Weekly Vulnerability Summary by CISA: Ivanti Avalanche, Apache Dubbo, OpenSSH, and More
The Cybersecurity and Infrastructure Security Agency (CISA) has released a new vulnerability summary for the latest security vulnerabilities. The summary for the week of December 18 includes numerous critical vulnerabilities and may constitute the majority of the latest vulnerabilities assigned a CVE in 2023.
For an in-depth look at the exploited CVEs of 2023, explore our blog post titled “2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog.” It provides yearly statistics and a detailed examination of types, targeted vendors, and more information about the vulnerabilities added to CISA’s exploited list in 2023.
Returning to our subject, in this blog post, we will outline some of the critical vulnerabilities featured in the latest CISA vulnerability summary that could impact organizations’ digital resilience.
In this overview of the weekly CISA vulnerability summary, we will delve into instances such as Ivanti Avalanche, affected by over a dozen critical vulnerabilities, Apache Dubbo facing deserialization vulnerabilities, Projectworlds and Kashipara projects that are vulnerable to SQL injection, and another set of critical vulnerabilities in various WordPress plugins, and more.
As we delve into this weekly roundup, our goal is to highlight the most pressing threats requiring immediate attention and proactive mitigation efforts.
Ivanti Avalanche
Multiple vulnerabilities have been discovered in Ivanti’s Avalanche Mobile Device Management (MDM) system. Avalanche MDM is designed for centralized device management via an internet connection, facilitating supply chain mobility.
An attacker can cause memory corruption by sending specially crafted data packets, potentially resulting in a Denial of Service (DoS) or code execution due to the vulnerabilities listed below:
- CVE-2023-41727
- CVE-2023-46216
- CVE-2023-46217
- CVE-2023-46220
- CVE-2023-46221
- CVE-2023-46222
- CVE-2023-46223
- CVE-2023-46224
- CVE-2023-46225
- CVE-2023-46257
- CVE-2023-46258
- CVE-2023-46259
- CVE-2023-46260
- CVE-2023-46261
Detailed information about these vulnerabilities is available in our previous blog post, which you can visit through the following link:
Additionally, three other vulnerabilities impacting Avalanche can lead to Remote Code Execution (RCE) and Server-Side Request Forgery (SSRF):
- CVE-2023-46263 & CVE-2023-46264 (CVSS Score: 9.8): In Avalanche versions 6.4.1 and below, an unrestricted upload of a file with a dangerous type vulnerability exists, allowing an attacker to achieve RCE.
- CVE-2023-46265 (CVSS Score: 9.8): An unauthenticated user could exploit an XML External Entity (XXE) vulnerability in the Smart Device Server to leak data or perform SSRF.
Apache Dubbo
Apache Dubbo is a high-performance WEB and RPC framework designed for building enterprise-level microservices, offering various functionalities.
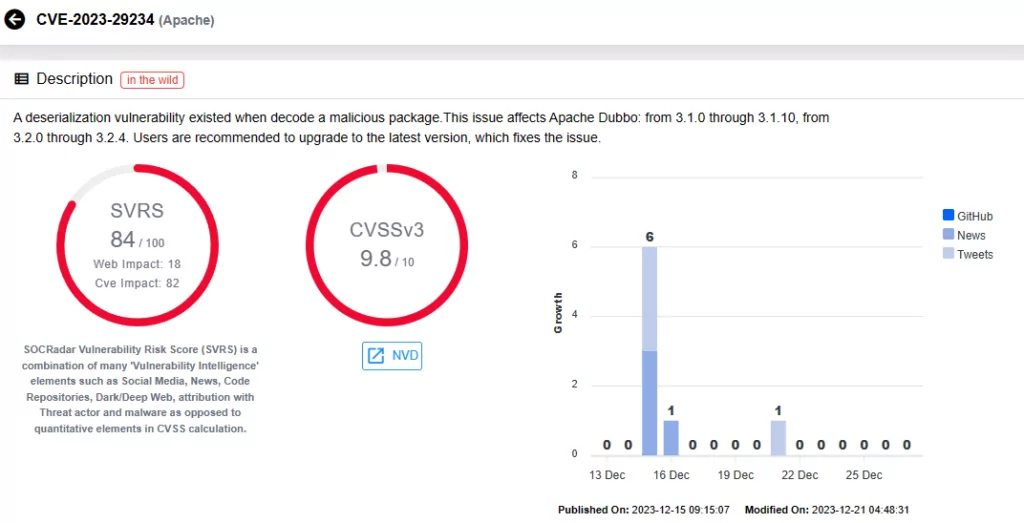
- CVE-2023-29234 (CVSS Score: 9.8): A deserialization vulnerability exists when decoding a malicious package. This issue impacts Apache Dubbo versions from 3.1.0 through 3.1.10 and from 3.2.0 through 3.2.4.
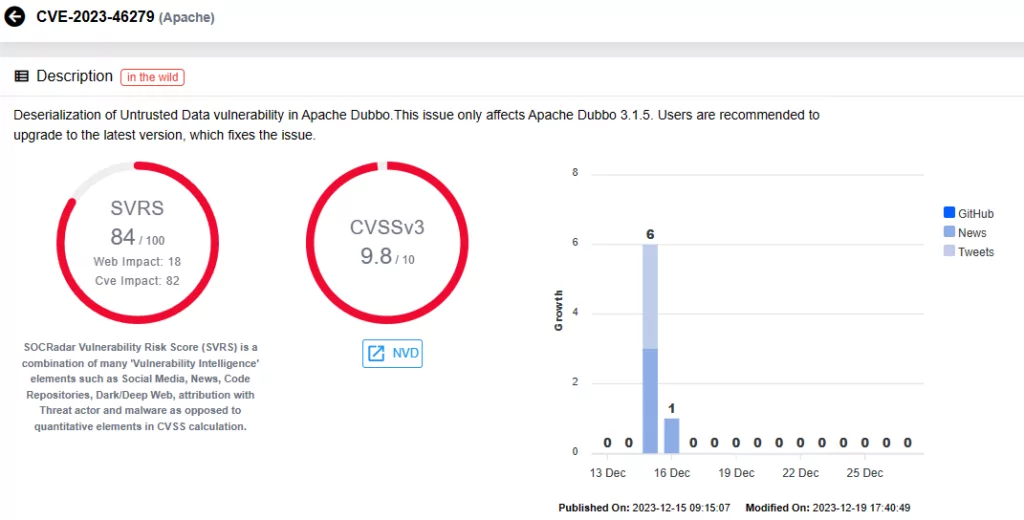
- CVE-2023-46279 (CVSS Score: 9.8): There is a Deserialization of Untrusted Data vulnerability in Apache Dubbo. This specific issue is present in Apache Dubbo version 3.1.5 only.
Projectworlds & Kashipara
Multiple critical SQL injection vulnerabilities have been discovered in various projects hosted on Projectworlds and Kashipara platforms, all carrying CVSS scores of 9.8.
The vulnerable projects on Projectworlds include:
- Online Voting System Project v1.0
- Online Examination System v1.0
- Online Matrimonial Project v1.0
- Railway Reservation System v1.0
- Student Result Management System v1.0
The vulnerable projects on Kashipara include:
- Job Portal v1.0
- Student Information System v1.0
Notably, most of these SQL injection vulnerabilities do not require privilege for exploitation. For the details of these vulnerabilities, refer to the complete weekly vulnerability summary on CISA.
Deepin Linux
Deepin Linux, an open-source distribution based on the Debian stable branch, is affected by a critical vulnerability:
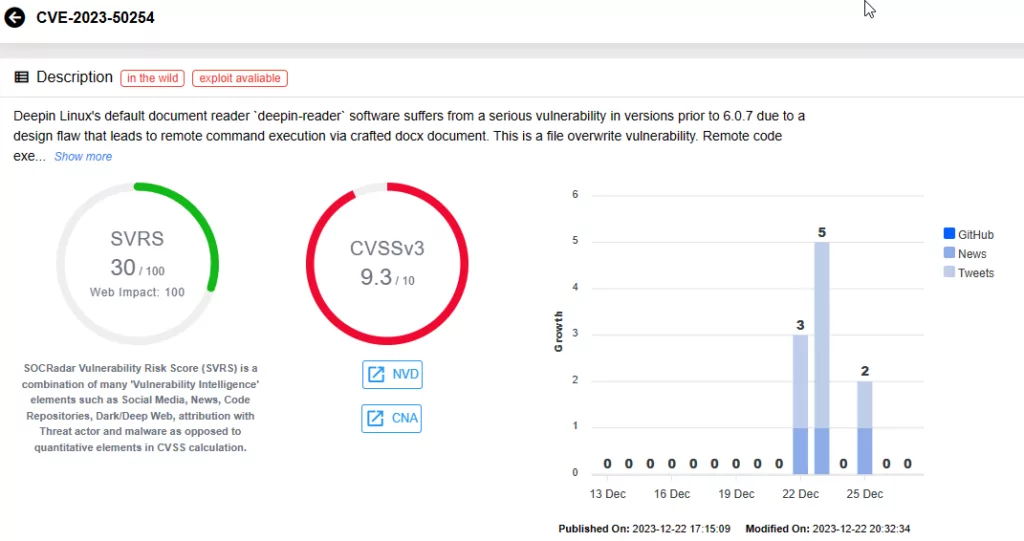
- CVE-2023-50254 (CVSS Score: 9.3): The default document reader software, deepin-reader, in versions prior to 6.0.7 has a design flaw, allowing RCE through a crafted DOCX document. The vulnerability, categorized as a file overwrite issue, allows RCE by overwriting files like .bash_rc, .bash_login, etc.
WordPress
Several critical vulnerabilities have been identified in various WordPress plugins, with five of them having the maximum CVSS score of 10:
- CVE-2023-25970: Unrestricted Upload of File with Dangerous Type vulnerability in Zendrop – Global Dropshipping plugin.
- CVE-2023-29384: Unrestricted Upload of File with Dangerous Type vulnerability in HM Plugin WordPress Job Board and Recruitment Plugin – JobWP.
- CVE-2023-49772: Deserialization of Untrusted Data vulnerability in Phpbits Creative Studio Genesis Simple Love.
- CVE-2023-49773: Deserialization of Untrusted Data vulnerability in Tim Brattberg BCorp Shortcodes.
- CVE-2023-49778: Deserialization of Untrusted Data vulnerability in Hakan Demiray Sayfa Sayac.
There are two other critical WordPress plugin vulnerabilities, listed with other vendors’ names, carrying CVSS scores of 9.8:
- CVE-2023-6559: The MW WP Form plugin for WordPress is vulnerable to arbitrary file deletion in all versions up to, and including, 5.0.3, because it does not properly validate the path of an uploaded file before deletion. This can lead to deletion of arbitrary files, including the configuration file, and result in site takeover and RCE.
- CVE-2023-6553: The Backup Migration plugin for WordPress is vulnerable to RCE in all versions up to, and including, 1.3.7 via the /includes/backup-heart.php file, allowing unauthenticated attackers to execute code on the server.
Tenda
Tenda i29 v1.0 V1.0.0.5 is afflicted with multiple critical vulnerabilities, including buffer overflows (CVE-2023-50984, CVE-2023-50985, CVE-2023-50986, CVE-2023-50987, CVE-2023-50988, CVE-2023-50990), two command injection vulnerabilities (CVE-2023-50983 and CVE-2023-50989), and a stack overflow (CVE-2023-50992). These vulnerabilities, with a CVSS score of 9.8, pose significant risks within the Tenda firmware.
It is noteworthy that various Tenda firmware vulnerabilities were also previously included in previous weekly summaries, indicating an ongoing need for attention and remediation.
Uffizio
Uffizio, a prominent GPS tracking software company specializing in fleet management services for the global B2B market, is currently facing a critical security issue:
- CVE-2020-17485 (CVSS Score: 9.8): Uffizio’s GPS Tracker, across all versions, is vulnerable to RCE attacks. This vulnerability allows an attacker to compromise the web server by uploading and executing a web/reverse shell. Exploiting this vulnerability could enable unauthorized execution of commands, browsing system files, and accessing local resources.
A similar vulnerability was previously reported in another fleet management service: CVE-2023-6248, affecting Syrus4 IoT Gateway.
OpenSSH
- CVE-2023-51385 (CVSS Score: 9.8): In versions of OpenSSH before 9.6, there is a potential for OS command injection if a username or hostname contains shell metacharacters, and this name is referenced by an expansion token in specific situations. An example scenario involves an untrusted Git repository that includes a submodule with shell metacharacters in a username or hostname.

Users and administrators are strongly advised to update to the latest version of OpenSSH to mitigate this vulnerability and enhance system security.
Monitor Emerging Vulnerabilities with SOCRadar
SOCRadar’s Extended Threat Intelligence provides organizations with tools for rapid identification, evaluation, and mitigation of vulnerabilities. With the Attack Surface Management module, you can access details about your digital assets and receive alerts about security vulnerabilities affecting them, effectively managing patching efforts.
For deeper insights, updates, and hacker trends associated with identified vulnerabilities, you can also use SOCRadar’s Vulnerability Intelligence feature.