
0-Day Exploit Sales for Outlook and Jenkins, Insurance and Banking Data Leaks, and More
Journey through the sinister realms of cyberspace with SOCRadar’s Dark Web Team. The sale of critical 0-day exploits, targeting Outlook and Jenkins, set a daunting precedent. Meanwhile, unauthorized access sales for an Indonesian airport and an American internet provider were detected.
As a custom hacking service emerged, promising illicit deeds, an API breach jeopardized Buenos Aires. Additionally, threat actors leaked alleged databases from HDI Insurance Mexico and Qatar National Bank (QNB).
Receive a Free Dark Web Report for Your Organization:
0-Day Exploit for CVE-2024-21413 and CVE-2024-23897 is on Sale
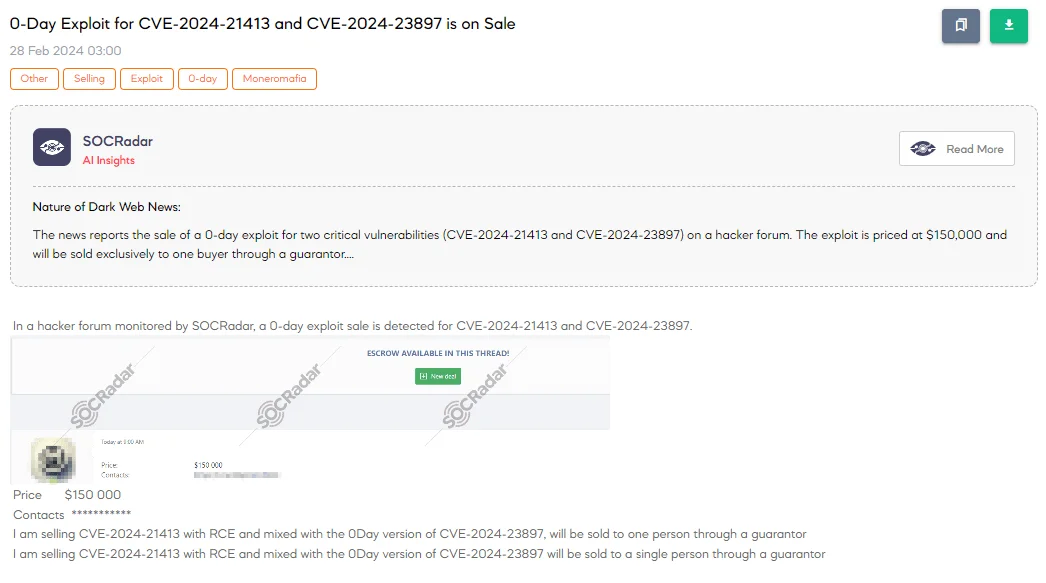
A SOCRadar Dark Web Analyst has detected a sale for 0-day exploits targeting CVE-2024-21413 and CVE-2024-23897 on a hacker forum, priced at $150,000. CVE-2024-21413(CVSS:9.8) is a critical remote code execution (RCE) flaw in Microsoft Outlook, allowing attackers to bypass Protected View, while CVE-2024-23897(CVSS: 7.5) affects Jenkins, enabling arbitrary file reads through its CLI. indicating severe risk. The sale is limited to a single buyer, emphasizing the exploit’s high value and potential for widespread impact.
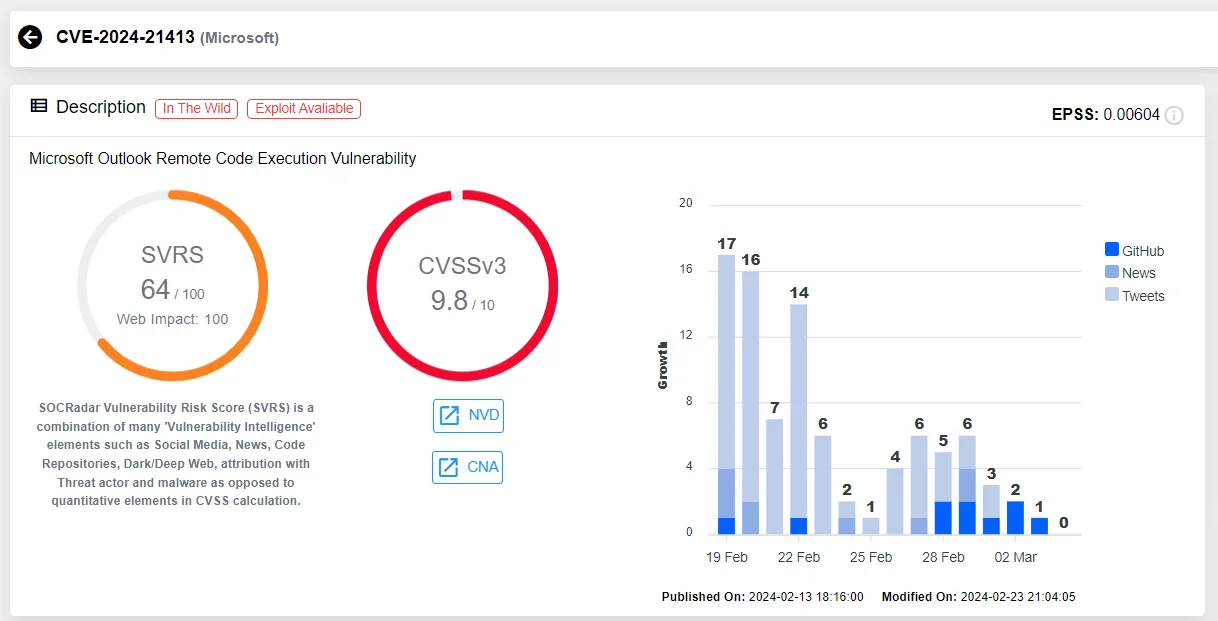
Vulnerability card of CVE-2024-21413 (SOCRadar Vulnerability Intelligence)
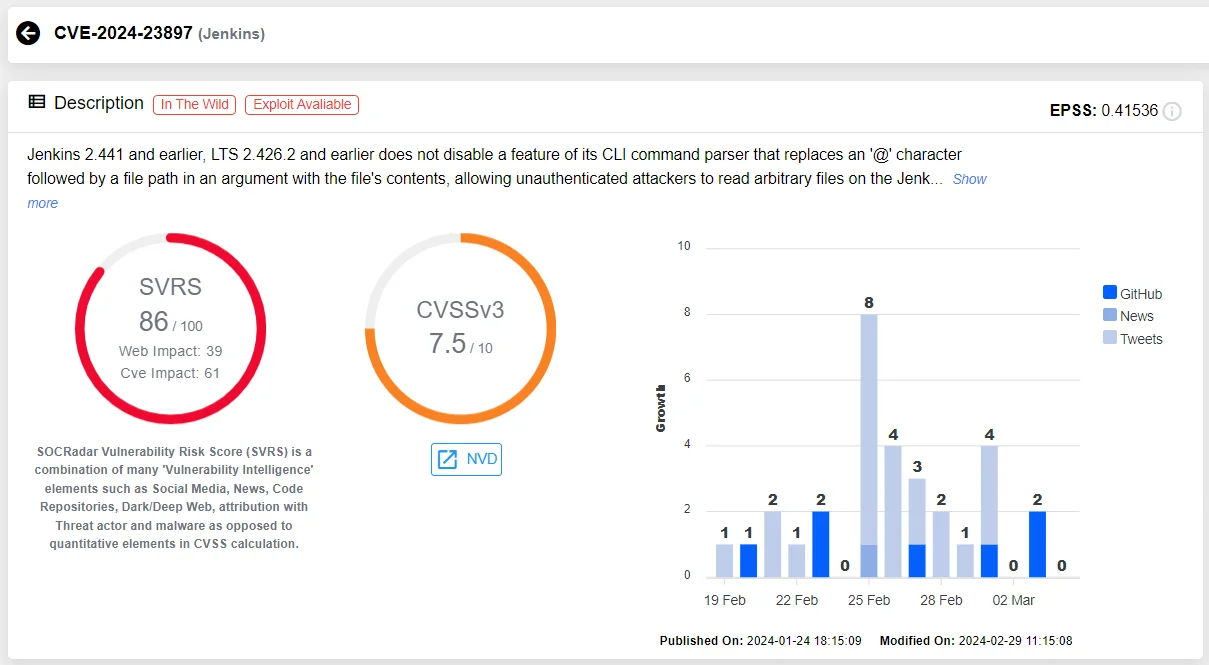
Vulnerability card of CVE-2024-23897 (SOCRadar Vulnerability Intelligence)
Unauthorized VPN Access Sale is Detected for an Indonesian Airport
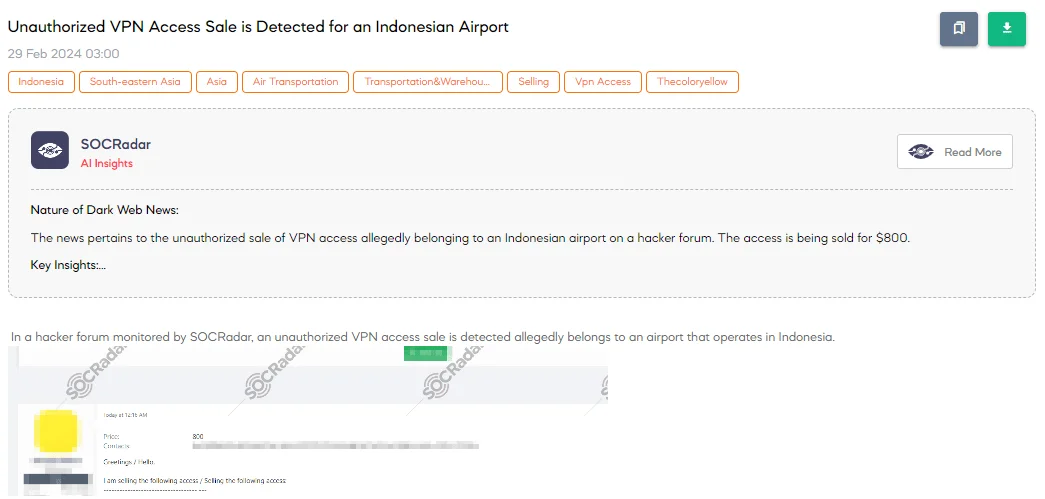
The SOCRadar Dark Web Team has identified a post on a hacker forum where a threat actor claims to be selling unauthorized VPN access allegedly linked to an Indonesian airport. As mentioned in the forum post, this airport is significant in scope, with reported revenues reaching $457 million, indicating its substantial size and the critical nature of its operations within the airport and transportation industry. According to the threat actor, the access sold is specifically for a VPN connection utilizing Fortinet technology, priced at $800.
A New Custom Hacking Service is Detected
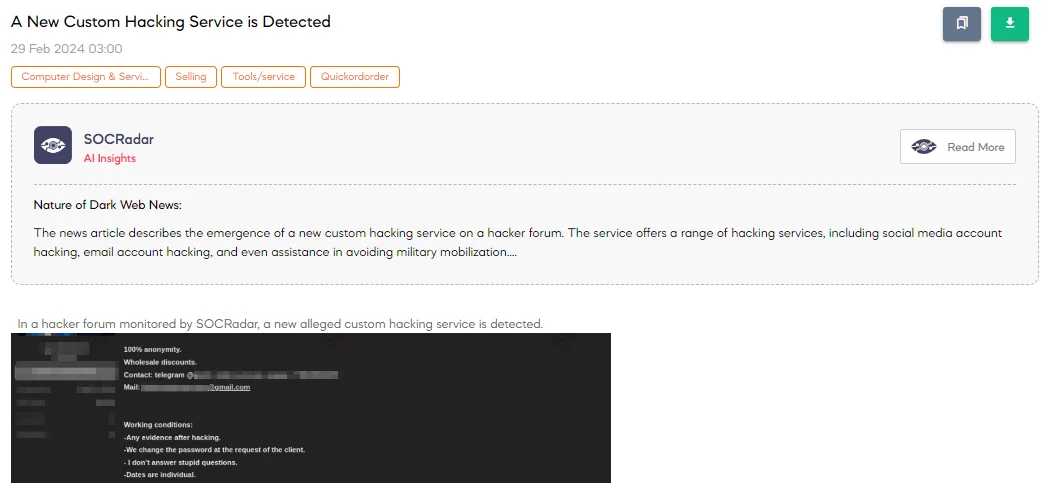
On February 29, the SOCRadar Dark Web Team uncovered a disturbing development in the digital underworld: a threat actor advertising a new custom hacking service on a hacker forum. This service promises 100% anonymity and includes illegal activities such as hacking social networks (e.g., Facebook, Twitter, WhatsApp), email services (e.g., Google, Yandex), and even aiding in evading military mobilization by altering official records. Additionally, it claims to remove negative online information and offers lessons in hacking.
Unauthorized RDP Access Sale is Detected for an American Internet Provider Company
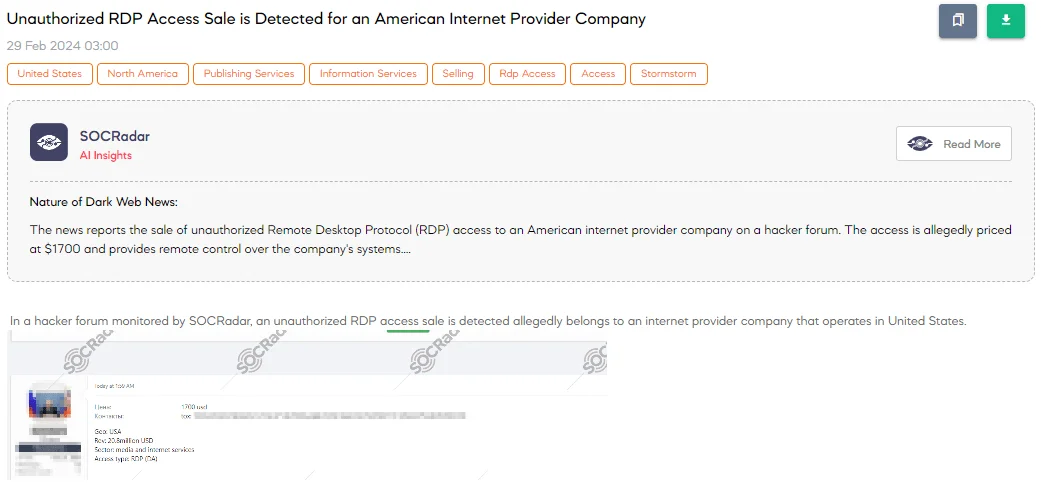
The SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor is advertising the sale of unauthorized Remote Desktop Protocol (RDP) access. This access allegedly belongs to an American internet provider company, identified to be operating within the media and internet services sector, with a reported revenue of $20.8 million. The price for this illegal access is set at $1,700.
RDP access allows for remote control over a computer or network, making unauthorized access particularly alarming. It can provide the threat actor, or whoever purchases this access, the ability to control the company’s network, potentially leading to data theft, deployment of malware, or other malicious activities. The fact that this company operates in the media and internet services sector only amplifies the potential impact, as it could affect a wide range of customers and associated businesses.
Unauthorized API Access Leak is Detected for Province of Buenos Aires
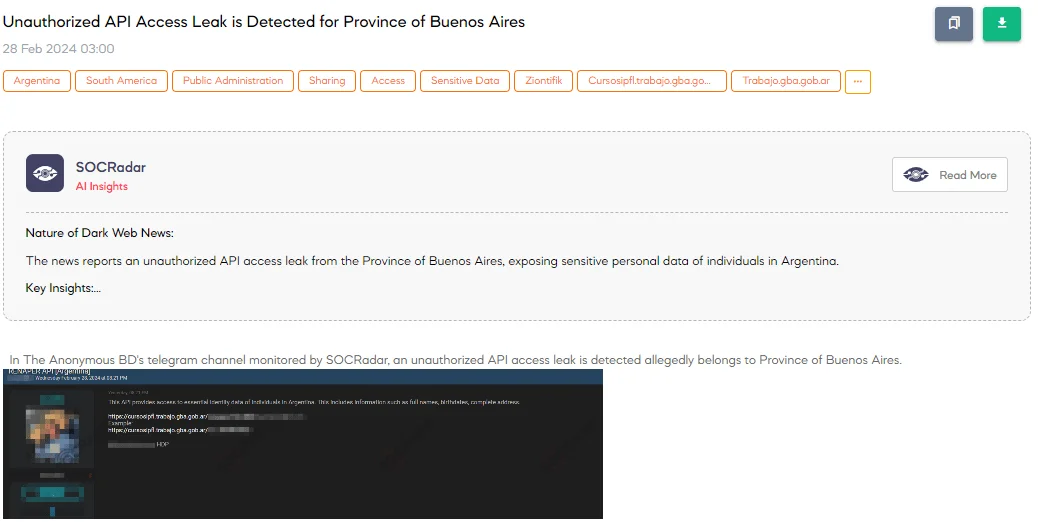
The SOCRadar Dark Web Team has uncovered a concerning security incident involving a threat actor’s claim on a hacker forum about gaining unauthorized access to an Application Programming Interface (API) allegedly belonging to the Province of Buenos Aires. According to the post, this API grants access to critical identity data of individuals residing in Argentina, encompassing sensitive information such as full names, birthdates, and complete addresses.
Unauthorized access to such an API poses a significant risk to the privacy and security of many individuals. APIs are critical components in modern software development, allowing different systems to communicate with each other. When secure, they enable the seamless flow of data and functionality. However, when compromised, they can become gateways for malicious actors to access and exploit sensitive data.
The data exposed in this breach is particularly sensitive because it goes to the heart of individual identity, potentially opening the door for various malicious activities and fraud, from identity theft to sophisticated phishing attacks targeting individuals. The complete addresses, full names, and birthdates provide a solid foundation for fraudsters to impersonate individuals or craft targeted scams.
Documents of HDI Insurance Mexico is Leaked
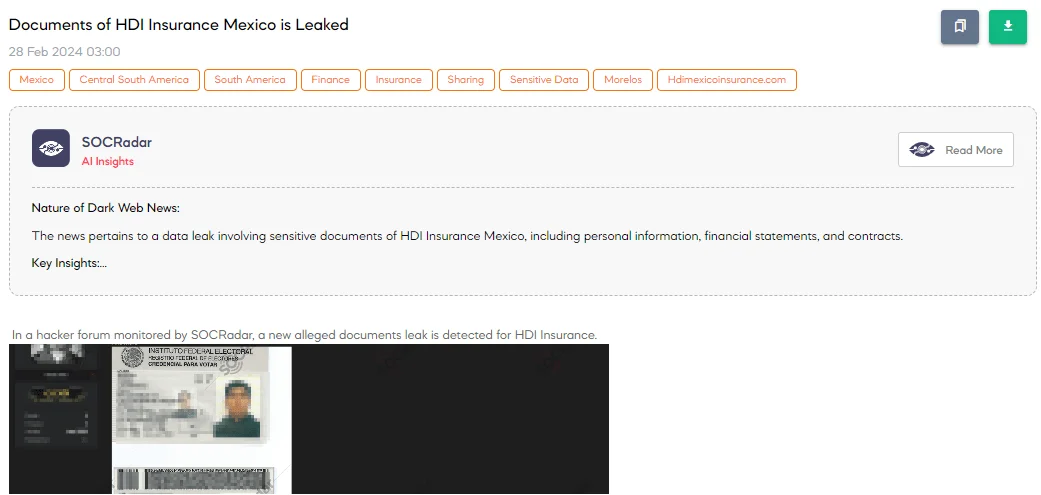
The SOCRadar Dark Web Team detected a significant security breach concerning HDI Insurance in Mexico, as reported on a hacker forum. A threat actor claims to have leaked a substantial amount of sensitive data, including 50,000 files obtained illegally. The disclosed files reportedly encompass confidential documents, such as national identification cards, life insurance policies under HDI, financial statements from Banorte (a major banking institution), various contracts, and additional undisclosed content.
Alleged Database of Qatar National Bank is Leaked
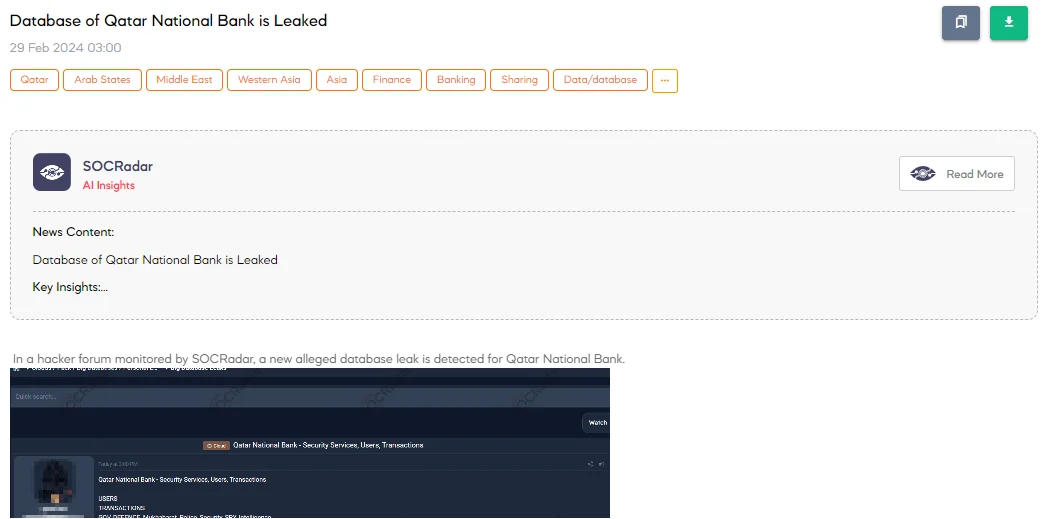
The SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked the database of the Qatar National Bank (QNB). This database allegedly includes a wide range of sensitive information encompassing security services, users, and transactions.
The depth of information claimed to be part of this leak is extensive and includes details such as national ID, country of residence, date of birth, contact information, names, language code, customer type, marital status, passport numbers, account information, and even specific data like the number of children within certain age ranges. This level of detail could potentially expose individuals to a high risk of identity theft, fraud, and could compromise personal and national security.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































