
Using Threat Intelligence to Monitor Industry-Specific Threats
Threat intelligence (TI) is essential to today’s cybersecurity practice because it enables organizations to gain insight into the motivations and methods of current and potential cyber threats, including industry-specific threats.
Threat intelligence increases early threat detection and prevention capabilities. Organizations can leverage timely and relevant TI to identify potential threats before they occur. As a result, they can take proactive measures to prevent attacks and protect their critical assets.
Organizations can use qualified threat intelligence to improve their situational awareness of the threat landscape. Hence, they can keep up with the latest threats and vulnerabilities, thus adjusting their security posture accordingly.
Shared threat intelligence creates a collaborative environment and increases the overall cyber resilience of the community. Organizations can learn from each other and improve their ability to detect, prevent and respond to emerging incidents.
The threat landscape is evolving rapidly, and new cyber risks are emerging daily. Therefore, those risks should be prioritized to keep pace. Organizations can better manage risks by using threat intelligence. They can make efficient decisions about applying countermeasures to specific significant threats obtained from quality threat intelligence.
What Type of Threat Intelligence Do We Need?
Peter Drucker said, “Efficiency is doing things right; effectiveness is doing the right things.” This maxim is just as applicable to cybersecurity and cyber threat intelligence.
To utilize cyber threat intelligence effectively, we should identify what intelligence should be collected, analyzed, and consumed. This process is also called identifying threat intelligence requirements.
According to SANS, while defining high-level threat intelligence requirements, we should identify the following;
- the countries of operation
- the business industries of operation
- the business’s top critical assets
- the types of adversaries targeting your business
- and the consumers of the collected/produced intelligence.
Besides identifying TI requirements, we should consider the data quality because security operation teams can’t take action with the vast amounts of threat data practically. They need actionable -accurate, timely, and relevant- threat intelligence against the latest threats.
As a result, after identifying the business industry, we should ask how we can monitor industry-specific threats via actionable cyber threat intelligence.
How to Monitor Industry-Specific Threats?
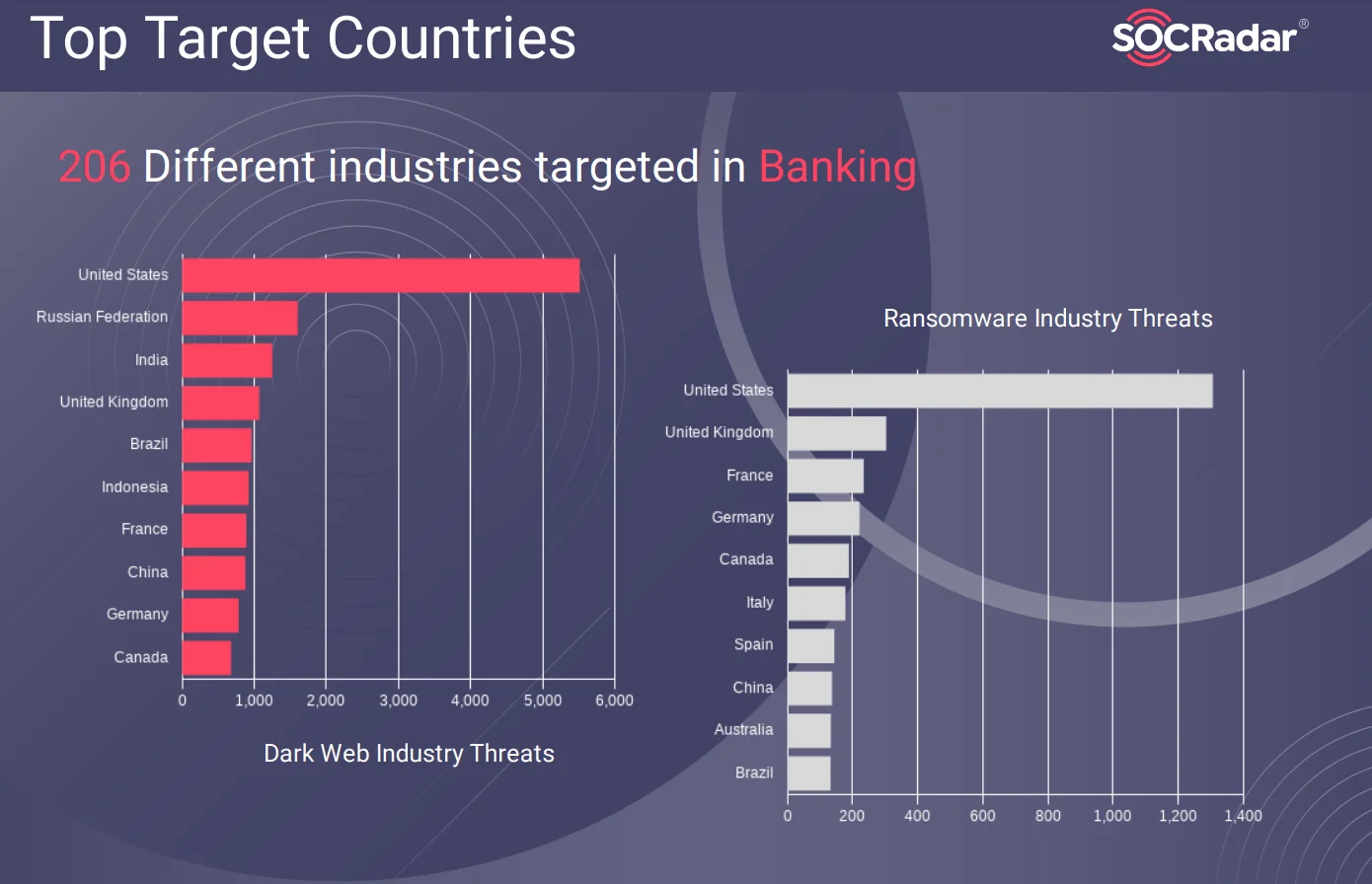
In this blog, we focus on two industries to give solid examples: financial and healthcare. According to the SOCRadar End of Year Report, the finance and healthcare industries are among the most targeted.
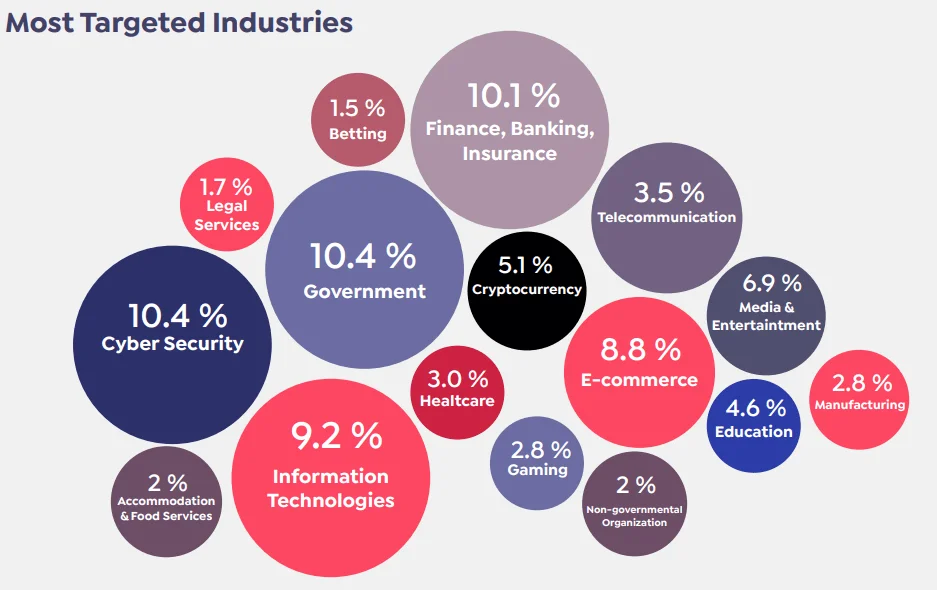
SOCRadar End of Year Report 2022 – Most Targeted Industries
There are several actions that we should carry out while monitoring industry-specific threats.
First, we should identify our attack surface, assess the risks, and identify the most critical assets. What might happen when the bad guys get their hands on a particular asset? What would be the impact of a successful attack on that asset? We should conduct risk prioritization after those assessments. Risk prioritization shows us the most critical assets, vulnerabilities, and threats to monitor.
After identifying what should be monitored, we should keep pace with the emerging industry-specific threats and vulnerabilities via subscribing to relevant cybersecurity blogs, RSS feeds, and newsletters. Dark Reading, The CyberWire, KrebsOnSecurity, and SANS NewsBites are examples of cybersecurity news sources.
Additionally, we should leverage threat intelligence tools to proactively prevent, detect, and respond to cyber threats specific to a particular industry. These tools can provide early warnings, alerts, and recommendations about the latest threats.
SOCRadar cannot detect organizations’ internal assets unless they are exposed publicly. However, you can monitor significant vulnerabilities that affect your critical internal assets by subscribing to the Vulnerability Intelligence page within the Cyber Threat Intelligence module. You get an email notification if a new vulnerability emerges about the subscribed product.
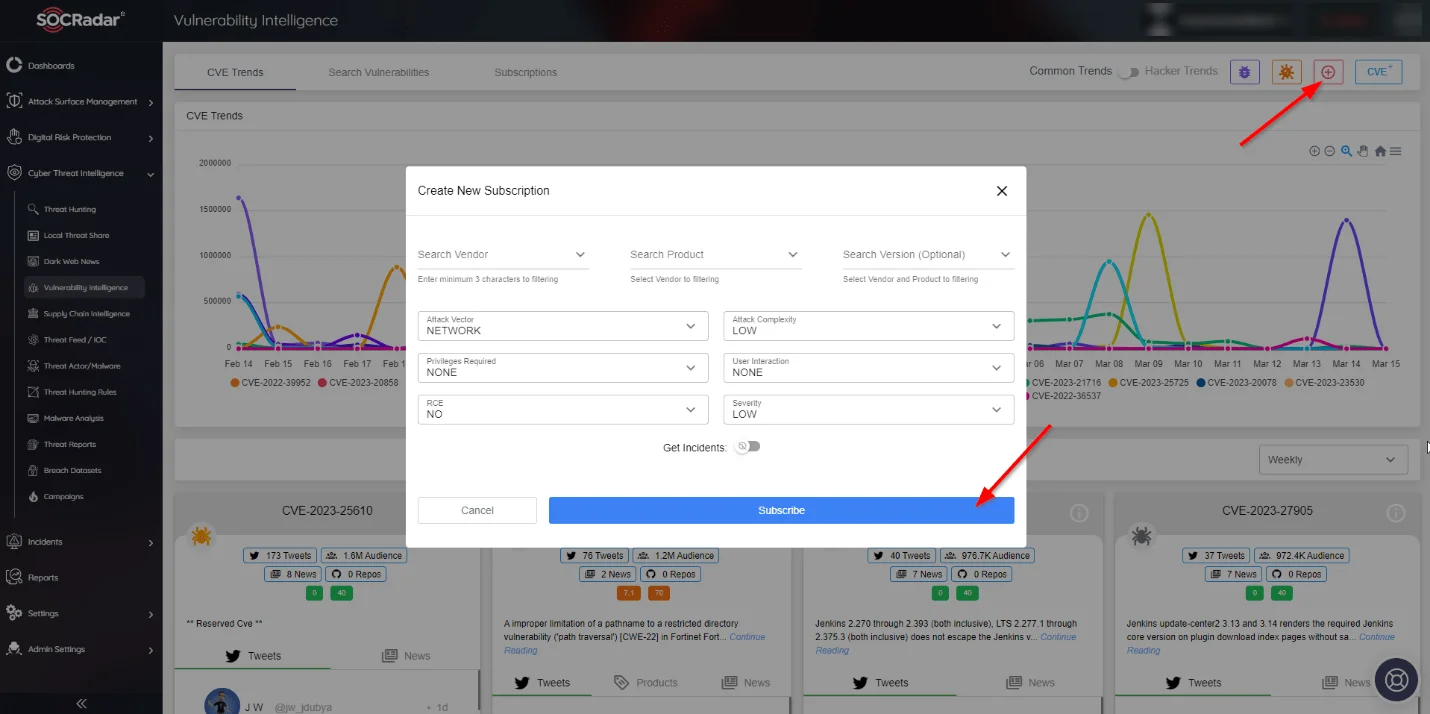
Vulnerability Intelligence page subscription option
SOCRadar is an excellent example of a comprehensive threat intelligence tool that you can consider. We will dive deep into its capabilities in the following section.
Lastly, the industry improves its overall security posture via collaboration. Sharing industry-specific threat intelligence is essential while confronting targeted attacks. Specific ISACs (Information Sharing and Analysis Centers) exist for every critical sector. Regarding the healthcare and financial industry, Health-ISAC (Health Information Sharing and Analysis Center) and FS-ISAC (Financial Services Information Sharing and Analysis Center) provide valuable services so stakeholders can share TI and collaborate against recent industry-targeted threats.
How Can SOCRadar Be Used to Monitor Industry-Specific Threats?
SOCRadar XTI platform has many practical features to assist organizations in monitoring industry-specific threats.
The SOCRadar Reports page allows you to obtain an industry-specific report on a tactical level. You can also subscribe to this report.
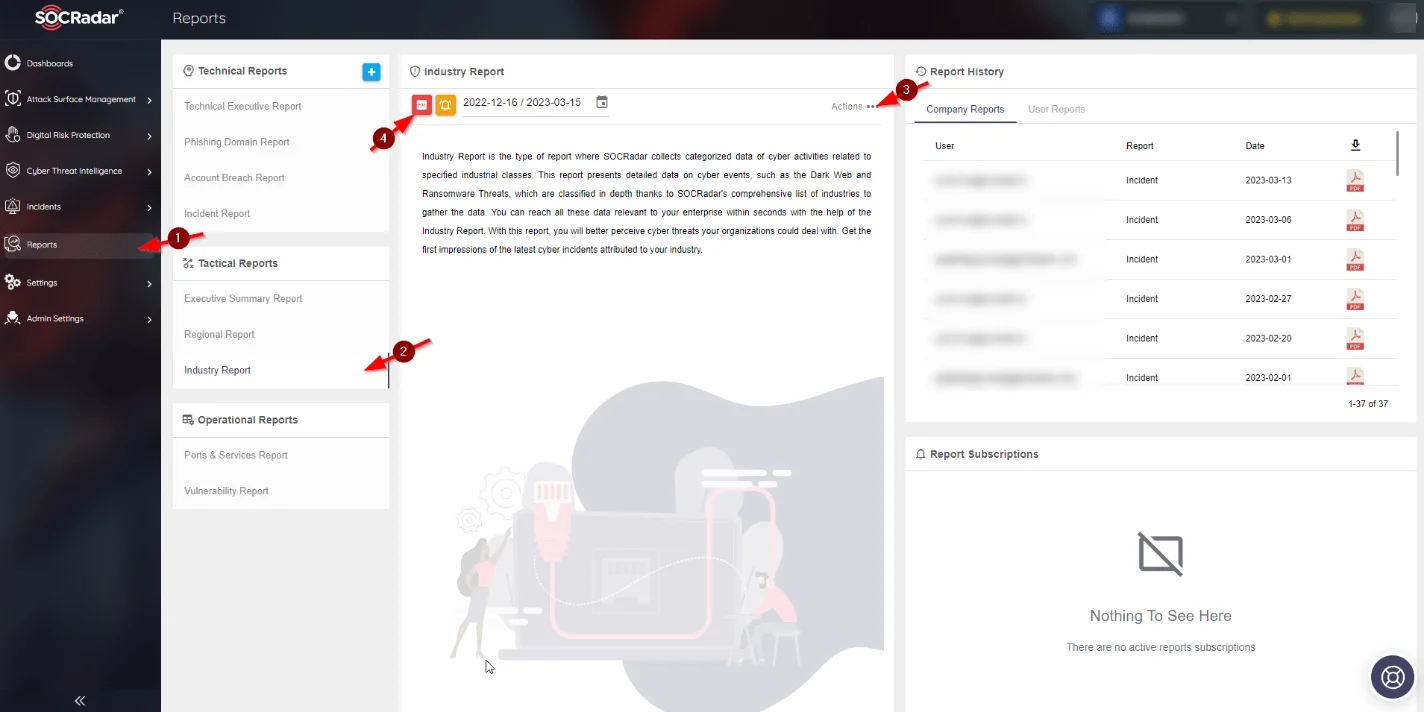
SOCRadar Reports page – industry report generation/subscription
Financial industry report sample
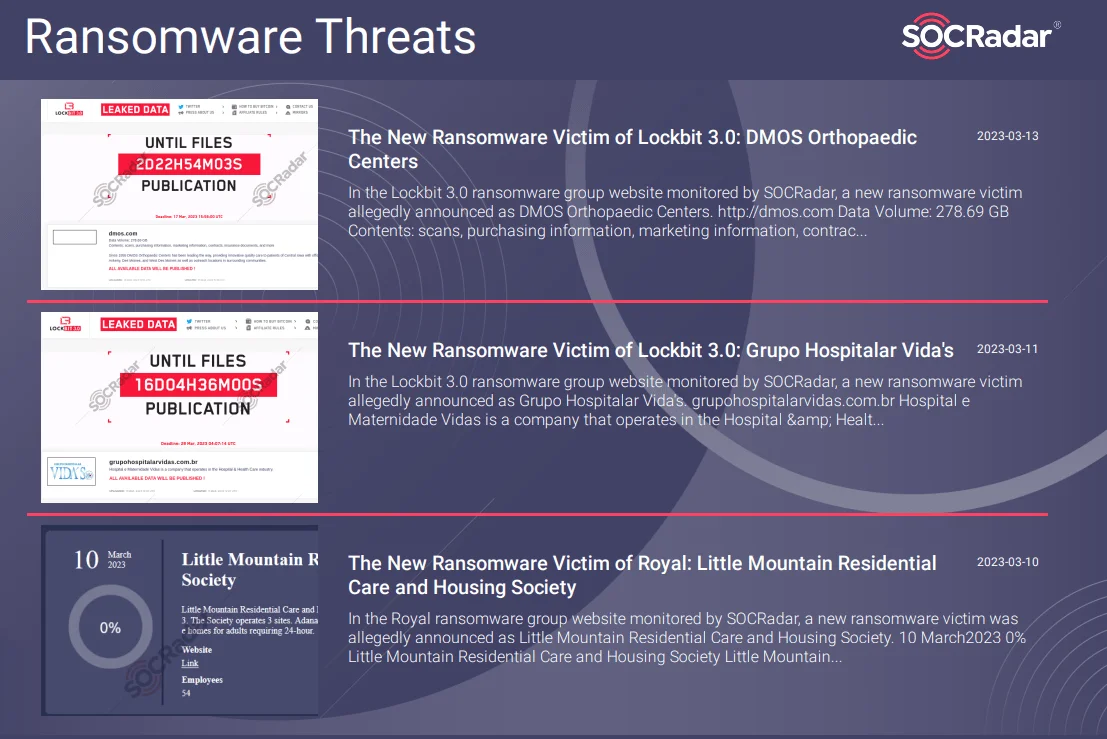
Healthcare industry report sample
The SOCRadar Dark Web News page also has a subscription option to help you monitor Dark Web threats. You can subscribe to it from the Subscriptions page.
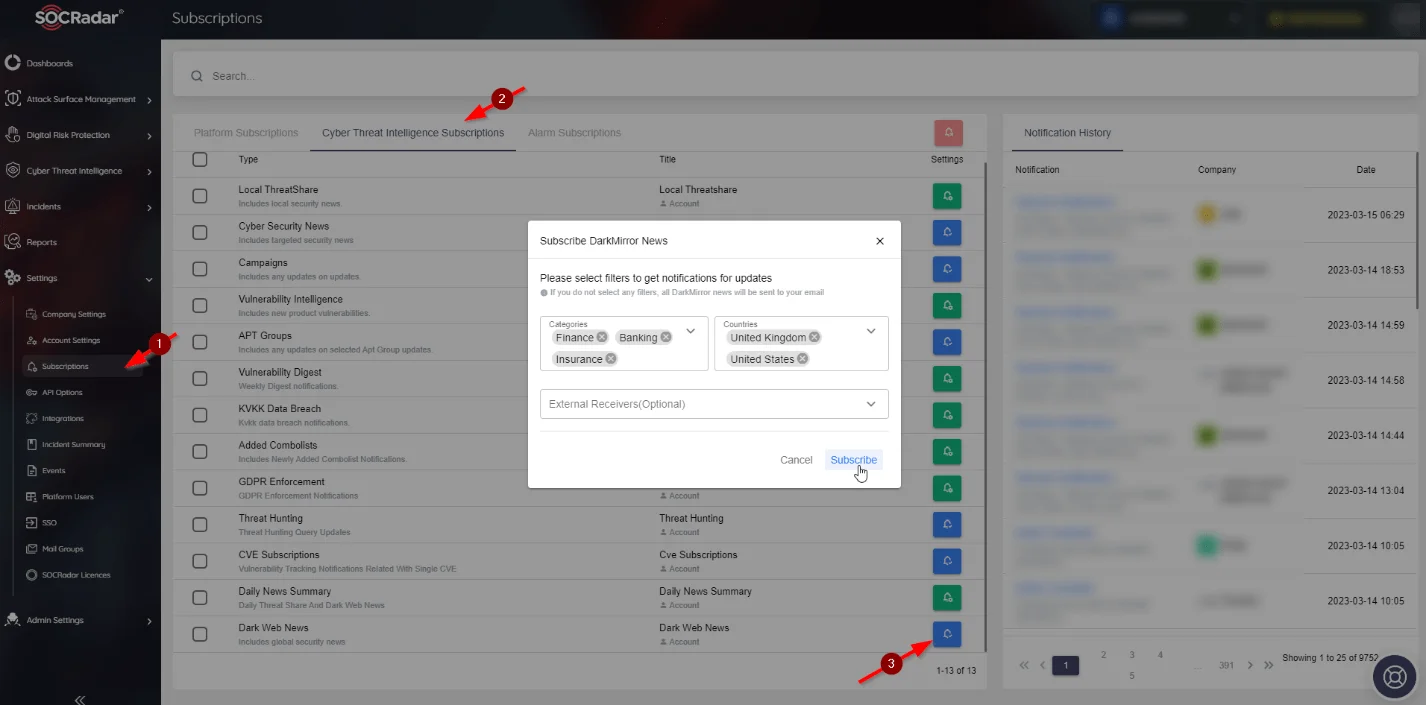
SOCRadar Dark Web News page – subscription
Besides the SOCRadar Extended Threat Intelligence platform, there are some free tools that you do not need to log in to. These free tools are provided on the SOCRadar Labs. DarkMirror, a free Dark Web news tool, has a subscription feature that you can filter by industry and country. It is a free version of the Dark Web News feature of the SOCRadar platform.
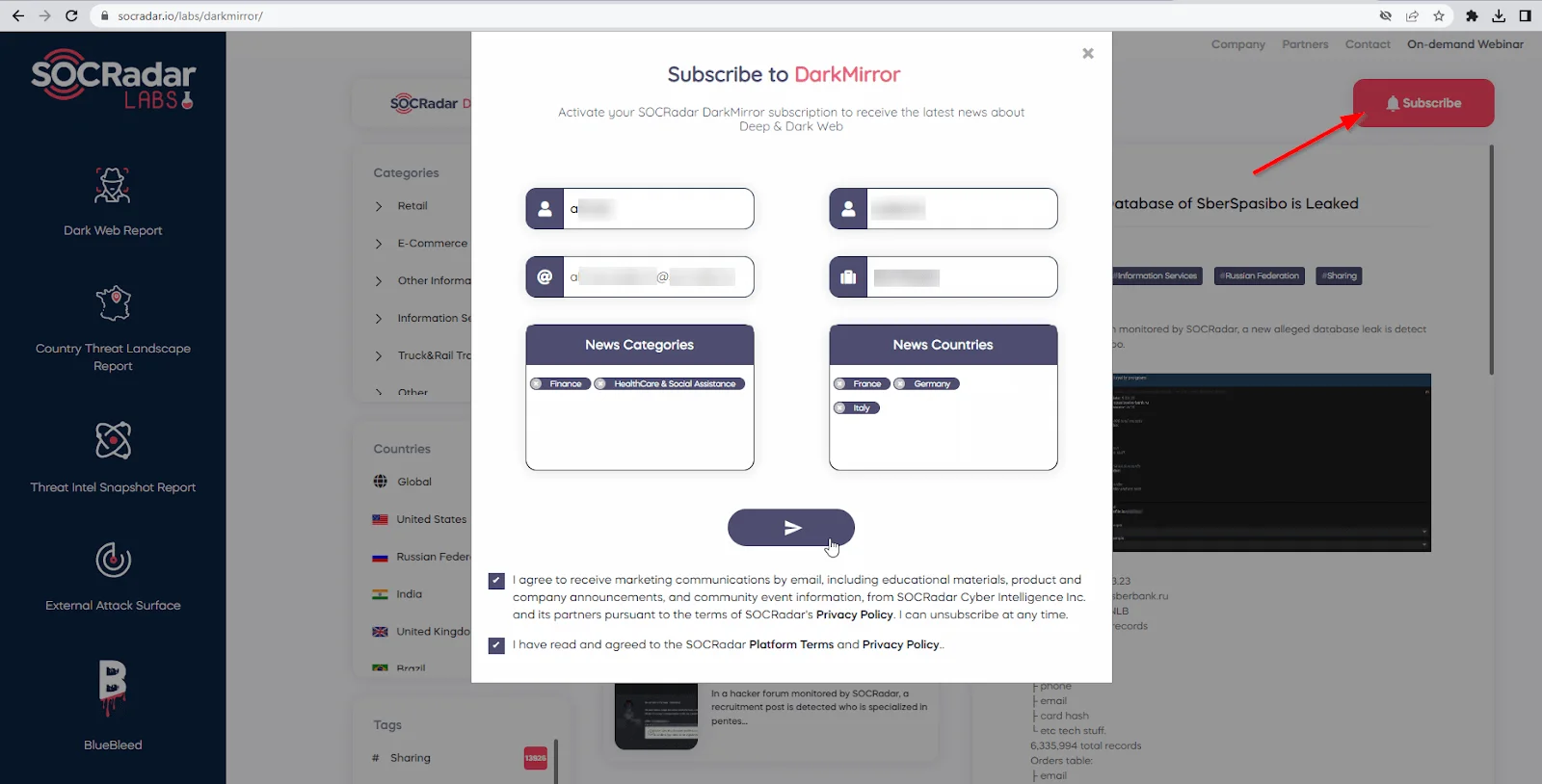
Dark Mirror subscription
As seen, we can prioritize risk and increase our preparedness against targeted cyber threats by subscribing to different levels of industry-based threat intelligence reports and news feeds on the tools within the SOCRadar XTI platform or SOCRadar Labs.




































