
BPFdoor Malware Targets Linux Systems Unnoticed for Five Years
It turned out that the backdoor malware called BPFdoor, which cybersecurity researchers recently discovered, has been targeting Linux and Solaris systems for over five years. BPFdoor allows threat actors to remotely connect to a Linux shell to gain full access to a compromised device.
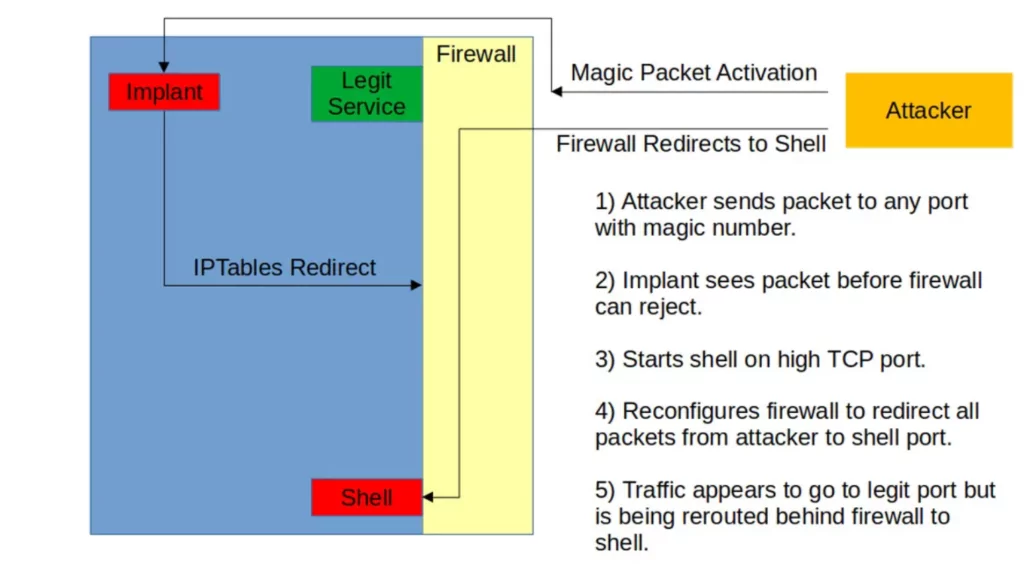
The malware, which does not need to open any ports to gain access, cannot be stopped by firewalls. It is a helpful tool for espionage and persistent attacks, as it can respond to commands from any IP address.
Can Be Used to Send Remote Commands
BPFdoor is defined as a passive backdoor. It can listen for packets from one or more hosts on one or more ports. This allows attackers to send commands to a compromised network remotely.
According to cybersecurity researcher Kevin Beaumont, who published a blog post about the malware, threat actors use a password to control actions. The defining feature of BPFdoor that has allowed it to operate undetected for so long is that it can monitor any port, even if that port is used by legitimate services such as web servers, FTP, or SSH.
BPFdoor Bypasses Firewalls
According to a detailed analysis published in Sandfly Security, including IoCs, BPFdoor implements highly effective circumvention techniques. The article describes these methods as follows:
- Settles in the system memory and deletes all processes related to the process.
- Installs a Berkeley Packet Filter (BPF) sniffer allowing it to run in front of the local firewall to see packets.
- Changes the “iptables” rules to allow the attacker’s communication while receiving a relevant packet.
- Renames itself to “dev/shm/kdmtmpflush” and runs.
- Changes the file’s date to October 30, 2008, before deleting it.
According to Sandfly’s analysis, changing the date may be to hide from a tool that searches the system for new files.
May Have More Than 21 Versions
According to VirusTotal scans, 21 versions of BPFdoor have been detected so far. Findings, the oldest of which is August 2018, are suspected to be more.
It is striking that variants of BPFdoor, which emerged in 2019 and affected Solaris systems, were not detected until 2022, while 28 antiviruses today label it as malware.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.



































