
What Is Babuk? The Ransomware Gang You Should Know About
[Update] January 10, 2024: “Babuk Tortilla Ransomware Variant Decrypted”
Babuk, also known internally as Babyk, initially “Vasa Locker,” is a pretty new ransomware threat discovered at the beginning of 2021. The gang, defining itself as a non-malicious group created to reveal the security issues inside the corporate networks, is responsible for attacks on at least five big enterprises.
According to security researchers, Babuk Locker’s coding is amateurish but includes secure encryption that prevents victims from recovering their files for free.
In April 2021, the group threatened Washington D.C.’s Metropolitan Police Department (M.P.D.) to release sensitive information pulled from the department’s systems and demanded a $4 million ransom. Babuk’s cybercriminals declared they had downloaded 250 GigaBytes of data and threatened to release information about police informants to criminal gangs and to continue attacking the state sectors, including the F.B.I. and the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency.

The ransomware gang does not have a stable internal structure. The group claimed to get retired after attacking the Metropolitan Police Department and feeling the heat from U.S. law enforcement. However, one month later, some group members splintered off to relaunch the ransomware as Babuk V2 and declared that they would quit ransomware-as-a-service (RaaS) crypto locking and focus on data-theft extortion.
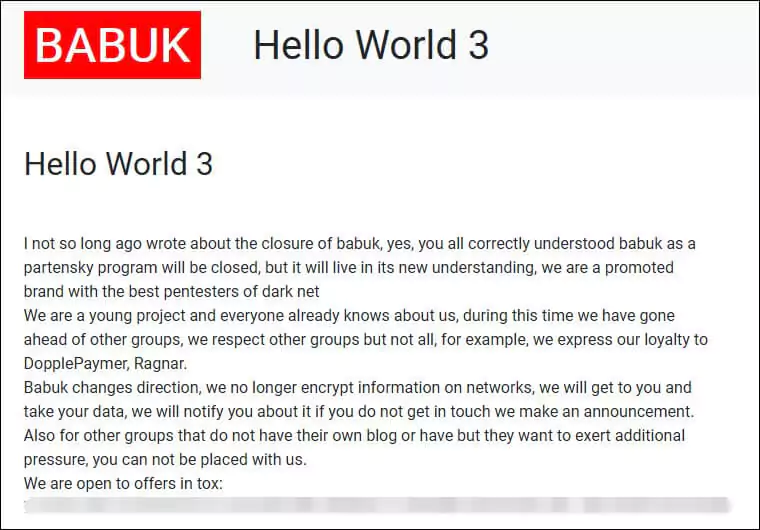
Ransomware Group Drama At Cybersecurity News
In July 2021, RAMP, the forum started by Babuk, has seen a surge of flooding and spamming with pornographic GIFs. An unknown individual stated they had 24 hours to pay $5,000, and this situation was called “ransomware group drama” at cybersecurity news.
Finally, one of the developers for the Babuk ransomware group, a 17-year-old person from Russia, leaked the entire Babuk source code for Windows, ESXI, and NAS in September. It is wondered what is going to be the next step of the gang.
Are You A Probable Target for Babuk?
The group generally targets the transportation, healthcare, plastic surgery, electronics, and agricultural sectors across multiple geographies, especially in Germany, Hong Kong, Sweden, and the United States. Anecdotal data also suggests that malware samples have appeared in other Asian, European, and North American countries, even though this may be a consequence of increased security researcher activity rather than active compromises.
On the other hand, they are pretty clear about categories of organizations they do not attack. The gang claims that it does not audit the hospitals except private plastic surgery or dental clinics, any non-profitable charitable foundation, schools except significant universities, and small businesses with annual revenue of less than $4 million.
How Does Babuk Break-in?
The gang utilizes big-game hunter tactics to ‘steal, encrypt and leak’ victim data in an attempt to extort payments. Upon execution, Babuk performs the typical ransomware process of attempting to terminate services and procedures related to standard applications, backup programs, endpoint security solutions, and server software. In terms of their modus operandi, the cybercriminals behind Babuk are using similar tactics, techniques, and procedures (TTPs) as other RaaS families.
These include exploiting a variety of popular entry vectors into their target environments. These can include: email phishing where the initial email is linked to a different malware strain that acts as a loader; exploiting publicly disclosed but unpatched common vulnerabilities and exposures (CVEs), particularly in remote access software, web servers, network edge hardware, and firewalls; and breaking in using valid accounts, often via weakly protected remote desktop protocol (RDP) access with credentials obtained via commodity info stealers, for example.
Babuk recruits individuals with pentesting abilities, so security teams should be aware of any traces indicating some open-source tools, such as Bloodhound, winPEASE, and SharpHound, or threat emulation software such as Cobalt Strike or Metasploit.
The group has used ChaCha8 symmetric encryption algorithms for file encryption, but the latest version of Babuk has switched to the HC-128 algorithm from ChaCha8. For file key encryption, Elliptic-curve Diffie–Hellman (ECDH) is used, making it impossible to get the file key for decryption without the private key, which is known only to the cybercriminals.
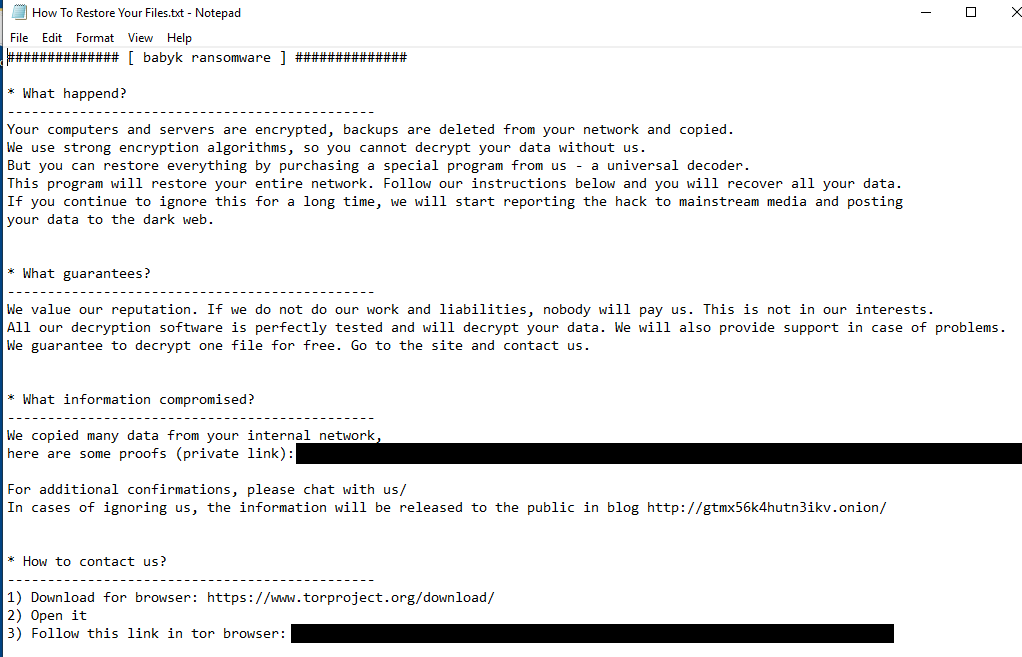
Babuk Tortilla Ransomware Variant Decrypted
On January 9, 2024, Cisco Talos, in collaboration with Dutch Police and Avast, has released a new decryptor for the Babuk Tortilla ransomware variant. This significant breakthrough was achieved by acquiring a private decryption key, integrated into Avast’s Babuk decryptor, aiding victims in recovering their files. The effort highlights a successful partnership against cyber threats. It marks a critical development in the fight against the Babuk ransomware, which emerged in 2021 and quickly evolved, with its code spawning various variants.
Victims of the Tortilla ransomware can access the updated Babuk decryptor through two sources: the NoMoreRansom website’s decryptors section or Avast’s decryptor download page. This provides a resource for those impacted to potentially restore their encrypted files.
Precautions for Avoiding From Babuk and Other Ransomware Gangs
- Ransomware threats often exploit known vulnerabilities. Therefore, robust patch management procedures need to be implemented to secure exposed infrastructure.
- Unusual behavior such as endpoint security events and excessive file operations must be continuously monitored to identify a security breach early.
- Sensitive data should be adequately secure, such as through the use of encryption or additional controls by any legal or regulatory requirements.
- Limiting access to administrative and system management tools, such as those abused by ransomware threats, can prevent misuse by threat actors.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free

































