
Ransomware Groups Target VMware and QNAP Products
Linux-based Black Basta ransomware targets VMware ESXi virtual machines, while DeadBolt ransomware targets QNAP NAS (network-attached storage) products.
Black Basta has deployed a new Linux-based version to target VMware ESXi servers. DeadBolt stands out with a multi-layered ransomware implementation for both vendors and victims.
Cyber security researchers underline that ransomware’s constantly evolving tactics and strategies should be observed correctly.
Black Basta Attacks With The Linux Version
In the new report released by Uptycs, it is stated that Black Basta has developed the Linux version specifically to target VMware ESXi servers. Previously, Linux encryptors of seedlings such as LockBit, REvil, AvosLocker, and Hive were on the headlines.
Black Basta looks for /vmfs/volumes stored on the virtual machines’ compromised ESXi servers like other Linux encryptors. There is no detailed information for now, as the encoder was developed to target only ESXi servers.
DeadBolt’s Multi-Layer Extortion Plan
According to the analysis published in Trend Micro, DeadBolt offers multiple cryptocurrency payment options, targeting both vendors and victims, making it different from other NAS ransomware. This extortion technique, which may cause bigger problems for the victims, includes a configuration file that dynamically adjusts itself according to the targeted vendor and can be configured to adapt to other campaigns.
One of the payment plans offered allows the victim and the other the seller to pay a ransom for the decryption key. With a single master key, all victims’ encrypted data can be accessed.
According to Trend Micro’s analysis, this tactic could be adopted by other ransomware groups in the future because a more effective attack can be carried out with less effort.
Who is Black Basta Ransomware?
Black Basta is a newly emerged ransomware gang. Their first activity was in April, they attacked 12 companies in a matter of weeks. There are assumptions that it may be a rebranding of the Conti ransomware group due to the similarity of their leak sites. Whether the case, Black Basta has grown rapidly and already gained its reputation among other ransomware gangs.
Black Basta has targeted enterprises in various sectors and is now targeting VMware ESXi machines running on Linux servers, with most enterprises recently migrating to virtual machines. This makes them able to infiltrate multiple servers simultaneously, with multiple processors, thus providing faster encryption.
Black Basta’s ransomware looks for the /vmfs/volumes directory in which virtual machines reside on the infiltrated VMware ESXi server. ESXi servers, on point, are the only targets of encryption for Black Basta. In this case, they used a combination of the ChaCha20 algorithm and RSA-4096 key for encryption. Black Basta runs with admin privileges while encrypting and deleting shadow copies, then disables recovery and boots in safe mode:
C:WindowsSysNativevssadmin.exe delete shadows /all /quiet
C:WindowsSysNativebcdedit.exe /deletevalue safeboot
C:WindowsSysNativebcdedit /set safeboot networkChanges
After encrypting the victims’ system, Black Basta’s usual routine is to convert all extensions to “.basta” and change icons (%Temp%fkdjsadasd.ico). The gang then changes the desktop wallpaper to a ransom message (%Temp%dlaksjdoiwq.jpg) and instructions in a readme.txt file.

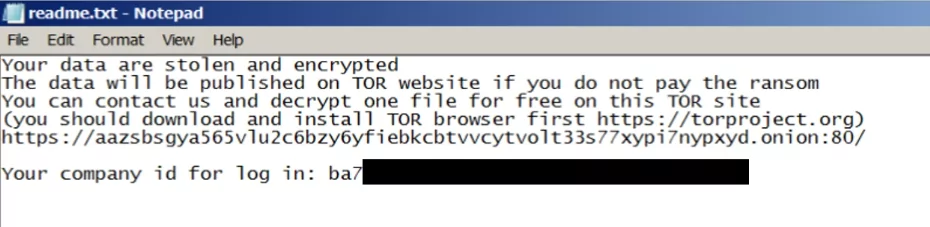
Black Basta IoCs
Domain:
aazsbsgya565vlu2c6bzy6yfiebkcbtvvcytvolt33s77xypi7nypxyd.onion
MD5:
3f400f30415941348af21d515a2fc6a3
SHA256:
5d2204f3a20e163120f52a2e3595db19890050b2faa96c6cba6b094b0a52b0aa
7883f01096db9bcf090c2317749b6873036c27ba92451b212b8645770e1f0b8a
ae7c868713e1d02b4db60128c651eb1e3f6a33c02544cc4cb57c3aa6c6581b6e
17205c43189c22dfcb278f5cc45c2562f622b0b6280dcd43cc1d3c274095eb90
a54fef5fe2af58f5bd75c3af44f1fba22b721f34406c5963b19c5376ab278cd1
1d040540c3c2ed8f73e04c578e7fb96d0b47d858bbb67e9b39ec2f4674b04250
2967e1d97d32605fc5ace49a10828800fbbefcc1e010f6004a9c88ef3ecdad88
f088e6944b2632bb7c93fa3c7ba1707914c05c00f9491e033f78a709d65d7cff
SHA1:
bd0bf9c987288ca434221d7d81c54a47e913600a
Detection Names:
Avast: (Win32:Malware-gen)
Combo Cleaner: (Gen:Heur.Ransom.REntS.Gen.1)
ESET-NOD32: (Win32/Filecoder.OKW)
Kaspersky: (HEUR:Trojan.Win32.DelShad.gen)
Microsoft: (Trojan:Win32/Sabsik.FL.B!ml)
DrWeb -> Trojan.DelShadows.20
BitDefender -> Gen:Heur.Ransom.REntS.Gen.1
Malwarebytes -> Malware.AI.3879235874
Rising -> Ransom.Agent!8.6B7 (CLOUD)
Tencent -> Win32.Trojan.Filecoder.Lmay
TrendMicro -> TROJ_GEN. R002H09DP22
Who is DeadBolt Ransomware?
The DeadBolt ransomware was first seen targeting QNAP Systems, Inc. in January 2022. A report from attack surface solutions provider Censys.io noted that 130,000 QNAP NAS machines were possible targets. Infection was detected in 4,988 services. ASUSTOR, a producer of NAS equipment and video surveillance solutions, was also hit by DeadBolt ransomware attacks that affected an unknown number of its devices a few weeks later. DeadBolt attackers targeted QNAP devices again in March; according to Censys.io, the number of infections had reached 1,146 on March 19, 2022.
We can see that a vast number of devices (2834) were infected with this ransomware and are still infected.
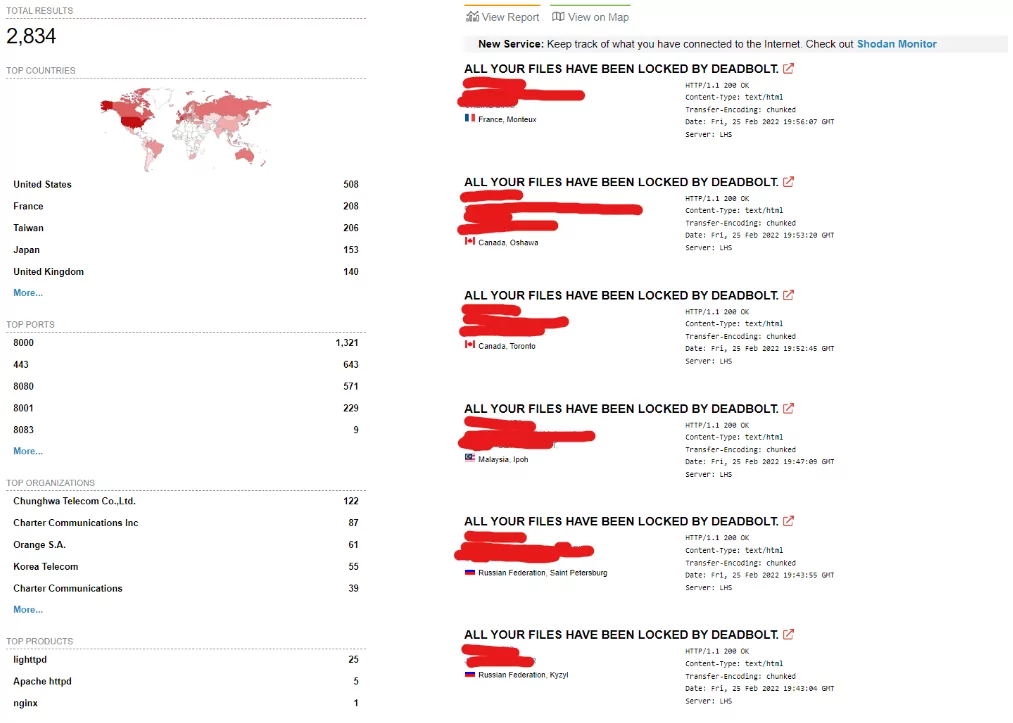
DeadBolt ransomware encrypts all of the files on the devices and appends the.deadbolt extension to each of them. Victims must pay a ransom of 0.03 bitcoins ($1.100) to a unique Bitcoin address in exchange for a decryption key. During its execution, the ransomware leaves a ransom message on the devices’ “login page,” instructing the user on how to restore the files.
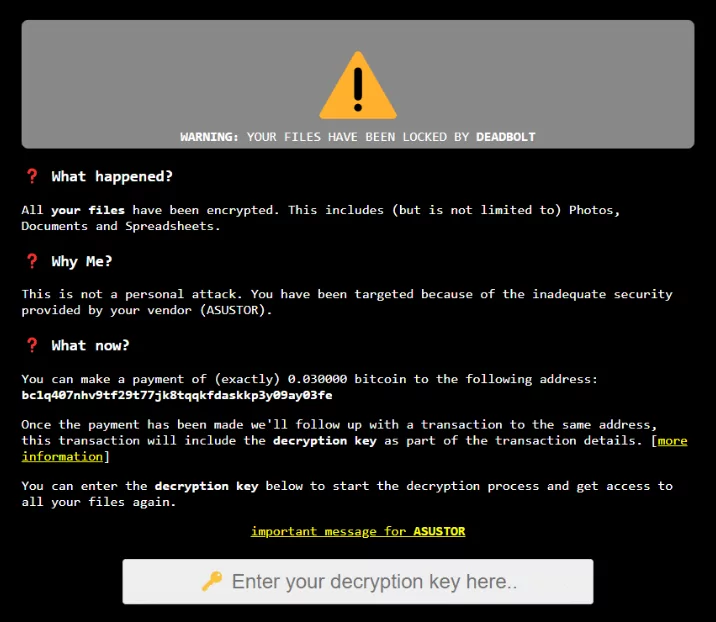
The ransomware begins by placing a binary file in the /mnt/HDA ROOT/ directory. Then the ransomware executable launched with the help of a configuration file that contains a lot of information, including the encryption key.
The /share folder on QNAP devices is then encrypted; here is where the users’ files and folders are stored.
Deadbolt encrypts files with specific file extensions during its execution. The files are encrypted using the AES128 algorithm. It appends the following data to the encrypted file in binary format after encrypting the file’s content:
- .deadbolt extension
- The original file size
- A 16-byte client (victim) ID
- The AES initialization vector (IV) is different for each file
- The SHA-256 of the AES 128-bit key
- The SHA-256 of the “master” key
- 16 null-bytes
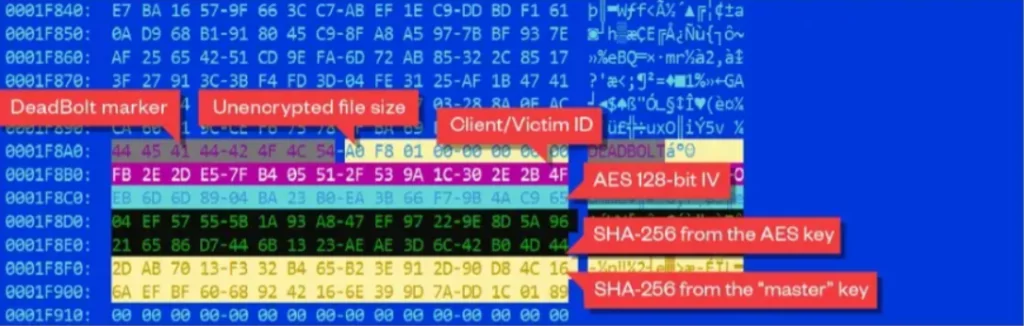
DeadBoltIoCs
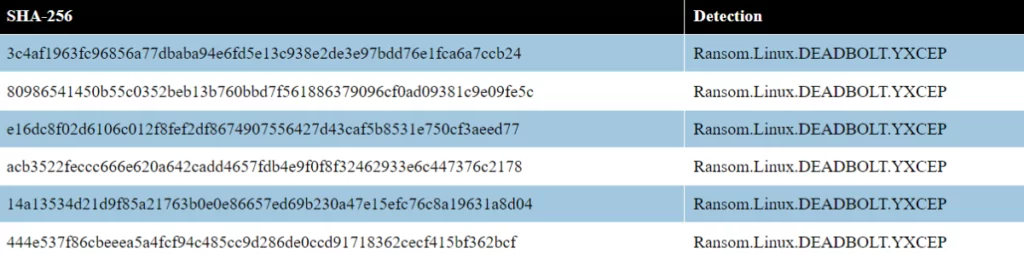
YARA rules:
rule deadbolt_cgi_ransomnote : ransomware {
meta:
description = “Looks for CGI shell scripts created by DeadBolt”
author = “Trend Micro Research”
date = “2022-03-25”
hash = “4f0063bbe2e6ac096cb694a986f4369156596f0d0f63cbb5127e540feca33f68”
hash = “81f8d58931c4ecf7f0d1b02ed3f9ad0a57a0c88fb959c3c18c147b209d352ff1”
hash = “3058863a5a169054933f49d8fe890aa80e134f0febc912f80fc0f94578ae1bcb”
hash = “e0580f6642e93f9c476e7324d17d2f99a6989e62e67ae140f7c294056c55ad27”
strings:
$= “ACTION=$(get_value ”$DATA” ”action”)”
$= “invalid key len”
$= “correct master key”
$= “‘{”status”:”finished”}’”
$= “base64 -d 2>/dev/null”
condition:
uint32be(0) != 0x7F454C46 // We are not interested on ELF files here
and all of them
}
rule deadbolt_uncompressed : ransomware {
meta:
description = “Looks for configuration fields in the JSON parsing code”
author = “Trend Micro Research”
date = “2022-03-23”
hash = “444e537f86cbeeea5a4fcf94c485cc9d286de0ccd91718362cecf415bf362bcf”
hash = “80986541450b55c0352beb13b760bbd7f561886379096cf0ad09381c9e09fe5c”
hash = “e16dc8f02d6106c012f8fef2df8674907556427d43caf5b8531e750cf3aeed77”
strings:
$= “json:”key””
$= “json:”cgi_path””
$= “json:”client_id””
$= “json:”vendor_name””
$= “json:”vendor_email””
$= “json:”vendor_amount””
$= “json:”payment_amount””
$= “json:”vendor_address””
$= “json:”master_key_hash””
$= “json:”payment_address””
$= “json:”vendor_amount_full””
condition:
elf.type == elf.ET_EXEC
and all of them
}
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.



































