
What is a Rootkit and How to Detect It
A rootkit is a software that allows hackers to gain access to and control a computer. Although most rootkits attack software and the operating system, some can also infect the hardware and firmware of your machine. Rootkits are good at hiding their presence, yet they are still active when concealed.
When a rootkit infects your system, it behaves like a zombie computer, allowing the hacker to take complete control of your device via remote access. This is the section of the rootkit definition that gives them their strength.
Because the hacker has privileged access to system files and processes, rootkits may appear legitimate, similar to how fileless malware leverages legal programs without leaving a trace. Rootkits cause your computer to deceive you, as well as antivirus and security applications.
Rootkits, acquired on the dark web, can be deployed during phishing attacks or as a social engineering method to persuade victims to allow the rootkits to be placed on their computers, allowing remote attackers administrator access to the machine.
A rootkit allows the remote actor access to and controls practically every part of the operating system once installed (OS). Most anti malware applications can now search for and remove rootkits hidden within a system, unlike older antivirus programs that struggled to detect them.
How Rootkits Work
Because rootkits cannot increase on their own, they must rely on covert techniques to infect computers. Rootkits are installed and hidden until hackers activate them when unwary users grant rootkit installation applications permission to install on their computers. Banking credential stealers, password stealers, keyloggers, antivirus disablers, and bots for distributed denial-of-service assaults are all included in rootkits.
Rootkits are spread via the same methods as other malicious software, such as email phishing campaigns, harmful executable files, designed malicious PDF or Microsoft Word documents, connecting to infected shared drives, or downloading rootkit-infested software from dangerous websites.
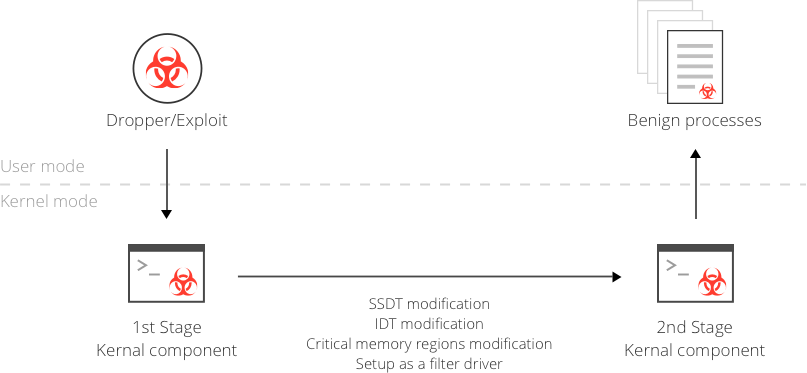
What does the Rootkit do?
Rootkits hide other types of malware on your device, making it more difficult to remove them.
Rootkits allow you to access your operating system from a distant location while avoiding detection. Remote access frauds are becoming increasingly related to rootkit infections.
Some rootkits can infiltrate your system and open a cybersecurity backdoor, allowing the hacker to return later.
A hacker can intercept your internet traffic, watch your keystrokes, and even read your emails if you have a rootkit installed.
Some Rootkit Examples
Necurs
In 2012, Necurs emerged as a rootkit and reportedly detected in 83,000 infections. Associated with elite cybercriminals in Eastern Europe, Necurs stands out due to its technical complexity and ability to evolve.
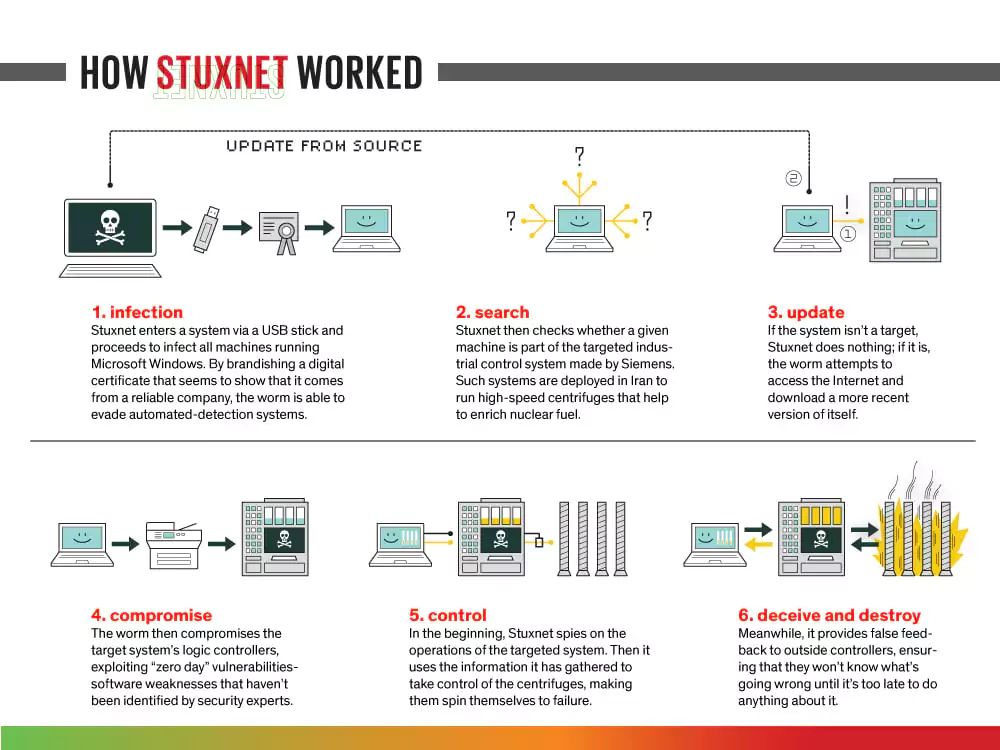
Stuxnet
One of the most notorious rootkits in history is Stuxnet, a malicious computer worm discovered in 2010 and believed to have been in development since 2005. Stuxnet caused substantial damage to the nuclear program of Iran. Although neither country admitted responsibility, it is widely considered a cyberweapon jointly created by the US and Israel in a collaborative effort known as the Olympic Games.
NTRootkit
NTRootkit was one of the first malicious rootkits targeted at Windows OS.
Flame
A computer malware discovered in 2012 that attacks computers running Windows OS. It can record audio, screenshots, keyboard activity, and network traffic.
Tips for Preventing a Rootkit Attack
Make sure your software is up to date. Rootkit users are constantly probing operating systems and other systems for security flaws. Because OS and system software providers are aware of this, they issue security updates as soon as vulnerabilities are discovered in their products. IT should update software as soon as a new version is released as a best practice.
Network monitoring and observability software can quickly alert IT if there is an unusually high amount of activity at any point in the network, if network nodes suddenly go offline, or other signs of network activity could be interpreted as an anomaly.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































