How To Track APT Groups and Get Fresh IOC/TTP?
50% of Fortune 500 companies have been compromised by APTs.[1] More than 90% of intrusions aren’t even discovered by the victims themselves but through third-party notification.
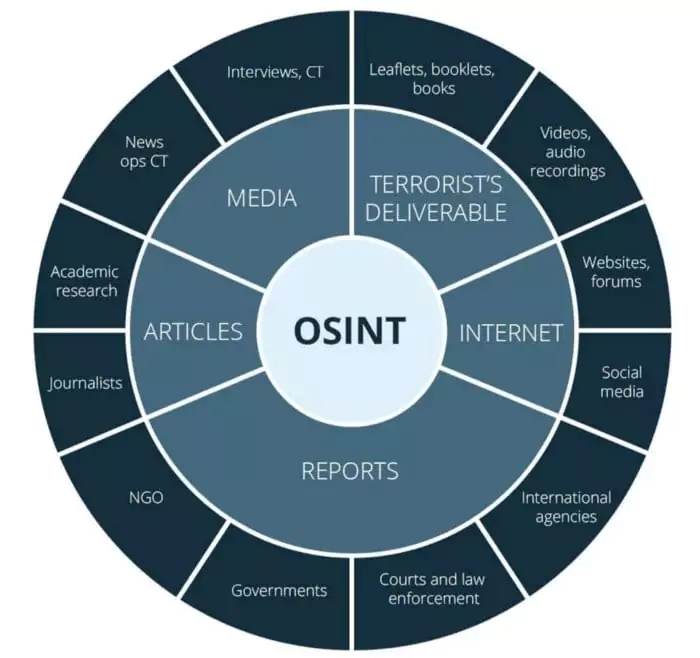
Open Source Intelligence (OSINT) is not only useful but crucial to security teams for analyzing advanced persistent threats. Through OSINT analysis, it is possible to discover clues to APT attack methods, their tactics, techniques and procedures (TTPs), and IoCs (Indication of Compromise).
Security researchers have shown time and again that cyber actors frequently recycle effective attack methods. These attack methods retain telltale signatures even as a threat actor’s targeting and tools evolve. That makes OSINT even more essential to monitor to keep up with adversaries.
What is OSINT?
Open Source Intelligence, better known as OSINT, is a technology that refers publicly available and open sources of information (as opposed to covert or secret sources) used in connection with intelligence. OSINT is information that comes from public and open sources. A large amount of actionable and predictable intelligence is obtained from public and non-classified sources. It means that the information collected is available not only to the public for consumption, but also to the entire intelligence community.
What are the OSINT resources?
The most common OSINT resources are as follows;
- Metadata search
- Search Engines
- Social Media
- Online Communities
- Email Addresses
- Usernames
- People Search Engines
- Telephone Numbers
- Online Maps
- Code search
- Documents
- Images
- Videos
- Domain Names
- IP Addresses
- Government & Business Records
- Virtual Currencies
- Advanced Linux Tools
- Geospatial Research
- Data Breaches & Leaks
Technically, anyone who knows how to use these tools and techniques to access information is said to have used this process. However, because these techniques are fluid due to technological changes, a large part of them cannot be carried out by anyone with knowledge.
What does APT mean?
APT (Advanced Persistent Threats) is a sophisticated, long-term malicious attack that seems to play the long game by spying on the target infrastructure for months or years before successfully breaking through the network.
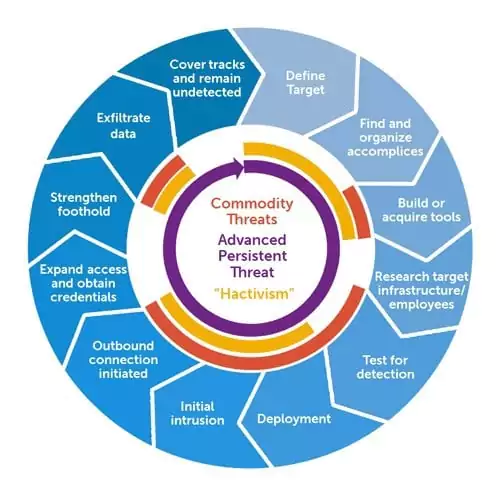
Why the APT attacks are so dangerous?
- Attacks by APT groups are more sophisticated and complicated than the usual hacking.
- APT groups consist of highly qualified, capable, and elusive members with deeply technical backgrounds.
- The motivation behind the hacker groups is often financial or political while the motivation behind APT groups is most of the time strategic.
- In general, APT groups are nation-state or state-sponsored who have much better and advanced devices and are already financially covered.
Why OSINT is crucial to monitor the threats?
- Leveraging OSINT gives us a more comprehensive insight into APT groups.
- APT groups have limited resources and time. They may reuse some custom tools or infrastructures again and again.
- External intelligence will be helpful.
- OSINT can help us correlate evidence of the actor.
How to use OSINT to monitor apt groups and get fresh IOC/TTP?
The intelligence gathered via OSINT can give us lots of critical information about the APT groups and IoCs.
Find APT tools
The tools used by APT groups, most of the time, available on the Internet. Analyzing such tools gives us a clear idea of what kind of weapons are used by the APT groups and what strategy to develop to prevent these attacks.
It is impossible to make an exact estimate of how much an APT attack costs. One reason is the difficulty of putting a value on the unique software used by criminal groups. Most of the time these APT groups don’t even have to use expensive tools to hack. For example;[2]
- Spear phishing is an effective way to penetrate a company’s internal network and is used by 90 percent of APT groups. Tools for creating malicious attachments, not including the cost of exploits for zero-day vulnerabilities, cost around $2,000.
- After penetrating the internal network, half of the APT groups use legitimate administration tools and commercial penetration testing software costing from $8,000 to $40,000.
Detect malicious domains and IP addresses used by APT groups
APT groups could still use the same domains or IP addresses to imitate brands in phishing attacks. These domains and IP addresses easily can be found on the Internet.
For instance, the following domains were used by APT groups many times for phishing attacks:
- fb-login[.]cf
- drives-google[.]com
- microsoft-upgrade[.]mobi
- gmal[.]cf
- hot-mail[.]ml
Continuous monitoring of malicious domains is needed to ensure that IP address blacklists stay up to date.
Sometimes, while even tools can not detect malicious domains or IP addresses, they can easily be detected by OSINT. The table below shows other domains that are not tagged as malicious and their associated IP addresses revealed by DNS Lookup. The IP addresses were then run on VirusTotal to check if they are malicious.

Discover new APT targeted campaigns
In 2019, Kaspersky discovered a malicious toolset that was utilized by the APT group Turla. The malware is delivered to targets via legitimate software installers infected with the Trojan dropper. Once delivered, the attackers gain remote access to the device. Kaspersky published its findings publicly in order to prevent such attacks on organizations. OSINT would let organizations know about such campaigns before they even take a place.
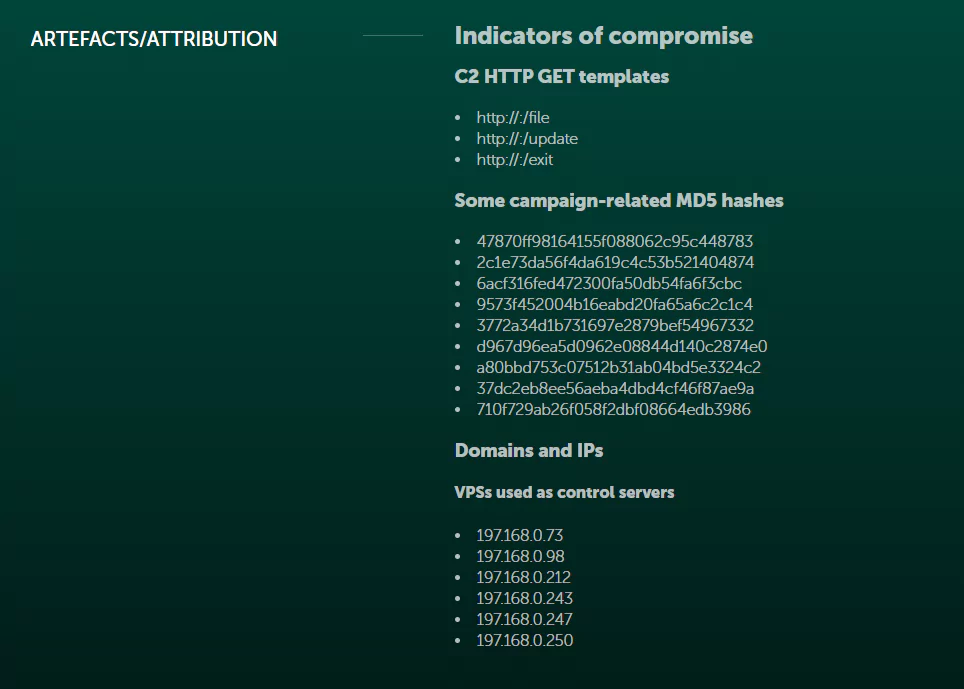
Source
Identify vulnerabilities in your technology stack
Nowadays, with the continuous flow of novel forms of sophisticated attacks and their variants, it is a challenge to keep an IDS updated. Open Source Intelligence (OSINT) could be explored to effectively obtain this knowledge, by retrieving information from diverse sources.
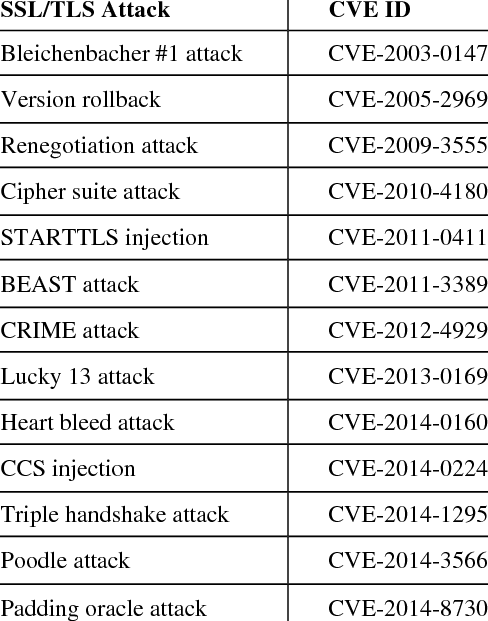
OSINT helps security teams unearth clues that individuals leave in the open that compromise security. Like using a vulnerability scanner to find flaws in systems.
Monitor mentions, threat actors, breaches, and targets
Understanding your threat landscape is an essential part of securing your organization. With access to real-time reporting on attacks and breaches around the world, OSINT can help you find and prioritize the actors most likely to cause harm.
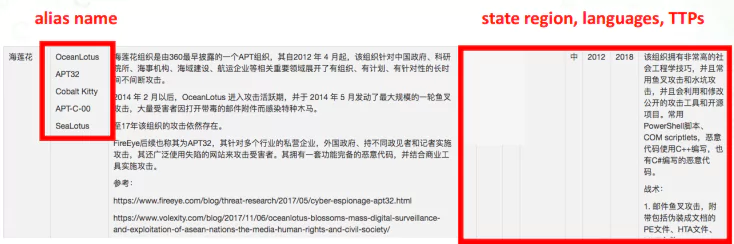
To get an idea, the tactics, techniques, and procedures used by threat actors enable their presence to be anticipated on a network. Also, having an understanding of the intent and capability of threat actors allows CTI analysts and leads to react appropriately in the event of a breach and mitigate its impact as much as possible.
SOCRadar Threat Actor Tracking
Threat actors and APT groups often integrate a variety of tools and tactics to achieve their objectives. Understanding and tracking these adversaries in a dynamic manner provides insights on current TTPs which may be way more important than easily-changed IOCs. Through automated data collection, classification, and AI-powered analysis of hundreds of sources across surface, deep and dark web, SOCRadar keeps you alerted on APT groups’ activities, helping you define use cases to more effectively detect and prevent malicious activities.
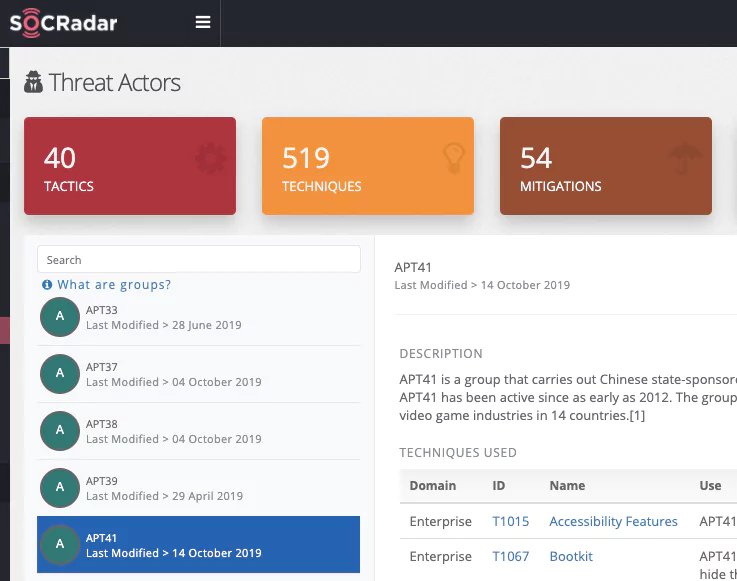
SOCRadar presents an approach for improving OSINT processing to generate threat intelligence of quality in the form of enriched IoCs. This improved intelligence is obtained by correlating and combining IoCs coming from different OSINT feeds that contain information about the same threat, aggregating them into clusters, and then representing the threat information contained within those clusters in a single enriched IoC.
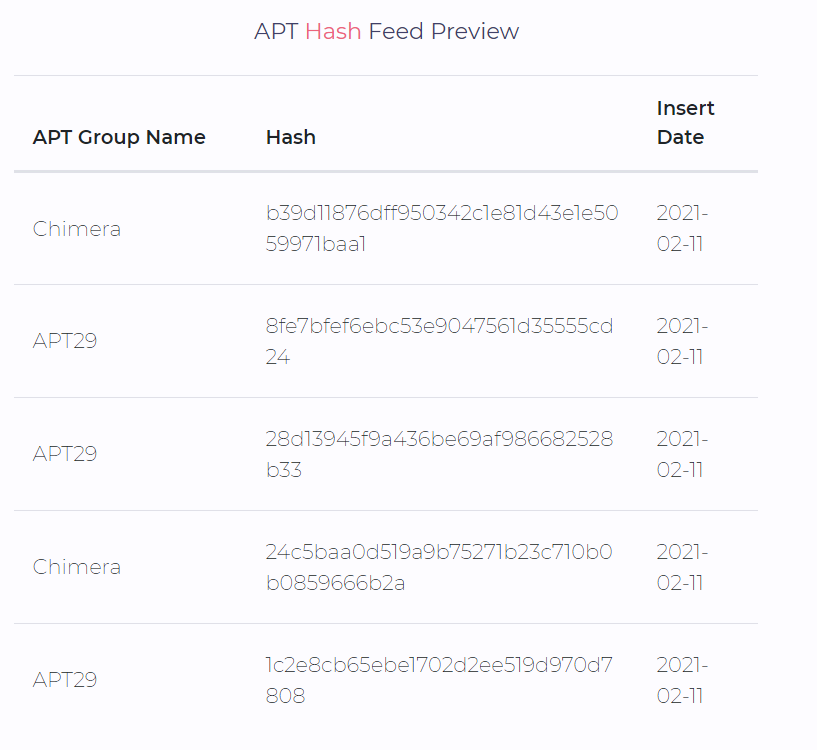
SOCRadar free daily APT feed
SOCRadar collects advanced persistent threat (APT) IOC feeds from several public and private sources and sensors. These feeds are free and refreshed daily. Download daily APT feed
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.


































