Under the Spotlight: State of Evolving Australian Threat Landscape in 2023
While cyber-attacks gain momentum in parallel with the increase in digitalization, companies operating in both public and private sectors continue to experience the effects of cyber-attacks; what is concerning, if unsurprising, is the different forms of financial and reputational losses that shake up the industries.
Data breaches have been more prevalent in recent years than ever before, with two of the reasons for them being the expanding attack surface and the sophistication of cyber-attacks. According to many research insights, the Asia-Pacific had the privilege of being the global region heavily exposed to the most cyber-attacks, especially ransomware, prompting calls for Australia to do more to safeguard critical infrastructure and businesses from costly extortion during 2022.
Particularly, after the suffering of Medibank and Optus massive breaches, it’s worth mentioning that the Australian government took a series of measures such as increasing cyber defense investment($ 1.7 billion), establishing an army to hack the hackers, and aggravating legal penalties. Despite mentioned security measures taken in 2022, according to SOCRadar, Australia is still an attractive target of cyber criminals by falling victim to many kinds of cyber-attacks. In this article, we will examine the data breaches and ransomware incidents peculiar to Australia in 2023 via a data-driven analysis of emerging security and intelligence trends.
Key Findings
- SOCRadar Research analysts identified and analyzed more than 100 cyber incidents related to Australia since the beginning of 2023 and reached the following key conclusions as a result of their analyses.
- In 2023, Information systems and telecommunications, Finance & Insurance, and Retail Trade are the sectors that targeted the most data breaches.
- It was determined that approximately 20 sectors were exposed to data breaches. This is important proof that cyber-attack surface expansion triggers the potential attack vectors for malicious activities.
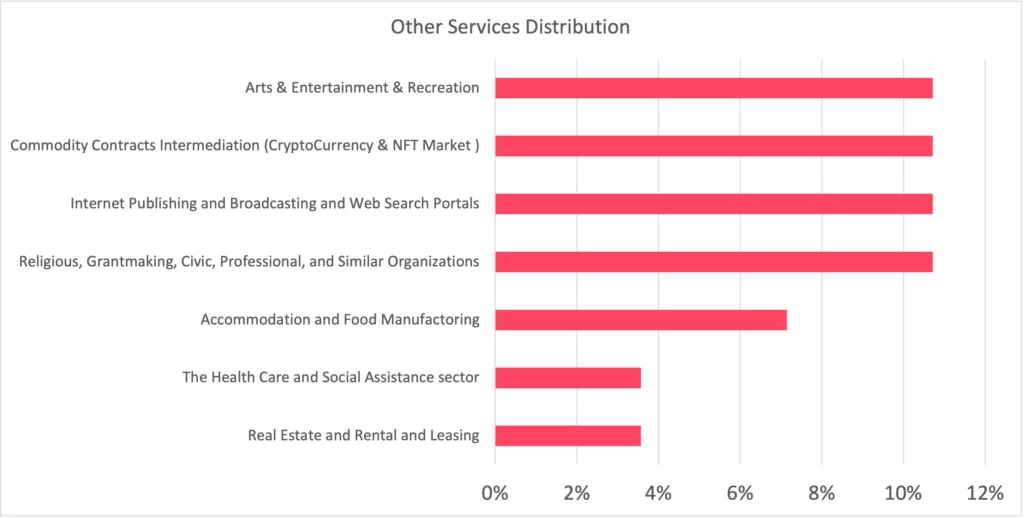
- The prominent sectors in the other category such as Arts & Entertainment & Recreation, Commodity Contracts, Intermediation (cryptocurrency & NFT Market), Internet Publishing and Broadcasting, and Web Search Portals.
- In the first half of 2023, 30 ransomware attacks and 14 different ransomware groups were observed targeting Australian organizations. The top ransomware actors that achieved their goals are AlphVM Blackcat, LockBit 3.0, and Cl0p, respectively.
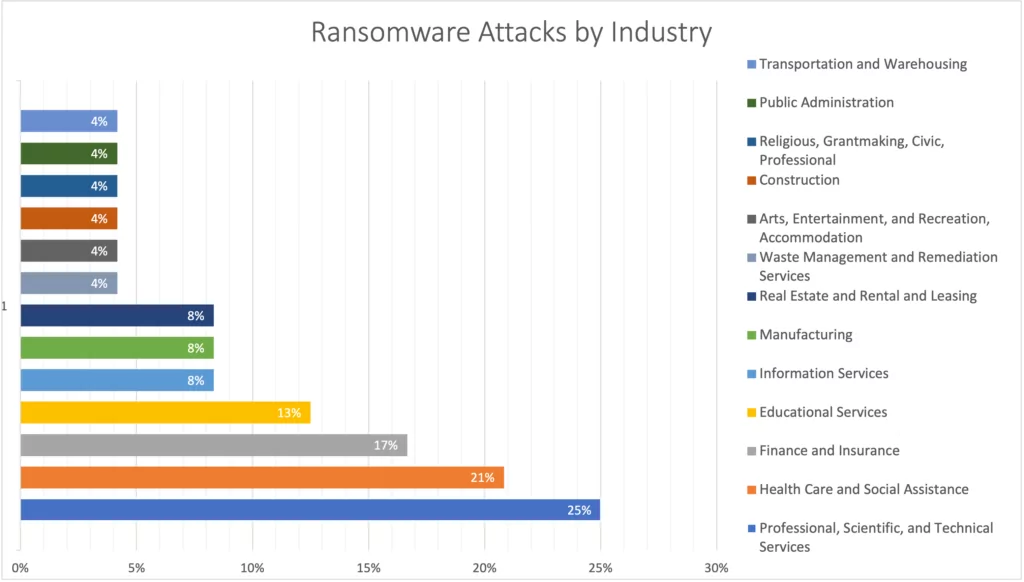
- For 2023, Professional, Scientific, and Technical Services, Health Care and Social Assistance Finance, and Insurance Educational Services are the leading sectors where they are targeted for successful ransomware attacks.
Spotlight on: Dark Web Threats Targeting Australian Organizations
The distribution of cyber incidents targeting Australia by sector is given below. It is clear that not only data breaches are expanding on a sectoral basis, but also the number of victims is increasing as well.
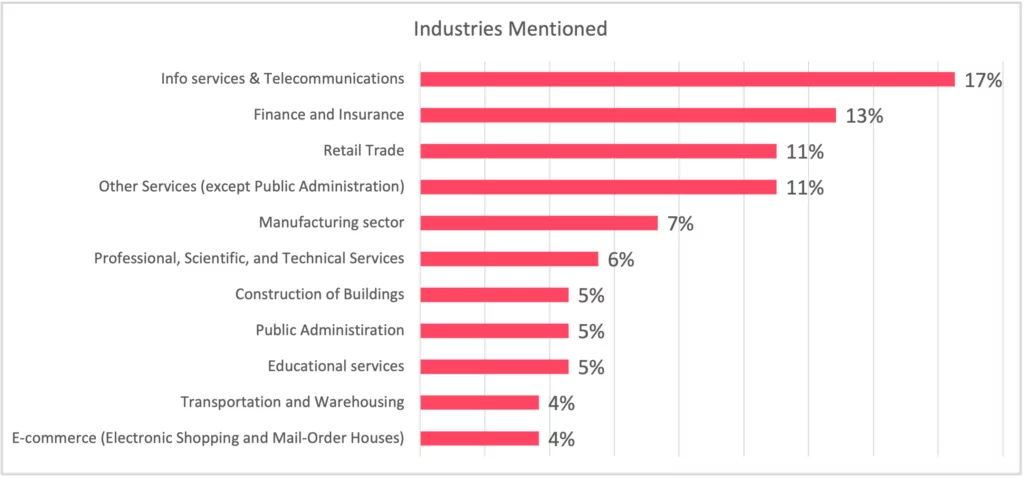
The breakdown of the sectors and sub-sectors in the “Other services” category is also shown below. It can be a lesson learned, as stated in the Verizon Data Breach Investigation Report, verified data breaches account for approximately 10 percent of the actual percentage, even if there are legal enforcements, so it is not possible to determine exactly which type of data of which institution is in the hands of threat actors without monitoring dark web forums and channels. Moreover, one of the critical conclusions of the Top 12 Takeaways from Verizon 2023 Report, humans are still a significant factor supporting data breaches.
Dark web intelligence refers to a stream of compiled and analyzed data gleaned from the dark web that has been proven to be one of the best solutions to proactively fight against cybercriminals and reduce data loss. It also protects you against future cyber-attacks by providing actionable intelligence on compromised accounts of your customers/employees before your organizations are targeted.
The hard fact to face is that over 50 percent of the leaked data contains customer and sensitive information. The second most common location where it is shared is the dark web (34%), specifically the Admin portal, RDP, and VPN access information used for initial access, which represents the most critical phase of a cyber attack. Consequently, the shared data is not limited to data breaches but also encompasses critical information that is sold for use in subsequent cyber attacks.
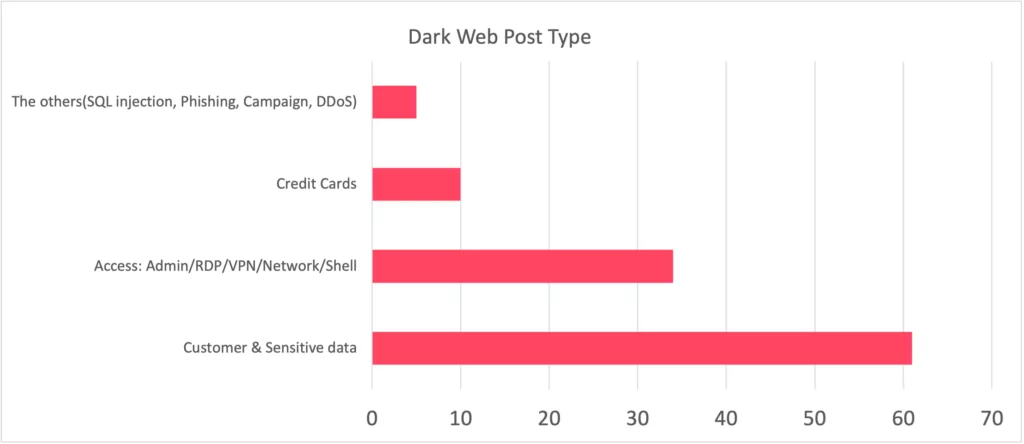
Recent Dark Web Activities Targeting Australian Entities
In the first half of 2023, some of the prominent dark web threats targeting Australian businesses are listed below in detected time sequence order.
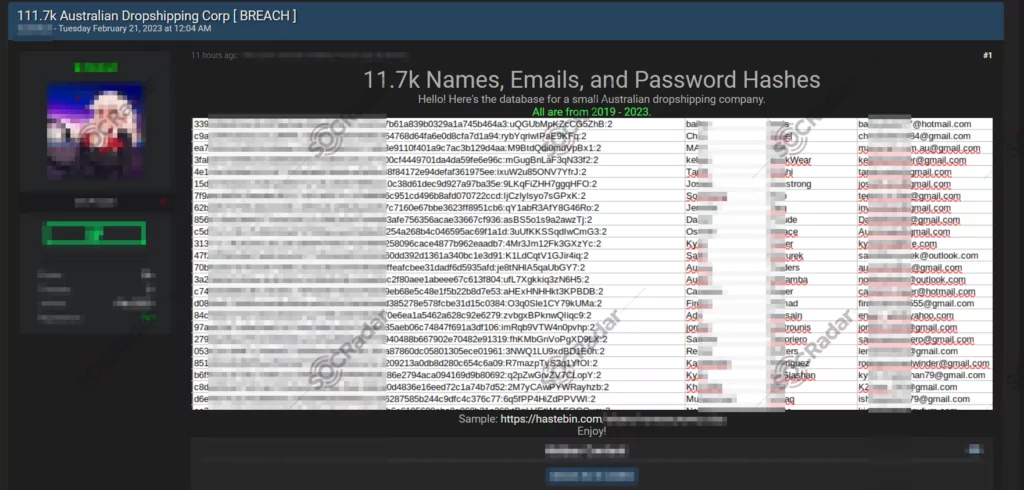
On February 21, 2023, a new alleged database leak for an Australian Dropshipping company was detected on a hacker forum monitored by SOCRadar. It contains 11.7K names, emails, and password hash information.
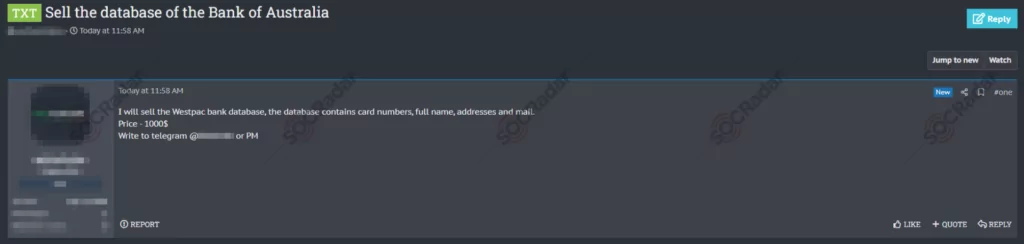
On April 14, 2023, on a hacker forum monitored by SOCRadar, a sale of a database allegedly belonging to an Australian-based multinational bank was detected. The bank database sale includes numbers, full names, addresses, and email details for $1000.
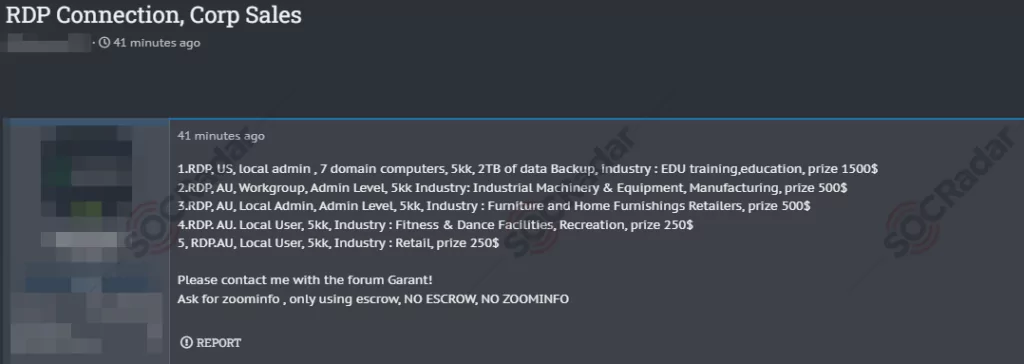
On May 24, 2023, a hacker forum monitored by SOCRadar identified unauthorized RDP access sales allegedly belonging to several companies operating in the United States and Australia. The targeted industries were identified as Industrial Machinery, Equipment, Manufacturing, Furniture and Home Furnishings, Retailers, Fitness, Dance Facilities, and Recreation.
Most initial access sales involve VPN or RDP credentials and occur through dark web forums and marketplaces. The most widely used and well-known of credential marketplaces, despite the seizure of Genesis by the FBI, is the Russian market, which continues to operate with 2easy. The majority of these access sales are obtained through stealer malware, which has remained relevant in recent years. Another popular method for acquiring these credentials is by exploiting security vulnerabilities in applications exposed to the internet.
According to current analyses by SOCRadar researchers, ransomware groups are one of the primary affiliates of initial access brokers. This method began to intertwine with the emergence of the RaaS model used by groups such as Lockbit 3.0.
On June 6, 2023, on a hacker forum followed by SOCRadar Dark web team, an unauthorized sale of administrator access allegedly belonging to an e-commerce company operating in Australia was detected. This access contains WordPress admin logins that were being sold via auction.
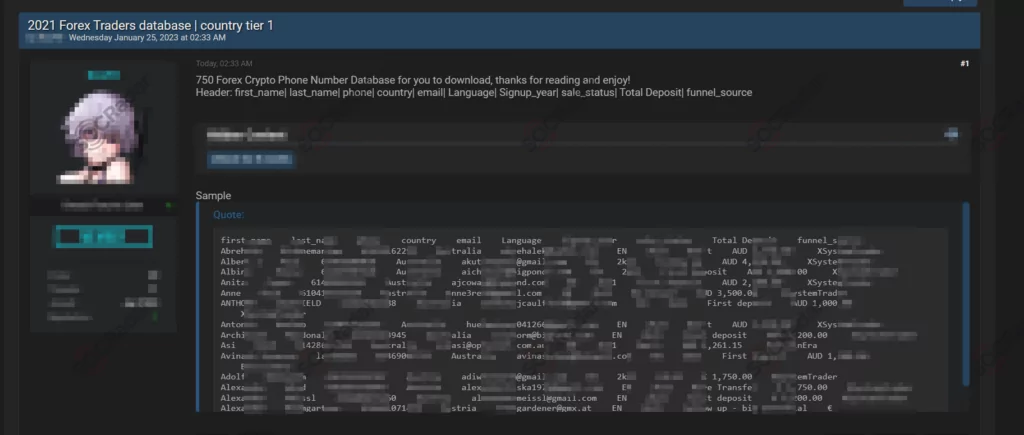
On June 25, 2023, a new alleged database leak for Australian Forex traders was detected on a hacker forum monitored by SOCRadar. This database contains 750 first names, last names, phone numbers, addresses, email, language, sign up year, sale status, total deposit, and funnel source.
Top Ransomware Groups Targeting Australian Entities
According to the 2023 DBIR report, Ransomware maintains its critical rank with 24% among cyberattacks. It is also an important cause of data breaches where the double extortion method in which threat actors threaten to publicly leak the victim’s sensitive data in addition to encrypting it, is adopted and continues to be a major threat and spread for organizations of all sizes and sectors. Furthermore, considering that most current cyber-attacks are designed by organized crime threat actors and that they contain a large proportion of Ransomware, we can infer that there is regrettably still an increasing trend, taking into account that the main motivation is money.
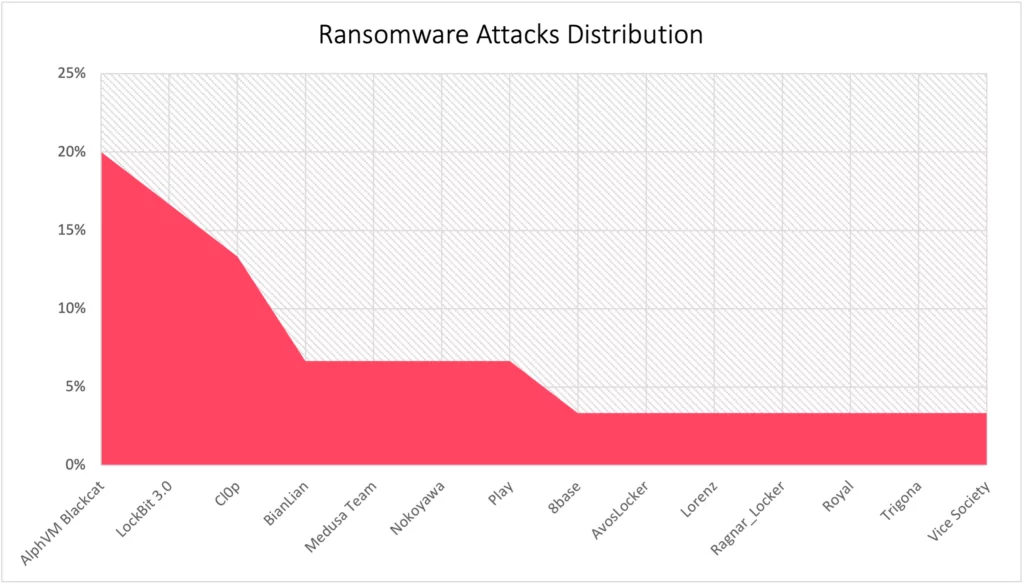
Up to July in 2023, SOCRadar Dark web analysts detected that there were 30 ransomware attacks and 14 different ransomware groups targeting Australian institutions. The distribution of ransomware attacks by actors is given below.
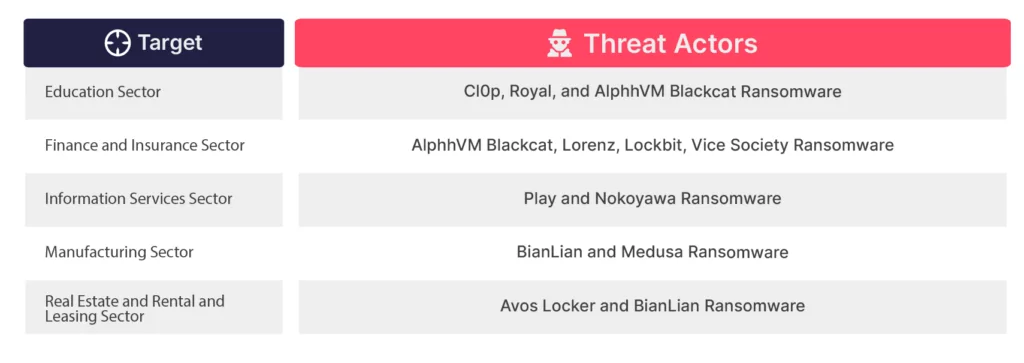
During the first half of 2023, the distribution of ransomware attacks across various Australian industries is as follows. After this useful intel, a critical relevant question arises: which ransomware groups are targeting specific sectors? In response to this, SOCRadar Research analysts have derived the following supplementary insights from a threat intelligence perspective pertaining to the Australian industry.
Some important cyber incidents targeting Australia are announced by ransomware groups that are constantly monitored and tracked by the SOCRadar dark web team.
On June 10, 2023, on the AlphVM/Blackcat ransomware group website, a new ransomware victim was allegedly announced as FIIG. FIIG is Australia’s leading fixed-income specialist. For over 24 years, they have been providing investors with direct access to bond markets and a range of term deposits, and other cash solutions. Leaked databases include 385 GB of data containing confidential and sensitive information such as projects, plans, documents, and other commercial confidential data.

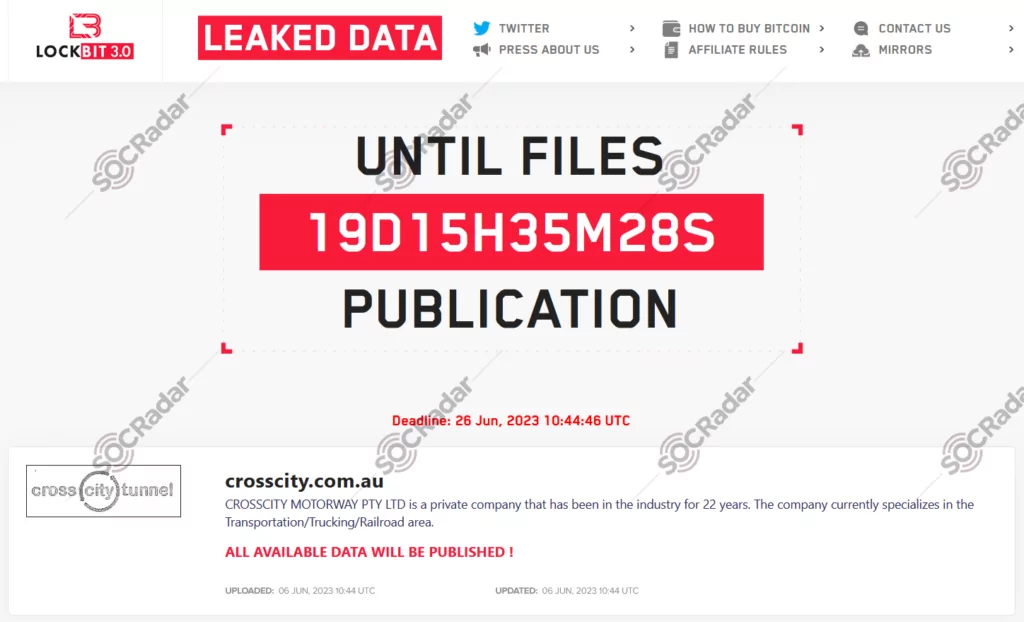
On June 6, 2023, a new ransomware victim on the Lockbit 3.0 ransomware group website, was allegedly advertised as Crosscity Motorway. CROSSCITY MOTORWAY PTY LTD is a private company that has been in the industry for 22 years. The company currently specializes in the Transport/Truck/Railway area in Australia.
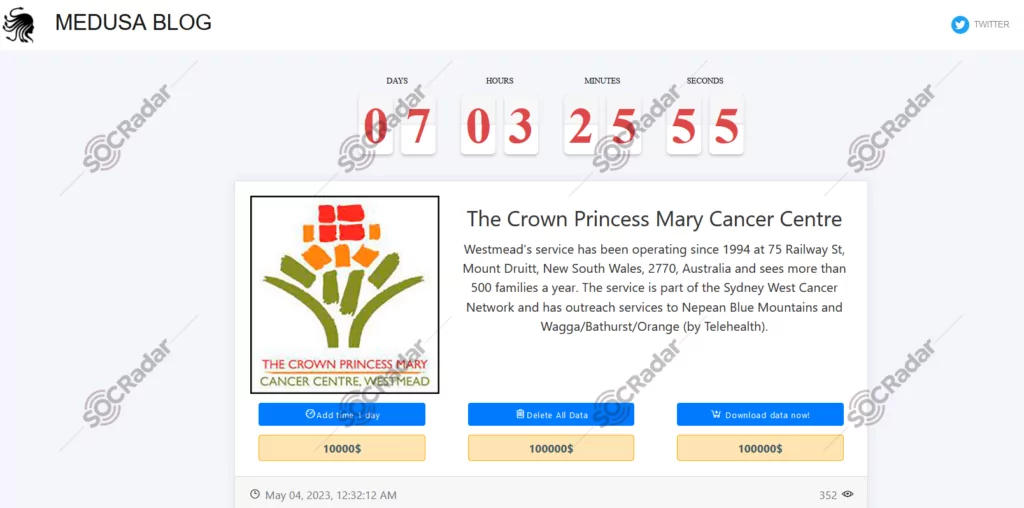
On May 4, 2023, on the Medusa Team ransomware group website, a new ransomware victim was claimed to be the Crown Princess Mary Cancer Centre. Crown Princess Mary Cancer Centre Westmead’s service has been operating since 1994 as part of the Sydney West Cancer Network.
Prominent Threat Actors targeting Australian Entities
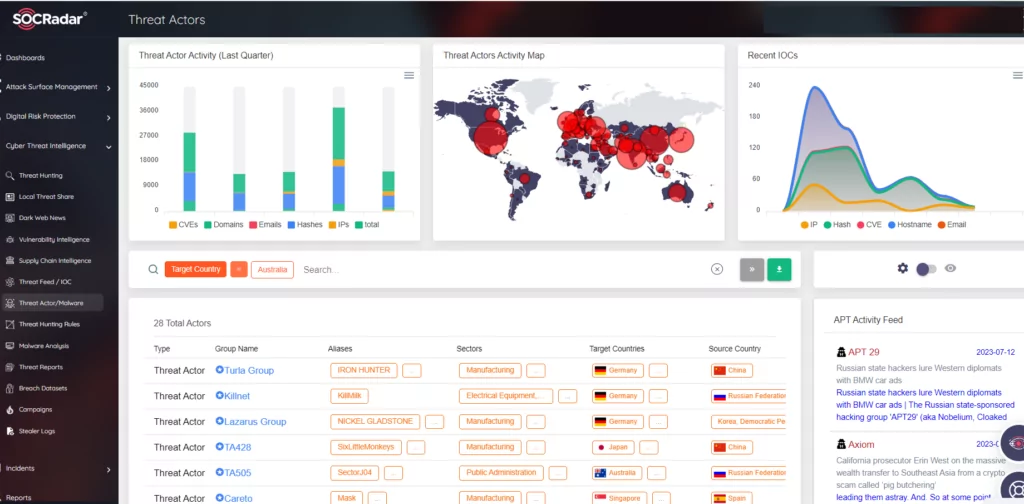
According to SOCRadar observations, Russian-based threat group Turla, the Lazarus APT group also known as Hidden Cobra, active since at least 2009 and widely believed to be North Korean state-sponsored, and TA505 cybercriminal group linked to Cl0p ransomware, and also Killnet and Anonymous Sudan as hacktivist groups, recently target countries including Australia.
Given the inference that threat actors specifically select their victims and could be sector-based concentrated, it is necessary to obtain contextual information extracted from dark web intelligence about the changing TTP and malware campaigns of cyber attackers for proactive measures via SOCRadar Threat Actors module.
Moreover, SOCRadar Campaigns page, which is enriched with dark web and surface (OSINT) intelligence information about recent campaigns, contains a series of attack activities that are active at certain periods of time, have been successful in their targets, and continue to spread.
Supply chain attacks are especially emerging threats that target organizations by infecting legitimate software to distribute malware, usually linked to third-party vendors‘ vulnerabilities. Therefore, SOCRadar Supply Chain Intelligence module can alert you to companies that are currently exposed to cyber-attacks, extract actionable intelligence information from manufacturers’ historical cyber incidents and data breaches, and provide you with a report enriched with threat intelligence insights.
Conclusion and Recommendations
SOCRadar research findings suggest that Australia faces challenges in keeping up with the ever-changing and evolving threat landscape, although it is one of the countries that have made the most progress in creating a cyber defense environment. There are many reasons, such as the difficulty of managing growing attack surfaces and the lack of actionable and reliable intelligence on the weapons (TTPs) used by cyber attackers.
In addition, international tensions arising from instability, such as the Russia-Ukraine war, can also result in threat actors joining forces with their backroom handlers to create pretexts. A typical example of this is the case of Killnet and Anonymous Sudan, where Australia is one of the main targets. It is also essential to take measures to build strong cyber resilience strategies against such uncontrollable situations.
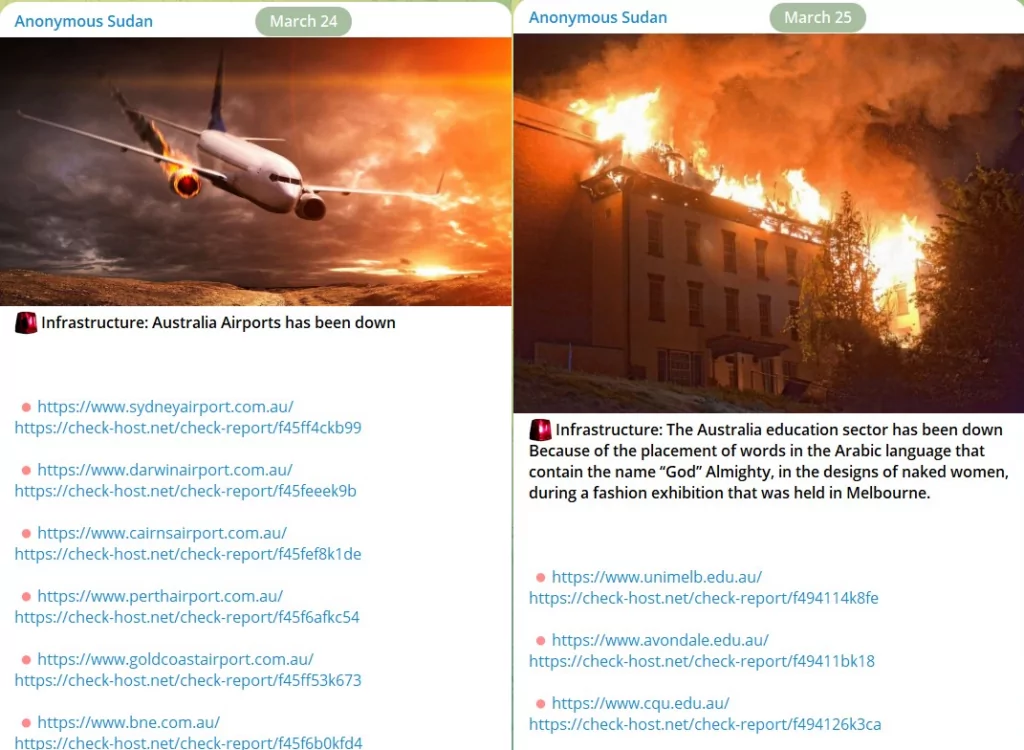
Compared to the first half of 2022, there is a notable increase in threat actors targeting Australia, especially ransomware groups. This environment has naturally led to an increase in cyber incidents. This grave situation does not mean that the government’s struggles are invalid but reminds us that we need to act more cautiously against unseen enemies in cooperation with other countries by utilizing the power of cyber threat intelligence.
Organizations often learn that their data has been stolen or hacked long after they have been exposed to a cyber-attack such as ransomware. As a result, they need a SOC infrastructure powered by CTI feeds that can help proactive and predictive defense against rising and sophisticated cyber threats.
It is critical to ensure the boundaries of your attack surface and combine them with effective vulnerability management processes. SOCRadar EASM (External Attack Surface Management) Module discovers your digital assets, assesses your cyber security risk, and mitigates them. This service can provide a unified view of your cyber assets to get full visibility of your expanding attack surface and help you identify potential vulnerabilities.