
Mandiant Leak Alleged: A PR Trial?
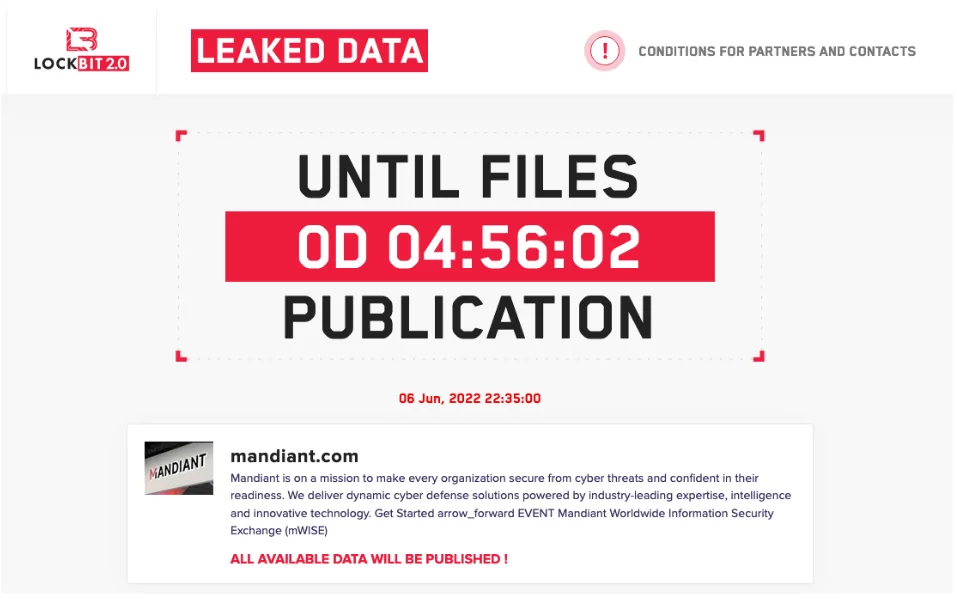
LockBit ransomware gang claimed that they had stolen Mandiant’s data. The gang posted a countdown on their data leak site earlier today. They claimed to have hacked the cybersecurity company and stolen 356,841 files from their network.
Mandiant stated it was investigating the matter at the time the countdown was posted:
“Mandiant is aware of these LockBit-associated claims. At this point, we do not have any evidence to support their claims. We will continue to monitor the situation as it develops.”
“No Evidence of Breach”
The hacking claims came right after Mandiant’s reports regarding Evil Corp, LockBit saying, “All available data will be published.” It also seems timed with RSA Conference.
There was no evidence of a breach; furthermore, LockBit still hasn’t revealed any qualified data on its listing, so it’s still unknown whether the claims are valid. LockBit’s data leak listing only contains a 0-byte file named mandiantyellowpress[.]com.7z that is related to another domain (mandiantyellowpress[.]com, which redirects to ninjaflex[.]com). The domain has no sensitive data in-store.
LockBit might have brought up this incident only to protest against Mandiant’s reports (UNC2165, related to June 2nd) before RSAC. According to Brett Callow, the gang has made several false claims in the past, a threat analyst with cybersecurity firm Emsisoft who follows the ransomware ecosystem closely.
Update on the incident:
For the latest EvilCorp accusations, the LockBit ransomware organization chose to provoke and/or troll Mandiant.
The Mandiant “ransom” has been “released” by the LockBit ransomware organization. The “leaked document” is a note from LockBit debunking recent charges that he’s related to Maksim Yakubets, who was sanctioned by the Department of Justice (i.e., EvilCorp)

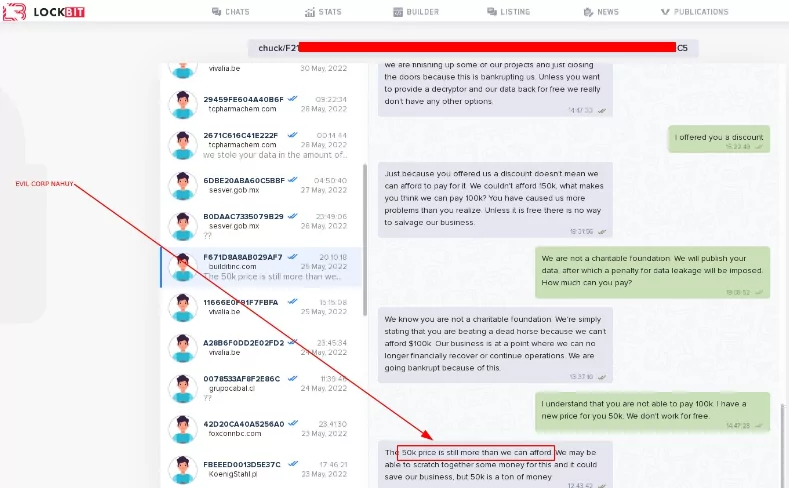
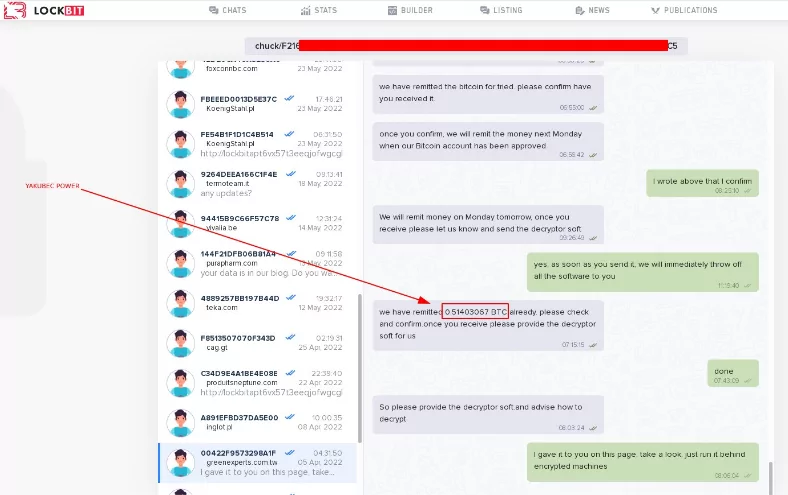
Could LockBit Be Threatening Mandiant?
Cybersecurity experts state that even if the attack was actual, it is not entirely possible to identify the actors who committed the breach. LockBit is a ransomware-as-a-service (RaaS) provider and can provide this service to anyone for a fee.
On the other hand, it is a remarkable detail that Mandiant is active in some critical issues in the field of cyber security. He contributed to detecting Chinese cyber espionage groups in 2013 and to the investigation of the SolarWinds incident in 2020. Recently, it has been watching Russia-based Evil Corp.
FireEye acquired Mandiant in December 2013 for $ 1 million. The hacking of FireEye in 2020 made a big splash, and Symphony Technology Group bought the company for $ 1.2 billion in June 2021. Then Google acquired Mandiant for $ 5.4 billion.
LockBit TTPs
Technique ID Technique Description
T1107 File Deletion
T1055 Process Injection
T1112 Modify Registry
T1215 Kernel Modules and Extensions
T1060 Registry Run Keys / Start Folder
T1179 Hooking
T1055 Process Injection
T1179 Hooking
T1124 System Time Discovery
T1046 Network Service Scanning
T1083 File and Directory Discovery
T1016 System Network Configuration Discovery
T1012 Query Registry
T1082 System Information Discovery
T1057 Process Discovery
T1063 Security Software Discovery
T1047 Windows Management Instrumentation
T1035 Service Execution
T1075 Pass the Hash
IoCs
SHA256 Compile TimeStamp
ffbb6c4d8d704a530bdd557890f367ad904c09c03f53fda5615a7208a0ea3e4d 1992:06:20
286bffaa9c81abfb938fe65be198770c38115cdec95865a241f913769e9bfd3f 2009:02:12
76a77def28acf51b2b7cdcbfaa182fe5726dd3f9e891682a4efc3226640b9c78 2009:02:12
faa3453ceb1bd4e5b0b10171eaa908e56e7275173178010fcc323fdea67a6869 2009:02:12
70cb1a8cb4259b72b704e81349c2ad5ac60cd1254a810ef68757f8c9409e3ea6 2019:11:29
ec88f821d22e5553afb94b4834f91ecdedeb27d9ebfd882a7d8f33b5f12ac38d 2019:12:01
13849c0c923bfed5ab37224d59e2d12e3e72f97dc7f539136ae09484cbe8e5e0 2019:12:11
6fedf83e76d76c59c8ad0da4c5af28f23a12119779f793fd253231b5e3b00a1a 2019:12:17
c8205792fbc0a5efc6b8f0f2257514990bfaa987768c4839d413dd10721e8871 2019:12:18
15a7d528587ffc860f038bb5be5e90b79060fbba5948766d9f8aa46381ccde8a 2020:01:23
0f5d71496ab540c3395cfc024778a7ac5c6b5418f165cc753ea2b2befbd42d51 2020:01:23
0e66029132a885143b87b1e49e32663a52737bbff4ab96186e9e5e829aa2915f 2020:01:23
410c884d883ebe2172507b5eadd10bc8a2ae2564ba0d33b1e84e5f3c22bd3677 2020:02:12
e3f236e4aeb73f8f8f0caebe46f53abbb2f71fa4b266a34ab50e01933709e877 2020:02:16
0f178bc093b6b9d25924a85d9a7dde64592215599733e83e3bbc6df219564335 2020:02:16
1b109db549dd0bf64cadafec575b5895690760c7180a4edbf0c5296766162f18 2020:02:17
26b6a9fecfc9d4b4b2c2ff02885b257721687e6b820f72cf2e66c1cae2675739 2020:02:17
69d9dd7fdd88f33e2343fb391ba063a65fe5ffbe649da1c5083ec4a67c525997 2020:02:17
0a937d4fe8aa6cb947b95841c490d73e452a3cafcd92645afc353006786aba76 2020:02:17
1e3bf358c76f4030ffc4437d5fcd80c54bd91b361abb43a4fa6340e62d986770 2020:02:17
5072678821b490853eff0a97191f262c4e8404984dd8d5be1151fef437ca26db 2020:02:20
ca57455fd148754bf443a2c8b06dc2a295f014b071e3990dd99916250d21bc75 2020-02-20
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.


































