
Using OSINT to Strengthen Organizational Security
Open-source intelligence or “OSINT” is collecting and analyzing data gathered from publicly available open sources (social media, news, dark web, etc.) to produce actionable intelligence crucial to organizational security.
A wide range of individuals and organizations now uses open-source intelligence. Academics use OSINT for research; militaries use OSINT for strategic planning and organization of combat operations; and Threat Intelligence professionals use OSINT to provide a wealth of information that can be used to identify potential threats, monitor threat actors, and develop actionable intelligence.
What is OSINT?
Open-Source Intelligence is one of the most dominant sub-types of Threat Intelligence. Threat intelligence refers to collecting, analyzing, and disseminating information about potential or actual threats to an organization’s information assets. Organizations often use Threat intelligence to identify and mitigate cybersecurity threats, including malware, phishing attacks, and other types of cyberattacks.
OSINT and Threat Intelligence are complementary approaches that can be used together to improve an organization’s cybersecurity posture. OSINT can provide valuable information on potential threats, while Threat Intelligence can provide a more comprehensive view of the threat landscape, including non-publicly available information.
By combining OSINT and Threat Intelligence, organizations can gain a complete picture of the threat landscape and make more informed decisions.
Information you can refer to as open-source data includes:
- Social media information
- News / Press Releases
- Public meetings
- Public reports
- Metadata search
- Forum discussions
- Search engine resultsfinds
- Public code repositories
- Data leaks
- Paste sites
There are many different use cases for OSINT:
- Threat intelligence: OSINT can be used to gather information on potential cyber threats, such as malware, phishing attacks, and data breaches. For example, OSINT tools can help identify phishing domains by monitoring newly registered domains, analyzing their SSL/TLS certificates over certificate transparency logs, and checking for similarities with legitimate domains. OSINT can be used to analyze the behavior of malware by looking for information about its code, network connections, and known command-and-control servers. This information can help security teams to identify emerging threats and take preventive measures to protect against them.
- Competitive intelligence: OSINT can gather information on competitors, including their market position, product offerings, and marketing strategies. This information can help organizations stay ahead of the competition and make more informed business decisions.
- Brand monitoring: OSINT can monitor mentions of an organization’s brand or products on social media, news sites, and other online platforms. This information can help organizations identify potential issues and respond quickly to negative publicity.
- Law enforcement: OSINT can be used by law enforcement agencies to gather information on criminal activities, including human trafficking, drug trafficking, and terrorism. This information can help to identify suspects, disrupt criminal networks, and prevent future crimes.
Two-way Roller Coaster: OSINT
Open-source information is available to everyone so that OSINT can be used on both sides. While organizations are using OSINT to keep tabs on threat actors, threat actors are also using OSINT to keep tabs on organizations.
Threat actors often gather victims’ personal information and perform phishing attacks to damage organizations.
Another technique threat actors use is Google hacking, also named Google dorking. For the average person, Google is just a search engine used to find the usual things on the internet. However, Google is one of the most useful hacking tools ever. Google hacking is using Google to find vulnerable web applications, public code repositories, servers, and much more by using Google search engine capabilities.
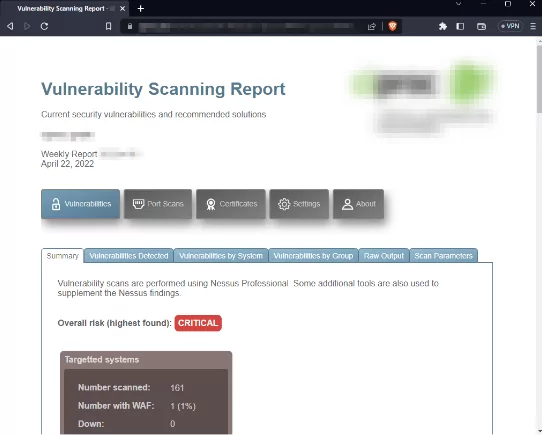
For example, a simple Google dork (intitle:”report” (“qualys” | “acunetix” | “nessus” | “netsparker” | “nmap”) filetype:html intext:”3389″) will find reports of vulnerability tools like Nmap, Nessus, Netsparker etc. which can be analyzed and exploited by threat actors easily.
Using OSINT to Strengthen Organizational Security
OSINT can be a valuable tool to strengthen organizational security by providing insights into potential threats and vulnerabilities.
8 steps to follow to use OSINT to strengthen organizational security:
– Identify your assets
The first step is identifying the assets you must protect, such as sensitive data, intellectual property, and critical infrastructure. This will help you focus your OSINT efforts on areas that are most vulnerable to attacks.
– Use OSINT tools
There are many OSINT tools available that can help you monitor your organization’s digital footprint and detect potential threats.
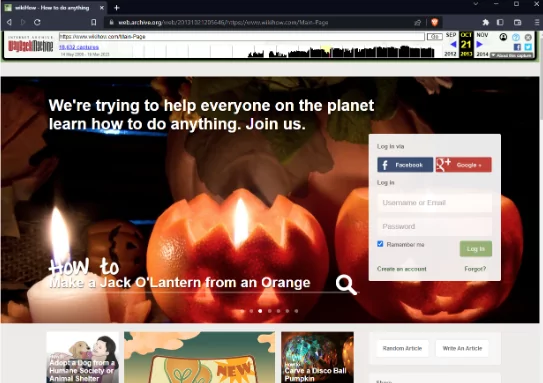
- The Wayback Machine
The Wayback Machine is a time machine that allows you to access archived versions of websites, including websites that may no longer be available online. It can retrieve information from websites that have been deleted, altered, or taken down. Even if the websites containing any information about their old versions have been updated over time and made suitable for today’s security understanding, the old versions, which are still viewable through The Wayback Machine, can lead to significant vulnerabilities.
For instance, if a website’s content or data was not adequately secured when originally published, the Wayback Machine might still have a snapshot of that information. This can expose sensitive information, such as personal or login credentials. Attackers could potentially analyze those snapshots if the archived website version contains known vulnerabilities. To put it more clearly, they can analyze the code, configurations, and interactions in those snapshots to gain insights into potential weaknesses. Armed with knowledge about the vulnerability and its exploitation, attackers can attempt to replicate the same attack on the current website version.
- Shodan
Shodan is a popular search engine for internet-connected devices and is often used in OSINT investigations. Unlike other search engines focusing on websites, Shodan allows users to search for and identify devices such as servers, routers, and webcams connected to the internet. The image below shows an office webcam, forgotten open on the public internet.
One of the features of Shodan is identifying vulnerable devices provides information on devices operating on protocols like HTTP, SSH, FTP, Telnet, and IMAP, IP Lookups.
- HaveIbeenPwned
HaveIBeenPwned is a big data breach notebook that allows you to check if your email address or username has been involved in a data breach. It is used to identify potential security risks and data breaches.
- Metagoofil
Metagoofil is a tool for extracting metadata from publicly available files, such as PDFs, Word documents, and images. It can gather information from extracted documents about a target’s network infrastructure, such as server names, IP addresses, and email addresses.
-Monitor the internet
Use OSINT tools to monitor the internet for mentions of your organization, employees, and assets. This can help you detect threats like phishing attacks, social engineering attempts, or data breaches.
-Analyze social media
Social media platforms can provide valuable insights into potential threats and vulnerabilities. You can use OSINT tools to analyze social media activity related to your organization, including posts, comments, and mentions.
For instance, The Wells Fargo unauthorized accounts scandal, also known as the Wells Fargo fake accounts scandal, emerged in 2016 when it was revealed that employees had opened millions of unauthorized bank and credit card accounts in customers’ names without their knowledge or consent. Aggressive sales goals and incentive systems within the bank drove this fraudulent activity.
A whistleblower uncovered the scandal and subsequent investigations, resulting in hundreds of millions of dollars in fines and settlements paid by Wells Fargo to regulators. The bank also faced lawsuits from affected customers and investors. The scandal highlighted the need for stronger oversight and ethical practices in the banking industry, resulting in leadership changes, reforms, and discussions about consumer protection.
-Conduct a threat assessment
You can use OSINT to assess and identify potential threats to your organization. This could include cybercriminals, hacktivists, or insider threats. Begin by defining the scope and specific threats you want to assess. Identify reliable OSINT sources, such as online platforms, news outlets, and social media. Gather relevant information from these sources, including public records and social media posts. Analyze the information for patterns, suspicious behavior, and vulnerabilities.
Verify accuracy by cross-referencing multiple sources and assessing the credibility of each source. Organize findings into categories or themes. Evaluate each threat’s potential impact and likelihood and prioritize based on risk. Create a concise threat assessment report summarizing the identified threats and recommended actions. Examples include assessing online threats to a high-profile individual by gathering information from social media, forums, and news articles or assessing cybersecurity risks to an organization by analyzing public records, data breaches, and hacker forums.
-Assess vulnerabilities
OSINT helps you to assess your organization’s vulnerabilities, such as weak passwords, unsecured networks, or outdated software. This can help you identify areas that need improvement and take corrective actions.
-Stay informed
Stay up to date with the latest security news and trends to stay ahead of potential threats. Subscribe to security blogs, follow security experts on social media, and attend security conferences to stay informed.
-Take action
Use the insights from OSINT to take preventive measures and improve your organizational security posture. This could include implementing security policies and procedures, upgrading your software and hardware, or providing employee training on security practices.
In conclusion, OSINT can provide organizations with valuable insights and intelligence that can be used to make more informed decisions, reduce risks, and gain a competitive advantage. By harnessing the power of OSINT, organizations can stay ahead of the curve and respond quickly and effectively to a rapidly changing information landscape.
OSINT is an essential tool for threat intelligence professionals, as it helps to develop actionable intelligence. SOCRadar offers a three-in-one solution to strengthen your cybersecurity posture. Extended Threat Intelligence platform that combines External Attack Surface Management, Digital Risk Protection Services, and Cyber Threat Intelligence.



































