
Top Five Causes of Ransomware Attacks
Ransomware attacks deeply affect our lives nowadays. Every day we wake up to the news of another attack. To better prevent these attacks, it is critical to understand the tactics attackers use to deliver.
There are multiple ransomware variants in use in various attack vectors, including through the network, SaaS-based applications, and directly to endpoints.
In this blog post, we will discuss the most commonly used methods in ransomware attacksin 2020. There are several attack vectors ransomware can exploit to take over computers or servers. According to last year’s Datto’s Global State of the Channel Ransomware Report, these are the five most common ways ransomware infects its victims.

1. Phishing Emails
With phishing emails, poor user practices, and lack of tactical cyber threat intelligence training on top of the list of leading causes of ransomware attacks, it becomes clear that end-user education is an essential part of IT security.
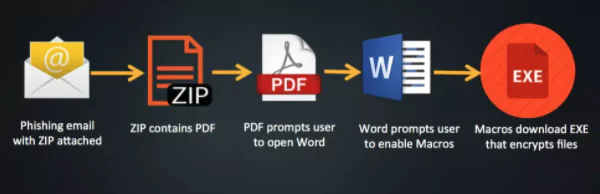
Hackers use crafted emails to trick a victim into opening an attachment or clicking on a link that contains a malicious file. That file can come in different formats, including a PDF, ZIP file, Word document, or JavaScript.
In the case of a Word document, the attacker most commonly tricks the user into “Enabling Macros” upon opening the document. This case lets the attacker run a script that downloads and executes a malicious executable file (EXE) from an external web server. The EXE would include the functions necessary to encrypt the data on the victim’s machine.
Once the data is encrypted and ransomware gains a foothold on one machine, the more advanced ransomware variants will spread to other devices on the network. All it takes is for one person to open an attachment in the mail, and an entire organization can be infected.
2. Poor Users Practises
According to one industry report, the number of crypto-ransomware attacks increased from 2014 by more than 4,000 %, with small to medium-sized enterprises (SMEs) being the main target due to poor security practices. Spams, malware, and bad URLs detection engines or services can be installed in networks rather than individual boxes installed in front of email servers.
We would want such protection as part of the available internet connection to protect email, browsing, and other internet-related operations such as file transfer and remote access.
There are also many excellent commercial cloud-based email spam, malware, and URL detection services available. These are well worth looking for smaller enterprises that must consider costs of ownership, support, and overall effectiveness.
From this point of view, we can emphasize the importance of knowing good practices, especially in small companies. This brings us to the extent of cyber security training.
3. Lack of Cybersecurity Training
A global study of cybersecurity professionals by the Information Systems Security Association (ISSA) and Enterprise Strategy Group (ESG) reveals that the shortage of skills in cybersecurity caused by a lack of cybersecurity training impacts 70% of organizations, and this decline is going on for a long time.
The shortage in this skill area is impacting a majority of organizations in various ways. The most common ramifications include uneven workload for employees and unfilled positions. The impacts of this shortage are far-reaching: the inability of organizations to apply cybersecurity technologies to their full potential puts them at significant risk to the threat of cybercrime.
This study indicates that there has been no significant progress towards finding a solution. There is a strong need to identify the root cause of the shortage of cybersecurity skills. The report suggests a need for a holistic approach to continuous cybersecurity education, where each stakeholder needs to play a role instead of operating in silos.
It is important to note that security training must go beyond just how to identify phishing attacks. While phishing topped the list, weak passwords, open RDP access, and many other user errors were also to blame for breaches.

4.Weak Passwords and Access Management
Weak passwords were one of the most common cybersecurity vulnerabilities in 2019, causing 30% of ransomware infections in 2019. A Google survey about beliefs and behaviors around online security showed that two in three individuals recycle the same password across multiple accounts. More than 50% admitted using one “favorite” password for the majority of the charges. Only one-third of respondents knew how to define the password manager.
Using hard-to-guess passwords represents the first step in securing sensitive online information. However, according to the UK’s National Cyber Security Centre study, password re-use and weak passwords still represent a significant risk for companies and individuals worldwide.
The breach analysis indicated that 23.2 million victim accounts from all parts of the world used “123456” as a password. Another 7.8 million data breach victims chose a 12345678 password. More than 3.5 million people globally picked up the word “password” to protect access to their sensitive information.

5. Open RDP Access
An increasingly popular mechanism in which attackers are infecting victims is through Remote Desktop Protocol (RDP). As the name implies, Remote Desktop Protocol was created to enable IT administrators to securely access a user’s machine remotely to configure it or use the device. RDP typically runs over port 3389.
While opening doors to a device for legitimate use has many benefits, it also presents an opportunity for a bad actor to exploit it for illegitimate use.
Hackers can search for those machines on search engines such as Shodan.io to find devices that are vulnerable to infection. Once the target machines are identified, hackers commonly gain access by brute-forcing the password so they can log on as an administrator.
Open source password-cracking tools help achieve this objective. Popular tools, including Cain and Able, John the Ripper, and Medusa, allow cybercriminals to quickly and automatically try multiple passwords to gain access.
Once they’re in as administrators, hackers have complete control of the machine and initiate the ransomware encryption operation. To create additional damage, some hackers will disable the endpoint security software running on the device or delete Windows file backups before running the ransomware. And this creates even more reason for the victim to pay the ransom, as the Windows backup options may no longer exist.
References
[1]Studies and Surveys About Cybersecurity Skills
[3]Article About The Damages of Using Weak Password
[4]Popular Methods Hackers Use to Spread Ransomware
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































