
Spain Database and Australian Access Sale, Everlast Breach, macOS Metamask Stealer, New Microsoft Exploit
In the latest edition of the Week in Dark Web, the SOCRadar Dark Web Team has uncovered significant revelations, such as the sale of a government database, a data breach involving over 400,000 lines of data, and the availability of the source code for a macOS Metamask stealer. Additionally, we bring attention to the discovery of a new Microsoft exploit.
Find out if your data has been exposed.
Database of Spain Government is on Sale
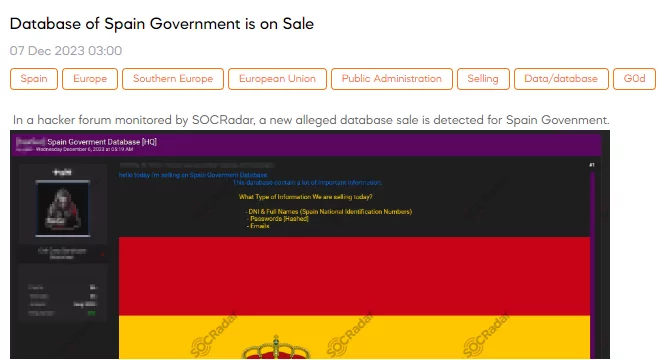
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor claims to sell a database allegedly belonging to the Spanish government. According to the threat actor, the offered database contains critical information, including DNI (Documento Nacional de Identidad) numbers, full names of individuals, hashed passwords, and email addresses.
Database of Everlast is Leaked
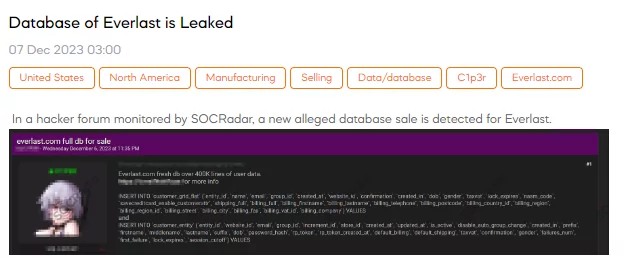
The SOCRadar Dark Web Team has identified a post on a hacker forum indicating a potential data breach of Everlast. The threat actor claims to be selling an Everlast[.]com database containing over 400,000 lines of user data. The provided SQL queries suggest that the leaked data includes a variety of personal information such as names, email addresses, group IDs, creation dates, website IDs, and more.
Source Code of MacOS Metamask Stealer is on Sale
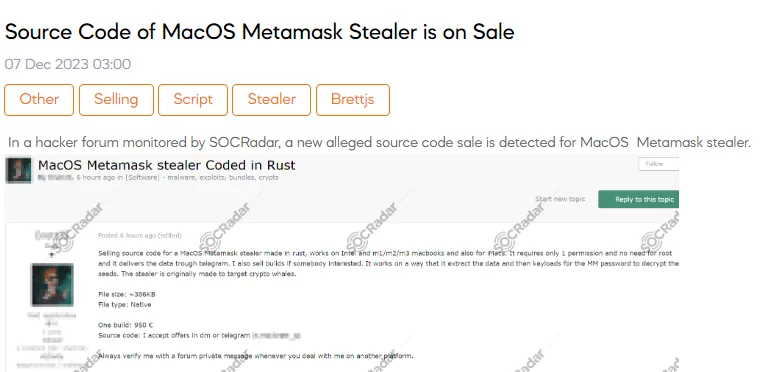
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor claims to sell the source code of a MacOS Metamask stealer. According to the threat actor, this malicious tool, developed in Rust, is purportedly compatible with Intel and various Macbook models, including M1, M2, and M3, as well as iMacs. The stealer operates with minimal permissions, does not require root access, and reportedly transmits stolen data through Telegram. The attacker emphasizes the tool’s capability to extract and subsequently decrypt Metamask seeds by keyloading for the Metamask password, suggesting a focus on targeting cryptocurrency enthusiasts. The file size is approximately 386KB, and the threat actor offers both a single build for €950 and the complete source code, with interested parties encouraged to make offers via direct message or Telegram.
New Exploits are on Sale
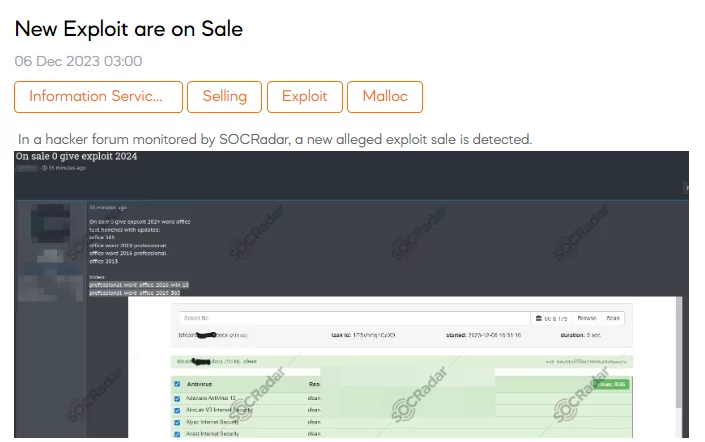
The SOCRadar has discovered a post on a hacker forum indicating the sale of a new exploit. The threat actor claims to offer an exploit for Microsoft Word 2024, along with test benches and updates for various Office versions, including Office 365, Office Word 2019 Professional, Office Word 2016 Professional, and Office 2013. The post includes a video showcasing the exploits, specifically highlighting compatibility with Windows 10 for Office 2016 and 2019. The price for this exploit is 10.210875 BTC (Bitcoin).
Unauthorized RDP Access Sale is Detected for an Australian Company
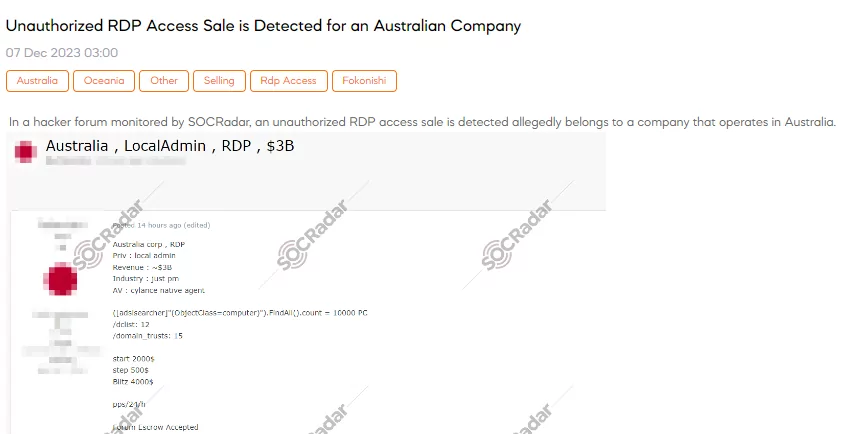
The SOCRadar Dark Web Team has uncovered a hacker forum post advertising the unauthorized sale of RDP access to an Australian company, including details on revenue, industry, and security measures. The threat actor is asking for a starting price of $2,000, with increments of $500 and a Blitz (instant buy) option for $4,000. The post also mentions the use of a forum escrow for the transaction.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































