
What is Strategic Cyber Intelligence and How to Use it
As cyber threats become more sophisticated, many organizations are paying more attention to their security programs. Organizations of all sizes are building security teams to deploy network solutions and address threats. A key component to the success of these initiatives is access to up-to-date cyber threat intelligence.
Cyber Threat Intelligence (CTI)
Before deep-diving into Strategical CTI, we should describe what Cyber Threat Intelligence (CTI). CTI is a form of threat intelligence that can be used to better understand the threats it currently deals with or will deal with in the future. Collecting, analyzing, and classifying cyber threat information is used for providing firms with an actionable vision to identify, measure and rank vulnerabilities and mitigate cyber risks. Better knowledge about cyber CTI gives the latest threat trends on the cyber threat landscape. For your cybersecurity strategy to be effective, you must understand the different types of cyber information.
What are the types of cyber threat intelligence?
Threat intelligence falls into 4 categories within the framework of applicable information: Strategic, Tactical, Operational, and Technical. For these 4 types of intelligence, data collection, analysis, and consumption of intelligence differ. SOCRadar generates intelligence at different levels with the information it collects and ensures the best use of information.
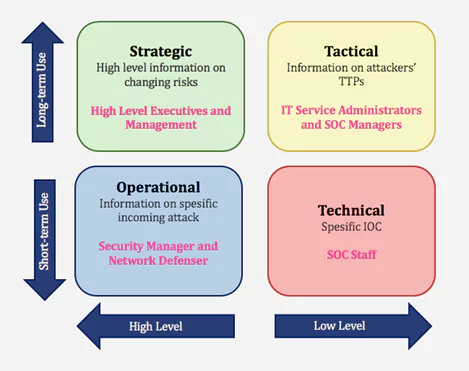
- Strategic Cyber Intelligence: The audience does not need technical knowledge. High-level information on changing risks. High-level information on risk-based intelligence is used by high-level decision-makers (Executives and management). Whitepapers, policy documents, and publications are some examples of strategic cyber intelligence.
- Operational Cyber Intelligence: Actionable information about specific incoming attacks. Infiltrating hacker chat rooms to anticipate the incoming attacks.
- Tactical Cyber Intelligence: Details of threat actor tactics, techniques, and procedures (TTPs).
- Technical Cyber Intelligence: Technical threat indicators such as specific IOC for SOC Staff.
What is Strategic Cyber Threat Intelligence?
Strategic Threat Intelligence provides a high level of information on the cybersecurity posture, threats, financial impact of cyber activities, attack trends, and their impact on business decisions. The information obtained can be used by senior executives at the company, such as CISO. The purpose of Strategic Threat Intelligence is to manage existing cyber risks and unknown future risks. This intelligence offers a risk-based approach. It focuses on the effects and possibilities of risks. The information provided here is suitable for long-term use. It helps in making strategic business decisions. For example, it can evaluate these results when deciding on budget / employee / product balance in protecting critical assets. Data collection sources for strategic intelligence are also high-level sources: OSINT, CTI vendors, and ISAO / ISACS.
Who Uses Strategic CTI, Why, and How?
In most organizations, strategic CTI users are “C-Suite” individuals – the CEO, CFO, CIO, etc., depending on the structure. In other words, this staff is comprised of senior management, executives, and management of an organization. Strategic CTI users don’t need a technical background when making risk-based decisions related to personnel, technologies, cybersecurity requirements, and ultimately budgets. Cyber threat intelligence provides data to better understand patterns and high-level threats to the organization for high-level users.
For example, these results can be considered when deciding on the balance between budget, people, and products to protect critical assets.
- Strategic intelligence provides a high level of information.
- The information provided by intelligence can be used by high-level managers.
- This information is suitable for long-term use.
Strategic intelligence provides answers to questions such as:
- Who are your adversaries? What do they want?
- What is the financial impact of cyber-attacks?
- What are Trend Threat actors and attack trends?
- What is the statistical information about data breaches?
- What are the cyberattacks for companies in the same industry?
- Have there been cyberattacks against our organization in the past, what has been the effect?
- What actions are necessary to reduce your risk profile?
Understanding these questions enables mapping responses to critical systems and business processes and performing a comprehensive risk analysis. It also explains investments in specific programs, technologies and personnel.
Strategic CTI Use Cases: Brand Protection
One of the important areas for strategic CTI users is brand reputation. Brand protection for cyber threat intelligence consists of multiple data points to consider, including phishing campaigns, fake domains, fake social media accounts, and exploited web pages. Assessing risks in each of these areas helps them understand how/why their brands are chosen by threat actors to exploit their customers. Have threat actors taken over existing or forgotten open internet infrastructure? Should they buy additional space to block threat actors? Using CTI to discover and understand brand exposure is an easy way for strategic users to protect both their organization and their customers, which increases profitability.
What SOCRadar Provides
SOCRadar® provides;
- Digital assets (domains, IPs, 3rd applications, CMS, vb) to manage the attack surface,
- Attack surface risk,
- Information of industry-specific cyber-attacks,
- Information of geopolitical cyber-attacks,
- Monitoring popular threat actors,
- Cyber security reports,
- Brand monitoring,
- Executive Intelligence reports to monitor the company risk
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free

































