
Windows 0-Day Exploit and RDP Access Sales, Database Leaks for Domasa City and Jeevess Ayurveda
Threat actors persist in engaging in illicit activities within the enigmatic realm of the dark web. The SOCRadar Dark Web Team recently encountered an exclusive 0-day exploit for multiple Windows versions, as well as an RDP access sale targeting a company in the automotive service sector. Furthermore, this week’s notable database leaks include a luxury resort in India and a city in Slovakia.
Let’s delve into the most recent weekly discoveries from the SOCRadar Dark Web Team.
Find out if your data has been exposed.
0-day Exploit of Windows LPE is on Sale
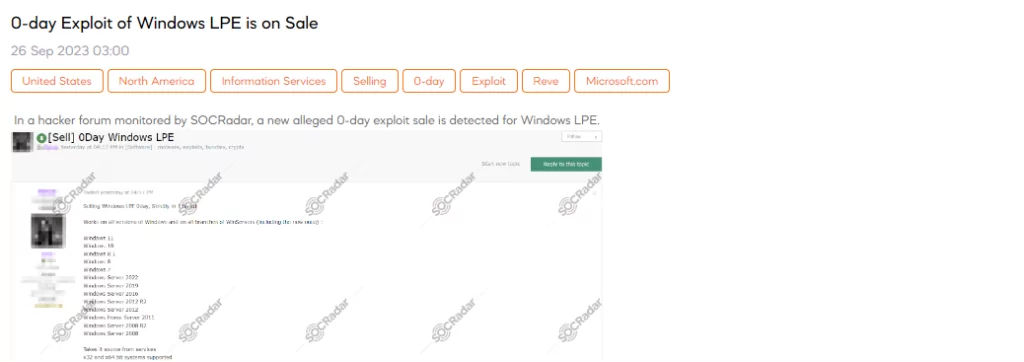
SOCRadar Dark Web Team detected a post in a hacker forum in which a threat actor claims to be selling a 0-day exploit for Windows Local Privilege Escalation (LPE). This exploit is advertised as being exclusive, working on various Windows versions, including Windows 11, Windows 10, Windows 8.1, Windows 8, Windows 7, and multiple Windows Server versions. It is designed to elevate privileges from Low to System in less than a second and is sourced from system services.
The threat actor offers the complete source code, written in Delphi, upon purchase. Threat actor asserts that the exploit can bypass security mechanisms and has been tested with various tools, including Cobalt Strike and custom solutions. Notably, the exploit is designed to remove itself from services, leaving no traces behind. The price for this 0-day exploit is $250,000
Unauthorized RDP Access Sale is Detected for an Automotive Repair Company
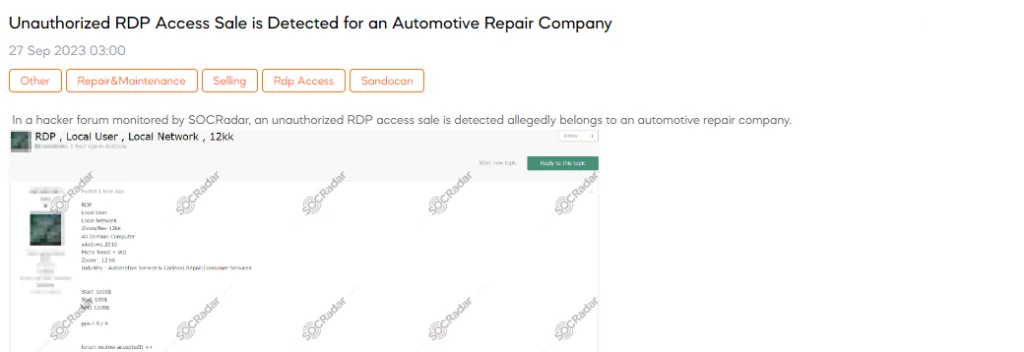
SOCRadar Dark Web Team has detected a post that a threat actor claims to be selling unauthorized RDP (Remote Desktop Protocol) access allegedly belonging to an automotive repair company. The advertised access includes RDP, local user privileges, and access to the local network. The compromised network comprises 40 domain computers running Windows Server 2016 and protected by both Micro Trend and Windows Defender. The sale offers a starting price of $1,000, with increments of $100 and a blitz (instant buy) option for $1,200.
Database of Domasa City is Leaked
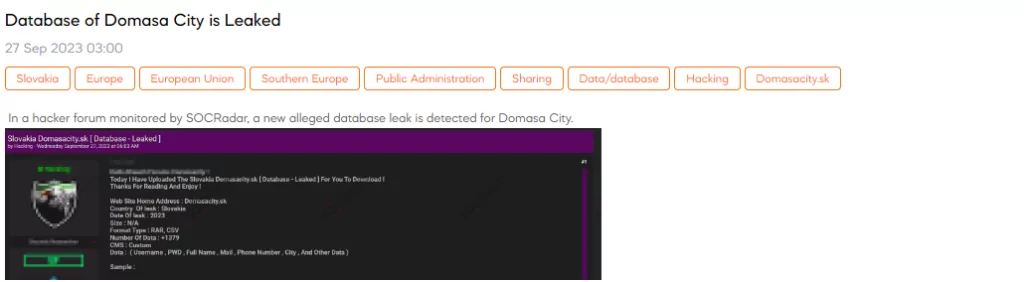
On 27 September, The SOCRadar Dark Web Team detected a post in a hacker forum in which a threat actor claims to have leaked a database related to Domasa City in Slovakia. This alleged database leak includes data from the website Domasacity[.]sk and contains information on more than 1,379 individuals. The data is said to include usernames, passwords, full names, e-mail addresses, phone numbers, city of residence, and other unspecified data. The format of the leaked data is reported as RAR and CSV.
Database of Jeevess Ayurveda is Leaked
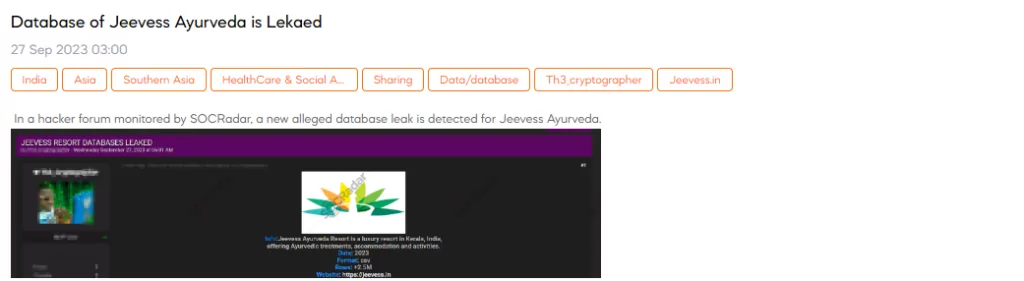
SOCRadar Dark Web Team has identified a post in a hacker forum. In the post, a threat actor claims to have leaked a database associated with Jeevess Ayurveda, a luxury resort located in Kerala, India. This database leak is alleged to have occurred in 2023 and is provided in CSV format with over 2.5 million rows of data.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































