives to prevent unauthorized modifications.
- Software Configuration: Employ application control solutions such as AppLocker and Device Guard to block untrusted applications.
- Encrypt Sensitive Information: Obfuscate or encrypt event files both locally and in transit to mitigate unauthorized access.
- Privileged Account Management: Limit access to privileged accounts and enforce stringent password policies.
- Regular Software Updates: Keep systems and software up to date to reduce the risk of exploitation.
Remediation Tactics
To remediate potential infections, organizations should implement the following measures:
- Monitor Command Execution: Identify executed commands that attempt to modify system settings or registry keys.
- Analyze Network Traffic: Inspect anomalous traffic patterns that could indicate malicious activity.
- File and Process Monitoring: Detect unusual file creations, modifications, and process executions indicative of malware behavior.
- Incident Response: Deploy automated tools and workflows to isolate affected systems and mitigate further damage.
SOCRadar’s Role in Combatting Threats Like the Meeten Campaign
SOCRadar plays a key role in defending against advanced threats like Meeten through its comprehensive Extended Threat Intelligence (XTI) platform. With modules such as Advanced Malware Detection and Dark Web Monitoring, SOCRadar ensures real-time threat detection and timely alerts for compromised credentials or discussions related to campaigns like Meeten.
Leveraging Cyber Threat Intelligence, SOCRadar provides actionable insights into Meeten’s Tactics, Techniques, and Procedures (TTPs), helping organizations stay ahead of adversaries. The platform’s Vulnerability Intelligence identifies exploitable weaknesses, while Incident Response Support streamlines mitigation efforts after detection.
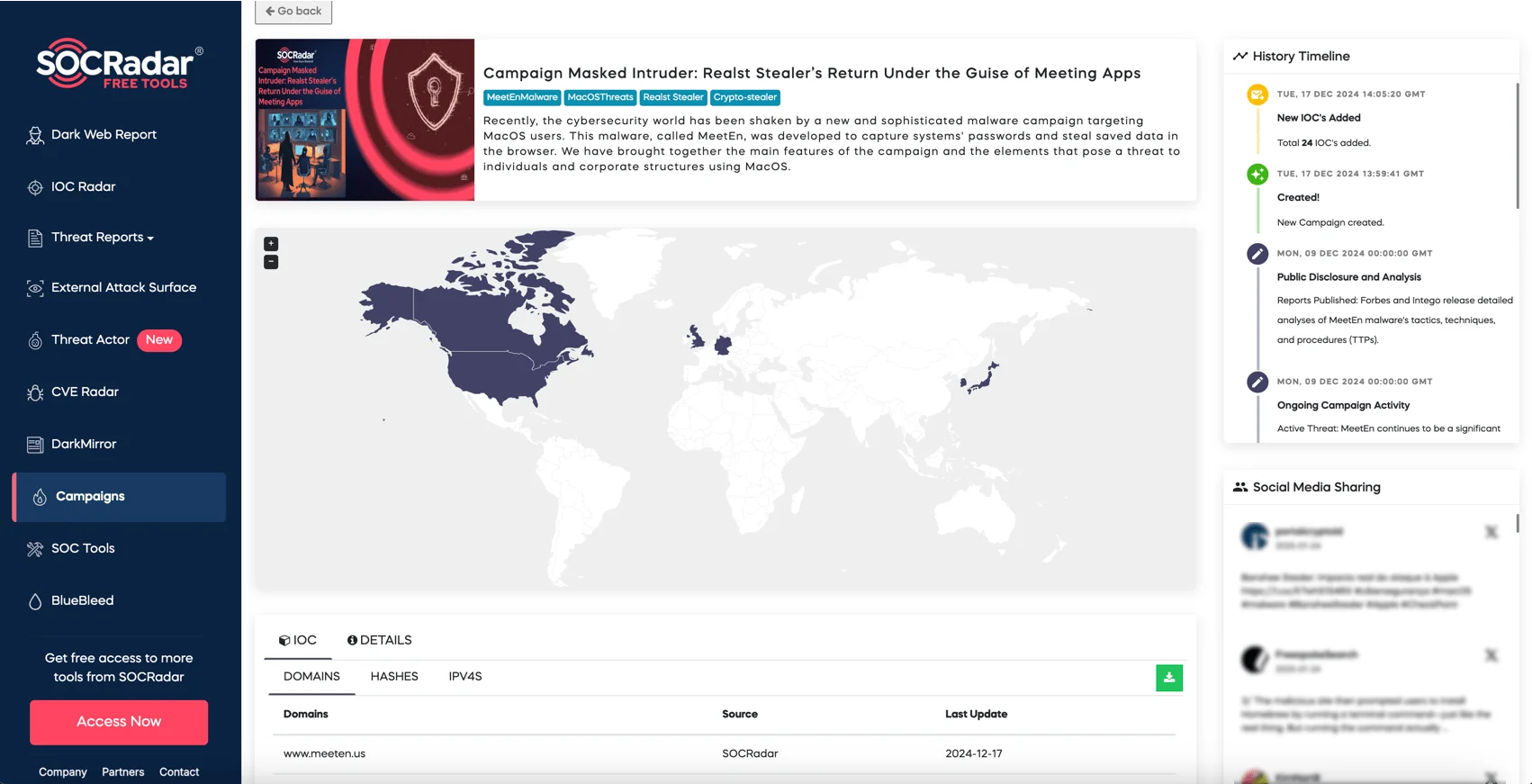
Meeten campaign page on SOCRadar LABS
SOCRadar LABS also offers a dedicated Campaigns page for Meeten, featuring detailed analysis, IoC information, and the latest insights to ensure businesses are well-prepared to handle this persistent threat. By utilizing SOCRadar’s Extended Threat Intelligence and proactive defense tools, organizations can strengthen their cybersecurity posture and protect their critical assets.


































