Top 10 Malware Analysis Platforms & Tools
While cyberspace constantly expands, some dangers like malware come to the surface in parallel. A mail attachment, an innocent-looking application downloaded from the internet, or even a piece of code injected into a legitimate site can become a big problem for organizations and individuals. Even older than the internet, malware is still and will continue to be a constant danger in cyberspace.
Thankfully, the cybersecurity community has risen to the challenge by developing various malware analysis tools. These tools play a vital role in curbing the relentless surge of cyber threats by enabling security analysts to gather and analyze malware samples, unravel their capabilities, and guide investigations.
In this article, we will explore a curated selection of top-notch malware analysis platforms and tools. What sets these tools apart is that they are not only effective but also free!
With these powerful resources at your disposal, you can enhance your cybersecurity defenses without breaking the bank. Without further ado, let’s dive into the top 10 favorite malware analysis tools and platforms. While this list is not ranked in any particular order, each tool brings unique strengths and functionalities to the table.
VirusTotal
VirusTotal is a well-known and widely-used malware analysis platform. It allows users to upload suspicious files or URLs and scans them with multiple over 70 antivirus scanners, and URL/domain blocklisting services. The platform aggregates the results and provides a comprehensive report on the file’s reputation. VirusTotal also offers additional features such as behavior analysis and sandbox execution.
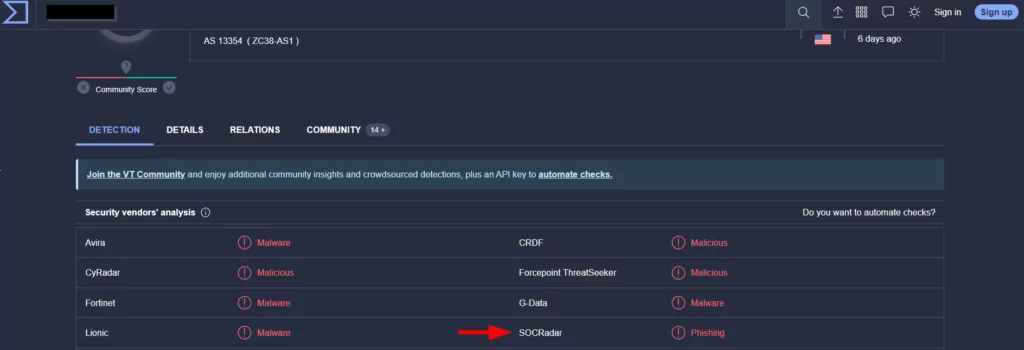
Also, SOCRadar and VirusTotal joined forces! SOCRadar’s partnership with VirusTotal aims to enhance organizations’ ability to protect against sophisticated cyber threats by providing enriched data. This collaboration perfectly aligns with SOCRadar’s mission of offering comprehensive threat intelligence, empowering businesses to safeguard their digital assets proactively.
- Pros: Extensive antivirus engine coverage, suspicious domain scans and threat feeds, easy-to-use interface, provides detailed reports.
- Cons: Files added to VirusTotal will be open to public access, and the 32 MB upload limitation can be restrictive in some scenarios. (You can upload files up to 200 MB via a special upload URL: /file/scan/upload_url endpoint.)
DOCGuard
DOCGuard is a malware analysis service whose primary use case is to integrate with SEGs (Secure Email Gateways) and SOAR solutions.
The service performs a new kind of static analysis called structural analysis. The structural analysis dissembles the malware and passes it to the core engines with respect to file structure components. By using this approach, DOCGuard can precisely detect the malware in seconds and extract the false positive free IoCs and may also identify obfuscation and encryption in the form of string encoding and document encryption.
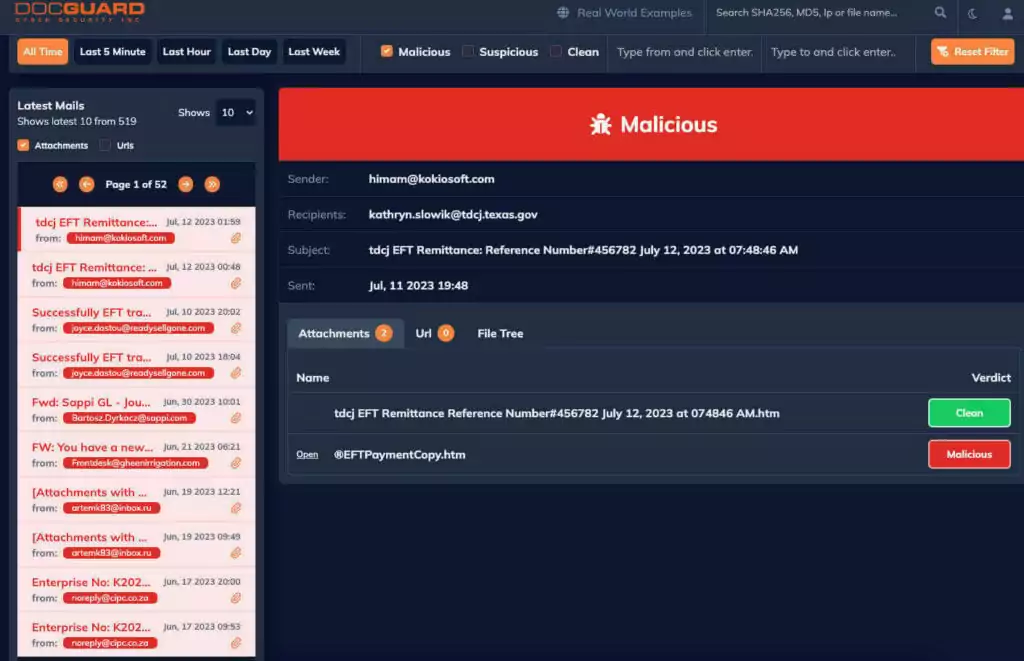
The currently supported file types are Microsoft Office Files, PDFs, EMLs, MSGs HTML, HTMs, LNKs, JScripts, ISOs, IMGs, VHDs, VCFs, and archives (.zip, .rar, .7z, etc.). The detailed findings of the structural analysis are presented in a detailed view in the GUI. The reports can be downloaded as a JSON file and gathered over API.
- Pros: Fastest scanner in the market. Easy-to-use interface, free for cloud and on browser, provides detailed reports. They also have a “Real World Example” service, which will help users to see the fresh malware samples bypassing their current Antivirus Solutions.
- Cons: While it is available for free on the cloud, acquiring a license is necessary for utilizing it through the API.
Hybrid Analysis
Hybrid Analysis combines static and dynamic analysis techniques to provide a holistic view of malware. It enables users to submit files and URLs for analysis and executes them in a controlled virtual environment to observe their behavior. The platform offers detailed reports, including network traffic, system changes, and process activity.

- Pros: In-depth behavioral analysis, comprehensive reports, supports Windows and Linux environments including Android.
- Cons: Limited availability of public reports, may have usage limitations for free users.
Cuckoo Sandbox
Cuckoo Sandbox is an open-source platform that focuses on behavioral analysis. It allows analysts to submit suspicious files or URLs and executes them in an isolated environment to monitor their behavior. Cuckoo Sandbox generates detailed reports, including network activities, file modifications, and system calls.
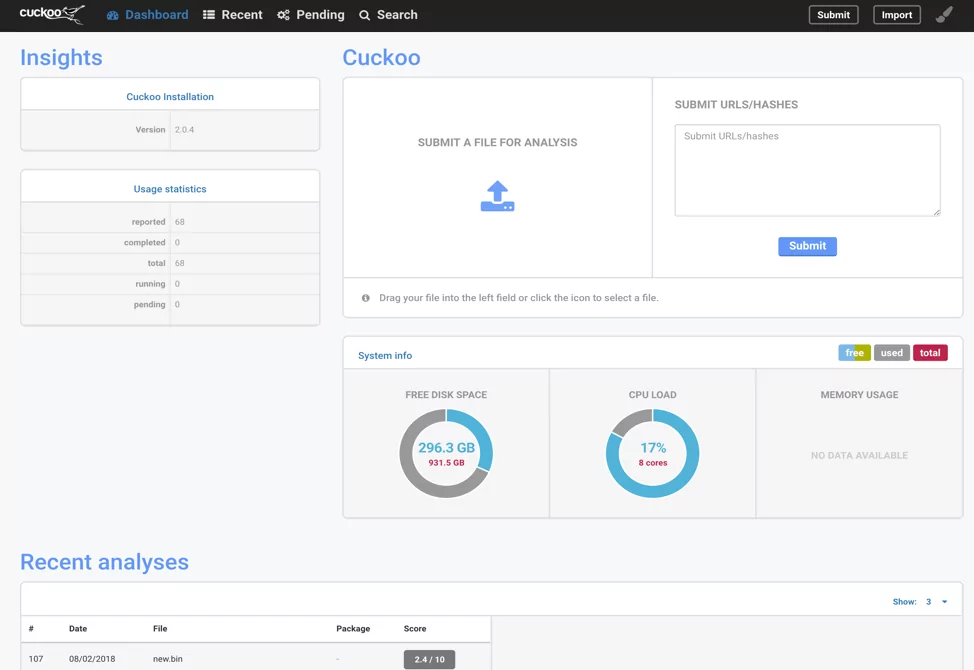
- Pros: Open-source, customizable, extensive behavioral analysis capabilities, and active community support.
- Cons: Requires technical expertise to set up and may be incompatible with specific file formats, if necessary packages are not installed such as, .iso or .7z.
Any.Run
Any.Run is a powerful interactive malware analysis platform. It allows users to run suspicious files and observe their real-time behavior via web browser. The platform provides a sandbox environment where analysts can interact with malware samples and analyze their activities step-by-step.
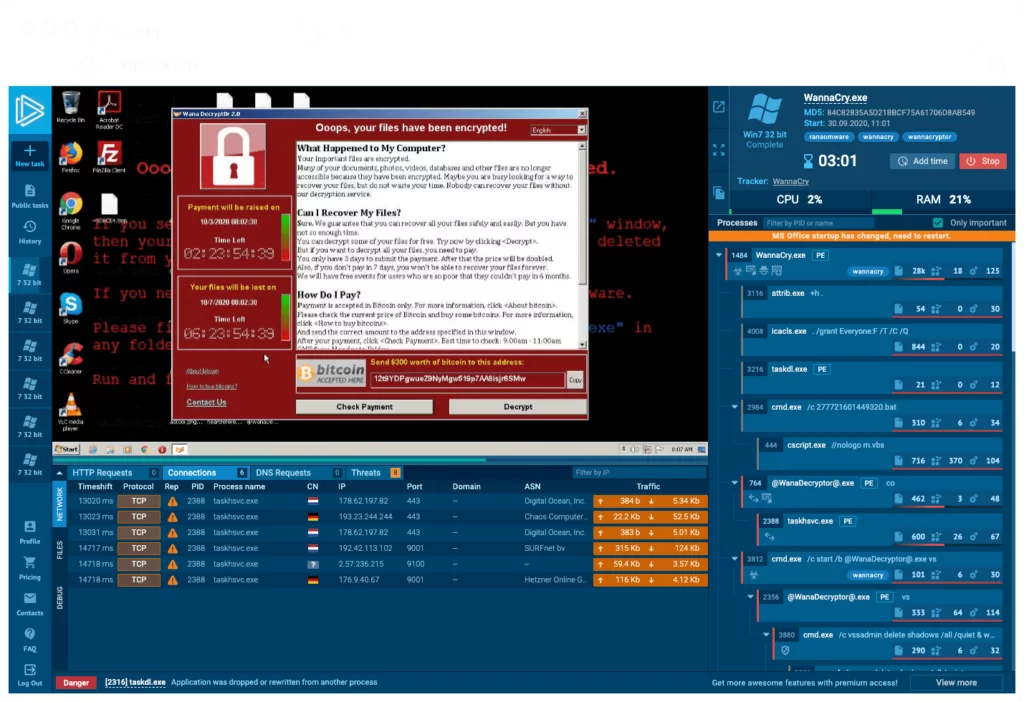
- Pros: Real-time behavior analysis, interactive sandbox environment, collaboration features.
- Cons: Limited capabilities for free users, requires a subscription for full access to advanced features such as, private reports and more advanced Windows versions. For free users, only Win 7/32 bit is available .
Joe Sandbox
Joe Sandbox is a comprehensive malware analysis platform that caters to static and dynamic analysis techniques. It offers a range of analysis options, including file and URL submissions, and provides detailed reports on behavioral activities, network connections, and system changes.
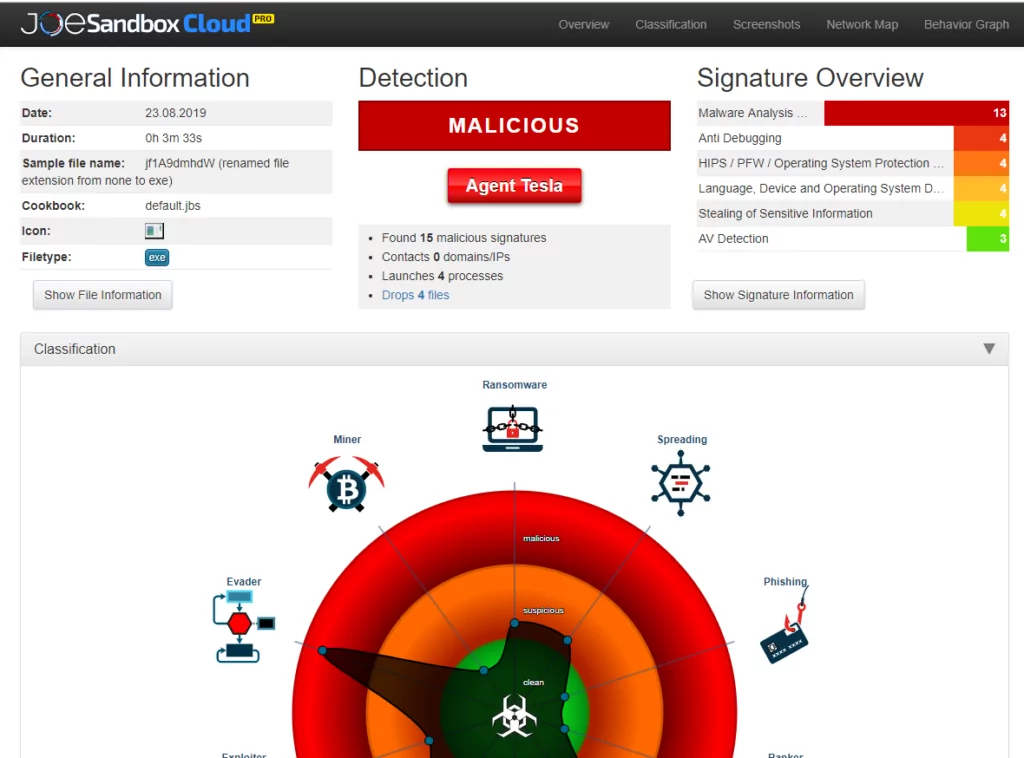
- Pros: Rich feature set, extensive behavioral analysis, customizable analysis configurations.
- Cons: Monthly limits for free users, a business e-mail is required, may have a steep learning curve for beginners.
Viper Framework
Viper Framework is a binary analysis and management platform. It incorporates various analysis techniques under its different modules. Viper Framework offers a user-friendly web interface to upload and analyze files and the ability to create and export analysis profiles.
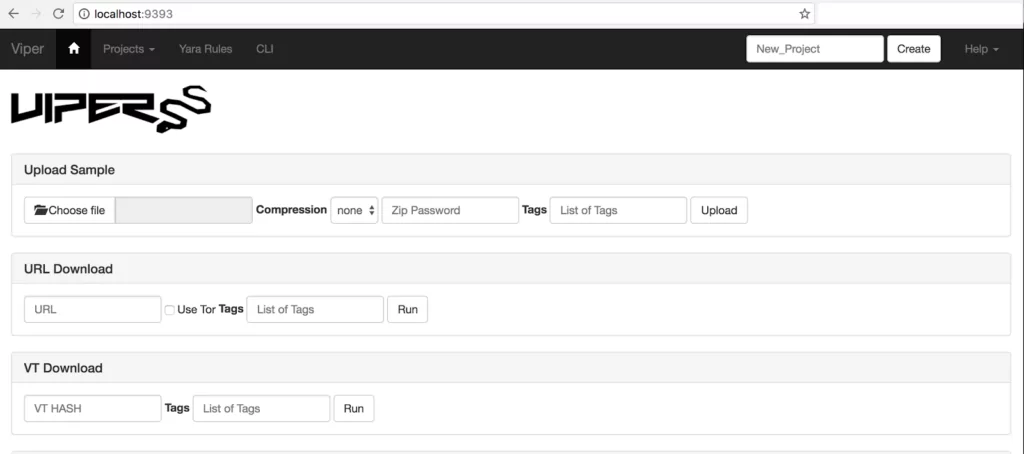
- Pros: Open-source and customizable, supports multiple analysis techniques, collaborative features.
- Cons: Although it can act as an analysis tool, its primary purpose is malware and script collection organizer, and analysis sources are dependent on external sources such as VirusTotal.
Tria.ge
Triage, also known as the Triage Sandbox, is an advanced malware sandboxing solution initially created by Hatching. It provides users with the ability to execute malware samples within a secure and isolated environment, enabling the analysis of their actions and evaluation of their potential risks.
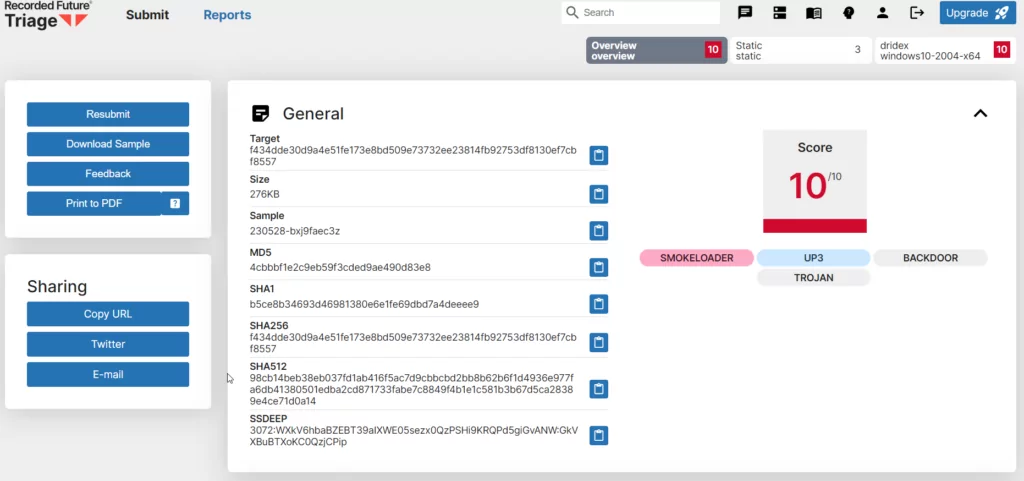
- Pros: Supports automated malware analysis for many platforms such as Windows and Linux, Android, and macOS. In addition to static analysis reports, provides an easy-to-use sandbox environment up to Windows 10 for free.
- Cons: There is no Windows 11 support yet, and the reports must be open to the community as long as the enterprise membership is not purchased.
FileScan
FileScan.IO is an advanced sandboxing solution and a free malware analysis service. What sets it apart is its unique adaptive threat analysis technology, enabling zero-day malware detection and extracting a greater number of IoCs. Importantly, FileScan.IO offers these capabilities to users without any cost.
- Pros: Conducts IoC extraction for uploaded files, provides users with the convenience of uploading private files securely, with the option to encrypt the uploaded files.
- Cons: Some community feedback complains that the results are sometimes not accurate.
Cape Sandbox
CAPE (Malware Configuration And Payload Extraction) is a malware sandbox that was published on Github in September 2016. It is based on Cuckoo (more specifically, spender sandbox) and can automatically extract payload and configuration information from a wide range of well-known malware. It was derived from Cuckoo in order to add automated malware unpacking and configuration extraction.
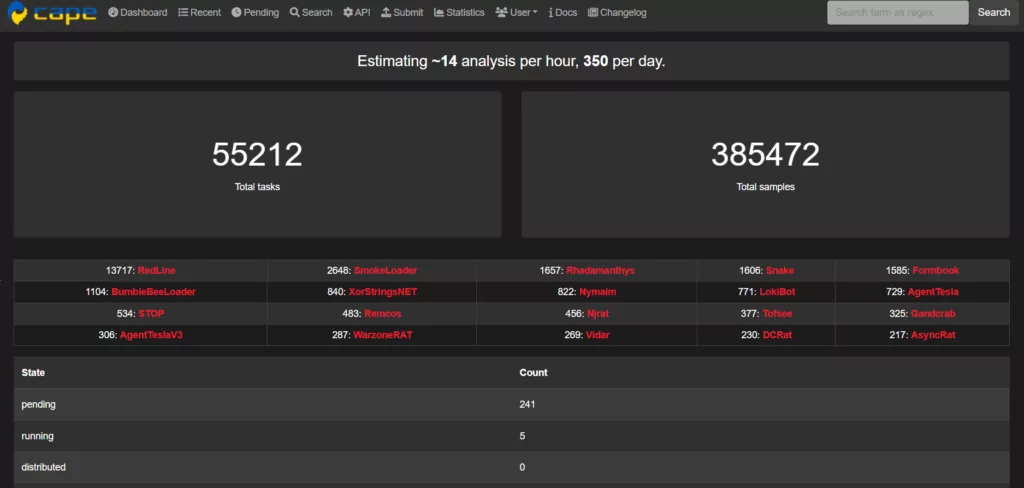
- Pros: It is open source and has a free version available to the community. It effectively detects evasive malware by providing dynamic countermeasures with Yara signatures.
- Cons: It mostly works slowly, and you have to activate your registered membership by contacting via Twitter.
Other Tools to Assist the Malware Analysis
Ghidra
Ghidra is a powerful open-source software reverse engineering framework developed by the National Security Agency (NSA). It provides many features, including disassembly, decompilation, and scriptable analysis. Ghidra supports various file formats and assists analysts in understanding the inner workings of malware.
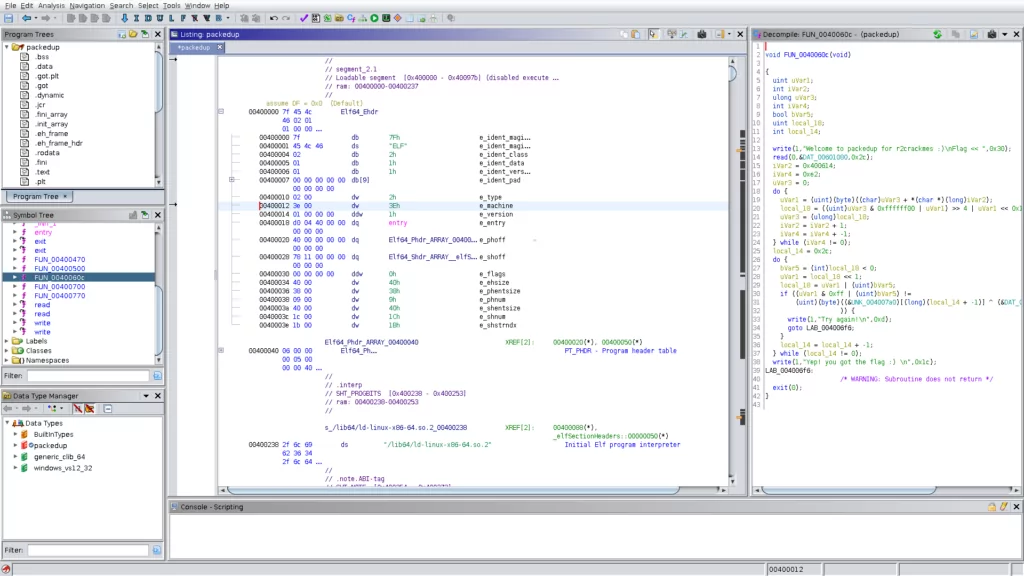
- Pros: The decompiler tool generates readable code, the collaborative analysis element encourages collaboration, and the GUI is simple to use.
- Cons: Lacks substantial debugging features. It is necessary to have a powerful computer because analyzing large files might be resource-intensive.
X64dbg
x64dbg is an advanced debugger for Windows systems. It is a popular tool for Malware Analyzers and stands out among other debuggers. This is because it has a user-friendly interface, a built-in disassembler, and a powerful script language. In reverse engineering, it helps to gain insight into the inner workings of software/malware by disassembling its code, but it is also helpful for software developers to identify and resolve bugs.
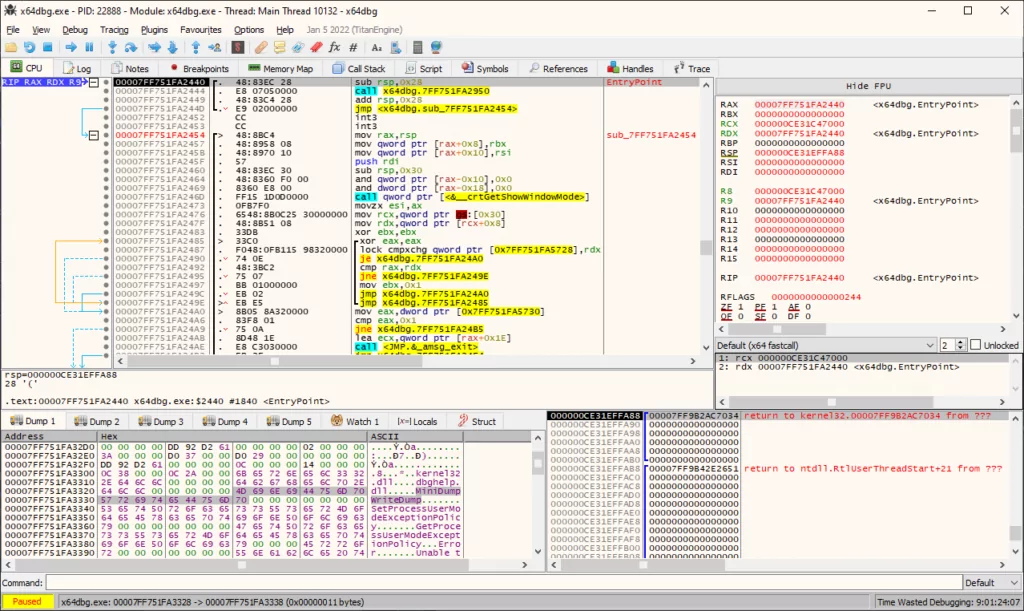
- Pros: It is open-source software, and it is possible to modify it as desired, benefit from community plugins, and even add your own plugin.
- Cons: Advanced features include steep learning curves, even for experienced security experts.
IDA Pro
Since IDA Pro has been around since 1991, it is one of the oldest and most classic tools, so there is little to say about it. IDA Pro, both a disassembler and a debugger, is well known for its solid architecture analysis capabilities.
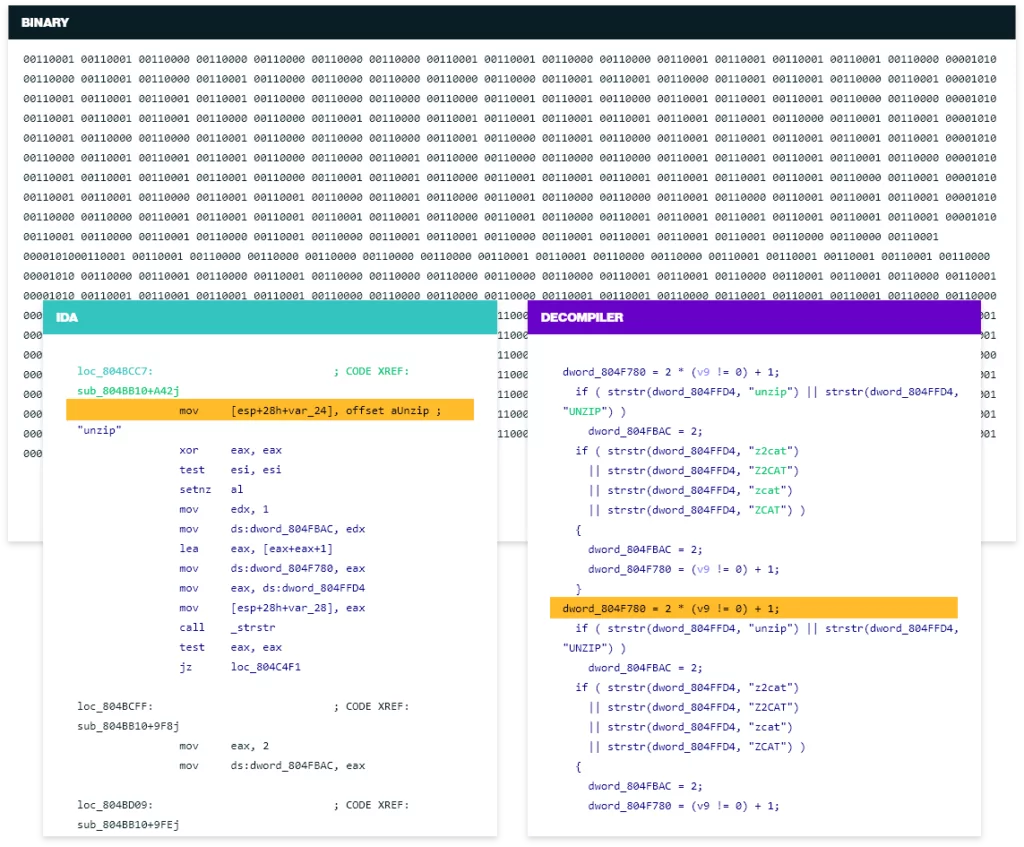
- Pros: It supports various platforms like Windows, Linux, and macOS/iOS. It is suitable for a wide range of uses as it gathers features such as disassembly, decompilation, and debugger under a single roof.
- Cons: Requires a large amount of RAM and processing power; therefore, running on under-resourced virtual machines can be difficult.
Conclusion
These platforms and tools we have listed will help analysts at different levels depending on their needs and experience. While each platform has its advantages and disadvantages, security researchers should keep multiple platforms and tools handy.
In addition to its many features, SOCRadar can help your efforts with its Malware Analysis module, allowing you to analyze a very extensive array from Binary to Office files including EML files while getting instant reports of the files you have uploaded.
SOCRadar’s Malware Analysis is designed to provide users with a comprehensive understanding of malware samples, allowing for swift identification and analysis. The tool boasts a range of functionalities to assist security teams in combatting and neutralizing potential threats.
Key Features:
- Static Analysis: SOCRadar’s Malware Analysis performs static analysis to examine the code structure, identify critical functions, and detect potential vulnerabilities or malicious intent.
- Threat Intelligence Integration: It leverages threat intelligence feeds, enabling users to correlate malware samples with known IoCs and gain insights into the broader threat landscape.
- Reporting and Visualization: SOCRadar’s solution provides detailed reports and visualizations, allowing security professionals to effectively understand and communicate the findings. These reports aid in decision-making processes and facilitate collaboration within security teams.
- Supported File Formats: SOCRadar Malware Analysis can analyze a larger array of file types more than many tools. Supported formats include: .slk .csv .xls .xll .xlw .xlt .wbk .xlsx .xlsm .xlsb .xlam .xltx .xltm .doc .dot .rtf .docx .docm .dotx .dotm .wll .ppt .pps .pptx .pptm .ppsx .ppam .pub .pdf .lnk .hta .html .htm .xhtml .js*** .zip .7z .rar .iso .vhd .vhdx .eml .msg
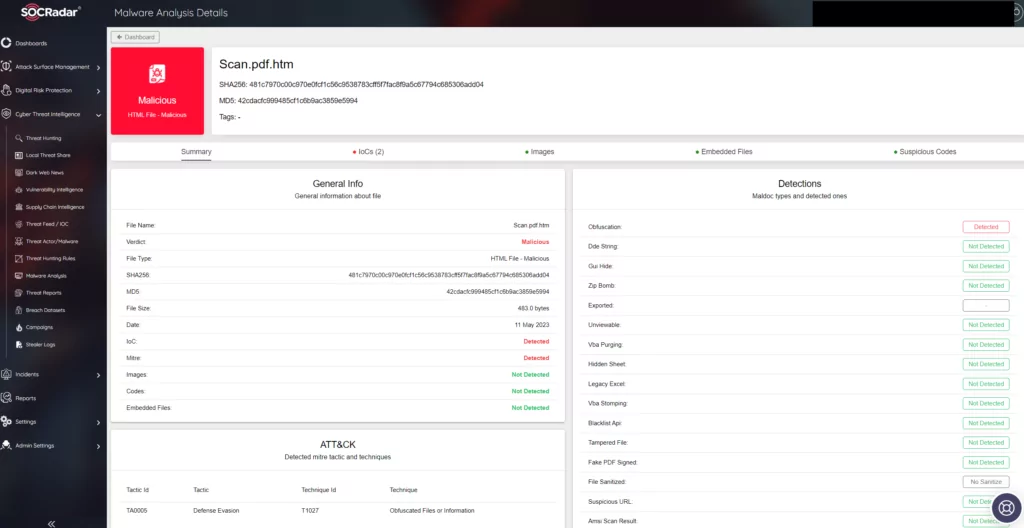
In addition to the Malware Analysis feature embedded in the platform, you can use the EML analyzer, and Grader features separately within SOCRadar Labs for free as well.