
Top 10 Attack Surface Management Tools
Attack Surface Management (ASM) tools have become critical for organizations in identifying, managing, and mitigating vulnerabilities in digital environments. These tools enable continuous monitoring, discovery, and analysis of both known and unknown assets, allowing security teams to stay ahead of potential threats.
This blog discusses the 10 Attack Surface Management tools for improving your organization’s cyber resilience by providing comprehensive visibility and proactive risk management.
What is Attack Surface Management (ASM)?
Attack Surface Management (ASM) is a cybersecurity strategy that aims to identify and manage all potential entry points into an organization’s IT environment that attackers could exploit. These entry points include both known assets, such as registered websites and servers, and unknown assets, which are frequently forgotten or unmonitored.

AI illustration of ASM Tools
ASM tools also address asset impersonation, such as malicious infrastructures that impersonate legitimate company assets, as well as third-party assets, such as external JavaScripts and hosting servers. Effective ASM continuously monitors these assets, reducing vulnerabilities while maintaining visibility of the digital footprint and proactively addressing potential security risks.
Now let’s dive in top 10 attack surface management tools:
1. UpGuard
UpGuard provides a powerful attack surface management tool that identifies and reduces risks through daily scanning, real-time alerts, and automated remediation workflows. This platform enables security teams to continuously monitor domains, IP addresses, and digital assets, ensuring threats are detected and addressed quickly.
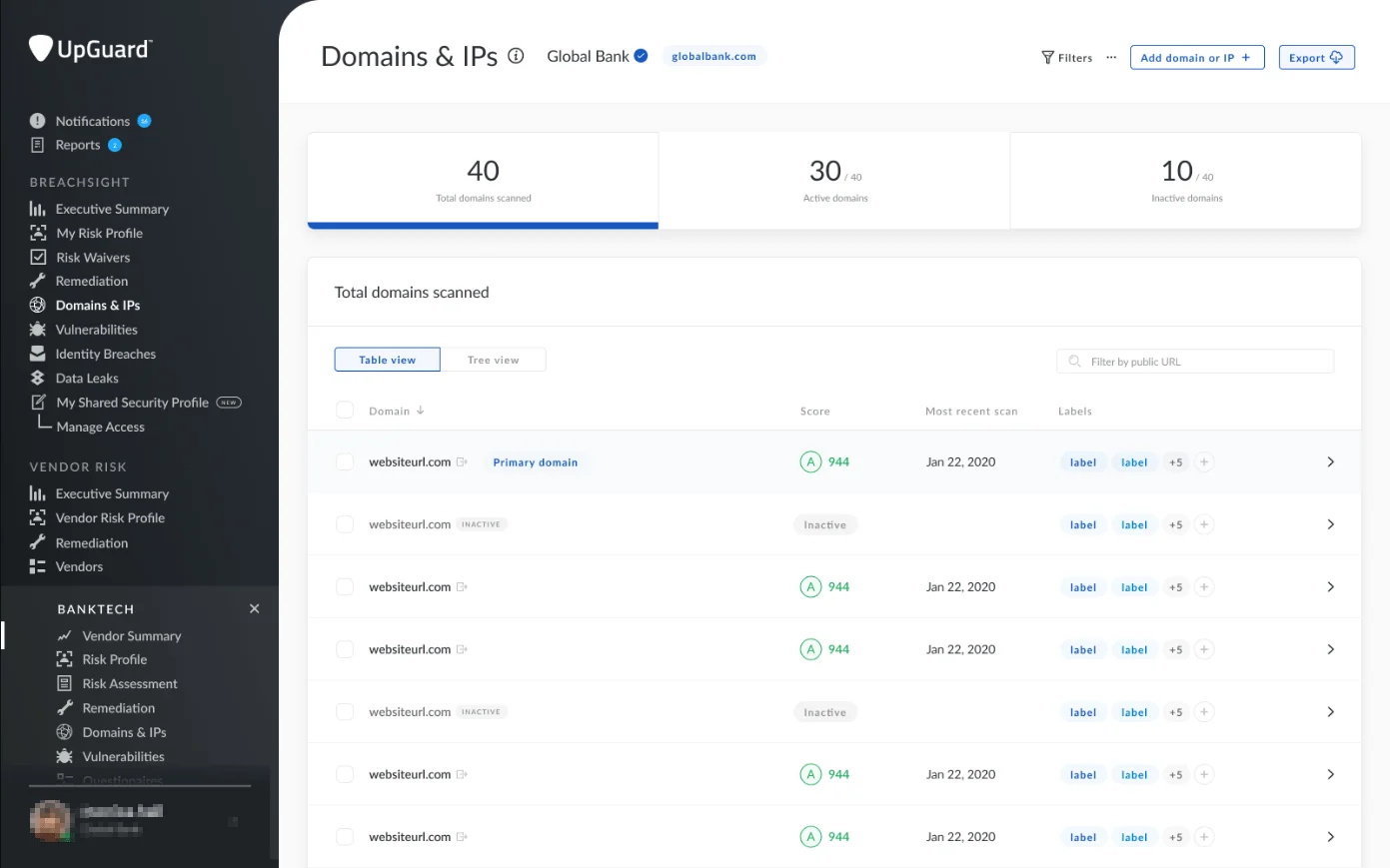
UpGuard ASM Domains & IPs section (Source: upguard.com)
Key Features:
- Real-time Scanning & Alerts: Continuous monitoring of external assets with instant threat notifications.
- Vulnerability Detection: Identify software vulnerabilities and domain permutations at risk of typosquatting.
- Data Leak Detection: Detect leaked credentials using a combination of manual analysis and dark web scanning.
- Automated Reporting: Generate executive summaries and detailed reports instantly for easy communication of risks.
UpGuard’s simplified remediation workflow and impact forecasting enable organizations to manage risks more efficiently and effectively, saving significant time and resources. UpGuard, trusted by thousands around the world, improves security operations by prioritizing tasks and providing actionable insights.
2. SOCRadar Attack Surface Management
SOCRadar Attack Surface Management enables organizations to maintain strong security against evolving cyber threats. Using advanced continuous monitoring algorithms, it provides:
- Continuous Visibility: Provides enhanced visibility and context for both current and future attack surfaces without the need for manual asset inventory.
- Proactive Monitoring: Tracks vulnerable software, exposed information, third-party software, expired SSL certificates, DNS records, and cloud assets continuously.
- Shadow IT Discovery: Unveils unmanaged and unsecured network elements, enabling preemptive vulnerability addressing.
- Digital Footprint Analysis: Identifies and secures exposed assets and hidden vulnerabilities across various platforms.
SOCRadar’s comprehensive ASM solution keeps organizations ahead of cyber threats by providing continuous visibility, proactive monitoring, and strong security for digital assets. Integrating our platform allows you to detect vulnerabilities early on, effectively monitor public-facing infrastructures, and improve your overall cybersecurity posture.
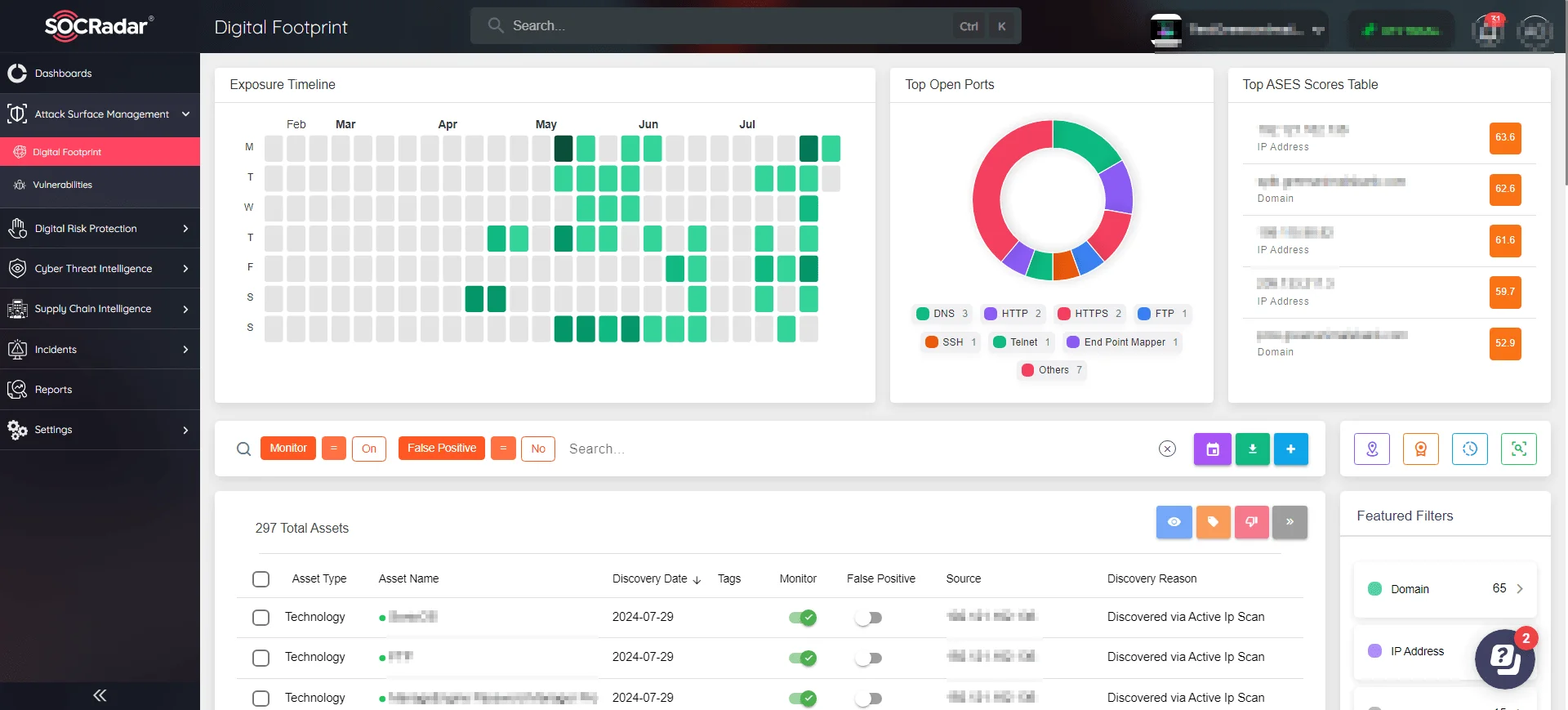
SOCRadar ASM Module’s Digital Footprint
Protect your digital footprint and reduce risks with SOCRadar’s cutting-edge technology. Experience the transformative power of our ASM solution and protect your organization’s digital assets today.
Begin with our freemium and learn how SOCRadar can help you strengthen your cybersecurity efforts.
3. Microsoft Defender External Attack Surface Management
Microsoft Defender EASM provides comprehensive visibility into your organization’s external attack surface, highlighting potential attacker perspectives. Unmanaged assets, shadow IT, and vulnerabilities across multi cloud and hybrid environments are identified and prioritized by continuously monitoring and analyzing external-facing resources.
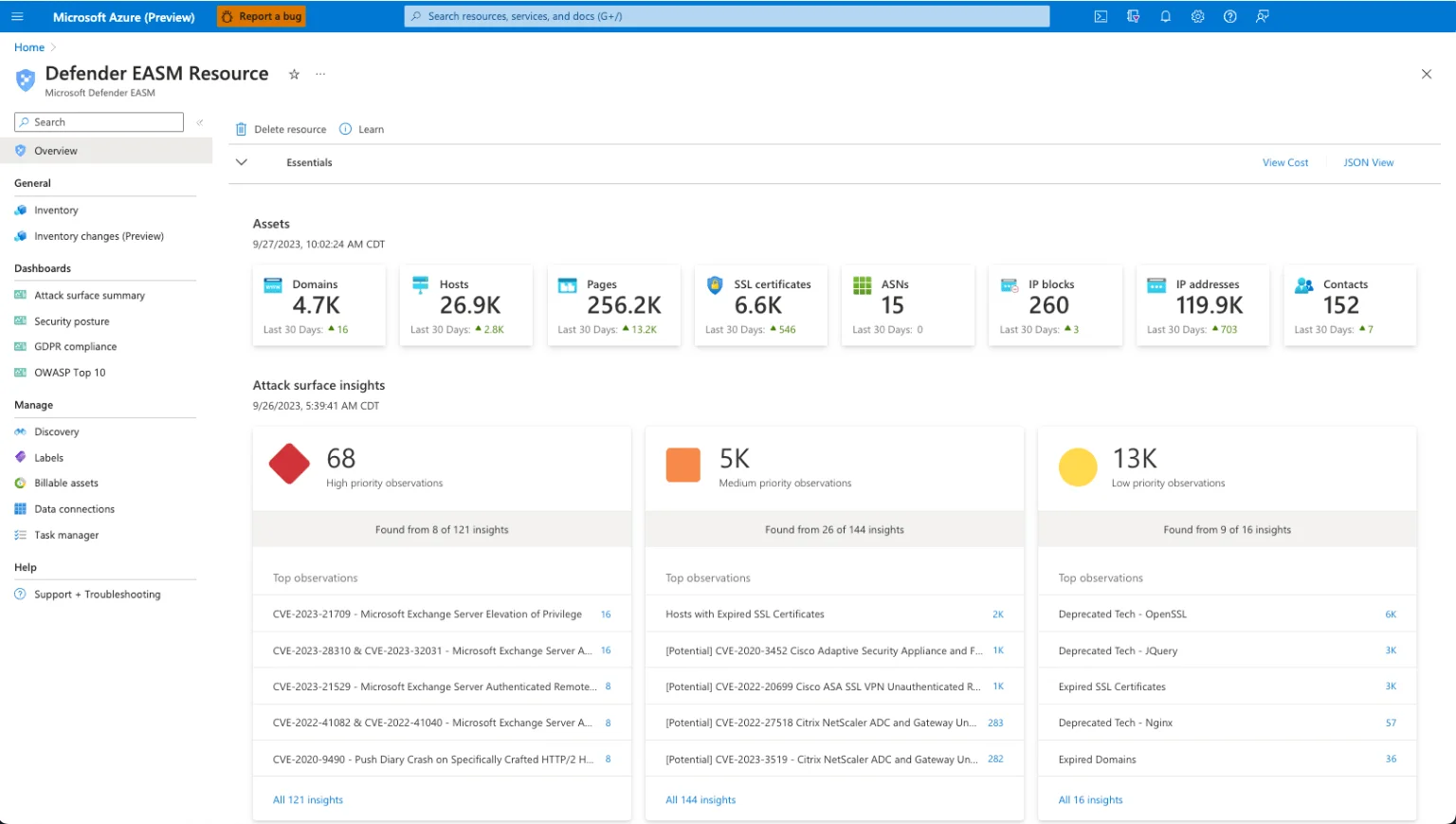
Microsoft Defender External Attack Surface Management tool (Source: microsoft.com)
Key Features:
- Continuous Visibility: Real-time monitoring of external attack surfaces.
- Discovery & Prioritization: Identifies and categorizes unmanaged resources, prioritizing vulnerabilities and misconfigurations.
- AI-Driven Insights: Utilizes generative AI to convert natural language into actionable inventory queries and provides insights into risky assets.
Defender EASM enables cloud security teams to manage and mitigate risks more effectively, resulting in a stronger security posture.
4. CyCognito
CyCognito Attack Surface Management is a comprehensive solution that scales to meet the external risk requirements of large global organizations. This platform provides an attacker’s perspective by continuously mapping an organization’s business structure to identify vulnerabilities throughout the entire digital supply chain.
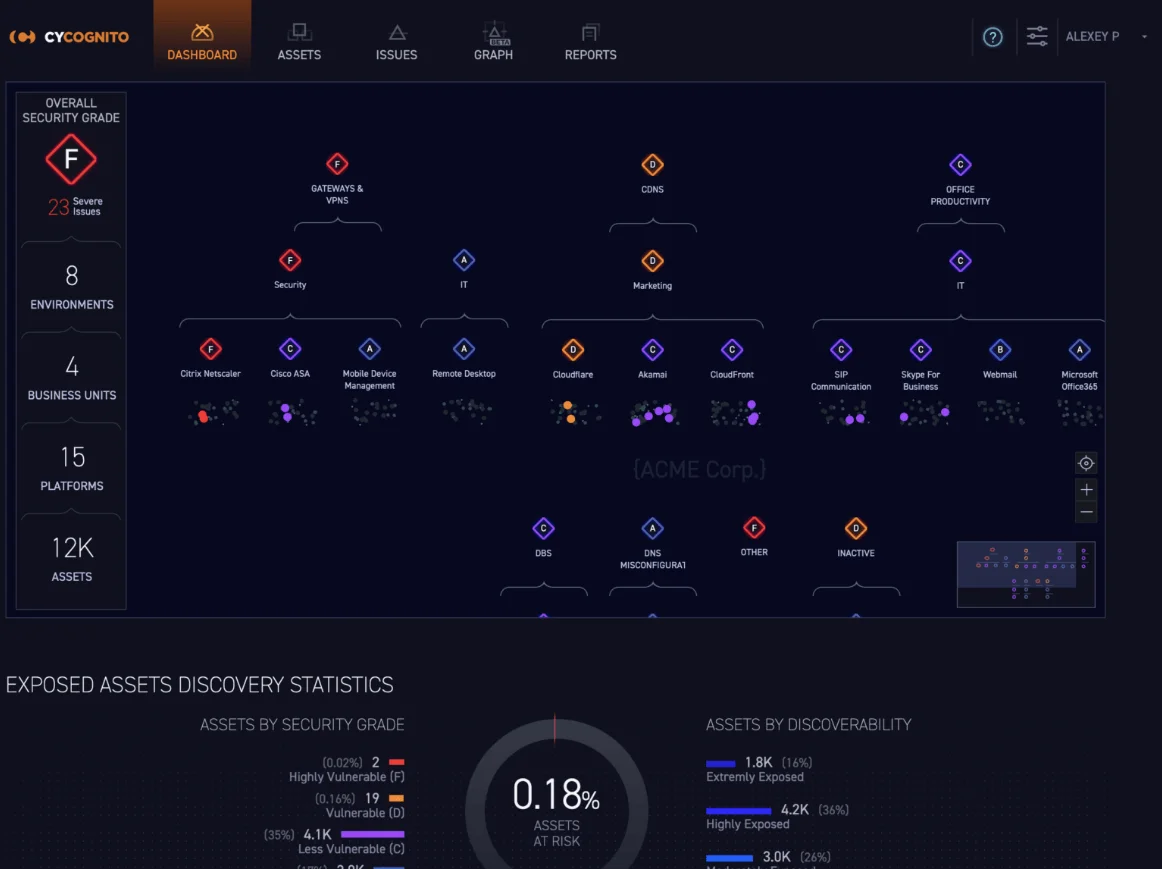
CyCognito Dashboard (Source: cycognito.com)
Key Features:
- Real-Time Attack Surface Discovery: Using AI, CyCognito provides continuous, automated discovery of an organization’s entire attack surface, including shadow IT and assets within subsidiary networks.
- Automated Attribution: This feature helps understand how assets are connected and their associated risks, including hyperlinks, gateways, and third-party code usage.
- Supply Chain Risk Reduction: Monitors third-party software libraries and open-source components for potential vulnerabilities, allowing early risk identification and mitigation.
- Contextual Risk Insight: Offers detailed context for each asset, showing its discoverability and accessibility from an attacker’s point of view. This helps prioritize actions based on the criticality of the threats.
- Risk-Based Scoring: Focuses on the critical by using risk scoring frameworks such as CVSS to determine issues that matter most, ensuring that the most impactful vulnerabilities are addressed promptly.
Benefits:
- Provides clear, contextual risk insights across the entire attack surface.
- Enables organizations to make efficient decisions and bolster their defenses against potential threats.
- Enhances visibility into digital assets, ensuring that both known and unknown risks are managed effectively.
- Helps streamline the remediation process with automated workflows and prioritization based on real-time data.
CyCognito’s attack surface management solution is built to offer unparalleled visibility and proactive risk management, ensuring that organizations can stay ahead of potential threats and safeguard their digital assets comprehensively. By adopting an outside-in perspective, CyCognito helps security teams understand their attack surface just as attackers would, allowing for more effective defense strategies. It was also mentioned in our blog post about top 5 free ASM tools, which you can check by clicking this link.
5. Rapid7 CAASM
Rapid7 Cyber Asset Attack Surface Management (CAASM) uses data integration, conversion, and analytics to provide a single view of all cyber assets on an enterprise network.
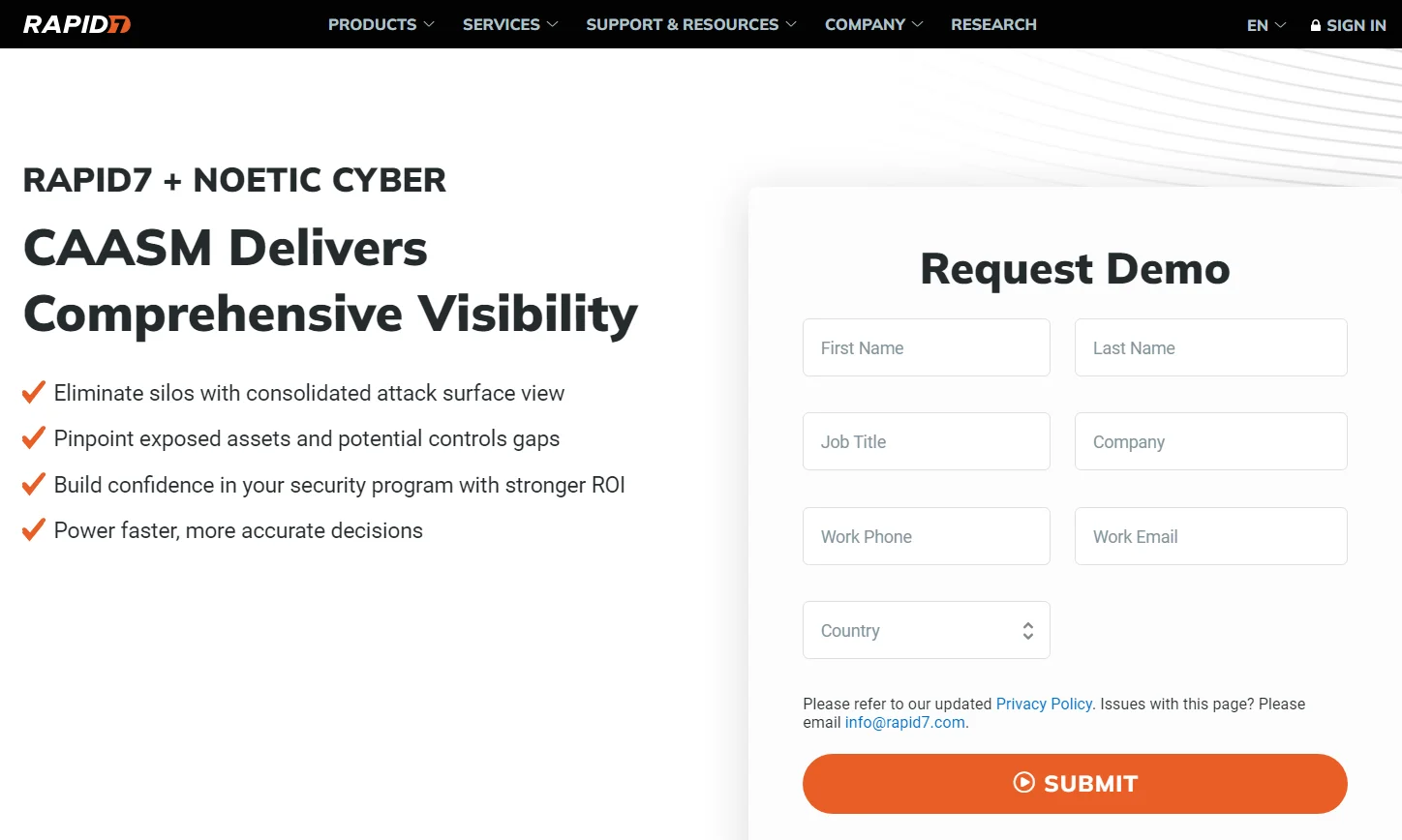
Rapid7 CAASM demo
Here are its key features and functionalities:
- Asset Visibility: Identifies and catalogs all physical and digital assets, providing real-time inventory monitoring.
- Vulnerability Management: The platform aids in identifying and prioritizing vulnerabilities and security gaps across the network. By automating security control gap analysis, CAASM boosts efficiency and breaks down operational silos between IT and security teams.
- Integrated Workflows: Seamlessly integrates with existing workflows for consistent security policy enforcement.
- Contextual Analysis: Offers detailed insights into asset interconnections and dependencies.
- Compliance Support: Maintains asset inventories and supports regulatory compliance frameworks.
- Access Management: Enforces authentication protocols to prevent unauthorized access.
Key Benefits of CAASM:
- Lower Risk Profile: Continuous automation tools help discover and address risks in previously unknown assets.
- Reduced Attack Surface: Automation and NAC tools help shrink the attack surface, making it harder for threat actors to exploit vulnerabilities.
- Strengthened Partnerships: Sharing data between IT and security teams becomes more efficient, improving vulnerability discovery and exploitation mitigation.
These capabilities improve the overall security posture, streamline operations, and provide comprehensive attack surface management.
6. Halo Security
Halo Security offers a comprehensive attack surface management solution that allows organizations to view their network from an attacker’s perspective. This all-in-one platform protects customer data by detecting hidden assets and vulnerabilities, ensuring that every potential entry point is tracked.
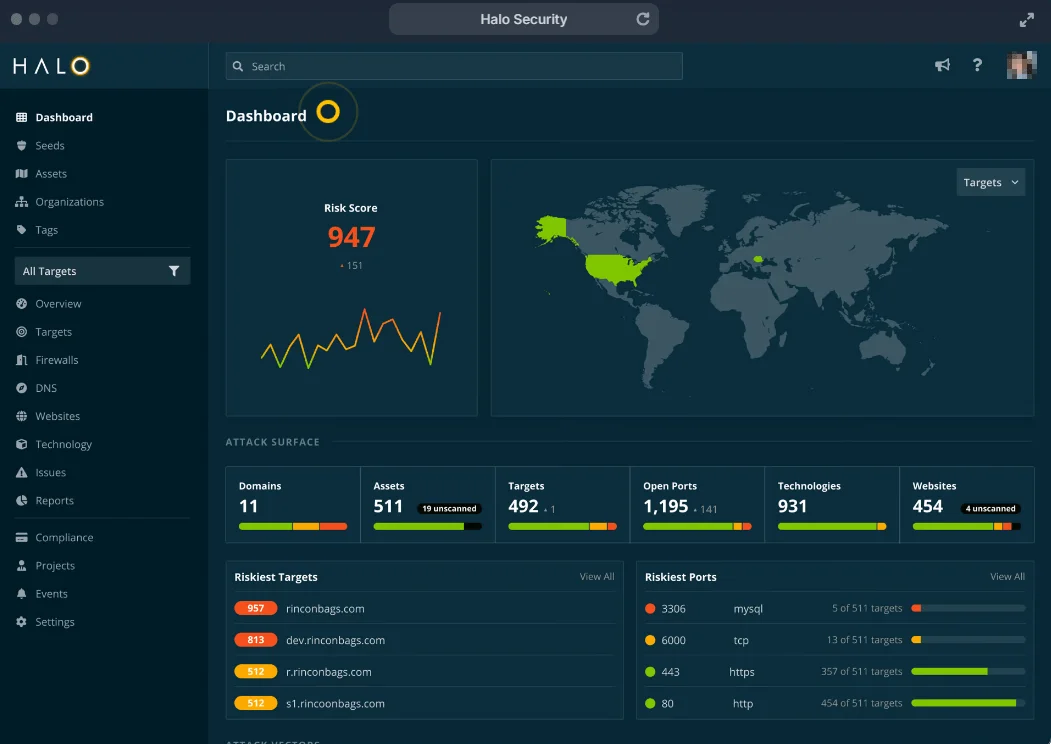
Halo ASM Dashboard
Key Features:
- Agentless Asset Discovery: Automatically finds and catalogs all external assets, including forgotten or newly added ones, providing a full picture of your attack surface.
- Centralized Security Management: Offers tools for firewall monitoring, penetration testing, and asset management from a single dashboard, ensuring efficient resource deployment.
- Real-Time Change Detection: Monitors the network perimeter for changes and alerts you instantly, reducing the risk of unexpected security issues.
- Support for Security Initiatives: Evaluates the security posture of subsidiaries, mergers, and cloud migrations, and enhances penetration testing efforts by focusing on complex vulnerabilities.
- Expert Assistance: Acts as an extension of your security team, offering expert validation of findings, discussion on new vulnerabilities, and deep dives into exposed assets.
Halo Security provides organizations with the tools and insights they need to manage and secure their attack surface effectively. The platform provides visibility into all network assets, detects and resolves outdated TLS certificates, running services, missing patches, and open ports, and improves security by automatically detecting OWASP security threats.
Halo Security assists you in staying ahead of potential threats and comprehensively safeguarding your digital assets by providing a detailed view of your network from the perspective of an attacker.
7. Cortex Xpanse
Cortex Xpanse provides a comprehensive Attack Surface Management (ASM) solution that tracks both known and unknown assets in real time, allowing you to quickly identify and mitigate exposure risks. Cortex Xpanse, which originated at DARPA, continuously updates asset inventories and integrates with other security tools to ensure seamless operation.
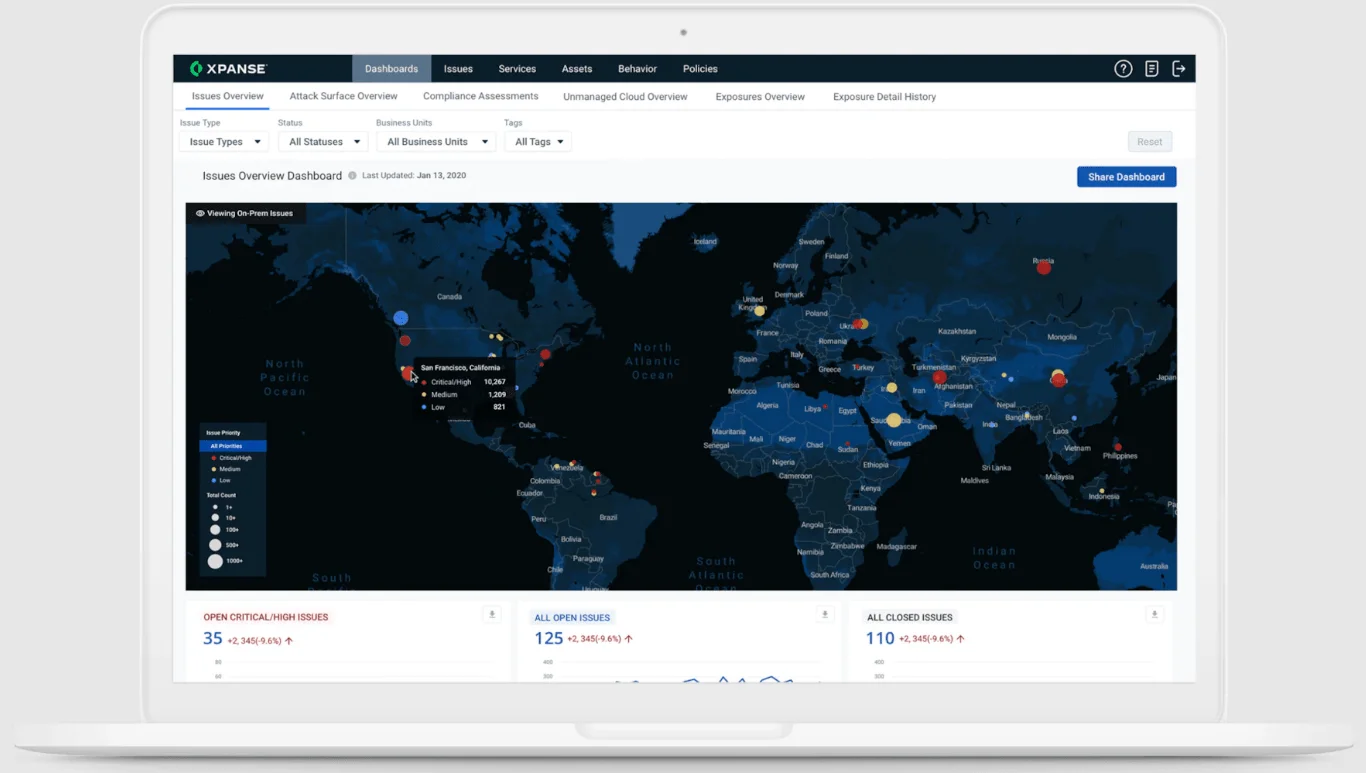
Cortex Xpanse ASM Dashboard (Source: paloaltonetworks.com)
Key Features:
- Continuous Asset Discovery: Multiple daily scans of the entire IPv4 space keep asset records current and accurate.
- Automated Remediation: Quickly assigns and mitigates risks with integrations for streamlined workflows.
- Third-Party and Acquired Company Security: Identifies vulnerabilities from supply chain partners and acquisitions.
- Enhanced Intelligence: Provides detailed context and ownership for assets, facilitating faster remediation.
- Integrated Attack Surface Program: Combines data from various tools to build a cohesive ASM strategy.
Cortex Xpanse provides numerous advantages, including rapid risk identification and mitigation, comprehensive asset visibility, improved security operations coordination, and increased protection against ransomware and other attacks. This resilient ASM solution enables organizations to stay ahead of potential threats and maintain a secure digital environment.
8. IBM Security Randori
IBM Security Randori is a leading Attack Surface Management (ASM) solution that improves cyber resilience by continuously discovering, analyzing, resolving, and monitoring cybersecurity vulnerabilities and attack vectors. It combines ASM and Automated Red Teaming to create high-quality offensive security programs at a fraction of the traditional cost.
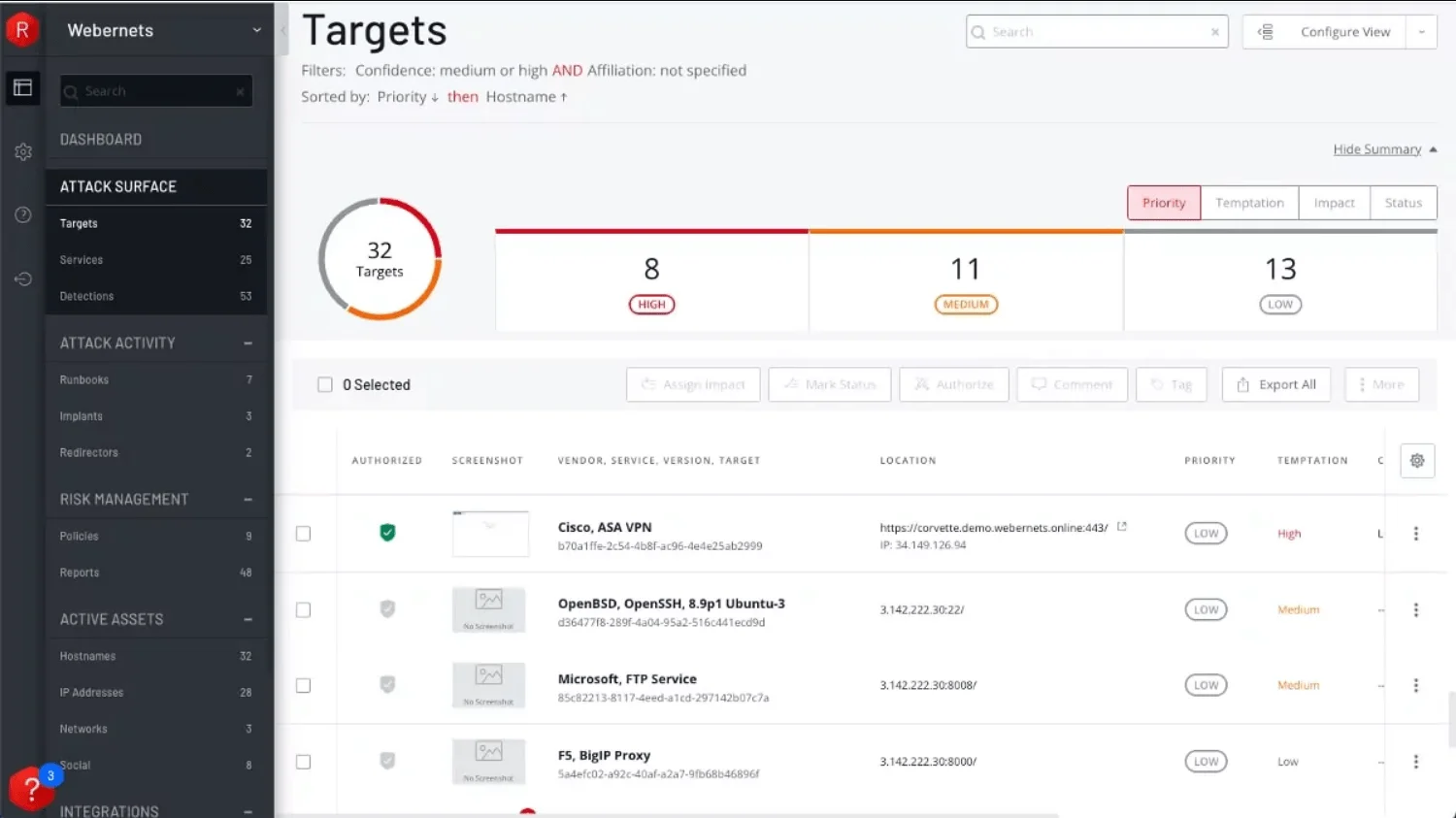
IBM Security Randori Targerts section (Source: ibm.com)
Key Features:
- Asset Discovery: Automatically identifies internet-facing hardware, software, and cloud assets.
- Classification and Prioritization: Analyzes vulnerabilities and prioritizes assets based on attackability.
- Remediation: Applies security controls and manages previously unknown assets.
- Continuous Monitoring: Detects new vulnerabilities and alerts security teams in real-time.
IBM Security Randori’s ASM capabilities eliminate shadow IT, reduce blind spots, and prioritize risks, allowing organizations to strengthen their cyber defenses more effectively and efficiently.
9. Coalfire
Coalfire Attack Surface Management is a cutting-edge solution that takes a continuous approach to offensive security. This platform uses Coalfire’s acquisition of Neuralys to automate asset discovery, testing, remediation, and reporting across expanding attack surfaces.
Coalfire Security service
Key features include:
- Continuous Discovery: Identifies cloud and internet-facing assets in real-time.
- Automated Validation: Verifies security postures continuously.
- Vulnerability Prioritization: Aggregates and prioritizes vulnerabilities and assets.
- Real-Time Monitoring: Tracks changes, remediation, and ownership for continuous protection.
Coalfire’s ASM solution is critical for managing dynamic and complex digital environments while also providing strong security measures for modern businesses.
10. CrowdStrike Falcon Surface
CrowdStrike Falcon Surface is the leading AI-native platform for unified attack surface management. It helps minimize risk from externally exposed assets using adversary-driven insights.
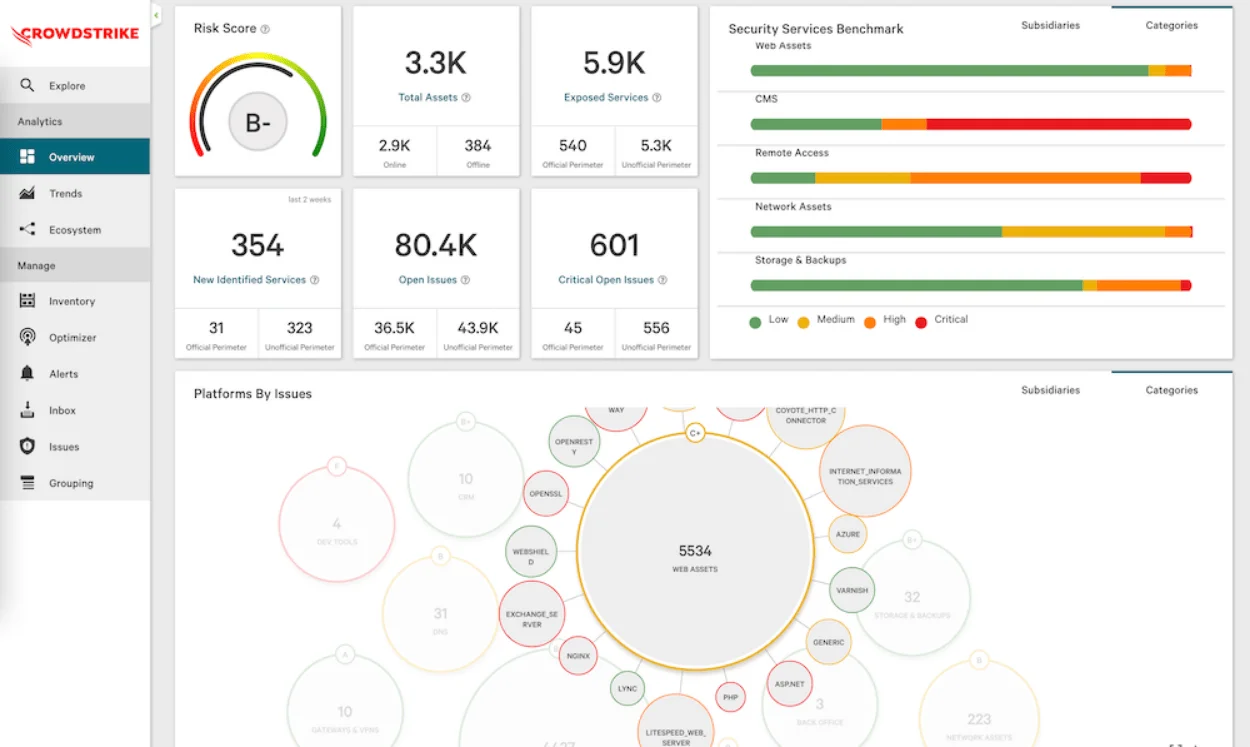
CrowdStrike Falcon Surface tool (Source: crowdstrike.com)
Key Features:
- Comprehensive Visibility: Gain complete visibility of internet-facing assets to identify potential exposures.
- Prioritized Risk: Utilize world-class adversary intelligence and AI-powered insights to pinpoint critical exposures.
- Enhanced Remediation: Leverage the unified Falcon platform for real-time vulnerability management and IT hygiene.
CrowdStrike Falcon Surface increases exposure visibility by 55%, decreases investigation time by 60%, and reduces external attack surface risks by 75%, establishing it as the clear leader in exposure management.
Conclusion
Choosing the right Attack Surface Management tool is critical to protecting your organization’s digital assets. From automated discovery and continuous monitoring to in-depth vulnerability assessment and remediation.
Investing in SOCRadar’s ASM solution provides continuous visibility and proactive threat mitigation. These advanced ASM tools will help you stay ahead of cyber threats, strengthen your security posture, and protect your digital footprint. Secure your organization today with the appropriate ASM solution and enjoy unrivaled cybersecurity protection.




































