
What You Need to Know About Cisco Unified Communications Manager SQL Injection Vulnerability (CVE-2023-20211)
In today’s connected world, efficient tools like the Cisco Unified Communications Manager (Unified CM) and Cisco Unified Communications Manager Session Management Edition (Unified CM SME) could be integral to businesses. But what happens when these crucial communication backbones face a security vulnerability? Recent reports have shone a spotlight on a significant SQL injection vulnerability in these Cisco products. Here’s what you need to know.
The Nature of the Vulnerability
The vulnerability in question, CVE-2023-20211, resides within the web-based management interface of both Cisco Unified CM and Unified CM SME. For those unfamiliar, Cisco Unified CM primarily manages voice and video calls, while Cisco Unified CM SME takes charge of session routing intelligence. This vulnerability could potentially grant an authenticated (low level privilege is required to exploit the issue), remote attacker the power to conduct SQL injection attacks on affected systems.
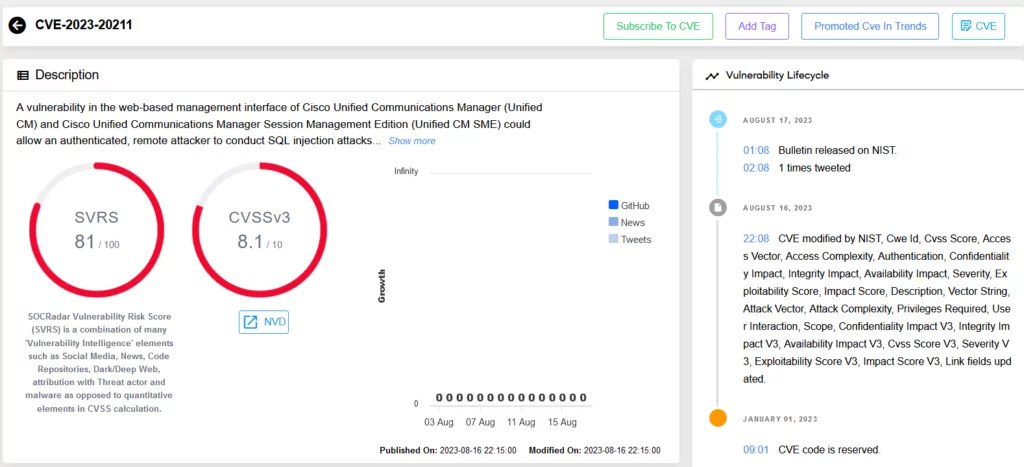
How does this happen? The root cause is due to an absence of proper validation for user-supplied input. In simple terms, if an attacker successfully authenticates into the application—even just as a user with read-only permissions—they can exploit this oversight. By sending strategically crafted HTTP requests to the system, the attacker can gain the ability to read or modify the underlying database. Even more concerning, they could escalate their privileges within the system.
Implications of a Successful Attack
A successful exploitation can have serious repercussions. Not only does it grant the attacker the ability to modify or read data, but it also poses a risk of privilege escalation. This means the attacker could potentially gain higher-level access, further endangering the system and the data within.
Proof-of-Concept Exploit Alert from Cisco
The Cisco PSIRT has confirmed the existence of a Proof-of-Concept (PoC) exploit for the SQL injection vulnerability in the Cisco Unified Communications Manager. While there haven’t been any reported malicious uses yet, the availability of a PoC means that attackers have a roadmap to exploit the vulnerability. It is crucial for users to promptly update their systems to guard against potential attacks leveraging this PoC.
Which Cisco Products Are Affected?
The primary targets of this vulnerability are the Cisco Unified CM and the Cisco Unified CM SME. It is reassuring, however, that a plethora of other Cisco products have been confirmed not to be vulnerable. These include the Emergency Responder, Finesse, Packaged Contact Center Enterprise (Packaged CCE), SocialMiner, Unity Connection, and more.
Securing Your Systems
Cisco has acted in response to this discovery. They’ve rolled out software updates specifically designed to address this vulnerability. If you are using either Cisco Unified CM or Unified CM SME, you’re strongly advised to upgrade to the latest software release to safeguard your systems from potential exploitation. Detailed information on the fixed software releases can be found directly on Cisco’s official advisory page.
Staying Ahead of Vulnerabilities with SOCRadar
In our interconnected era, vulnerabilities like these can pose serious risks to businesses and their communication infrastructures. Regularly consulting advisories for essential products, like Cisco’s, is a recommended practice for all IT professionals.
Moreover, staying a step ahead of potential vulnerabilities and threats is paramount. With SOCRadar’s Vulnerability Intelligence and External Attack Surface Management capabilities, businesses can proactively identify, evaluate, and rectify potential threats, ensuring their digital assets remain uncompromised.
Protecting your digital landscape is not just about responding to threats but anticipating them. Stay safe, and stay informed.




































