Threat Actors Employ New Phishing Tactic Using Google AMP
Researchers have uncovered a highly effective phishing tactic, which utilizes Google AMP (Accelerated Mobile Pages). Google AMP is an open-source HTML framework designed to create websites optimized for mobile browsers.
In this recent campaign, the attackers leveraged websites hosted on Google.com or Google.co.uk to exploit the trust associated with these domains and avoid security measures. They also employed various other tactics to bypass email security infrastructure, which has made this phishing campaign very successful at reaching its intended targets.
How Do Threat Actors Use Google AMP in Their Attacks?
Google enables the display of each web page on Google Search and grants the ability to utilize Google AMP Cache and Google Analytics, providing users with additional capabilities to track interactions on AMP pages. Another advantage is that it initially hosts webpages on a Google AMP URL.
The mentioned advantages can also attract threat actors. The Google AMP URL works in the same way as a redirect, leading users from the initial URL to the URL found within the path. Phishing threat actors have been observed hosting malicious web pages using the URL path within their phishing emails.
Because the URLs are hosted on legitimate Google domains, identifying them as malicious may be difficult for email security infrastructure. Additionally, threat actors can utilize Google Analytics to track user interactions on their phishing pages.
Example of a Phishing Page Hosted on Google AMP
Researchers provided a real-world example of a phishing URL:
hxxps://www[.]google[.]com/amp/s/netbitsfibra[.]com.br/css/tmp/…
The left half of the URL represents the authentic Google AMP path, while the right half corresponds to the webpage established by the Google AMP user (in this case, it is the phishing page).
Google AMP URL Path: hxxps://www[.]google[.]com/amp/s/
Phishing URL: hxxp://www[.]netbitsfibra[.]com.br/css/tmp/…
Unraveling the Tactics Used in Phishing Campaign
Threat actors have combined a new tactic with well-known methods to make phishing campaigns successful. The effectiveness of this new tactic lies in using trusted domains for hosting URLs and employing a redirection-like process, making automated analysis challenging. These campaigns employ various techniques, including:
- Trusted Domains: Hosting URLs on trusted domains complicates automated analysis, making it challenging to block only the malicious parts of the URL.
- Image-based Phishing Emails: Some observed emails are image-based, making them harder to detect compared to text-based emails. The images act as clickable links, directing users to the phishing attack.
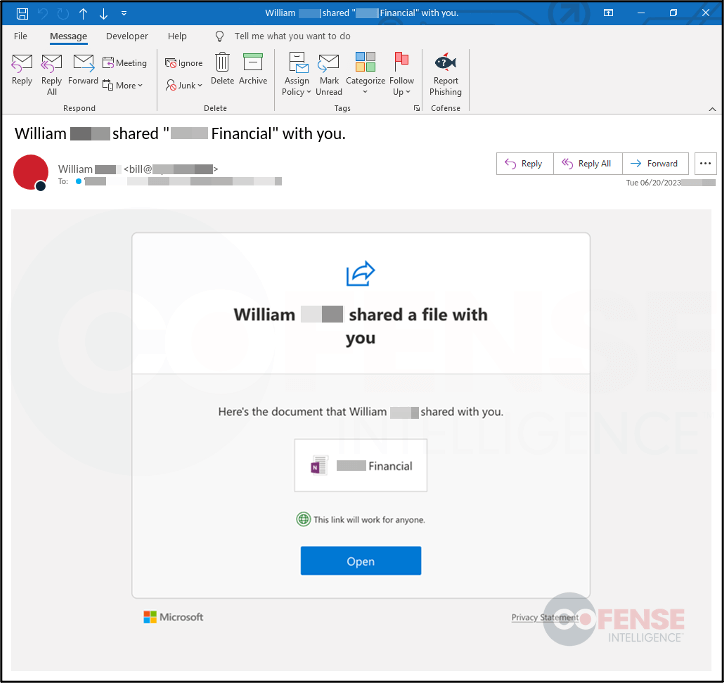
- URL Redirection: Utilizing multiple redirects within a single phishing attack chain, along with trusted domains, adds false legitimacy and hinders analysis.
- Cloudflare CAPTCHA: Abusing Cloudflare’s CAPTCHA service prevents automated analysis and requires manual user interaction to reach the final malicious URL. This tactic also allows threat actors to hide the domain’s original hosting provider.
The Success Rate of Google AMP Phishing Campaign
The use of Google AMP URLs has demonstrated significant success in reaching users within secure email gateway (SEG) protected environments. This success stemmed from variety of reasons, the most important of which is that the URLs are hosted on legitimate Google domains. According to Cofense researchers, the main goal of these emails is to steal employee email login credentials.
The Google AMP Campaign is Ongoing
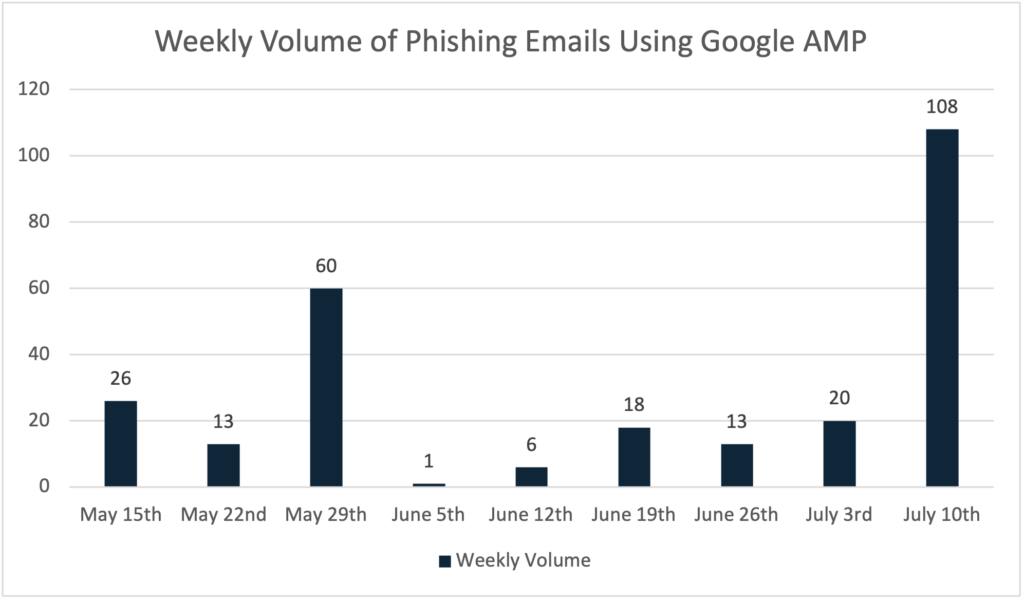
Phishing campaigns using Google AMP services surged in May and remain a persistent threat. The tactics varied, with peaks during the weeks of May 29 and July 10. On June 15, attackers shifted tactics by using Google.co.uk in the URLs, while the overall strategy remained the same.
Around 77% of observed URLs were on google.com and 23% on google.co.uk. Identifying this phishing campaign based on URL pathing is useful, but directly blocking “google.com/amp/s/” is challenging due to legitimate uses. Organizations should talk about valid uses of this pathing for their users before deciding on blocking. An alternative could be to flag URLs with this path.
Detect Phishing Domains and Threats with SOCRadar
Phishing attacks have been steadily increasing over the past few years, leveraging more advanced techniques and achieving higher success rates. It is vital to stay informed about the latest phishing techniques and to take proactive measures to protect against them.
Some precautions include exercising caution with spam emails, refraining from providing personal information in response to unsolicited requests, and utilizing threat intelligence tools.
SOCRadar offers a valuable service that identifies and responds to spoof domains aiming to collect login credentials and personally identifiable information from your staff and customers. With SOCRadar XTI, detecting these phishing domains becomes effortless, and you can receive immediate alarms for prompt response.