VMware and Cisco Patched Critical RCE and Privilege Escalation Vulnerabilities
[Update] June 21, 2023: VMware has revised a recent security advisory regarding a critical vulnerability, CVE-2023-20887, currently being exploited in the wild. This now-patched flaw, permitting remote code execution by unauthenticated actors, affects VMware Aria Operations for Networks. This advisory comes after numerous alerts from cybersecurity company GreyNoise, with the initial warning released a week after the patch released by VMware on June 15. It also comes shortly after security researcher Sina Kheirkhah divulged technical specifics and a proof-of-concept exploit code.
This blog post highlights the recent security patches released by VMware and Cisco to address critical vulnerabilities in their respective software solutions.
VMware has addressed multiple vulnerabilities in VMware Aria Operations for Networks, while Cisco has resolved a severe privilege escalation bug in Cisco Secure Client.
The vulnerabilities pose significant risks, ranging from remote code execution to unauthorized access and privilege escalation.
Multiple Critical Vulnerabilities Patched in VMware Aria Operations for Networks
VMware has released multiple security patches to fix vulnerabilities in VMware Aria Operations for Networks.
These vulnerabilities, classified as critical and high-severity, pose significant risks as they could potentially allow attackers to execute remote code or gain access to sensitive information.
Formerly known as vRealize Network Insight (vRNI), VMware Aria Operations for Networks is a tool used for network visibility and analytics, assisting administrators in optimizing network performance and managing various VMware and Kubernetes deployments.
CVE-2023-20887: This command injection vulnerability is considered the most severe among the vulnerabilities addressed in the security patches.
Unauthenticated threat actors can exploit it through low-complexity attacks that do not require user interaction.
If successfully exploited, a malicious actor with network access to VMware Aria Operations for Networks can remotely execute arbitrary code.
According to the provided information and our calculations, the CVSS score for this vulnerability is 9.8.
CVE-2023-20888: CVE-2023-20888 is an authenticated deserialization vulnerability that can lead to remote code execution on unpatched Aria Operations appliances.
To exploit CVE-2023-20888, the attacker requires network access to the vulnerable appliance and valid credentials with a ‘member’ role.
According to the provided information and our calculations, the CVSS score for this vulnerability is 8.8.
CVE-2023-20889: This is an information disclosure vulnerability. Upon successful exploitation of this flaw, malicious actors can gain unauthorized access to sensitive information following a command injection attack.
Apply Security Patches
To mitigate these vulnerabilities, VMware advises administrators to apply the necessary security patches to all VMware Aria Operations Networks 6.x on-prem installations. Unfortunately, there are no workarounds available to eliminate the attack vectors.
Detailed information about the security patches and the affected versions of Aria Operations for Networks can be found on VMware’s Customer Connect website. The website also provides step-by-step instructions for applying the patches. The procedure involves downloading the update patch file, logging in as the Administrator user in the vRNI GUI, and installing the patch from the “Settings > Install and Support > Overview and Updates” section.
Cisco Addresses a Severe Secure Client Bug Granting Privilege Escalation (CVE-2023-20178)
Cisco has addressed a high-severity vulnerability, identified as CVE-2023-20178, affecting its Cisco Secure Client software. The vulnerability could allow potential attackers to escalate privileges to the operating system’s SYSTEM account.
Cisco Secure Client, built upon AnyConnect Secure Mobility Client, is a security endpoint software that helps remote employees securely connect to their corporate network from any location via a Virtual Private Network (VPN).
How Does the CVE-2023-20178 Vulnerability in Cisco Secure Client Work?
The vulnerability, CVE-2023-20178, stemmed from the improper assignment of permissions to a temporary directory created during the software upgrade process. Local attackers with low privileges could exploit CVE-2023-20178 by manipulating a specific function in the Windows installer process without requiring actions from the user.
Patches Available for Cisco Secure Client and AnyConnect Secure Mobility Client
Cisco has patched the CVE-2023-20178 vulnerability in the Windows versions of Cisco Secure Client 5.0MR2 and AnyConnect Secure Mobility Client 4.10MR7. According to Cisco, there have been no reports or indications of the vulnerability’s exploit, nor has there been any public exploit code targeting this vulnerability in the wild.
Safeguard Against Vulnerabilities With SOCRadar
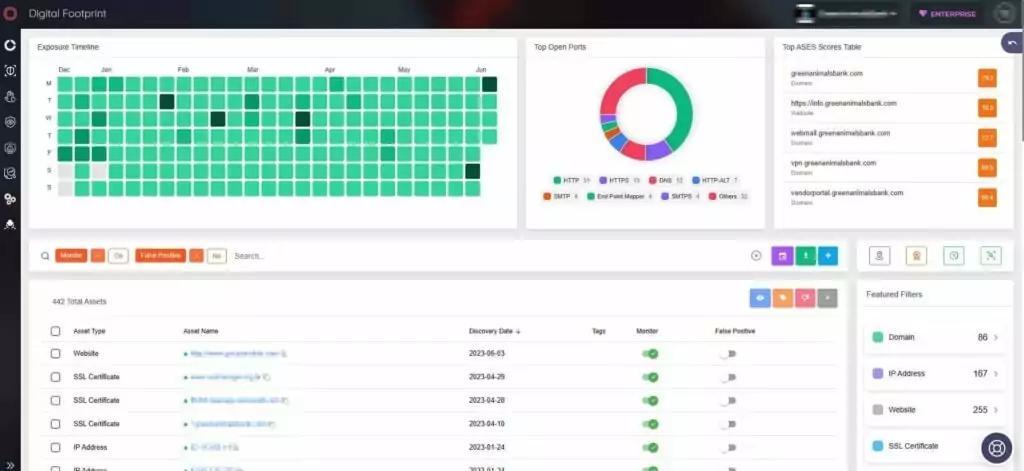
SOCRadar’s Attack Surface Management empowers organizations to proactively track vulnerabilities across their digital footprint and gain access to valuable contextual intelligence. With automated detection of digital assets and real-time monitoring, security teams can take swift actions to address any vulnerability.
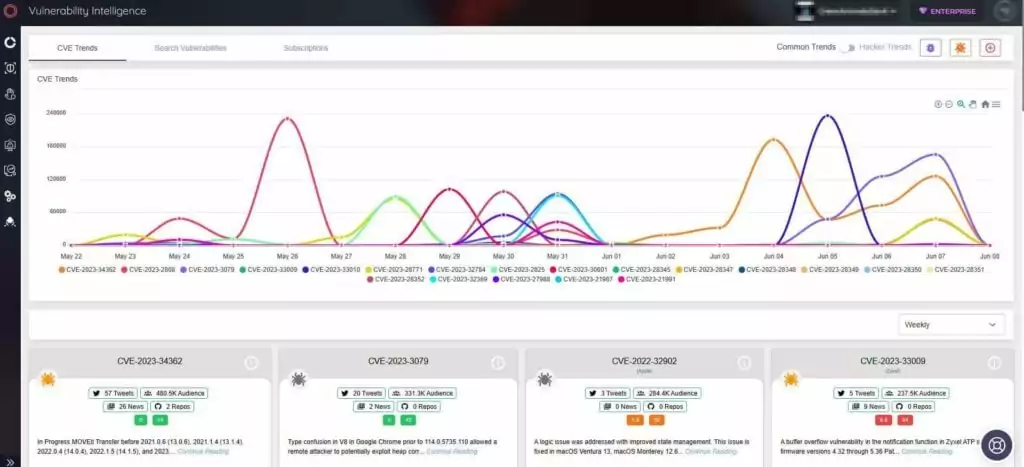
Furthermore, SOCRadar’s Vulnerability Intelligence provides detailed vulnerability information and updates about the latest exploitation trends. Having visibility into company vulnerabilities enables you to prioritize patches, effectively strengthening your organization’s overall security posture better.