
Top Threat Intelligence Use Cases for the E-Commerce Industry-I
The prevention of the landscape is no longer enough in today’s cybersecurity. All have never faced such high and concrete threats from advanced phishing operations to ransomware attacks to digital payment platforms and consumer databases of e-commerce firms.
What are the biggest cyber challenges for the e-commerce industry?
Cybercriminals targeting this industry have developed sophisticated and frequently programmed Tactics, Techniques, and Procedures (TTPs) to compromise and monetize stolen data and perform fraudulent activities.
From convincing phishing attacks tricking people into sharing personal and financial information, account hijacking to commit criminal acts, digital payment systems, and consumer accounts’ digital vulnerability has never been so high. The following statistics can show how cyber attacks could be a nightmare for SMEs.
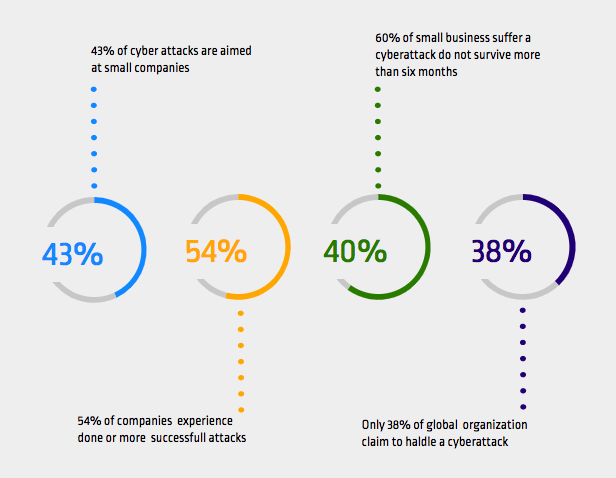
- In six months following a security threat, 60 percent of businesses are estimated to be shut down in operation.
- There are daily Magecart attacks on SMEs.
- Roughly 29% of the traffic on the website for e-commerce includes cyber threats.
- E-commerce fraud is estimated to result in a loss of $660,000 per hour.
- 25% of data breaches are mainly aimed at e-commerce purchase payments.
In recent years, there has been a rise in the number of attacks on e-commerce. The company consequence is evident: decreased income and declines in shareholder value; bad press leading to a decrease in customer confidence; millions in violation costs and related penalties. There is no question of a much bigger threat to e-commerce businesses than online payments. The following use-cases can show how serious these threats and damages are.
What are the cyber threat intelligence use-cases for the e-commerce industry?
Phishing attacks
Phishing is an attempt to trick users into revealing sensitive information such as PII, account credentials, or credit card details.

In 2019, McAfee announced that Amazon was recently attacked based upon a popular phishing package called 16Shop. Although the kit was designed for Apple users and has been targeted at the first, an updated version then targeted Amazon shoppers. 16Shop allows malicious actors to deliver disguised emails that seem to come directly from Amazon itself. The phishing emails containing links to a fake website with the same look as the Amazon login page. The fake webpage is intended to gather data from unsuspected victims.
Phishers use a wide variety of registrars to purchase domains. Registrars that offer free registration are often top choices. Cyber Threat Intelligence (CTI) can use this information as another input to detect phishing sites and inform organizations right away.
Credential stuffing attacks
Credential stuffing is a controlled injection of compromised username/password pairs to obtaining fraudulent access to user accounts. This is a subset of the brute force attacks: a large number of compromised credentials are tried in login pages using automation to find a combination that works.

On the 20th August 2018, Superdrug company in the UK targeted alleged blackmail, which shows hackers breaching the site and stealing 20,000 user data. Then these data are used for credential stuffing attacks to glean fake proof information.
To gather information such as data leakage, sensitive information, vulnerabilities related to the business in real-time, CTI continuously monitors the internet, deep web, and obscure sites.
Magecart attacks
Web skimming attacks are essentially easy, but specialized technological capabilities are necessary from hackers. The aim is for hackers to obtain access to a backend server, relevant tools, or third-party widgets of a store website, where malicious code is installed and executed on the frontend of the website. There are two strategies for Magecart attacks for hackers; the first is to target the web portal or program and the second is to take advantage of tags from third parties. In both instances, malicious JavaScript is implemented to bypass information from HTML forms and to transfer this data to attacker-controlled servers.

In 2019, Macy’s confirmed a breach of Magecart card-skimming code on the online payment portal of the organization. Although Macy’s code was deleted the next day, shoppers who placed online orders or put financial details in their wallets have been deprived of their details.
Hacking teams, funded by the state of North Korea, hack into online shops to inject malicious code that can capture the data of their payment card as they access the checkout page and complete payment forms.
CTI researchers discovered a web skimmer that offers payment information by inserting HTML iframe into the targeted pages and informing related organizations to prevent the cyber incident from spreading.
Third-party attacks
Third-party attacks are drastically changing the threat landscape for organizations. Attackers can infiltrate the infrastructure of a third party who has access to the ultimate target.
In 2020, a third-party app used by EU merchants on Amazon UK, PayPal, and Shopify was hacked. 8 million sales records including customers’ data were stolen.
Debenhams Flowers hacked via Ecomnova a third-party eCommerce provider and the details of 26,000 people were revealed. During the attack, hackers stole payment details, names, addresses, and financial information.
The threat intelligence targeting diverse sectors and third parties must be included in a successful third-party risk program. The vulnerability data will then be used to model hacker workflows for identified attack scenarios. The threat information is comprehensive. This review helps to recognize measures for security that can prevent and avoid these attacks both in business and across portfolios critical of third parties.
Dark web sales
The dark web is where deception and crime organizations are found. It is the latest business risk hotbed. Regular search engines such as Google or Bing do not index the dark web. Financial data like stolen payment cards, credit and debit cards, or account credentials can be found all over the dark web. Sometimes massive information including both usernames and passwords, called combo lists, are on-sale or given for free on the dark web.

Minted, a US-based independent artists’ market, has announced a data leak after a hacker sold a five-million-user account on a dark web market. Minted is an online marketplace that gives individual artists the ability to show their work, which the minted audience then votes. The good applications would then be sold to the customer as paintings, home decor, and paperwork.
Increased data protection can be accomplished by leveraging knowledge from hacker groups such as the dark web. Such information on risks should be made accessible to a vast range of organizations to facilitate protection measures and to secure their facilities more and more efficiently. The path to future advancement in this field is ongoing innovation and automation. CTI can find breached credit or debit cards on deep web or darknet marketplaces immediately and warn related financial institutions right away to be able to limit the damage.
How threat intelligence can help the e-commerce industry?
There are too many security risks to e-commerce. The best thing, though, is to be prepared just to avoid cyber threats from occurring with CTI.
The threat intelligence is actionable, automated information, so that businesses can identify and prioritize threats both in and outside their network. This is so important because it helps cybersecurity departments to concentrate their attention on the most important risks to their network.
To recognize and secure sensitive assets such as customer and payment information and intellectual property, threat intelligence is highly effective. It will help e-commerce business owners determine where and how the attackers are involved in these assets. With this information, security teams will enforce adequate protection measures in advance.
SOCRadar help financial services by providing unified threat intelligence solutions
SOCRadar provides the actionable and timely intelligence context you need to support financial services with external attack surface management, digital risk protection, and threat intelligence capabilities modules.

SOCRadar’s ThreatFusion provides actionable insights into future cybersecurity threats with a big data-powered threat investigation module to assist in searching deeper context, real-time threat investigation, and analysis.
SOCRadar’s RiskPrime builds on industry-leading instant phishing domain identification, Credit card monitoring, customers’ PII protecting, and compromised credential detection technologies by aggregating and correlating massive data points into actionable intelligence alerts.
SOCRadar’s AttackMapper provides insight and visibility into these assets to discover and monitor everything related to your organization on the Internet to bring the enormous scale of your attack surface into focus.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.


































