
Unauthorized Fortinet VPN Access, Chrome Extension Loader, New macOS Stealer, and More
Explore the latest revelations from the SOCRadar Dark Web Team; our latest discoveries involve unauthorized VPN sales targeting prestigious organizations, a new macOS stealer tool, and a batch of Singaporean credit cards for sale. Particularly alarming is the sale of a private loader for Chrome extensions, raising concerns of data theft, malicious code injection, and more.
Without delay, let’s uncover the dark realities of the digital underworld.
Receive a Free Dark Web Report for Your Organization:
Unauthorized VPN Access Sales Detected for Multiple Companies
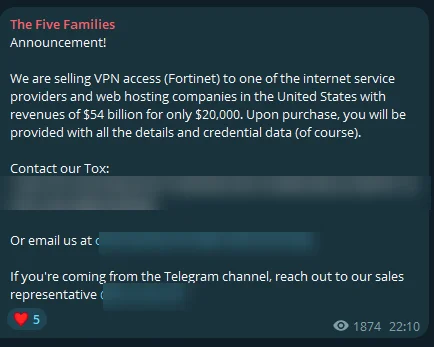
On February 11, The SOCRadar Dark Web Team, monitoring The Five Families Telegram channel, stumbled upon allegations of unauthorized VPN access sales targeting various organizations. Among the claims, the threat actor alleged selling VPN access to a Taiwanese university with reported revenues of $9 million for a mere $500.
Additionally, an assertion of offering similar access to a U.S. insurance company, boasting $36 million in revenues, for $950, was observed. The most audacious of these claims involves purported VPN access to a major U.S. internet service provider and web hosting company, with staggering revenues of $54 billion, priced at $20,000.
Each allegation includes the promise of detailed credential data upon purchase, hinting at a breach of security protocols via Fortinet VPN vulnerabilities or compromised credentials.
macOS Stealer Tool Sale is Detected
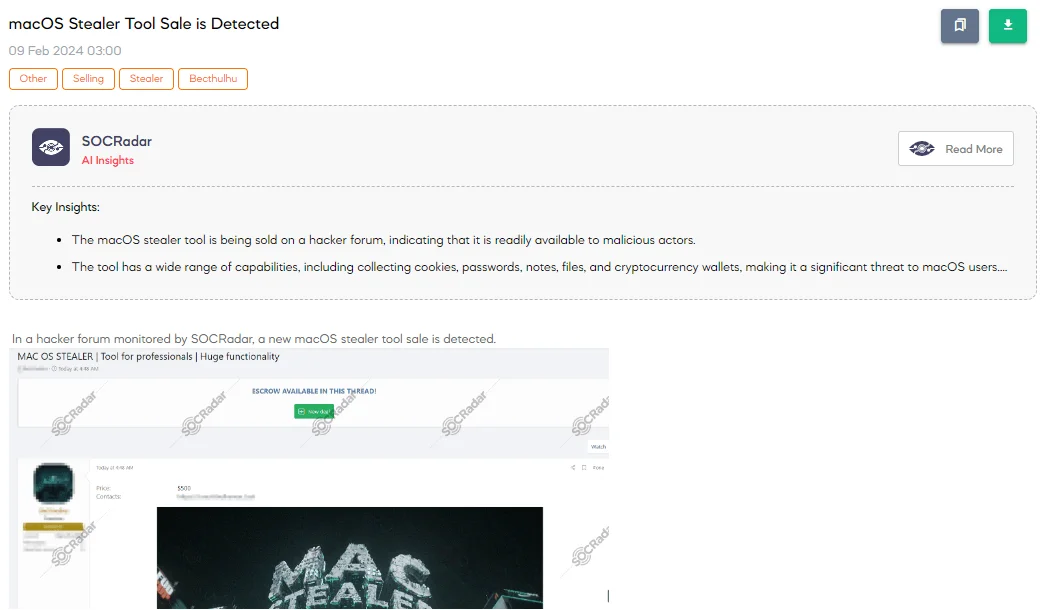
SOCRadar Dark Web Team has identified a post on a hacker forum where a threat actor is advertising the sale of a new macOS stealer tool. This tool is priced at $500 and is claimed to possess a variety of functionalities aimed at compromising the security of macOS users.
According to the threat actor’s claims, the tool’s capabilities include collecting cookies and passwords from browsers like Chrome, Firefox, and Brave; gathering and automatically transcribing Notes; executing a Fast FileGrabber for file types such as .TXT, .RTF, .DOCX, .JPG; decrypting and collecting Keychain data; and extracting information from more than 10 desktop wallets and over 90 web wallets, including MetaMask. It can also collect passwords from Steam, Telegram, and FileZilla accounts.
Crucially, the tool is marketed with a geo-block feature that restricts its operation in CIS countries, with a strict prohibition on its use or discussion in Russia. This restriction provides essential information about the threat actor.
600 Credit Cards Belonging to Singapore are on Sale
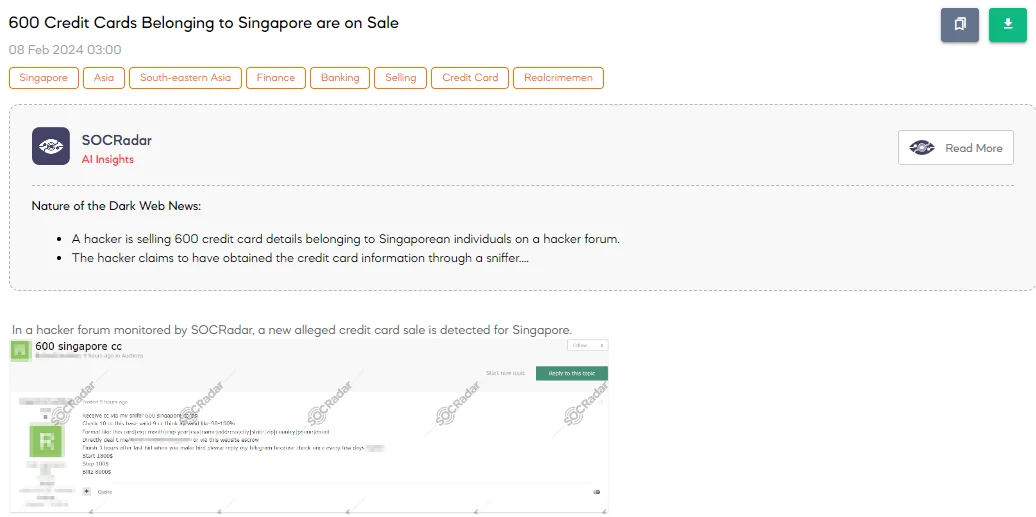
The SOCRadar Dark Web Team has discovered a post on a hacker forum where a threat actor claims to be selling a batch of 600 credit cards purportedly originating from Singapore. The threat actor alleges that these cards were obtained through a sniffing operation, suggesting a high validity rate of 90-100% based on a sample check where 9 out of 10 cards were valid. The data format provided for these cards includes sensitive information such as the card number, expiration date, CVV, cardholder’s name, address, city, state, zip code, country, phone number, and email address.
Private Loader Method for Chrome Extensions is on Sale
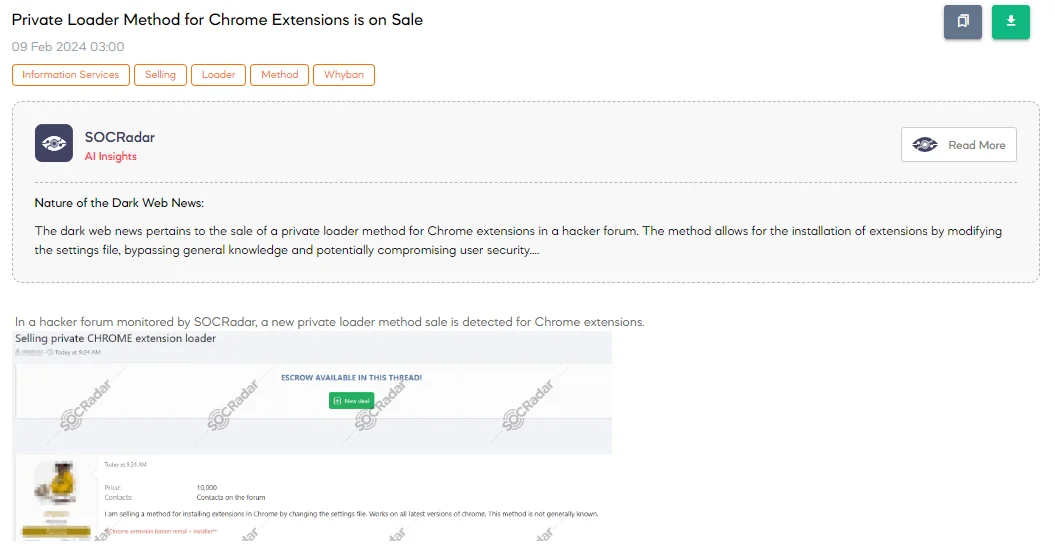
The SOCRadar Dark Web Team’s discovery of a post on a hacker forum advertising a new private loader method for Chrome extensions raises significant concerns. The threat actor is offering this method for a notably high price of $10,000, asserting that it enables the installation of extensions in Chrome by altering the settings file, and claims compatibility with all latest versions of Chrome. Additionally, the seller suggests that this technique is not widely known, potentially adding to its value among cybercriminals looking for novel ways to circumvent browser security mechanisms.
The asking price of $10,000 is very high, reflecting the perceived value of a method that can bypass Chrome’s security features to install extensions without user consent or knowledge. Threat actors could use such a method for various malicious purposes, including but not limited to data theft, spying, and injecting malicious ads or code.
Unauthorized Access Sale is Detected for Ledger
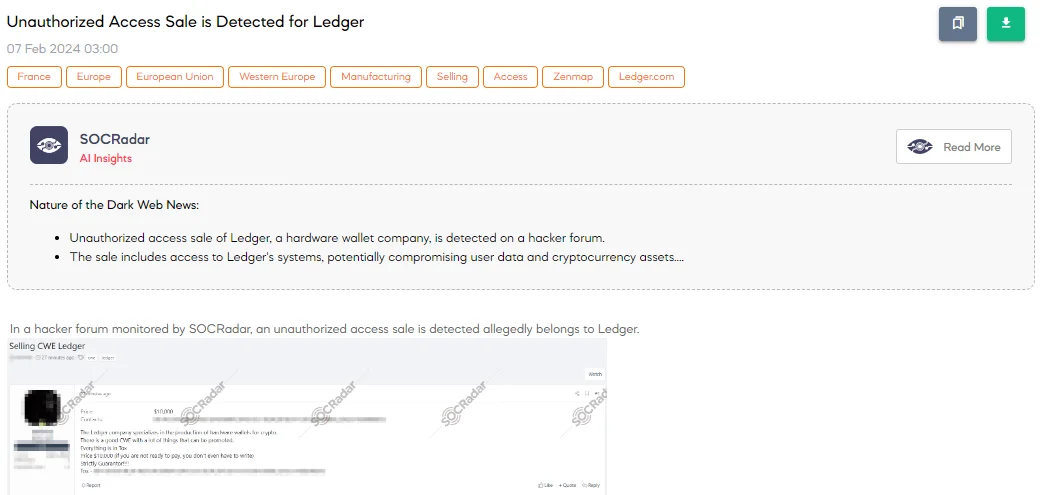
A SOCRadar Dark Web Analyst has detected a post on a hacker forum where a threat actor claims to sell unauthorized access allegedly belonging to Ledger, a company known for producing cryptocurrency hardware wallets. The access is offered at $10,000, with the seller insisting on communication through Tox, a peer-to-peer instant messaging and video-calling software that offers end-to-end encryption.
The threat actor emphasizes the presence of a good Common Weakness Enumeration (CWE) within the system, suggesting that threat actors can leverage multiple vulnerabilities or points of exploitation for malicious purposes. The insistence on a “Strictly Guarantor” arrangement implies that the transaction would involve a third party to hold the funds until the terms of the sale are met, aiming to add a layer of trust to the transaction.
Unauthorized Access Sale is Detected for a Singaporean POS Terminal
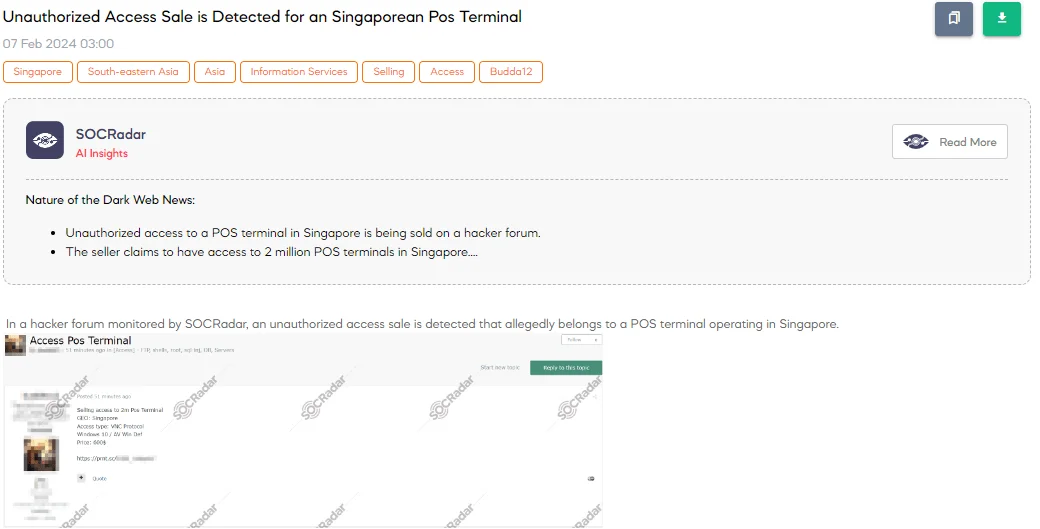
The SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor is allegedly offering unauthorized access for sale to a POS (Point of Sale) terminal operating in Singapore. The sold access purportedly utilizes the VNC (Virtual Network Computing) protocol, allowing remote control of another computer’s screen. The specified system is reported to be running Windows 10 with Windows Defender as its antivirus solution. The price set for this unauthorized access is $600.
Unauthorized Admin Access Sale is Detected for an Italian Energy Company
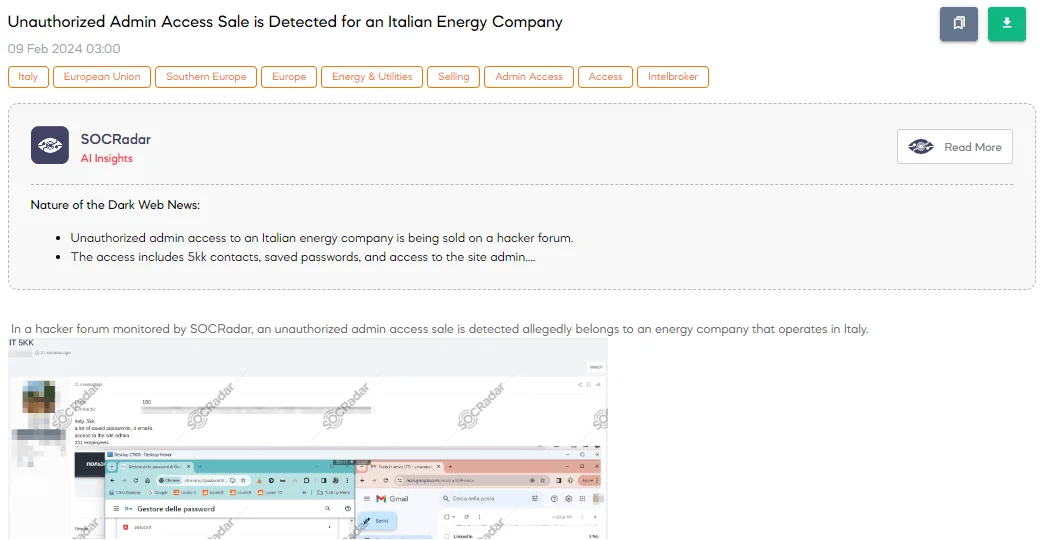
A SOCRadar Dark Web Analyst has identified a post on a hacker forum where a threat actor is advertising the sale of unauthorized administrative access, purportedly belonging to an Italian energy company. The company in question reportedly has a 5 million-dollar revenue, indicating it’s a significant player in the energy sector. The access is being offered at a relatively low price of $150, suggesting the threat actor may seek a quick transaction.
According to the threat actor, the sale includes not just administrative access to the company’s site but also a collection of saved passwords and access to three email accounts associated with the company.
Unauthorized Mail Access Sale is Detected for the Argentine Federal Police
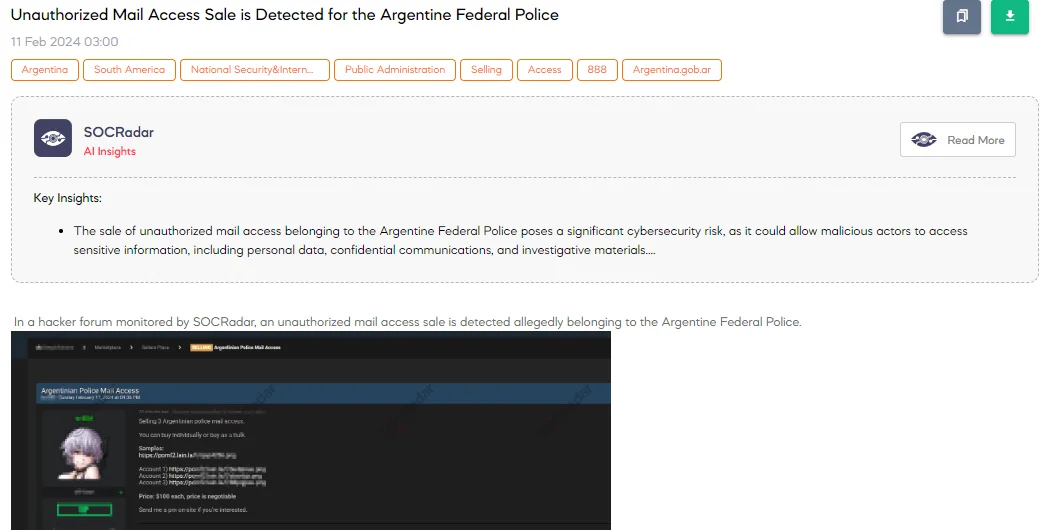
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor claims to be selling unauthorized access to email accounts allegedly belonging to the Argentine Federal Police. The threat actor is offering access to three different police email accounts. Each account is priced at $100.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































