
Top Threat Intelligence Use Cases for the E-commerce Industry-II
Prevention of the landscape is no longer enough in today’s cybersecurity. All have never faced such high and concrete threats from advanced phishing operations to ransomware attacks to digital payment platforms and consumer databases of e-commerce firms.

What are the biggest cyber challenges for the e-commerce industry?
Cybercriminals targeting this industry have developed sophisticated and frequently programmed tactics, techniques, and procedures (TTP) to compromise and monetize stolen data and perform fraudulent activities.
From convincing phishing attacks tricking people into sharing personal and financial information, account hijacking to commit criminal acts, digital payment systems, and consumer accounts’ digital vulnerability has never been so high. The following statistics can show how cyber attacks could be a nightmare for SMEs.
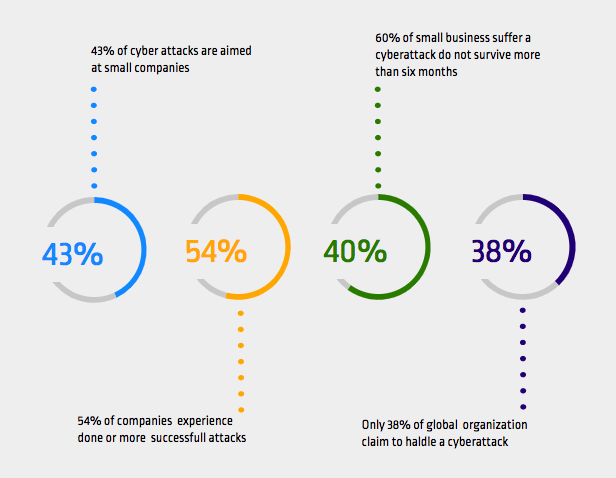
- In six months following a security threat, 60 percent of businesses are estimated to be shut down in operation.
- There are daily Magecart attacks on SMEs.
- Roughly 29% of the traffic on the website for e-commerce includes cyber threats.
- E-commerce fraud is estimated to result in a loss of $660,000 per hour.
- 25% of data breaches are mainly aimed at e-commerce purchase payments.
In recent years, there has been a rise in the number of attacks on e-commerce. The company consequence is evident: decreased income and declines in shareholder value; bad press leading to a decrease in customer confidence; millions in violation costs and related penalties. There is no question of a much bigger threat to e-commerce businesses than online payments. Following use-cases can show how serious these threats and damages are.
What are the cyber threat intelligence use-cases for the e-commerce industry?
DDoS attacks
Denial of Service is a cyberattack that aims to temporarily or indefinitely disrupt the services of a host connected to the Internet, making a machine or network resources unavailable to actual users.
DDoS provider Link11 experienced DDoS attacks on e-commerce vendors rising by over 70% in contrast to the other days on Black Friday. In 2018, Attacks rose 109 percent on Cyber Monday, relative to the average in November. Several attacks on Black Friday and Cyber Monday went up to 100 Gbps, with each under 6 Gbps, as usual, relative to the usual 4,6 Gbps for July and September, a rise of 40 percent compared to the last quarter.

CTI can provide preemptive protection against DDoS attacks by providing real-time monitoring of botnets and their activities.
Threat actors
Due to rising creative and complicated fraud tactics and a massive amount of compromises in available data, the e-commerce industry is predicted to cost US $130 billion in Card-not-present (CNP) fraud between 2018 and 2023.
FIN6 is a threat actor group that focuses on e-commerce websites and operates since 2015. The group has abused the use of TRINITY POS (also called FrameworkPOS) malware by using a number of POS environments. In September 2017, forensic studies performed by many unrevealed organizations found that FIN6 actors moved to card non-present (CNP) target data when they were unable to execute their POS malware.

CTI provides information on malicious actors, their tools, and their infrastructure to be able to prevent or minimize the risks against such threats. The knowledge of the risks actors’ tactics, techniques, and procedures helps in detecting their presence in a network. Furthermore, by providing an understanding of the threat actors’ purposes and capacity, CTI analysts will improve incident response services including minimizing the damage in case of a compromise.
Zero-day vulnerabilities
A zero-day vulnerability is a cyber-security bug known to the software supplier but not patched by the update.
In the past 12 months, almost 2/3 of the e-commerce companies have been affected by zero-day attacks that have occurred at endpoints, according to a study undertaken at the Ponemon Institute dubbed the “2018 Status of Endpoint Protection Vulnerability Survey.” These attacks can be disruptive, with an estimated $7.12 million or $440 per endpoint cost to the average organization.
The zero-day potential of accused private corporations’ clients is gradually commoditized by the number of zero-days found in the wild. The number of zero-days used by organizations suspected or believe to be clients of private corporations who are offering aggressive cyber services has risen dramatically. Threat intelligence platforms can alert organizations to zero-day vulnerabilities as soon as they are known.
VIP accounts
Company executives are more likely to be the target of cyberattacks since they have more privileges within the organization.
Hackers often send malicious context into a social media box of e-commerce companies and wait for the message to be clicked on. These contexts affect not just the security of the website, but also the reputation of the website. Graham Ivan Clark, 17, reportedly hijacked 130 Twitter profiles. The hacked accounts included Amazon.com Inc. CEO Jeff Bezos and Tesla Inc. President and CEO Elon Musk.

CTI defends VIP accounts against account takeovers, spear-phishing, ransomware, abuse risks, and misrepresentation by monitoring the surface, deep, and dark web.
SSL and domain attacks
SSL certificates provide confidentiality for connections over the internet. They are commonly used for connecting to websites but they may be used to secure any communication over the internet. They are also used for validating software. Maintaining an SSL certificate has many aspects. They expire, they can be misconfigured, or they may be compromised. Any of these issues can create serious problems for businesses.

Security researchers say thousands of new websites that include terms such as Coronavirus, COVID, pandemics, virus, or vaccine are being released every day. Although certain websites may be legal, analysts think several domains are used to deter online fraud. According to the study, cybercriminals created more than 3,600 new domains related to covid-19 just between March 14 and 18.
Cyber threat intelligence platforms can monitor WHOIS records for expiration dates or important changes and can alert the organizations immediately. SSL monitoring can help organizations to stay ahead of malicious cyber-attacks and business disruptions.
How threat intelligence can help the e-commerce industry?
There are too many security risks to e-commerce. The best thing, though, is to be prepared just to avoid cyber threats from occurring with CTI.
The threat intelligence is actionable, automated information, so that businesses can identify and prioritize threats both in and outside their network. This is so important because it helps cybersecurity departments to concentrate their attention on the most important risks to their network.
In order to recognize and secure sensitive assets such as customer and payment information and intellectual property, threat intelligence is highly effective. It will help e-commerce business owners determine where and how the attackers are involved in these assets. With this information, security teams will enforce adequate protection measures in advance.
SOCRadar help financial services by providing unified threat intelligence solutions
SOCRadar provides the actionable and timely intelligence context you need to support financial services with external attack surface management, digital risk protection, and threat intelligence capabilities modules.

SOCRadar’s ThreatFusion provides actionable insights into future cybersecurity threats with a big data-powered threat investigation module to assist in searching deeper context, real-time threat investigation, and analysis.
SOCRadar’s RiskPrime builds on industry-leading instant phishing domain identification, Credit card monitoring, customers’ PII protecting, and compromised credential detection technologies by aggregating and correlating massive data points into actionable intelligence alerts.
SOCRadar’s AttackMapper provides insight and visibility into these assets to discover and monitor everything related to your organization on the Internet to bring the enormous scale of your attack surface into focus.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.



































