14 Million Credit Card Information Sold on Black Markets
The Q3 Finance Industry Threat Landscape Report prepared by SOCRadar analysts has been published this week. The report includes a detailed analysis of the cybersecurity threats that most impact the financial industry globally.
The threat landscape of finance is growing every day, with threat actors’ adaptiveness to new technologies and automated tools that enable them to target multiple institutions with one click. Money is always the primary motivation of cybercriminals.
You can read the full report by clicking here.
Finance is the top industry targeted by threat actors for the total number of posts and shares on deep web and hacker channels.
Threat Actors Mostly Prefer Data Sales
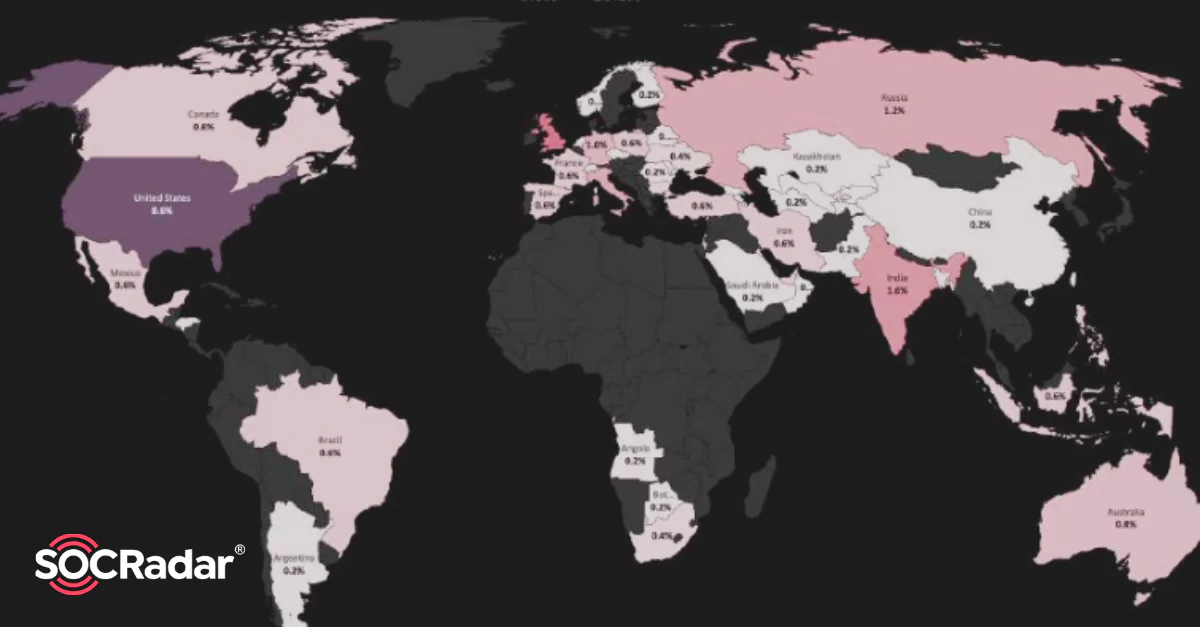
According to the report, the ratio of deep web posts targeting financial institutions has reached 11% in the third quarter of this year.
Most deep web posts targeting financial institutions are related to sensitive data sold by threat actors. The exposed data on sale includes credit card information, employee PII data, and customer databases. Data sales are almost 42% of deep web posts targeting financial institutions in the third quarter of 2021.
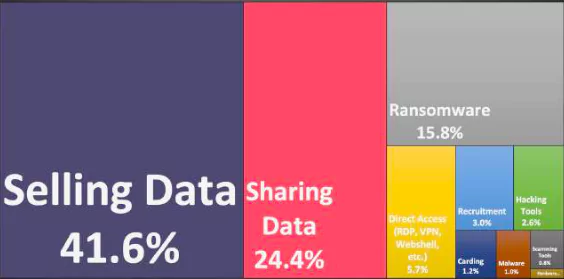
Financial institutions face many other threats. Threat actors exchange hacking tools and malware to target these companies and share their experience on how to cash out stolen credit cards.
One of the report’s highlights is that companies need to work with the right cyber threat intelligence solutions to gain visibility under the surface web. According to the report, companies need to work with the right cyber threat intelligence solutions to gain visibility under the surface web.
14 Million Credit Card Information Sold on Black Markets
The total number of credit card information sold on Black Markets and deep web hacker forums in the first three quarters of 2021 is 600 thousand. Even though the validity ratio is at most 10% for these shares, it is still a pretty large number affecting banking customers.
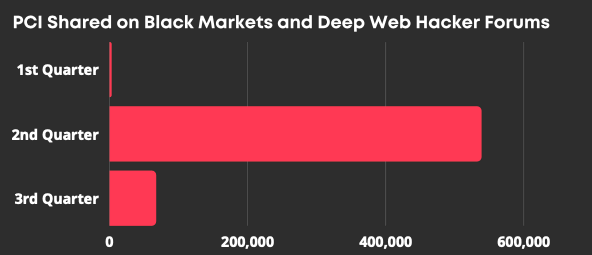
The posts in October so far set another bar with more than 14 million credit card data to be sold on the black markets. Half of them are from a single list posted on October 12.
SOCRadar closely monitors the black market where credit card information is sold in bulk. If shared, SOCRadar can identify the country and the bank it belongs to and send alarms accordingly.
Malware Targeting Banks and Their Customers
This report once again revealed that another cyber threat awaiting customers whose data is sold is malware. There is an increase in banking trojan spreads because of the increase of mobile banking users.
The source code leaks of two very effective bots, namely Anubis 2.5 and Cerberus, also contributed to the rapid rise in the number of banking trojans in the wild. With these leaks, threat actors created multiple private trojan versions actively targeting regions such as Poland, Spain, Turkey, and Italy.
Recent malware families, including Alien or Medusa, developed an approach for advertising by limiting their exposure on public forums and using side channels for the customers to communicate directly with the vendor.
On top of that, threat actors can upload the infectious apps by impersonating the legitimate apps to official mobile app stores such as Google Play Store. All these new adaptations enable cybercriminals to spread banking trojans more professionally.
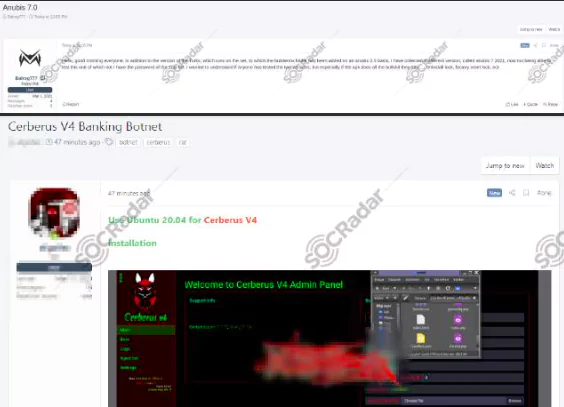
Recent Banking Trojans
- ERMAC: A new banking trojan called Ermac was introduced on a hacker forum in October. Ermac is almost entirely based on the well-known banking trojan Cerberus. The researchers believe that the operator behind this banking trojan is the BlackRock actors. BlackRock is another android malware that appeared in 2020 and can steal banking and other confidential data of a user.
- S.O.V.A.: In August, a new banking trojan dubbed SOVA was introduced in a Russian- speaking hacker forum. The creators of the Android malware claimed that there are already multiple overlays available for different banking institutions from the USA and Spain. The malware is capable of overlay attacks, keylogging, notification manipulation, and also session cookies theft.
In the continuation of the report, the latest situation of phishing attacks against the financial sector, software vulnerabilities exploited by threat actors and DDoS attacks, one of the new emerging threats, were mentioned.
You can read the full report by clicking here.
SOCRadar provides the actionable and timely intelligence context you need to manage the risks in the era of transformation.
Credit Card Monitoring: Enhance your fraud detection mechanisms with automation speed by identifying stolen credit card data on popular global black markets, carding forums, social channels, and chatters.


































