
VMware vCenter Server Updates Address Critical RCE and Privilege Escalation Vulnerabilities (CVE-2024-37079, CVE-2024-37080, CVE-2024-37081)
Broadcom has released a security update for its popular management platform, VMware vCenter Server, addressing several vulnerabilities of critical and high severity. The update, issued today, fixes vulnerabilities identified as CVE-2024-37079, CVE-2024-37080, and CVE-2024-37081.
vCenter Server is an advanced server management platform that centralizes the management of VMware vSphere deployments and automates virtual infrastructure across hybrid cloud environments.
What is the vCenter Server appliance used for? (VMware)
The recently discovered vulnerabilities in VMware vCenter Server pose significant security risks, as attackers could exploit them to escalate privileges and execute code remotely. This update is essential to maintain the integrity and security of virtual environments managed by vCenter.
Which VMware vCenter Server versions are affected?
The security vulnerabilities recently addressed by Broadcom impact several versions of VMware vCenter Server. Specifically, the affected versions include:
- vCenter Server 7.0
- vCenter Server 8.0
- Cloud Foundation (vCenter Server) versions 4.x and 5.x
These versions are susceptible to the critical and high severity vulnerabilities identified as CVE-2024-37079, CVE-2024-37080, and CVE-2024-37081; thereby, organizations using these versions are advised to apply the latest updates.
What are the critical CVE-2024-37079 and CVE-2024-37080 vulnerabilities?
Broadcom identified two critical security vulnerabilities in VMware vCenter Server, both rated with CVSS scores of 9.8. These vulnerabilities, tracked as CVE-2024-37079 and CVE-2024-37080, are heap-overflow issues within the DCERPC protocol implementation.
An attacker with network access to vCenter Server can exploit these vulnerabilities by sending a specially crafted network packet. This action could potentially allow the attacker to perform Remote Code Execution (RCE) on the affected system.
How do these vulnerabilities impact VMware vCenter Server?
The exploitation of these vulnerabilities could have severe consequences.
If an attacker successfully executes arbitrary code, they could gain control over the affected vCenter Server. This control could compromise the entire virtual infrastructure managed by the vCenter Server, leading to unauthorized access, data breaches, and further exploitation of the network.
Given the critical nature of these vulnerabilities, organizations must apply the latest security updates to their VMware vCenter Servers to mitigate these risks and protect their virtual environments.
A ZoomEye search for exposed VMware vCenter appliances reveals nearly 42,000 results, predominantly located in the United States and China, with France also having a significant presence.
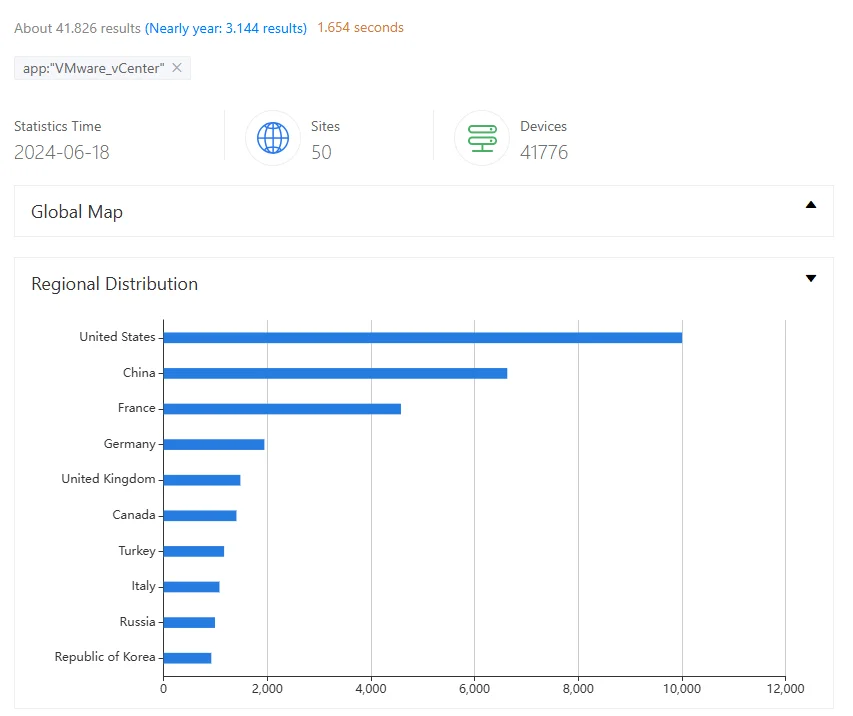
ZoomEye search results for VMware vCenter
Another Vulnerability Addressed in VMware’s New Patch
VMware’s latest advisory also addresses another severe vulnerability: CVE-2024-37081. With a CVSS score of 7.8, CVE-2024-37081 is classified as a high-severity vulnerability.
This vulnerability encompasses multiple privilege escalation issues in vCenter Server, stemming from the misconfiguration of the sudo utility. An authenticated local user with non-administrative privileges could exploit this vulnerability to escalate their privileges to root on the vCenter Server appliance.
For continuous monitoring and effective management of vulnerabilities, organizations can use SOCRadar’s Vulnerability Intelligence. With Vulnerability Intelligence, users can:
- Stay updated on the latest exploitation trends and threat landscapes to better protect their systems against potential attacks.
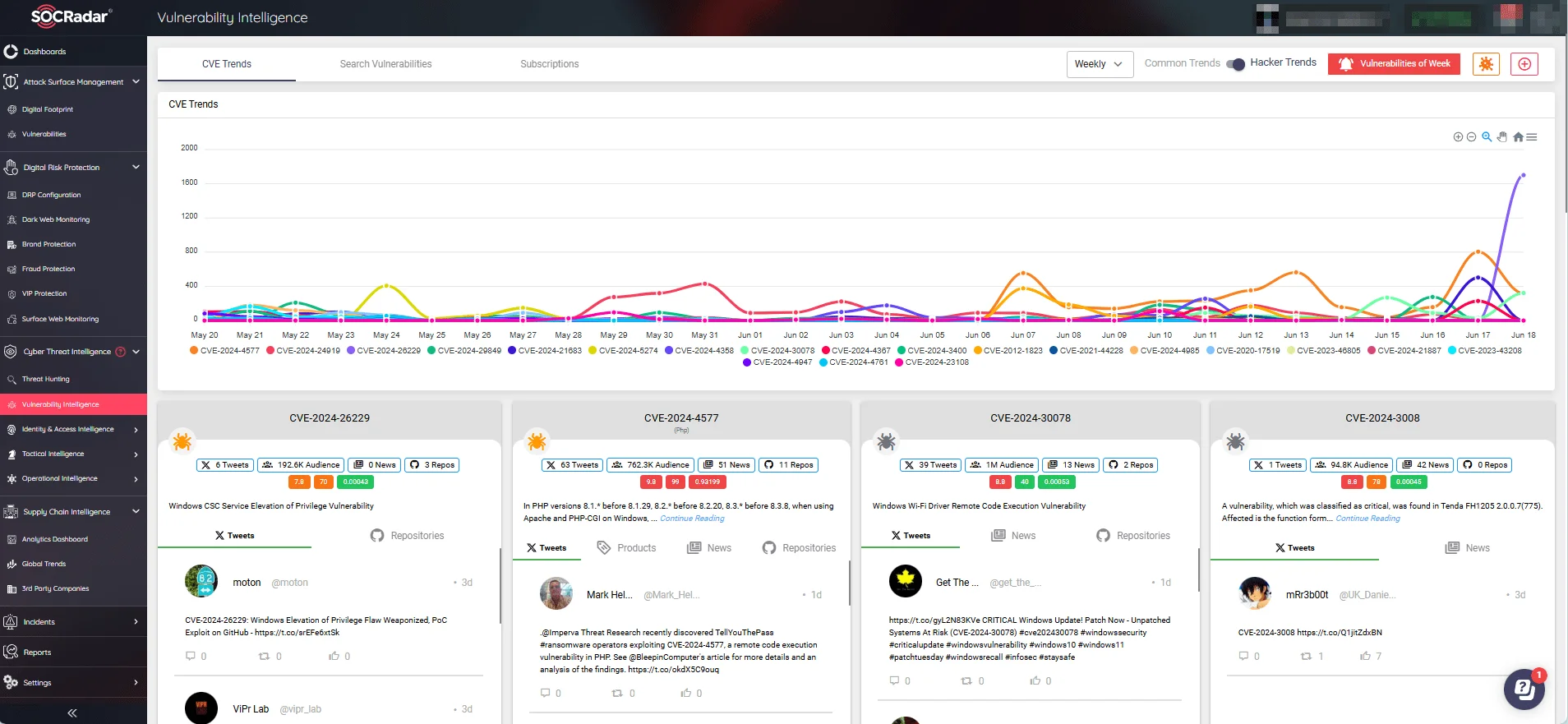
CVE and exploitation trends on Vulnerability Intelligence
- Obtain detailed information on emerging CVEs, including new exploits, mentions across different platforms, relevant repositories, affected software and systems, all references, observations of the vulnerability in the wild, and exploitability scores.
- Filter and search for vulnerabilities by product, vendor, and other tags, allowing for targeted and efficient vulnerability management.
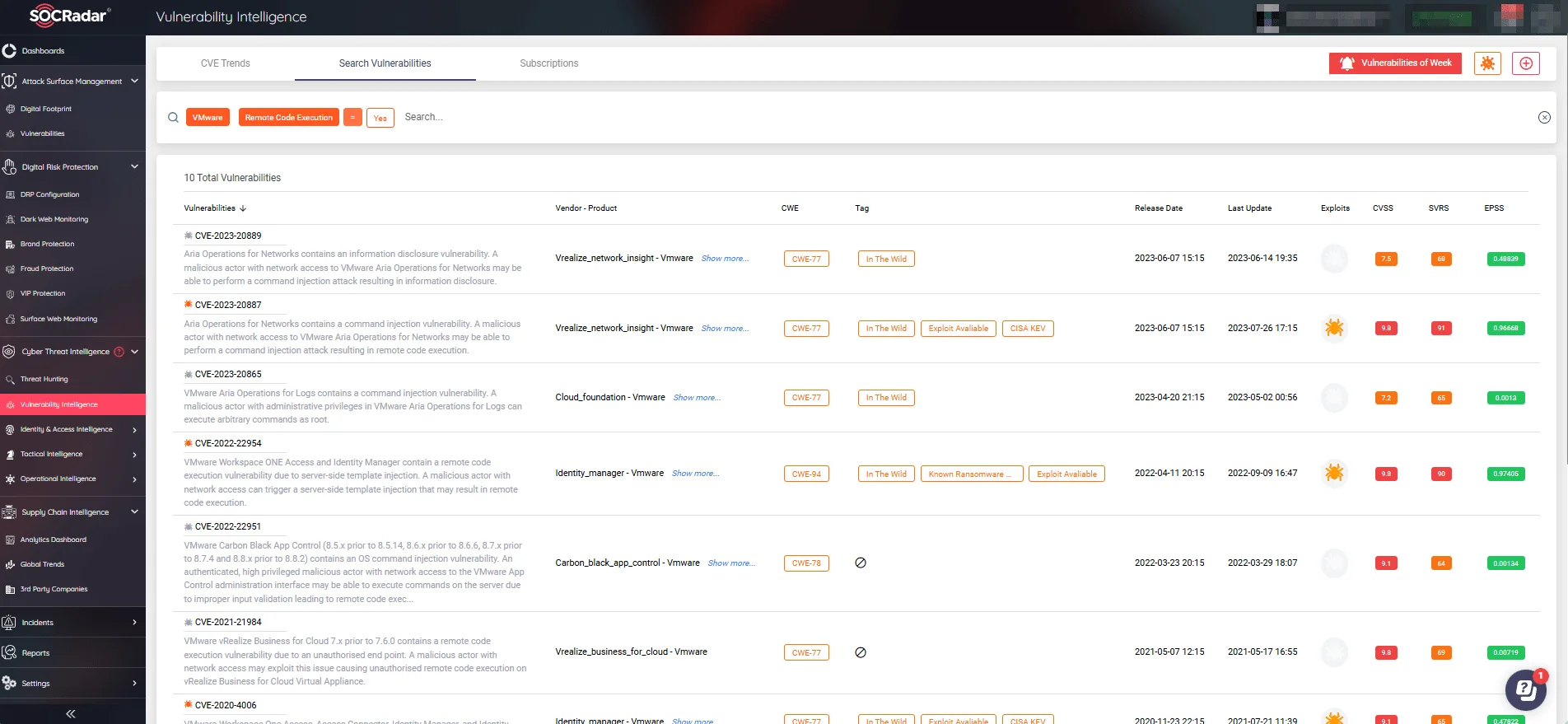
Search vulnerabilities with Vulnerability Intelligence
By leveraging these features, organizations can enhance their security posture and proactively mitigate the risks associated with vulnerabilities.
How can you address these vulnerabilities?
VMware has released security updates to mitigate the vulnerabilities identified in vCenter Server and Cloud Foundation. Users and administrators are strongly advised to apply these updates to prevent exploitation:
Are there any workarounds available?
For the critical vulnerabilities CVE-2024-37079 and CVE-2024-37080, Broadcom stated in the advisory that in-product workarounds were investigated but determined to be non-viable. As for the privilege escalation vulnerabilities (CVE-2024-37081) surrounding VMware vCenter Server, it was directly stated that no workarounds are available.
Given the unavailability of workaround methods, it is very important that vCenter Server users promptly address these issues by applying the necessary updates to avoid exploitation.
For more detailed information and to access updates, see Broadcom’s official advisory.
Monitor Assets and Identify Security Vulnerabilities via SOCRadar’s ASM
With SOCRadar’s Attack Surface Management (ASM) module’s continuous monitoring of digital assets, you can keep up with security incidents and respond quickly to new vulnerabilities.
SOCRadar’s ASM, Company Vulnerabilities
The ASM module sends real-time threat alerts with rapid and actionable insights, enabling effective preemptive actions to improve your cybersecurity posture. By leveraging SOCRadar’s ASM, organizations can stay ahead of potential threats, ensuring their digital environments remain secure and resilient against evolving cyber threats.



































