
What are STIX/TAXII?
The industry standard for sharing threat intelligence, STIX/TAXII is a great starting point for anyone new to threat intelligence.
Technically speaking, STIX and TAXII are not sharing programs, tools, or software, but rather components and standards that support them. STIX states the what of threat intelligence, while TAXII defines how that information is relayed.
STIX and TAXII are standards that were created to help with cyber-attack prevention and mitigation. The “what” of threat intelligence is defined by STIX, while the “how” is defined by TAXII. STIX and TAXII, unlike prior ways of sharing, are machine-readable and thus easily automated.
In a few ways, STIX/TAXII tries to increase security measures:
- Extend the present threat intelligence sharing capabilities
- Maintain a balance between reactive and proactive detection.
- Encourage a comprehensive threat intelligence methodology.
STIX/TAXII is an open, community-driven initiative that provides free specifications to aid in the automated expression of cyber threat information. Both have a thriving development and analyst community.
STIX
STIX is an acronym for Structured Threat Information eXpression. The name says it all: it’s a standard for providing structured and unambiguous information about computer threats. It has the capability to provide automatic information exchange between the many tools required to protect an organization’s security, as it is based on JSON.
TAXII
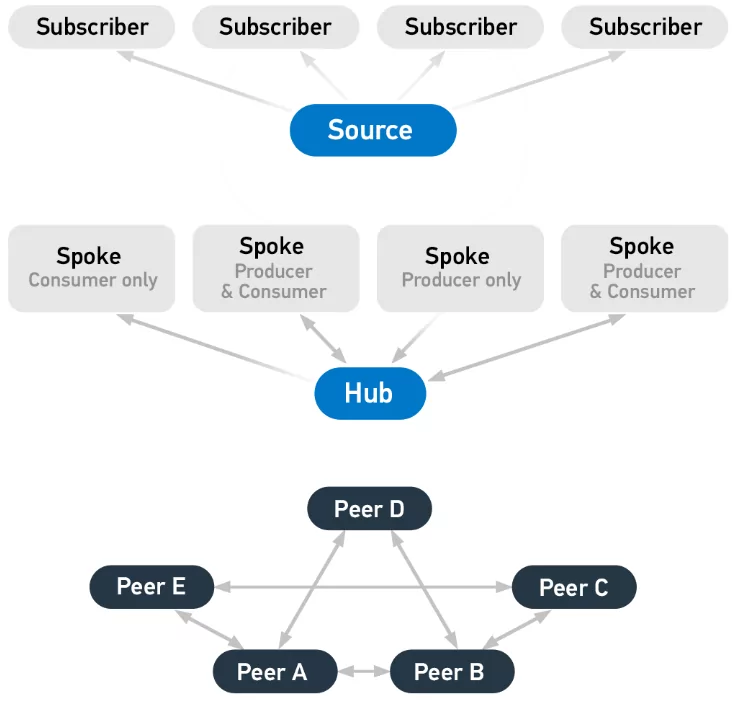
TAXII, or Trusted Automated eXchange of Intelligence Information, is a standard for sharing cyber threat information via services and message exchanges. It is built specifically to support STIX data, and it accomplishes this by offering an API that is compatible with popular sharing models. The following are the three main TAXII models:
- Hub and spoke — one repository of information
- Source/subscriber — one single source of information
- Peer-to-peer — multiple groups share information
TAXII defines four services. Users can select and implement as many as they require, and combine them for different sharing models.
- Discovery — a way to learn what services an entity supports and how to interact with them
- Collection Management — a way to learn about and request subscriptions to data collections
- Inbox — a way to receive content (push messaging)
- Poll — a way to request content (pull messaging)
SOCRadar ThreatFusion
ThreatFusion provides a big-data powered threat investigation module to help Threat Intelligence Teams searching for deeper context, real-time threat research and analysis. The suite is fed by massive data sources across surface, deep and dark web from paste sites to underground dark web forums. The module also includes API-ready intelligence feeds pulled from a broad variety of sources to provide IOCs of potential threats and threat actors targeting your industry.
SOCRadar ThreatFusion enables to define and share threats in STIX and TAXII format to make it much easier for your organization. Want to know more about it? Click here!
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.



































