
Verizon Data Breach, European Credit Cards, and APEC & APERC Databases Allegedly for Sale
Recent reports from the SOCRadar Dark Web Team have uncovered a series of significant cyber threats. Among the most concerning is the alleged data breach of Verizon’s Push-to-Talk (PTT) service. Additionally, databases from the Asia-Pacific Economic Cooperation (APEC) and the Asia Pacific Energy Research Centre (APERC) are allegedly up for sale. Other threats include the sale of a critical exploit for CVE-2024-38077, a DDoS attack on Belgium’s Cybersecurity Center by NoName057(16), and the auctioning of over a thousand European credit cards.
Receive a Free Dark Web Report for Your Organization:
Alleged Data of Verizon Are on Sale
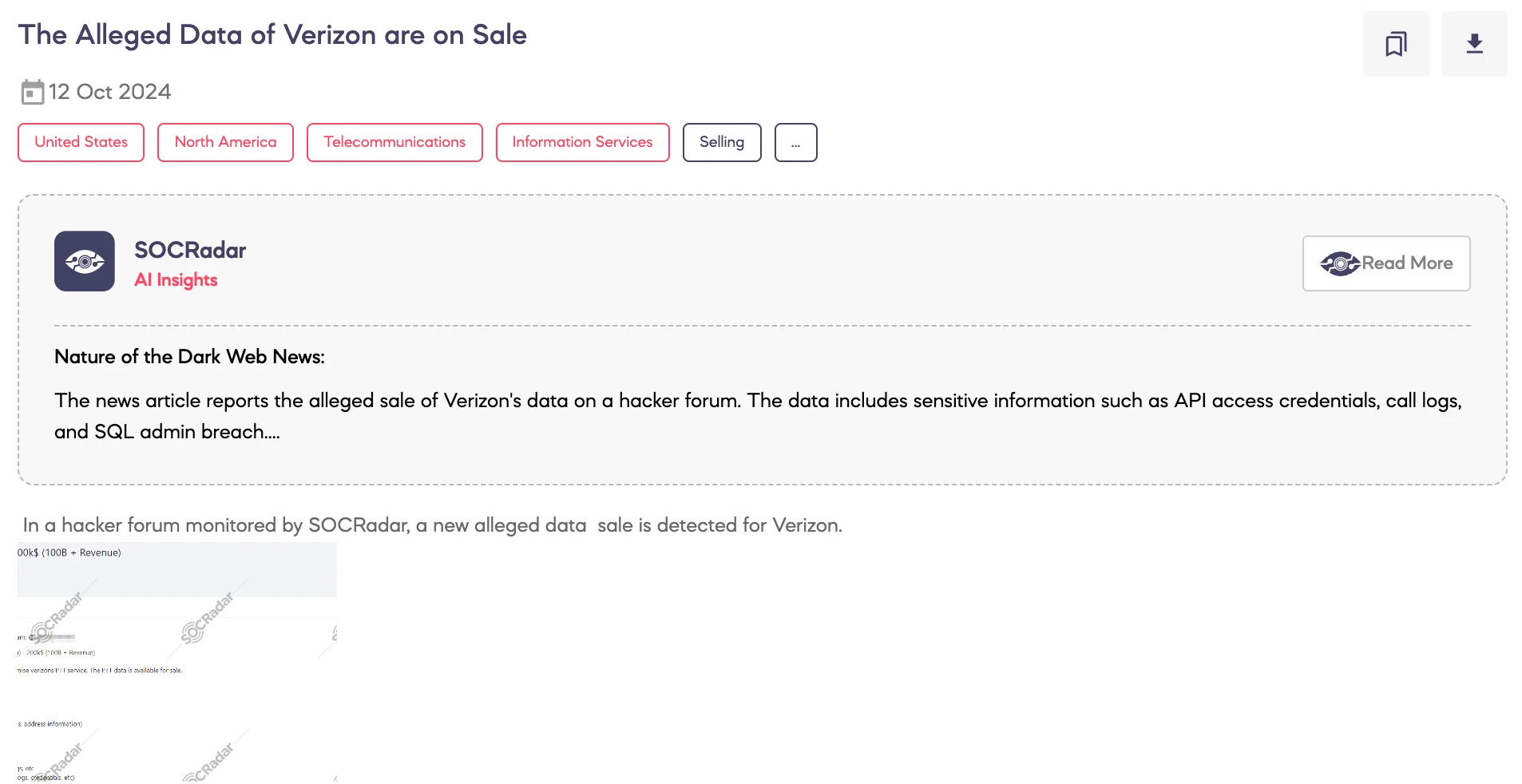
SOCRadar Dark Web Team detected that a threat actor has claimed to have breached Verizon’s Push-to-Talk (PTT) service and is offering the allegedly stolen data for sale on a hacker forum.
The threat actor is advertising the sale of 328GB of data for a price of $200,000. They claim to have fully compromised Verizon’s PTT service, which allegedly includes API access credentials, multiple F5 credentials, PTT call logs (containing phone numbers, emails, and address information), IMSI numbers, SIM keys and numbers, server logs, over 400 local host machine names, full SQL admin access (including logs and credentials), and former SSH access with IPs and credentials. The actor also mentioned the ability to clone the PTT SIM network.
Alleged Database of APEC and APERC is on Sale
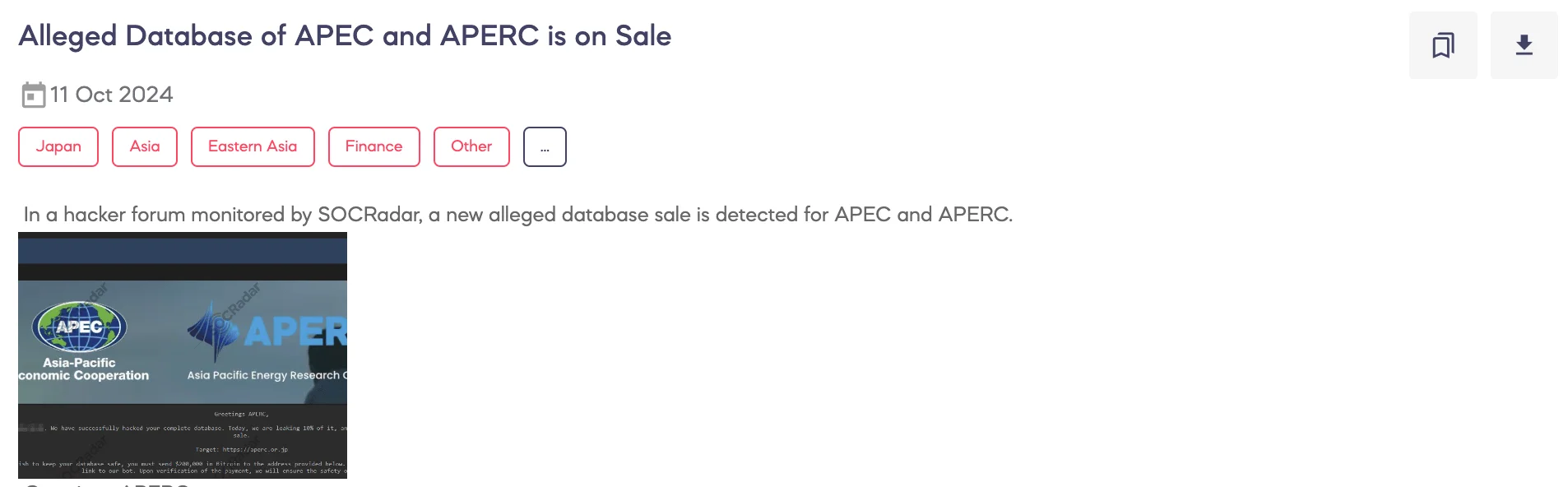
SOCRadar Dark Web Team detected that a threat actor has claimed to have compromised the databases of the Asia-Pacific Economic Cooperation (APEC) and the Asia Pacific Energy Research Centre (APERC) and is offering them for sale on a hacker forum.
According to the threat actor, they have successfully breached APERC’s entire database, and they are currently leaking 10% of the data as a sample. The remaining database is being offered for sale. The actor has targeted the website aperc[.]or[.]jp and is demanding a ransom of $200,000 in Bitcoin to prevent further leakage of the database.
Alleged CVE-2024-38077 Exploit is on Sale
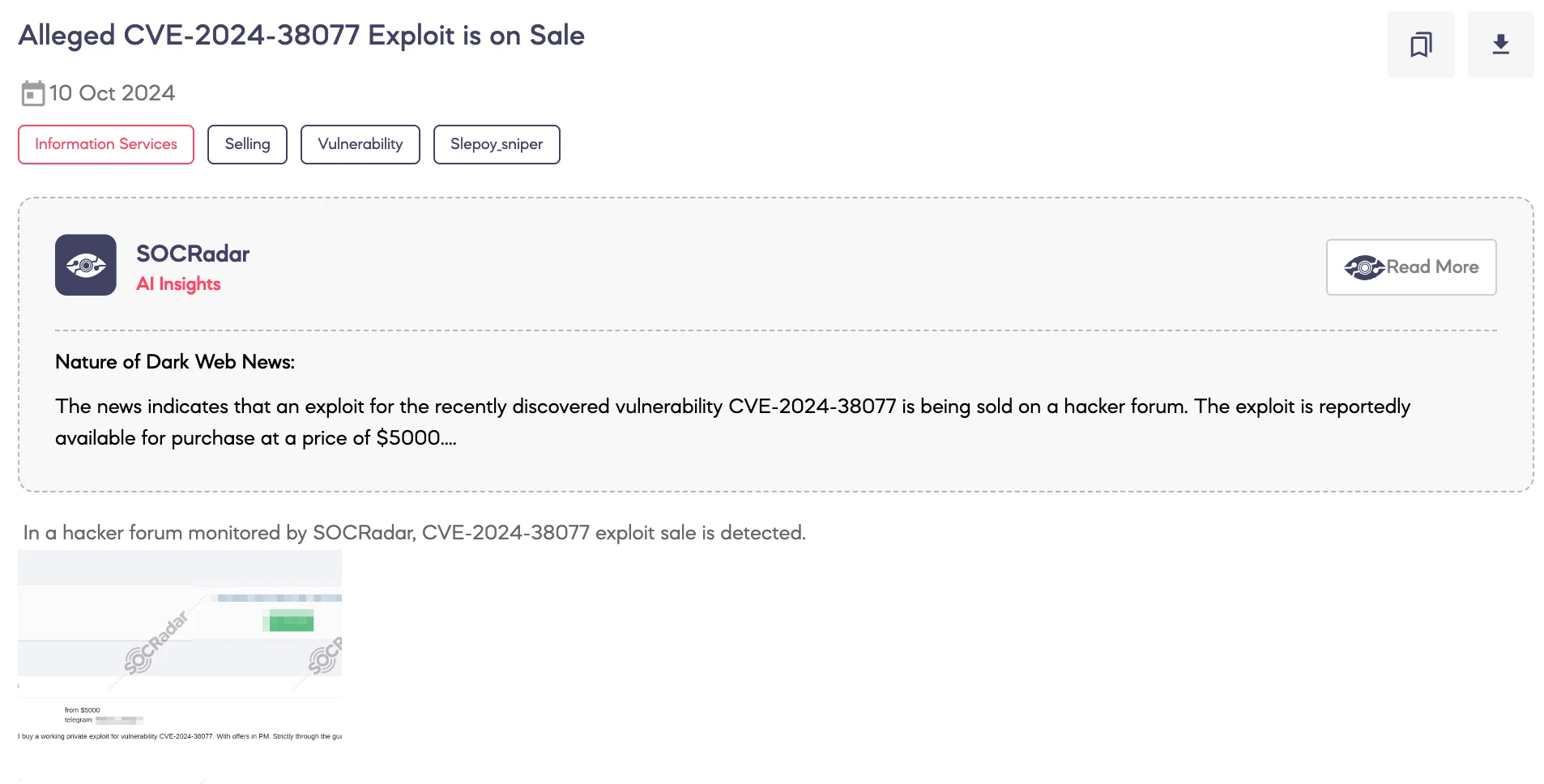
SOCRadar Dark Web Team detected that a threat actor is offering a private exploit for the CVE-2024-38077 vulnerability for sale on a hacker forum.
The threat actor claims to be selling the exploit with a starting price of $5,000 and is conducting communications via Telegram. They have stated that all offers must be made privately and that any transactions will be conducted through a guarantor to ensure security.
CVE-2024-38077 is a critical vulnerability (CVSS score: 9.8) affecting the Windows Remote Desktop Licensing Service. It is classified as a Remote Code Execution (RCE) vulnerability, stemming from a heap-based buffer overflow. This exploit was initially addressed in Microsoft’s July 2024 Patch Tuesday, where five critical vulnerabilities were patched, including this one.
NoName057(16) Conducted DDoS Attack on Cybersecurity Center Belgium
SOCRadar Dark Web Team detected on a Telegram channel that the pro-Russian hacktivist group NoName057(16) claims to have conducted a Distributed Denial-of-Service (DDoS) attack targeting the Centre for Cyber Security Belgium (CCB).
The threat actor addressed the CCB in a mocking tone, suggesting that the center was struggling to recover from the attack, which they described as “harmless.” They also referenced a report from check-host[.]net to demonstrate the impact of their attack.
This incident highlights NoName057(16)‘s continued activity in targeting European organizations with politically motivated cyberattacks, potentially disrupting the operations of the CCB.
1,561 Credit Cards Belonging to European Countries are Allegedly on Sale
SOCRadar Dark Web Team detected that a threat actor is allegedly selling 1,561 credit cards belonging to individuals from various European countries, excluding France, on a hacker forum.
The threat actor claims that the credit card data is being sold as-is, with no returns or replacements, and that the average validity rate is approximately 56%. They have provided screenshots from card checkers as proof of the data’s authenticity, with links to these screenshots on the forum. The auction for the credit cards starts at $2,000, with bids increasing in $200 increments, and a blitz price of $4,000.
According to the threat actor, the data format for 80% of the cards includes credit card number, expiration date, CVV, full name, address, city, state, zip code, country, phone number, date of birth, and email. The remaining 20% of the cards follow a simpler format that includes credit card number, expiration date, CVV, full name, and address details.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































